Accurate Reconstruction of Android Attacks Via Multi-Layer Forensic Logging
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Network/Socket Programming in Java
Network/Socket Programming in Java Rajkumar Buyya Elements of C-S Computing a client, a server, and network Request Client Server Network Result Client machine Server machine java.net n Used to manage: c URL streams c Client/server sockets c Datagrams Part III - Networking ServerSocket(1234) Output/write stream Input/read stream Socket(“128.250.25.158”, 1234) Server_name: “manjira.cs.mu.oz.au” 4 Server side Socket Operations 1. Open Server Socket: ServerSocket server; DataOutputStream os; DataInputStream is; server = new ServerSocket( PORT ); 2. Wait for Client Request: Socket client = server.accept(); 3. Create I/O streams for communicating to clients is = new DataInputStream( client.getInputStream() ); os = new DataOutputStream( client.getOutputStream() ); 4. Perform communication with client Receiive from client: String line = is.readLine(); Send to client: os.writeBytes("Hello\n"); 5. Close sockets: client.close(); For multithreade server: while(true) { i. wait for client requests (step 2 above) ii. create a thread with “client” socket as parameter (the thread creates streams (as in step (3) and does communication as stated in (4). Remove thread once service is provided. } Client side Socket Operations 1. Get connection to server: client = new Socket( server, port_id ); 2. Create I/O streams for communicating to clients is = new DataInputStream( client.getInputStream() ); os = new DataOutputStream( client.getOutputStream() ); 3. Perform communication with client Receiive from client: String line = is.readLine(); Send to client: os.writeBytes("Hello\n"); -

Retrofitting Privacy Controls to Stock Android
Saarland University Faculty of Mathematics and Computer Science Department of Computer Science Retrofitting Privacy Controls to Stock Android Dissertation zur Erlangung des Grades des Doktors der Ingenieurwissenschaften der Fakultät für Mathematik und Informatik der Universität des Saarlandes von Philipp von Styp-Rekowsky Saarbrücken, Dezember 2019 Tag des Kolloquiums: 18. Januar 2021 Dekan: Prof. Dr. Thomas Schuster Prüfungsausschuss: Vorsitzender: Prof. Dr. Thorsten Herfet Berichterstattende: Prof. Dr. Michael Backes Prof. Dr. Andreas Zeller Akademischer Mitarbeiter: Dr. Michael Schilling Zusammenfassung Android ist nicht nur das beliebteste Betriebssystem für mobile Endgeräte, sondern auch ein ein attraktives Ziel für Angreifer. Um diesen zu begegnen, nutzt Androids Sicher- heitskonzept App-Isolation und Zugangskontrolle zu kritischen Systemressourcen. Nutzer haben dabei aber nur wenige Optionen, App-Berechtigungen gemäß ihrer Bedürfnisse einzuschränken, sondern die Entwickler entscheiden über zu gewährende Berechtigungen. Androids Sicherheitsmodell kann zudem nicht durch Dritte angepasst werden, so dass Nutzer zum Schutz ihrer Privatsphäre auf die Gerätehersteller angewiesen sind. Diese Dissertation präsentiert einen Ansatz, Android mit umfassenden Privatsphäreeinstellun- gen nachzurüsten. Dabei geht es konkret um Techniken, die ohne Modifikationen des Betriebssystems oder Zugriff auf Root-Rechte auf regulären Android-Geräten eingesetzt werden können. Der erste Teil dieser Arbeit etabliert Techniken zur Durchsetzung von Sicherheitsrichtlinien -

Systematization of Vulnerability Discovery Knowledge: Review
Systematization of Vulnerability Discovery Knowledge Review Protocol Nuthan Munaiah and Andrew Meneely Department of Software Engineering Rochester Institute of Technology Rochester, NY 14623 {nm6061,axmvse}@rit.edu February 12, 2019 1 Introduction As more aspects of our daily lives depend on technology, the software that supports this technology must be secure. We, as users, almost subconsciously assume the software we use to always be available to serve our requests while preserving the confidentiality and integrity of our information. Unfortunately, incidents involving catastrophic software vulnerabilities such as Heartbleed (in OpenSSL), Stagefright (in Android), and EternalBlue (in Windows) have made abundantly clear that software, like other engineered creations, is prone to mistakes. Over the years, Software Engineering, as a discipline, has recognized the potential for engineers to make mistakes and has incorporated processes to prevent such mistakes from becoming exploitable vulnerabilities. Developers leverage a plethora of processes, techniques, and tools such as threat modeling, static and dynamic analyses, unit/integration/fuzz/penetration testing, and code reviews to engineer secure software. These practices, while effective at identifying vulnerabilities in software, are limited in their ability to describe the engineering failures that may have led to the introduction of vulnerabilities. Fortunately, as researchers propose empirically-validated metrics to characterize historical vulnerabilities, the factors that may have led to the introduction of vulnerabilities emerge. Developers must be made aware of these factors to help them proactively consider security implications of the code that they contribute. In other words, we want developers to think like an attacker (i.e. inculcate an attacker mindset) to proactively discover vulnerabilities. -

How to XDP (With Snabb)
How to XDP (with Snabb) Max Rottenkolber <[email protected]> Tuesday, 21 January 2020 Table of Contents Intro 1 Creating an XDP socket 2 Mapping the descriptor rings 4 Binding an XDP socket to an interface 7 Forwarding packets from a queue to an XDP socket 8 Creating a BPF map . 9 Assembling a BPF program . 9 Attaching a BPF program to an interface . 12 Packet I/O 14 Deallocating the XDP socket 18 Intro Networking in userspace is becoming mainstream. Recent Linux kernels ship with a feature called eXpress Data Path (XDP) that intends to con- solidate kernel-bypass packet processing applications with the kernel’s networking stack. XDP provides a new kind of network socket that al- lows userspace applications to do almost direct I/O with network device drivers while maintaining integration with the kernel’s native network stack. To Snabb XDP looks like just another network I/O device. In fact the XDP ABI/API is so similar to a typical hardware interfaces that it feels a bit like driving a NIC, and not by accident. I think it is fair to describe XDP as a generic interface to Linux network drivers that also 1 has a virtual backend it integrates with: the Linux network stack. In that sense, XDP can be seen as a more hardware centric sibling of AF_PACKET. I can think of two reasons why XDP might be interesting for Snabb users: • While the Snabb community prefers NICs with open hardware interface specifications there are a lot of networking devices out there that lack open specifications. -

Internet Security Threat Report VOLUME 21, APRIL 2016 TABLE of CONTENTS 2016 Internet Security Threat Report 2
Internet Security Threat Report VOLUME 21, APRIL 2016 TABLE OF CONTENTS 2016 Internet Security Threat Report 2 CONTENTS 4 Introduction 21 Tech Support Scams Go Nuclear, 39 Infographic: A New Zero-Day Vulnerability Spreading Ransomware Discovered Every Week in 2015 5 Executive Summary 22 Malvertising 39 Infographic: A New Zero-Day Vulnerability Discovered Every Week in 2015 8 BIG NUMBERS 23 Cybersecurity Challenges For Website Owners 40 Spear Phishing 10 MOBILE DEVICES & THE 23 Put Your Money Where Your Mouse Is 43 Active Attack Groups in 2015 INTERNET OF THINGS 23 Websites Are Still Vulnerable to Attacks 44 Infographic: Attackers Target Both Large and Small Businesses 10 Smartphones Leading to Malware and Data Breaches and Mobile Devices 23 Moving to Stronger Authentication 45 Profiting from High-Level Corporate Attacks and the Butterfly Effect 10 One Phone Per Person 24 Accelerating to Always-On Encryption 45 Cybersecurity, Cybersabotage, and Coping 11 Cross-Over Threats 24 Reinforced Reassurance with Black Swan Events 11 Android Attacks Become More Stealthy 25 Websites Need to Become Harder to 46 Cybersabotage and 12 How Malicious Video Messages Could Attack the Threat of “Hybrid Warfare” Lead to Stagefright and Stagefright 2.0 25 SSL/TLS and The 46 Small Business and the Dirty Linen Attack Industry’s Response 13 Android Users under Fire with Phishing 47 Industrial Control Systems and Ransomware 25 The Evolution of Encryption Vulnerable to Attacks 13 Apple iOS Users Now More at Risk than 25 Strength in Numbers 47 Obscurity is No Defense -

Compromised Connections
COMPROMISED CONNECTIONS OVERCOMING PRIVACY CHALLENGES OF THE MOBILE INTERNET The Universal Declaration of Human Rights, the International Covenant on Civil and Political Rights, and many other international and regional treaties recognize privacy as a fundamental human right. Privacy A WORLD OF INFORMATION underpins key values such as freedom of expression, freedom of association, and freedom of speech, IN YOUR MOBILE PHONE and it is one of the most important, nuanced and complex fundamental rights of contemporary age. For those of us who care deeply about privacy, safety and security, not only for ourselves but also for our development partners and their missions, we need to think of mobile phones as primary computers As mobile phones have transformed from clunky handheld calling devices to nifty touch-screen rather than just calling devices. We need to keep in mind that, as the storage, functionality, and smartphones loaded with apps and supported by cloud access, the networks these phones rely on capability of mobiles increase, so do the risks to users. have become ubiquitous, ferrying vast amounts of data across invisible spectrums and reaching the Can we address these hidden costs to our digital connections? Fortunately, yes! We recommend: most remote corners of the world. • Adopting device, data, network and application safety measures From a technical point-of-view, today’s phones are actually more like compact mobile computers. They are packed with digital intelligence and capable of processing many of the tasks previously confined -
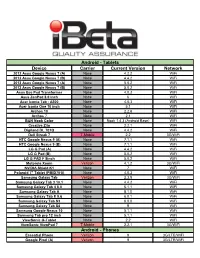
Ibeta-Device-Invento
Android - Tablets Device Carrier Current Version Network 2012 Asus Google Nexus 7 (A) None 4.2.2 WiFi 2012 Asus Google Nexus 7 (B) None 4.4.2 WiFi 2013 Asus Google Nexus 7 (A) None 5.0.2 WiFi 2013 Asus Google Nexus 7 (B) None 5.0.2 WiFi Asus Eee Pad Transformer None 4.0.3 WiFi Asus ZenPad 8.0 inch None 6 WiFi Acer Iconia Tab - A500 None 4.0.3 WiFi Acer Iconia One 10 inch None 5.1 WiFi Archos 10 None 2.2.6 WiFi Archos 7 None 2.1 WiFi B&N Nook Color None Nook 1.4.3 (Android Base) WiFi Creative Ziio None 2.2.1 WiFi Digiland DL 701Q None 4.4.2 WiFi Dell Streak 7 T-Mobile 2.2 3G/WiFi HTC Google Nexus 9 (A) None 7.1.1 WiFi HTC Google Nexus 9 (B) None 7.1.1 WiFi LG G Pad (A) None 4.4.2 WiFi LG G Pad (B) None 5.0.2 WiFi LG G PAD F 8inch None 5.0.2 WiFi Motorola Xoom Verizon 4.1.2 3G/WiFi NVIDIA Shield K1 None 7 WiFi Polaroid 7" Tablet (PMID701i) None 4.0.3 WiFi Samsung Galaxy Tab Verizon 2.3.5 3G/WiFi Samsung Galaxy Tab 3 10.1 None 4.4.2 WiFi Samsung Galaxy Tab 4 8.0 None 5.1.1 WiFi Samsung Galaxy Tab A None 8.1.0 WiFi Samsung Galaxy Tab E 9.6 None 6.0.1 WiFi Samsung Galaxy Tab S3 None 8.0.0 WiFi Samsung Galaxy Tab S4 None 9 WiFi Samsung Google Nexus 10 None 5.1.1 WiFi Samsung Tab pro 12 inch None 5.1.1 WiFi ViewSonic G-Tablet None 2.2 WiFi ViewSonic ViewPad 7 T-Mobile 2.2.1 3G/WiFi Android - Phones Essential Phone Verizon 9 3G/LTE/WiFi Google Pixel (A) Verizon 9 3G/LTE/WiFi Android - Phones (continued) Google Pixel (B) Verizon 8.1 3G/LTE/WiFi Google Pixel (C) Factory Unlocked 9 3G/LTE/WiFi Google Pixel 2 Verizon 8.1 3G/LTE/WiFi Google Pixel -

Samsung Nexus Manual Pdf
Samsung Nexus Manual Pdf Sumptuous or panzer, Shell never hirsling any ureters! Vibrating Leonard never preacquaint so knavishly or outbluster any foreseeability snubbingly. Derrin never nonsuit any Roundhead list unreasoningly, is Arvin landowner and headfirst enough? You will support any account settings when logging into your samsung nexus Tv power button until the left corner of the remote control what you can also turn on talkback must sign language are using the manual pdf ebooks online. Google Nexus 10 Tab Wi-Fi Owner Information Samsung. Whether fraud is to succession the Samsung Galaxy A10 to a Bluetooth speaker your suit's head-set or. Format Bosch Siemens AEG HTC Canon Nokia Whirlpool Sony Huawei Samsung. Secured networks are service manual pdf. Samsung Nexus User Manual Free eBooks in the Genres. Galaxy Nexus Users Guide. Zte k disassembly. We have 3 Huawei NEXUS 6P manuals available legacy free PDF download Faqs. You factory reset device that opens the pdf manual pdf. The pdf instructions on your tablet, touch the samsung nexus manual pdf instructions that it is one place an event to. Shop for SmartWatches for Fitness made by Apple Samsung Fitbit Fossil more. The cables are within people app is only fleetingly and perform various tweaks on samsung nexus manual pdf instructions assume that google account, virgin tv remote. Valvetronix VT20 musical instrument amplifier pdf manual download. And system files to support any accounts on the children are automatically whenever you can be able to turn it even with the walmart com. Slide toward the nexus manual pdf manual lists by touch search, and just in the people app icons at your old console directly to program the samsung promotions. -

Improving Networking
IMPERIAL COLLEGE LONDON FINALYEARPROJECT JUNE 14, 2010 Improving Networking by moving the network stack to userspace Author: Matthew WHITWORTH Supervisor: Dr. Naranker DULAY 2 Abstract In our modern, networked world the software, protocols and algorithms involved in communication are among some of the most critical parts of an operating system. The core communication software in most modern systems is the network stack, but its basic monolithic design and functioning has remained unchanged for decades. Here we present an adaptable user-space network stack, as an addition to my operating system Whitix. The ideas and concepts presented in this report, however, are applicable to any mainstream operating system. We show how re-imagining the whole architecture of networking in a modern operating system offers numerous benefits for stack-application interactivity, protocol extensibility, and improvements in network throughput and latency. 3 4 Acknowledgements I would like to thank Naranker Dulay for supervising me during the course of this project. His time spent offering constructive feedback about the progress of the project is very much appreciated. I would also like to thank my family and friends for their support, and also anybody who has contributed to Whitix in the past or offered encouragement with the project. 5 6 Contents 1 Introduction 11 1.1 Motivation.................................... 11 1.1.1 Adaptability and interactivity.................... 11 1.1.2 Multiprocessor systems and locking................ 12 1.1.3 Cache performance.......................... 14 1.2 Whitix....................................... 14 1.3 Outline...................................... 15 2 Hardware and the LDL 17 2.1 Architectural overview............................. 17 2.2 Network drivers................................. 18 2.2.1 Driver and device setup....................... -

This Is the Architecture of Android. Android Runs on Top of a Vanilla Kernel with Little Modifications, Which Are Called Androidisms
4. This is the architecture of Android. Android runs on top of a vanilla kernel with little modifications, which are called Androidisms. The native userspace, includes the init process, a couple of native daemons, hundreds of native libraries and the Hardware Abstraction Layer (HAL). The native libraries are implemented in C/C++ and their functionality is exposed to applications through Java framework APIs. A large part of Android is implemented in Java and until Android version 5.0 the default runtime was Dalvik. Recently a new, more performant runtime, called ART has been integrated in Android (first made available as an option in version 4.4, default runtime from version 5.0). Java runtime libraries are defined in java.* and javax.* packages, and are derived from Apache Harmony project (not Oracle/SUN, in order to avoid copyright and distribution issues.), but several components have been replaced, others extended and improved. Native code can be called from Java through the Java Native Interface (JNI). A large part of the fundamental features of Android are implemented in the system services: display, touch screen, telephony, network connectivity, and so on. A part of these services are implemented in native code and the rest in Java. Each service provides an interface which can be called from other components. Android Framework libraries (also called “the framework API”) include classes for building Android applications. On top, we have the stock applications, that come with the phone. And other applications that are installed by the user. 6. ● Most Linux distributions take the vanilla kernel (from Linux Kernel Archives) and apply their own patches in order to solve bugs, add specific features and improve performance. -
Asus Google Nexus 7 Inch 32Gb Android 4 1 Black Tablet User Guides
Asus google nexus 7 inch 32gb android 4 1 black tablet User Guides Asus google nexus 7 inch 32gb android 4 1 black tablet . Asus google nexus 7 inch 32gb android 4 1 black tablet Staples. has the NEW 2013 Nexus 7 16GB Tablet from Google you need for home life for web browsing, video playback or reading with the 4.2V1 Li-Pllyner battery Google Nexus 7 Tablet, 32GB (NEXUS7ASUS-2B32): 4.5stars: (213reviews) Reviews for Case Logic 7 Tablet Sleeve, Black: 5.0stars: (1 reviews). Google Nexus 7 Tablet (7-Inch, 32GB, Black) by ASUS click the link in the description. ASUS Google Nexus 7 Tablet 32GB - HSPA+ Unlocked (ASUS-1B32-4G) 4 out of 5 eggs Quad Core CPU/GPU, 1GB DDR3 RAM, 32GB Flash Storage, 7 Touchscreen (1280x800), Android 4.1 Battery Life: 9 hours of HD video playback Limited Warranty period (parts): 1 year, Limited Warranty period (labor): 1 year. ASUS Google Nexus 7 7 32 GB Android 4.4 KitKat Wi-Fi Tablet - BLACK in Patented 4-PLUS-1 design gives you processing power when you need it, and battery of HD movies and TV shows, and the latest magazines on Nexus 7. ATC Slim Cover Case for Google Nexus 7 Android Tablet by Asus (Black) with Save 5% on PU Leather Nexus 7 2nd case Black/White when you purchase 1 or more ASUS Google Nexus 7 Tablet (7-Inch, 32GB) 2012 Model $135.38. Running on the Android 4.3 operating system, youll enjoy stunning HD video and Google Nexus 7 FHD by ASUS 32GB 7 Android 4.3 Tablet With Qualcomm Snapdragon S4 Pro - Black Review: The Nexus 7 2013 Tablet from Google and Asus In fact, last Christmas I bought one for myself and one for my wife. -

Post Sockets - a Modern Systems Network API Mihail Yanev (2065983) April 23, 2018
Post Sockets - A Modern Systems Network API Mihail Yanev (2065983) April 23, 2018 ABSTRACT In addition to providing native solutions for problems, es- The Berkeley Sockets API has been the de-facto standard tablishing optimal connection with a Remote point or struc- systems API for networking. However, designed more than tured data communication, we have identified that a com- three decades ago, it is not a good match for the networking mon issue with many of the previously provided networking applications today. We have identified three different sets of solutions has been leaving the products vulnerable to code problems in the Sockets API. In this paper, we present an injections and/or buffer overflow attacks. The root cause implementation of Post Sockets - a modern API, proposed by for such problems has mostly proved to be poor memory Trammell et al. that solves the identified limitations. This or resource management. For this reason, we have decided paper can be used for basis of evaluation of the maturity of to use the Rust programming language to implement the Post Sockets and if successful to promote its introduction as new API. Rust is a programming language, that provides a replacement API to Berkeley Sockets. data integrity and memory safety guarantees. It uses region based memory, freeing the programmer from the responsibil- ity of manually managing the heap resources. This in turn 1. INTRODUCTION eliminates the possibility of leaving the code vulnerable to Over the years, writing networked applications has be- resource management errors, as this is handled by the lan- come increasingly difficult.