I Can't Generalize a Whole Lot About the Maxthon Cloud Browser, Which Got
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Web Never Forgets: Persistent Tracking Mechanisms in the Wild
The Web Never Forgets: Persistent Tracking Mechanisms in the Wild Gunes Acar1, Christian Eubank2, Steven Englehardt2, Marc Juarez1 Arvind Narayanan2, Claudia Diaz1 1KU Leuven, ESAT/COSIC and iMinds, Leuven, Belgium {name.surname}@esat.kuleuven.be 2Princeton University {cge,ste,arvindn}@cs.princeton.edu ABSTRACT 1. INTRODUCTION We present the first large-scale studies of three advanced web tracking mechanisms — canvas fingerprinting, evercookies A 1999 New York Times article called cookies compre and use of “cookie syncing” in conjunction with evercookies. hensive privacy invaders and described them as “surveillance Canvas fingerprinting, a recently developed form of browser files that many marketers implant in the personal computers fingerprinting, has not previously been reported in the wild; of people.” Ten years later, the stealth and sophistication of our results show that over 5% of the top 100,000 websites tracking techniques had advanced to the point that Edward employ it. We then present the first automated study of Felten wrote “If You’re Going to Track Me, Please Use Cook evercookies and respawning and the discovery of a new ev ies” [18]. Indeed, online tracking has often been described ercookie vector, IndexedDB. Turning to cookie syncing, we as an “arms race” [47], and in this work we study the latest present novel techniques for detection and analysing ID flows advances in that race. and we quantify the amplification of privacy-intrusive track The tracking mechanisms we study are advanced in that ing practices due to cookie syncing. they are hard to control, hard to detect and resilient Our evaluation of the defensive techniques used by to blocking or removing. -

Do Not Track a Nokia Browser Look
Do Not Track Nokia Browser Position - Vikram Malaiya Copyright: Nokia Corporation, 2011 Our understanding of Do Not Track (DNT) • DNT is a technology to enables users to opt out of third-party web tracking • No agreed upon definition of DNT. There are currently 3 major technology proposals for responding to third-party privacy concern. 1. Stanford University and Mozilla’s DNT HTTP Header technique. 2. Blacklist based technique such as Microsoft’s ‘Tracking Protection’ which is part of IE9 3. Network Advertising Initiative’s model of a per company opt-out cookie. Opt-out cookie approach is being promoted by Google. DNT as HTTP Header The Browser adds ‘DNT’/ ‘X-Do-Not-Track’ to its http header. The header is sent out to the server with every web request. This header acts as a signal to the server suggesting that the user wishes to opt out of tracking. Adoption: Firefox 4, IE9 DNT as HTTP Header • Pros: – Scope: Server could apply restrictions to all third party entities and tracking mechanisms – Persistent: No reconfiguration needed once set – Simple: Easy to implement on the browser side • Cons: – Only work as long as the server honors users preferences – No way to enforce national regulations/legislations to servers located beyond country boundaries Block(Black) List / Tracking Protection This is a consumer opt-in mechanism which blocks web connections from known tracking domains that are compiled on a list. First party Third party Adoption: ‘Tracking Protection’ in Internet Explorer 9 cy.analytix.com The downloadable Tracking allow Protection Lists enable IE9 xy.ads.com consumers to control what deny third-party site content can deny track them when they’re ads.tracker.com Tracking Protection online. -

Podcast Presentation
3/18/2009 Today’s Goals Podcasts: Understanding, 1. What is a podcast? Creating, and Deploying them 2. How do I get podcasts? 3. How do I play podcasts? 4. Why should I care about podcasts for Dr. Rick Jerz ediducation? 5. How do I produce my own audio podcasts? [email protected] 6. How do I deliver (deploy) my own podcasts? www.rjerz.com 1 © 2009 rjerz.com 2 © 2009 rjerz.com Demos 1) What is a Podcast? • It must be nothing, since the “podcast” is not in my dictionary. • It is something only children do. • It has something to do with fishing. • It is a radio talk show. • It a music file. • It is a TV program. • It is a lecture. 3 © 2009 rjerz.com 4 © 2009 rjerz.com Podcast Definition1 Rick’s Podcast Definition • Podcasting is a new format for distributing A method of obtaining (subscribing) audio and video content via the Internet. Actually, podcasting is just multimedia computer files (episodes), usually content enclosed into an RSS file. audio (mp3) or video (m4v), from a • RSS means Really Simple Syndication. RSS is a catalog (RSS feed, XML) on the special format based on XML. In fact, RSS Internet (website), and having them feeds are XML files containing data according to the RSS specification, and usually located automatically delivered to your on a website. computer and then to your iPod (or • XML: an HTML‐like file for handling data. other multimedia player) • HTML: Hyper Text Markup Language 1 ‐ http://www.rss‐specification.com/sitemap.htm 5 © 2009 rjerz.com 6 © 2009 rjerz.com 1 3/18/2009 2) How do I get podcasts? iTunes: An Aggregator -

View Managing Devices and Corporate Data On
Overview Managing Devices & Corporate Data on iOS Overview Overview Contents Businesses everywhere are empowering their employees with iPhone and iPad. Overview Management Basics The key to a successful mobile strategy is balancing IT control with user Separating Work and enablement. By personalizing iOS devices with their own apps and content, Personal Data users take greater ownership and responsibility, leading to higher levels of Flexible Management Options engagement and increased productivity. This is enabled by Apple’s management Summary framework, which provides smart ways to manage corporate data and apps discretely, seamlessly separating work data from personal data. Additionally, users understand how their devices are being managed and trust that their privacy is protected. This document offers guidance on how essential IT control can be achieved while at the same time keeping users enabled with the best tools for their job. It complements the iOS Deployment Reference, a comprehensive online technical reference for deploying and managing iOS devices in your enterprise. To refer to the iOS Deployment Reference, visit help.apple.com/deployment/ios. Managing Devices and Corporate Data on iOS July 2018 2 Management Basics Management Basics With iOS, you can streamline iPhone and iPad deployments using a range of built-in techniques that allow you to simplify account setup, configure policies, distribute apps, and apply device restrictions remotely. Our simple framework With Apple’s unified management framework in iOS, macOS, tvOS, IT can configure and update settings, deploy applications, monitor compliance, query devices, and remotely wipe or lock devices. The framework supports both corporate-owned and user-owned as well as personally-owned devices. -

Apple Has Built a Solution Into Every Mac
Overview Mac OS X iPhone iPod + iTunes Resources Vision Mac OS X solutions VoiceOver from third parties. Browse the wide variety of To make it easier for the blind and those with low-vision to use a accessibility solutions supported computer, Apple has built a solution into every Mac. Called VoiceOver, by Mac OS X. Learn more it’s reliable, simple to learn, and enjoyable to use. In Depth Device Support Application Support Downloads VoiceOver Application Support VoiceOver. A unique solution for the vision-impaired. Every new Mac comes with Mac OS X and VoiceOver installed and includes a variety of accessible More than 50 reasons to use applications. You can also purchase additional Apple and third-party applications to use with VoiceOver. VoiceOver. Learn more While this page lists a few of the most popular applications, many more are available. If you use an application with VoiceOver that’s not on this list, and you would like to have it added, send email to [email protected]. Unlike traditional screen readers, VoiceOver is integrated into the operating system, so you can start using new accessible applications right away. You don’t need to buy an update to VoiceOver, install a new copy, or add the application to a “white list.” Moreover, VoiceOver commands work the same way in every application, so once you learn how to use them, you’ll be able to apply what you know to any accessible application. Apple provides developers with a Cocoa framework that contains common, reusable application components (such as menus, text fields, buttons, and sliders), so developers don’t have to re-create these elements each time they write a new application. -

Legal-Process Guidelines for Law Enforcement
Legal Process Guidelines Government & Law Enforcement within the United States These guidelines are provided for use by government and law enforcement agencies within the United States when seeking information from Apple Inc. (“Apple”) about customers of Apple’s devices, products and services. Apple will update these Guidelines as necessary. All other requests for information regarding Apple customers, including customer questions about information disclosure, should be directed to https://www.apple.com/privacy/contact/. These Guidelines do not apply to requests made by government and law enforcement agencies outside the United States to Apple’s relevant local entities. For government and law enforcement information requests, Apple complies with the laws pertaining to global entities that control our data and we provide details as legally required. For all requests from government and law enforcement agencies within the United States for content, with the exception of emergency circumstances (defined in the Electronic Communications Privacy Act 1986, as amended), Apple will only provide content in response to a search issued upon a showing of probable cause, or customer consent. All requests from government and law enforcement agencies outside of the United States for content, with the exception of emergency circumstances (defined below in Emergency Requests), must comply with applicable laws, including the United States Electronic Communications Privacy Act (ECPA). A request under a Mutual Legal Assistance Treaty or the Clarifying Lawful Overseas Use of Data Act (“CLOUD Act”) is in compliance with ECPA. Apple will provide customer content, as it exists in the customer’s account, only in response to such legally valid process. -
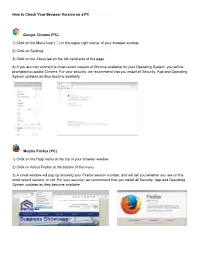
How to Check Your Browser Version on a PC
How to Check Your Browser Version on a PC Google Chrome (PC) 1) Click on the Menu Icon ( ) in the upper right corner of your browser window. 2) Click on Settings 3) Click on the About tab on the left-hand side of the page. 4) If you are not running the most recent version of Chrome available for your Operating System, you will be prompted to update Chrome. For your security, we recommend that you install all Security, App and Operating System updates as they become available. Mozilla Firefox (PC) 1) Click on the Help menu at the top of your browser window. 2) Click on About Firefox at the bottom of the menu. 3) A small window will pop up showing your Firefox version number, and will tell you whether you are on the most recent version, or not. For your security, we recommend that you install all Security, App and Operating System updates as they become available. Internet Explorer (PC) 1) Click on the Gear Icon at the top of your browser window. 2) Click on the About Internet Explorer option. 3) A window will pop up showing you your Internet Explorer version. 4) If you are using Internet Explorer 9 or 10, you will need to make sure that you have TLS 1.2 enabled by: A) Clicking on the Gear Icon again. B) Click on Internet Options. C) Click on the Advanced Tab and scroll down to the option titled “Use TLS 1.2”. (This should be found at the bottome of the list of options.) The box next to this should be checked. -

Copyrighted Material
05_096970 ch01.qxp 4/20/07 11:27 PM Page 3 1 Introducing Cascading Style Sheets Cascading style sheets is a language intended to simplify website design and development. Put simply, CSS handles the look and feel of a web page. With CSS, you can control the color of text, the style of fonts, the spacing between paragraphs, how columns are sized and laid out, what back- ground images or colors are used, as well as a variety of other visual effects. CSS was created in language that is easy to learn and understand, but it provides powerful control over the presentation of a document. Most commonly, CSS is combined with the markup languages HTML or XHTML. These markup languages contain the actual text you see in a web page — the hyperlinks, paragraphs, headings, lists, and tables — and are the glue of a web docu- ment. They contain the web page’s data, as well as the CSS document that contains information about what the web page should look like, and JavaScript, which is another language that pro- vides dynamic and interactive functionality. HTML and XHTML are very similar languages. In fact, for the majority of documents today, they are pretty much identical, although XHTML has some strict requirements about the type of syntax used. I discuss the differences between these two languages in detail in Chapter 2, and I also pro- vide a few simple examples of what each language looks like and how CSS comes together with the language to create a web page. In this chapter, however, I discuss the following: ❑ The W3C, an organization that plans and makes recommendations for how the web should functionCOPYRIGHTED and evolve MATERIAL ❑ How Internet documents work, where they come from, and how the browser displays them ❑ An abridged history of the Internet ❑ Why CSS was a desperately needed solution ❑ The advantages of using CSS 05_096970 ch01.qxp 4/20/07 11:27 PM Page 4 Part I: The Basics The next section takes a look at the independent organization that makes recommendations about how CSS, as well as a variety of other web-specific languages, should be used and implemented. -

Membandingkan Kinerja Web Browser
Membandingkan Kinerja Web Browser Daniel Setiawan, Rendra Setiawan , Rizka Karunia, Rory, I Wayan S. Wicaksana Sistem Informasi, Fakultas Ilmu Komputer, Universitas Gunadarma Jl. KH. Noer Ali, Kalimalang, Bekasi 17134 Telp : (021) 88860117 E-mail : dani_el.s, rendra_bgtz, rizka_1989 @studentsite.gunadarma.ac.id [email protected] Abstrak Internet adalah suatu komunikasi antara satu komputer dengan lainnya secara global melalui suatu media komunikasi. Selain itu, internet juga menyediakan berbagai macam informasi dari seluruh dunia. Sarana yang digunakan dalam mencari informasi ataupun komunikasi melalui internet, kita dapat menggunakan beberapa web browser yang terkenal saat ini. Makalah ini membahas mengenai kinerja web browser, ada lima web browser yang akan digunakan meliputi Mozilla Firefox, Google Chrome, Opera, Safari, dan Maxthon. Kami melakukan beberapa metodologi seperti, fitur, kecepatan, tes benchmark. 1. Pendahuluan 2. Penggunaannya atau pengoperasiannya harus 1.1. Latar Belakang simple sehingga mudah digunakan dan dipahami Internet yang berawal dari riset untuk cara kerjanya. pertahanan dan keamanan serta pendidikan berkembang 3. Kecepatan browser akan membuat penggunanya menjadi perangkat pendukung bisnis yang sangat yang sedang surfing akan menjadi nyaman. Hal ini berpengaruh. Browser adalah program aplikasi yang tergantung pada kemampuan browser, memproses menterjemahkan kode HTML dan merepresentasikan HTML dan Javascript dengan cepat, dan yang halaman web site. Aplikasi inilah yang paling sering paling penting dapat kompetibel dengan semua kita gunakan setiap hari untuk melakukan browsing di jenis website. dunia maya. Jenis browser saat ini semakin banyak dan 4. Fasiltas keamanan harus mutlak tersedia. Karena berkembang denganpesat diantaranya adalah Internet gangguan saat kita browsing dapat datang kapan Explorer, Mozilla Firefox, Opera, Google Chrome, pun. Mulai dari pop-up iklan, virus, hingga praktek Safari, Netscape, Flock, Avant Browser, dll. -

Statement of Justin Brookman Director, Consumer Privacy Center for Democracy & Technology Before the U.S. Senate Committee O
Statement of Justin Brookman Director, Consumer Privacy Center for Democracy & Technology Before the U.S. Senate Committee on Commerce, Science, and Transportation Hearing on “A Status Update on the Development of Voluntary Do-Not-Track Standards” April 24, 2013 Chairman Rockefeller, Ranking Member Thune, and Members of the Committee: On behalf of the Center for Democracy & Technology (CDT), I thank you for the opportunity to testify today. We applaud the leadership the Chairman has demonstrated in examining the challenges in developing a consensus Do Not Track standard and appreciate the opportunity to address the continued insufficiency of self-regulatory consumer privacy protections. CDT is a non-profit, public interest organization dedicated to preserving and promoting openness, innovation, and freedom on the decentralized Internet. I currently serve as the Director of CDT’s Consumer Privacy Project. I am also an active participant in the Worldwide Web Consortium’s Tracking Protection Working Group, where I serve as editor of the “Tracking Compliance and Scope” specification — the document that purports to define what Do Not Track should mean. My testimony today will briefly describe the history of online behavioral advertising and the genesis of the Do Not Track initiative. I will then describe the current state of the World Wide Web Consortium’s efforts to create Do Not Track standards and the challenges going forward to implement Do Not Track tools successfully. I will conclude with my thoughts on the future of Do Not Track. and why I believe that this protracted struggle demonstrates the need for the fundamental reform of our nation’s privacy protection framework for commercial and government collection and use of personal information. -

Amazon Silk Developer Guide Amazon Silk Developer Guide
Amazon Silk Developer Guide Amazon Silk Developer Guide Amazon Silk: Developer Guide Copyright © 2015 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. The following are trademarks of Amazon Web Services, Inc.: Amazon, Amazon Web Services Design, AWS, Amazon CloudFront, AWS CloudTrail, AWS CodeDeploy, Amazon Cognito, Amazon DevPay, DynamoDB, ElastiCache, Amazon EC2, Amazon Elastic Compute Cloud, Amazon Glacier, Amazon Kinesis, Kindle, Kindle Fire, AWS Marketplace Design, Mechanical Turk, Amazon Redshift, Amazon Route 53, Amazon S3, Amazon VPC, and Amazon WorkDocs. In addition, Amazon.com graphics, logos, page headers, button icons, scripts, and service names are trademarks, or trade dress of Amazon in the U.S. and/or other countries. Amazon©s trademarks and trade dress may not be used in connection with any product or service that is not Amazon©s, in any manner that is likely to cause confusion among customers, or in any manner that disparages or discredits Amazon. All other trademarks not owned by Amazon are the property of their respective owners, who may or may not be affiliated with, connected to, or sponsored by Amazon. AWS documentation posted on the Alpha server is for internal testing and review purposes only. It is not intended for external customers. Amazon Silk Developer Guide Table of Contents What Is Amazon Silk? .................................................................................................................... 1 Split Browser Architecture ...................................................................................................... -

Macos at CCSU – What’S New?
MacOS at CCSU – What’s New? MacOS is faster, more secure, and has several new features: 1. Jamf Computer Management and Self-Service Software Installations 2. Encryption and VPN for Laptops 3. Password Reset Procedures and Synchronization with NOMAD 4. Automatic Weekly Maintenance 5. Music, Video, Podcast and Safari Updates Jamf Computer Management & Self-Service Software Installations Jamf is a tool that allows the IT department to manage policies, updates and software on Mac computers. It allows us to keep the software on your computer updated to protect against security threats. Jamf also allows us to set policies to keep your account and computer safe, such as auto locking your computer after 15 minutes of inactivity. In addition, Jamf provides a Self-Service Software Installation tool that allows you to install CCSU-licensed software on your computer when needed. To access Self-Service, click on the icon in the Dock. If you do not see the icon, then open it from the Applications folder. To install an application from Self-Service, simply click on the Install button. Applications available to install include Adobe Creative Cloud, Chrome, Jabber, Webex, SPSS, Firefox, and more. MacOS Laptops If you use a MacBook Pro as your primary CCSU-issued computer, there are some added features: VPN (Virtual Private Network) The VPN connects your MacBook Drive Encryption to the campus network even when off campus. The connection to the The hard drive of your laptop is encrypted for campus network allows direct added security. Encryption uses your BlueNet access to resources such as Secure account as the credentials, so it is important to Apps (secureapps.ccsu.edu) for review the information on Page 2 to ensure the access to Banner, WebNow, encryption password stays synchronized.