Mass Storage: Getting Down to Basics
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Micro Chroma 68 from Motorola
10-1-79 AN - XXX MICRO CHROMA 68 THE· NEW "BUG" FROM MOTOROLA TVBUG 1® MOS Microcomputer Systems Applications Austin, Texas Prepared By Tim Ahrens Jack Browne Monitor written by John Dumas The information contained in this application note allows the construction of a low cost development system. Object code (machine language) programs may be entered from the keyboard or loaded from audio cassette tapes and be debugged and developed. The programs may be dumped to cassette tape for permanent storage. Techniques for increasing system capabilities are included. Although the information contained herein, as well as any information provided relative thereto, has been carefully reviewed and is believed accurate, Motorola assumes no 1i abil ity ari si ng out of its appl ication or use. Neither does it convey any license under its patent rights nor the rights of others. Copyright 1979 by Motorola Inc. 2 TABLE OF CONTENTS MOS HANDLING RECOMMENDATION 1. INTRODUCTION 2. Micro ChrOO1a 68 KIT PARTS 2.1 The MC6808 Microprocessor with Clock 2.2 The MC6847 Video Display .Generator & MC1372 RF Video Modulator 2.2.1 The MC6847 VDG(Video Display Generator) 2.2.2 The MC1372 RF Video Modulator 2.3 The MC6846P3 ROM, I/O, Timer 2.4 The MC6820/21 Peripheral Interface Adapter (PIA) 2.5 The MC6850 Asynchronous Communications Interface Adapter (ACIA) 3. Micro Chroma 68 HARDWARE 3.1 Ha rdwa re Ope rat ion 3.2 Construction Hints 3.2.1 Micro ChrOO1a 68 Debug 3.3 Soldering Tips 4. TVBUG® SOFTWAR E 4.1 TVBUG® Operating System 4.1.1 G-Go to User Program Function 4.1.2 -

Abkürzungs-Liste ABKLEX
Abkürzungs-Liste ABKLEX (Informatik, Telekommunikation) W. Alex 1. Juli 2021 Karlsruhe Copyright W. Alex, Karlsruhe, 1994 – 2018. Die Liste darf unentgeltlich benutzt und weitergegeben werden. The list may be used or copied free of any charge. Original Point of Distribution: http://www.abklex.de/abklex/ An authorized Czechian version is published on: http://www.sochorek.cz/archiv/slovniky/abklex.htm Author’s Email address: [email protected] 2 Kapitel 1 Abkürzungen Gehen wir von 30 Zeichen aus, aus denen Abkürzungen gebildet werden, und nehmen wir eine größte Länge von 5 Zeichen an, so lassen sich 25.137.930 verschiedene Abkür- zungen bilden (Kombinationen mit Wiederholung und Berücksichtigung der Reihenfol- ge). Es folgt eine Auswahl von rund 16000 Abkürzungen aus den Bereichen Informatik und Telekommunikation. Die Abkürzungen werden hier durchgehend groß geschrieben, Akzente, Bindestriche und dergleichen wurden weggelassen. Einige Abkürzungen sind geschützte Namen; diese sind nicht gekennzeichnet. Die Liste beschreibt nur den Ge- brauch, sie legt nicht eine Definition fest. 100GE 100 GBit/s Ethernet 16CIF 16 times Common Intermediate Format (Picture Format) 16QAM 16-state Quadrature Amplitude Modulation 1GFC 1 Gigabaud Fiber Channel (2, 4, 8, 10, 20GFC) 1GL 1st Generation Language (Maschinencode) 1TBS One True Brace Style (C) 1TR6 (ISDN-Protokoll D-Kanal, national) 247 24/7: 24 hours per day, 7 days per week 2D 2-dimensional 2FA Zwei-Faktor-Authentifizierung 2GL 2nd Generation Language (Assembler) 2L8 Too Late (Slang) 2MS Strukturierte -

2 9215FQ14 FREQUENTLY ASKED QUESTIONS Category Pages Facilities & Buildings 3-10 General Reference 11-20 Human Resources
2 FREQUENTLY ASKED QUESTIONS Category Pages Facilities & Buildings 3-10 General Reference 11-20 Human Resources 21-22 Legal 23-25 Marketing 26 Personal Names (Individuals) 27 Predecessor Companies 28-29 Products & Services 30-89 Public Relations 90 Research 91-97 April 10, 2007 9215FQ14 3 Facilities & Buildings Q. When did IBM first open its offices in my town? A. While it is not possible for us to provide such information for each and every office facility throughout the world, the following listing provides the date IBM offices were established in more than 300 U.S. and international locations: Adelaide, Australia 1914 Akron, Ohio 1917 Albany, New York 1919 Albuquerque, New Mexico 1940 Alexandria, Egypt 1934 Algiers, Algeria 1932 Altoona, Pennsylvania 1915 Amsterdam, Netherlands 1914 Anchorage, Alaska 1947 Ankara, Turkey 1935 Asheville, North Carolina 1946 Asuncion, Paraguay 1941 Athens, Greece 1935 Atlanta, Georgia 1914 Aurora, Illinois 1946 Austin, Texas 1937 Baghdad, Iraq 1947 Baltimore, Maryland 1915 Bangor, Maine 1946 Barcelona, Spain 1923 Barranquilla, Colombia 1946 Baton Rouge, Louisiana 1938 Beaumont, Texas 1946 Belgrade, Yugoslavia 1926 Belo Horizonte, Brazil 1934 Bergen, Norway 1946 Berlin, Germany 1914 (prior to) Bethlehem, Pennsylvania 1938 Beyrouth, Lebanon 1947 Bilbao, Spain 1946 Birmingham, Alabama 1919 Birmingham, England 1930 Bogota, Colombia 1931 Boise, Idaho 1948 Bordeaux, France 1932 Boston, Massachusetts 1914 Brantford, Ontario 1947 Bremen, Germany 1938 9215FQ14 4 Bridgeport, Connecticut 1919 Brisbane, Australia -

TPUG Newsletter
TPUG Newsletter Views and News of Toronto Pet Users Group c/o John Easton, 258 Lake Promenade, Etobicoke, Ontario, M8W 1B3 phone (416) 251-1511 Fall — 2014 From your President Greetings. not had my VIC for very long though number of people that turned up that when a friend of mine got a C64. It took day. For those that do not know me, my years of prodding my parents but I fi- name is Ian Colquhoun and I was elect- nally got a C64C for Christmas 1987. So here we are in 2014, ten years later. ed by the TPUG Board of Directors back Extremely late in the scheme of things, I am pleased to be given the opportuni- in the late spring to be the club’s next but I was happy. A 1541-II arrived 6 ty to lead such a great group of people. president. months later for my birthday. I was set! Already in 2014 we have made some great progress for TPUG’s future. At Before I introduce myself though, I I ran a BBS on my 64 (running Dark- the end of June we were able to close would like to thank Greg Van Laere for Star v3.1) from mid 1988 until early the TPUG locker where we had been his leadership and hard work as club 1994 when college was more important storing our “inventory”. Leif Bloomquist president since he took that post in than trying to keep my board up for the and a small team went through every- 2007. -
Timeline of Computer History
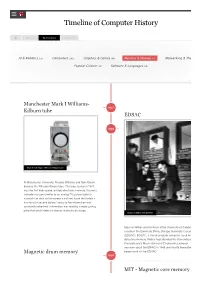
Timeline of Computer History By Year By Category Search AI & Robotics (55) Computers (145) Graphics & Games (48) Memory & Storage (61)(61) Networking & The Popular Culture (50) Software & Languages (60) Manchester Mark I Williams- 1947 Kilburn tube EDSAC 1949 Manchester Mark I Williams-Kilburn tube At Manchester University, Freddie Williams and Tom Kilburn develop the Williams-Kilburn tube. The tube, tested in 1947, was the first high-speed, entirely electronic memory. It used a cathode ray tube (similar to an analog TV picture tube) to store bits as dots on the screen’s surface. Each dot lasted a fraction of a second before fading so the information was constantly refreshed. Information was read by a metal pickup plate that would detect a change in electrical charge. Maurice Wilkes with EDSAC Maurice Wilkes and his team at the University of Cambrid construct the Electronic Delay Storage Automatic Calcula (EDSAC). EDSAC, a stored program computer, used me delay line memory. Wilkes had attended the University of Pennsylvania's Moore School of Engineering summer sessions about the ENIAC in 1946 and shortly thereafter Magnetic drum memory began work on the EDSAC. 1950 MIT - Magnetic core memory ERA founders with various magnetic drum memories Eager to enhance America’s codebreaking capabilities, the US Navy contracts with Engineering Research Associates (ERA) for a stored program computer. The result was Atlas, completed in 1950. Atlas used magnetic drum memory, which stored information on the outside of a rotating cylinder coated with ferromagnetic material and circled by read/write heads in Jay Forrester holding early core memory plane fixed positions. -

The Commodore 128 1 What's in This Book 2 the Commodore 128: Three Computers in One 3 the C128 Mode 6 the CP/M Mode 9 the Bottom Line 9
The Official Book T {&~ Commodore \! 128 Personal Computer - - ------~-----...::.......... Mitchell Waite, Robert Lafore, and Jerry Volpe The Official Book ~~ Commodore™128 Personal Computer Howard W. Sams & Co., Inc. A Subsidiary of Macmillan, Inc. 4300 West 62nd Street, Indianapolis, Indiana 46268 U.S.A. © 1985 by The Waite Group, Inc. FIRST EDITION SECOND PRINTING - 1985 All rights reserved. No part of this book shall be reproduced, stored in a retrieval system, or transmitted by any means, electronic, mechanical. photocopying, recording, or otherwise, with out written permission from the publisher. No patent liability is assumed with respect to the use of the information contained herein. While every precaution has been taken in the preparation of this book, the publisher assumes no responsibility for errors or omissions. Neither is any liability assumed for damages resulting from the use of the information contained herein. International Standard Book Number: 0-672-22456-9 Library of Congress Catalog Card Number: 85-50977 Illustrated by Bob Johnson Typography by Walker Graphics Printed in the United States of America The Waite Group has made every attempt to supply trademark information about company names, products, and services mentioned in this book. The trademarks indicated below were derived from various sources. The Waite Group cannot attest to the accuracy of this information. 8008 and Intel are trademarks of Intel Corp. Adventure is a trademark of Adventure International. Altair 8080 is a trademark of Altair. Apple II is a registered trademark of Apple Computer, Inc. Atari and Atari 800 are registered trademarks of Atari Inc. Automatic Proofreader is a trademark of COMPUTE! Publications. -

730013 Subsystem B Users M
Subsystem B User's Manual ProcessorTechnology 7100 Johnson Industrial Way Pleasanton, California 94566 Copyright © 1977, Processor Technology Corporation First Printing, August, 1977 All rights reserved. Manual No. 730013 SECTION TITLE PAGE 1.0 PROCESSOR TECHNOLOGY SUBSYSTEM B .... · 1-1 1.1 3P+S Peripheral Interface Module . .. .. 1-1 1.2 VDM-l Video Display Module . .. 1-3 1.3 Subsystem B Memory: 4KRA, 8KRA, or 16 KRA 1-3 1.4 CUTS: Computer User's Tape System.. .. 1-4 1.5 Subsystem B GPM (General Purpose Memory) .... 1-4 2.0 SUBSYSTEM B AND OPTIONS · . 2-1 2.1 Unpacking and Auditing Shipment Received · 2-1 2.2 Progression for Assembling Kits . 2-2 2.3 Printed Circuit Board Orientation and Legend. · 2-2 3.0 INSTALLING SUBSYSTEM B . 3-1 3.1 Jumpering 3P+S · . 3-1 3.1.1 Jumpering 3P+S for Keyboard Console and RS232-C ......... 3-1 3.1.2 Jumpering 3P+S for Keyboard Console and Current Loop Serial Interface . 3-1 3.2 VDM-1 Jumpering and Option Selection ... 3-2 3.3 CUTS Jumpering and Option Selection. .. 3-2 3.4 GPM Switch Selection ............. 3-2 3.5 Interconnect Cables and Diagrams ..... 3-8 4.0 SUBSYSTEM B OPERATING PROCEDURES . · . 4-1 4.1 Bringing Up the System . · . 4-2 4.2 Summary of CUTER Commands . · . 4- 3 4.3 Console Commands . · . 4-4 4.3.1 DUMP Command . · 4-5 4.3.2 ENTER Command · . 4-6 4.3.3 EXECUTE Command . 4-7 4.4 Cassette Interface Commands . 4-7 4.4.1 SAVE Commands . -

Electronic Dreams: How 1980S Britain Learned to Love the Computer. London: Bloomsbury Sigma, 2016
Lean, Tom. "The Boom." Electronic Dreams: How 1980s Britain Learned to Love the Computer. London: Bloomsbury Sigma, 2016. 115–141. Bloomsbury Collections. Web. 28 Sep. 2021. <http://dx.doi.org/10.5040/9781472936653.0008>. Downloaded from Bloomsbury Collections, www.bloomsburycollections.com, 28 September 2021, 15:11 UTC. Copyright © Tom Lean 2016. You may share this work for non-commercial purposes only, provided you give attribution to the copyright holder and the publisher, and provide a link to the Creative Commons licence. CHAPTER FIVE The Boom uying from a computer shop could be a bewildering Bexperience in 1983. You enter in search of expert help, tentatively move your way past the screens fl ashing with the newest games, racks of computer magazines and programming books, and fi nd a pale teenager who seems to work here. ‘ You want to buy your fi rst computer? ’ he asks ‘ Well, let ’ s see what we ’ ve got in stock … want to learn about computers? How about trying a ZX81? A bit old, and black and white, and the keyboard is a piece of plastic, but it ’ s cheap and there ’ s lots of software for it … Perhaps a BBC Micro? It’ s the one the kids use at school, and it ’ s been on television a lot, and its got Econet, the Tube, a printer port, ah but it’ s £ 400 … maybe something cheaper? The Oric ’ s quite nice if you like a 6502 machine, but there ’ s loads more games for the Spectrum… You don ’ t like the rubber keyboard? I ’ d off er you an Electron but we ’ ve got none in, so try a good old VIC-20, it ’ s only got 5k of RAM but we sell an expansion pack. -

The Life of a Data Byte Be Kind and Rewind
TEXT COMMIT TO 1 OF 24 memory ONLY The Life of a Data Byte Be kind and rewind JESSIE FRAZELLE byte of data has been stored in a number of different ways through the years as newer, better, and faster storage media are introduced. A byte is a unit of digital information that most commonly refers to eight bits. A bit is a unit of information Athat can be expressed as 0 or 1, representing a logical state. Let’s take a brief walk down memory lane to learn about the origins of bits and bytes. Going back in time to Babbage’s Analytical Engine, you can see that a bit was stored as the position of a mechanical gear or lever. In the case of paper cards, a bit was stored as the presence or absence of a hole in the card at a specific place. For magnetic storage devices, such as tapes and disks, a bit is represented by the polarity of a certain area of the magnetic film. In modern DRAM (dynamic random-access memory), a bit is often represented as two levels of electrical charge stored in a capacitor, a device that stores electrical energy in an electric field. (In the early 1960s, the paper cards used to input programs for IBM mainframes were known as Hollerith cards, named after their inventor, Herman Hollerith from the Tabulating Machines Company—which through numerous mergers is what is now known as IBM.) In June 1956, Werner Buchholz (archive. computerhistory.org) coined the word byte (archive. org) to refer to a group of bits used to encode a single acmqueue | may-june 2020 1 COMMIT TO 2 OF 24 memory I character of text (bobbemer.com). -

230 Computer
230 BBGICDEYoBu . - ' | :-l! . \L H..;I 1' _ I -. .'..-4-! '."-"'u _ 1- I-_I_,u——‘-M . ' 3. -"-..*-"" I "c. -' :- || ..— I '. '- ' ' . I .'‘ COMPUTER by Steve fi con/{Iii Ciarcia A Note about this book and its freefree availability oonlinenline Readers are encouraged to download this book of desidesigngn guidelines and application notes from Steve CiarciaCiarcia,, founder and editorial director of Circuit Cellar magazinemagazine.. Although the original title first appeared in 1981, prepre-dating-dating Circuit Cellar “the”the magazine,” II still get a number of purchase requests each year from electronics enthusiasts. Some are just interested in StevSteve’se’s brand of designing and ability to overcome obstacles, while others still find themselves tweaking projects that use parts described in Steve’s projects. Please note: The original work was only available as a hard copy. Thanks to Andrew Lynch and Bill Bradford for their work in creating the PDF and getting permission from copyright holder Steve Ciarcia to releaserelease it. Scanning done by Bill Bradford. You will be pleased to know that the same style of embedded computing articles can be found each month through Circuit Cellar magazine. Please visit www.circuitcellar.com to learn about this monthly resource for professional designers and electronics enthusiasts alike. Please enjoy “”BuildBuild Your Own Z80280 ComputerComputer”” as a great blast from the past. ItItss style is the foundation on which Circuit Cellar magazine was built and continues to grow. I llookook forward to seeing you become a part of the ongoing Circuit Cellar success story. Sincerely, Sean Donnelly, PublisherPublisher— – Circuit Cellar [email protected]@circuitcel|ar.com CIRCUIT CELLAIFI'llE MALLAZINE FUR L'UMI’U'I'ER Al-‘l’LiCA'I'lUNb Build YourOwn ZSO Computer Design Guidelines and Application Notes ; g Steve Ciarcia i BYTE Books/A McGraw-Hill Publication/ 70 Main S-t/Peterborough New Hampshire 03458 p Build Your Own Z80 Computer Copyright © 1981 by Steve Ciarcia. -

IBM Netfinity Enterprise Storage Tape Backup Subsystems
Netfinity Technology Center IBM Netfinity Enterprise Storage Tape Backup Subsystems Executive Summary Today’s applications process business data that must be maintained during system outages. The Tape drive is the industry standard for data backup. IBM’s Netfinity product line provides complete application solutions for today’s industry-standard, Intel-processor-based server marketplace. This paper addresses the technologies, performance, and capacity of current tape solutions offered in the Intel processor based server segments. 0498 IBM Netfinity White Paper Notice ã International Business Machines Corporation 1998. All rights reserved. References in this publication to IBM products, programs or services do not imply that IBM intends to make these available in all countries in which IBM operates. Any reference to an IBM product, program, or service is not intended to state or imply that only IBM’s product, program, or service may be used. Any functional equivalent program that does not infringe any of IBM’s intellectual property rights may be used instead of the IBM product, program or service. Information in this paper was developed in conjunction with use of the equipment specified, and is limited in application to those specific hardware and software products and levels. IBM may have patents or pending patent applications covering subject matter in this document. The furnishing of this document does not give you any license to these patents. You can send license inquiries, in writing, to the IBM Director of Licensing, IBM Corporation, 500 Columbus Avenue, Thornwood, NY 10594 USA. The information contained in this document has not been submitted to any formal IBM test and is distributed AS IS WITHOUT WARRANTIES OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. -

JULY 1977 ECU in the Queue Volume 2 Number 7
/Quit ¡pi: www.americanradiohistory.com The 9 -inch screen of the CT-VM monitor ($175) shown here with Southwest's new CT-64 illustrates the terminal's 64- character lines, switchable control character printing, and word highlighting. At just $500 for both, these matching units provide a complete CRT terminal with full cursor control, 110 -1200 Baud serial interface, and many other features. Now $325 buys a 64- character terminal kit Our new CT-64 terminal kit gives you scrolling, full The CT-64's features include: cursor control, 128 -character ASCII display (with both 64 or 32 characters per line (16 lines) upper and lower case), and two 1K memory pages. It's Premium display with both upper and lower case usable with any 8 -bit computer. letters, and descenders (g, j, etc.) Two 1K Add our optional fully assembled 12 MHz CT-VM pages of 8 -bit memory monitor for another $175 and you'll have the best CRT Scrolling or page mode operation terminal buy offered anywhere. 32 control character decoding Prints control characters (selectable) The CT-64 gives you full cursor control, home -up and 128 -character ASCII set erase, erase to end of line or end of frame, cursor on /off, 110 /220 Volt 50 -60 Hz power supply screen reversal, scroll or page, solid or blinking cursor, Highlights words with reversed background page selection, and end -of -page warning beeper. Optional 9 -inch monitor with matching cover available Complete with keyboard, power supply, 110 -1200 Baud serial interface, and case Okay, Southwest, I know a bargain when I see it or BAC # Exp.