AST2050 User Guide V1.01
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

BIOS EPOX, Motherboard 4PCA HT ======Change Optimized Defaults Are Marked !!! Změny Oproti DEFAULT Jsou Označeny !!! ======
BIOS EPOX, motherboard 4PCA HT =================================================== Change Optimized Defaults are marked !!! Změny oproti DEFAULT jsou označeny !!! =================================================== Standard CMOS Features ====================== Halt On [All, But Keyboard] !!! Advanced BIOS Features ====================== CPU Feature-Delay Prior to Termal [16 Min] Limit CPUID MaxVal [Disabled] Hard Disk Boot Priority Bootovani disku CPU L1 & L2 Cache [Enabled] Hyper-Threading Technology [Enabled] !!! First Boot Device [HDD] !!! Second Boot Device [Disabled] !!! Third Boot Device [Disabled] !!! Boot Other Device [Disabled] !!! Boot Up Floppy Seek [Disabled] !!! Boot Up NumLock Status [On] Security Option [Setup] x APIC Mode (zasedle) [Enabled] HDD S.M.A.R.T .... [Disabled] Advanced Chipset Features ========================= DRAM Timing Selectable [By SPD] x x x x Agresive Memory Mode [Standard] x x x System BIOS Cacheable [Enabled] VIDEO BIOS Cacheable [Disabled] AGP Aperture ... [128] Init Display First [AGP] DRAM DATA Inregrity Mode [ECC] Integrated Peripherals ====================== On Chip IDE Device: IDE HDD [Enabled] IDE DMA [Enabled] On-Chip Primary [Enabled] IDE Primary MASTER PIO [Auto] ... [Auto] On-Chip Secondary [Enabled] IDE Secondary MASTER PIO[Auto] ... [Auto] On Chip Serial ATA [Disabled] (ostatni sede) OnBoard Device: USB Controller [Enabled] USB 2.0 [Enabled] USB Keyboard [Auto] USB Mouse [Disabled] !!! AC97 Audio [Disabled] !!! Game Port [Disabled] !!! Midi Port [Disabled] !!! On Board LAN Device [Enabled] -

Product Line Card
Product Line Card ® CABLES Lenovo KEYBOARDS & NAS/SAN POWER SOLID STATE Accell MSI MICE D-Link PROTECTION/UPS DRIVES APC Cables by BAFO Shuttle Adesso Intel APC ADATA Link Depot ViewSonic Alaska Promise Opti-UPS Corsair StarTech.com ZOTAC Azio QNAP Tripp Lite Crucial SYBA Cooler Master SansDigital Intel EXTERNAL Corsair Synology POWER Kingston CASES ENCLOSURES Genius Thecus SUPPLIES OCZ AIC AcomData KeyTronic WD Antec PNY Antec Cremax Lenovo Apex Samsung Apex Eagle Tech Logitech NETWORKING Cooler Master WD CHENBRO iStarUSA Microsoft ASUS Corsair Compucase SIIG Razer Cisco Epower SURVEILLANCE Cooler Master Smarti SIIG D-Link FSP PRODUCTS Corsair StarTech.com Thermaltake Edimax In Win AVer Intel TRENDnet Emulex Intel D-Link In Win Vantec MEMORY Encore Electronics iStarUSA TP-LINK iStarUSA Zalman ADATA EnGenius Nspire TRENDnet Lian Li AMD Huawei Seasonic Vivotek Nspire FANS/HEATSINKS Corsair Intel Sentey Vonnic NZXT Antec Crucial Keebox Shuttle Zmodo Sentey Cooler Master Kingston NETGEAR Sparkle Power Edimax Supermicro Corsair Patriot SIIG Thermaltake Keebox Thermaltake Dynatron Samsung StarTech.com Zalman Winsis USA Enermax SYBA TABLETS Zalman Intel MONITORS TP-LINK PROJECTORS ASUS Noctua AOC TRENDnet ASUS GIGABYTE CONTROLLER StarTech.com ASUS Tripp Lite ViewSonic Lenovo CARDS Supermicro Hanns.G ZyXEL ViewSonic 3Ware Thermaltake Lenovo SERVERS HighPoint Vantec LG Electronics NOTEBOOKS/ AIC USB DRIVES Intel Zalman Planar NETBOOKS ASUS ADATA LSI ViewSonic ASI ASI Corsair Microwise HARD DRIVES ASUS Intel Kingston Promise ADATA MOTHERBOARDS -
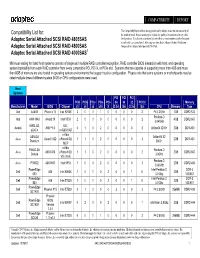
Compatibility List For: Adaptec Serial Attached SCSI RAID 4805SAS Adaptec Serial Attached SCSI RAID 4800SAS Adaptec Serial Atta
COMPATIBILITY REPORT This Compatibility Report reflects testing performed by Adaptec to test the interoperability of Compatibility List for: the products listed. It does not attempt to validate the quality of or preference for any of the Adaptec Serial Attached SCSI RAID 4805SAS listed products. It is also not an inclusive list and reflects a representative sample of products in each of the categories listed. All testing was done by the Adaptec Product Verification Adaptec Serial Attached SCSI RAID 4800SAS Group and the Adaptec InterOperability Test Lab. Adaptec Serial Attached SCSI RAID 4000SAS1 Minimum testing for listed host systems consists of single and multiple RAID controller recognition, RAID controller BIOS interaction with host, and operating system bootability from each RAID controller from every compatible PCI, PCI-X, or PCIe slot. Systems that are capable of supporting more than 4GB and more then 8GB of memory are also tested in operating system environments that support such a configuration. Please note that some systems or motherboards may be listed multiple times if different system BIOS or CPU configurations were used. Host Systems PCI PCI PCI PCIe PCIe PCIe PCIe PCI- 64 64 32 PCI 32 Memory Manufacturer Model BIOS Chipset x1 x4 x8 x16 X (3.3v) (5v) (3.3v) (5v) CPU Memory Type Abit AA8XE Phoenix 16 Intel 925XE 3 0 0 1 0 0 0 0 2 P4 3.2GHz 1GB DDR2-533 Pentium-D Abit AW8-MAX Award 19 Intel 955X 2 0 0 0 0 0 0 0 2 4GB DDR2-667 3.04GHz 939SLI32- ULI - Asrock AMI P1.0 0 1 0 2 0 0 0 0 3 Athlon64 3200+ 2GB DDR-400 eSATA m1695/1697 -
Product Line Card
Product Line Card 3Com Corporation ATI Technologies Distribution CCT Technologies 3M Attachmate Corporation Century Software 4What, Inc. Autodesk, Inc. Certance 4XEM Avaya, Inc. Certance LLC Averatec America, Inc. Chanx Absolute Software Avocent Huntsville Corp. Check Point Software ACCPAC International, Inc. Axis Communications, Inc. Cherry Electrical Products Acer America Corporation Chicony Adaptec, Inc. Barracuda Networks Chief Manufacturing ADC Telecommunications Sales Battery Technology, Inc. Chili Systems Addmaster Bay Area Labels Cingular Interactive, L.P. Adesso Bay Press & Packing Cisco Systems, Inc. Adobe Systems, Inc. Belkin Corporation CMS Products, Inc. Adtran Bell & Howell CNET Technology, Inc. Advanced Digital Information BenQ America Corporation Codi Advanced Micro Devices, Inc. Best Case & Accessories Comdial AEB Technologies Best Software SB, Inc. Computer Associates Aegis Micro/Formosa– USA Bionic CCTV ComputerLand AI Coach Bionic Video Comtrol Corporation Alcatel Internetworking, Inc. Black Box Connect Tech All American Semi Block Financial Corel Corporation Allied Telesyn BorderWare Corporate Procurement Altec Lansing Technologies, Inc. Borland Software Corporation Corsair Althon Micro Boundless Technologies, Inc. Corsair Altigen Brady Worldwide Countertrade Products Alvarion, Inc. Brands, Inc. Craden AMCC Sales Corp. Brenthaven Creative Labs, Inc. AMD Bretford Manufacturing, Inc. CRU-Dataport American Portwell Technology Brooktrout Technology, Inc. CryptoCard American Power Conversion Brother International Corporation CTX Anova Microsystems Buffalo Technology/Melco Curtis Young Corporation Antec, Inc. Business Objects Americas AOpen America, Inc. BYTECC Dantz Development Corp. APC Data911 Arco Computer Products, LLC Cables To Go, Inc. Datago Ardence Cables Unlimited Dataram Areca. US Caldera Systems, Inc. Datawatch Corporation Arima Computer Cambridge Soundworks Decision Support Systems Artronix Canon USA Inc. Dedicated Micros Aspen Touch Solutions, Inc. Canton Electronics Corporation Dell Astra Data, Inc. -

AMD Reports Fourth Quarter and Annual 2019 Financial Results
January 28, 2020 AMD Reports Fourth Quarter and Annual 2019 Financial Results – Record quarterly revenue of $2.13 billion; record annual revenue of $6.73 billion – – Gross margin expanded to 45 percent in Q4 2019 and 43 percent for 2019 – SANTA CLARA, Calif., Jan. 28, 2020 (GLOBE NEWSWIRE) -- AMD (NASDAQ:AMD) today announced revenue for the fourth quarter of 2019 of $2.13 billion, operating income of $348 million, net income of $170 million and diluted earnings per share of $0.15. On a non- GAAP(*) basis, operating income was $405 million, net income was $383 million and diluted earnings per share was $0.32. For fiscal year 2019, the company reported revenue of $6.73 billion, operating income of $631 million, net income of $341 million and diluted earnings per share of $0.30. On a non- GAAP(*) basis, operating income was $840 million, net income was $756 million and diluted earnings per share was $0.64. GAAP Quarterly Financial Results Q4 2019 Q4 2018 Y/Y Q3 2019 Q/Q Revenue ($B) $ 2.13 $ 1.42 Up 50% $ 1.80 Up 18% Gross margin 45 % 38 % Up 7pp 43 % Up 2pp Operating expense ($M) $ 601 $ 509 Up $92 $ 591 Up $10 Operating income ($M) $ 348 $ 28 Up $320 $ 186 Up $162 Net income ($M) $ 170 $ 38 Up $132 $ 120 Up $50 Earnings per share $ 0.15 $ 0.04 Up $0.11 $ 0.11 Up $0.04 Non-GAAP(*) Quarterly Financial Results Q4 2019 Q4 2018 Y/Y Q3 2019 Q/Q Revenue ($B) $ 2.13 $ 1.42 Up 50% $ 1.80 Up 18% Gross margin 45 % 41 % Up 4pp 43 % Up 2pp Operating expense ($M) $ 545 $ 474 Up $71 $ 539 Up $6 Operating income ($M) $ 405 $ 109 Up $296 $ 240 Up $165 Net -

Biostar P43 A7 Driver 8/13/2015
Download Instructions Biostar P43 A7 Driver 8/13/2015 For Direct driver download: http://www.semantic.gs/biostar_p43_a7_driver_download#secure_download Important Notice: Biostar P43 A7 often causes problems with other unrelated drivers, practically corrupting them and making the PC and internet connection slower. When updating Biostar P43 A7 it is best to check these drivers and have them also updated. Examples for Biostar P43 A7 corrupting other drivers are abundant. Here is a typical scenario: Most Common Driver Constellation Found: Scan performed on 8/12/2015, Computer: Sony VGN-NS230TE Outdated or Corrupted drivers:10/21 Updated Device/Driver Status Status Description By Scanner Motherboards Intel(R) 5000 Series Chipset Reserved Registers - 25F3 Outdated Mice And Touchpads ELECOM HID mouse Up To Date and Functioning ELECOM HID-compliant mouse Up To Date and Functioning Usb Devices Samsung SAMSUNG CDMA Technologies Corrupted By Biostar P43 A7 Samsung GT-S3350 Up To Date and Functioning Microsoft USB Composite Device Up To Date and Functioning Sound Cards And Media Devices Realtek Dispositivo High Definition Audio Up To Date and Functioning Creative Sound Blaster X-Fi Go! Pro Up To Date and Functioning Network Cards Samsung Remote NDIS based Internet Sharing Device Up To Date and Functioning Keyboards Microsoft HID Keyboard Up To Date and Functioning Hard Disk Controller Microsoft SiS PCI IDE Controller Corrupted By Biostar P43 A7 Others O2Micro Standard-CardBus-Controller Corrupted By Biostar P43 A7 ATMEL maxTouch I2C Boot Bridge Peripheral -

Workload Analysis and Acceleration Using Nvdimms and Software Brett Williams, Micron Per Brashers, Enmotus Infrastructure Now Enabled for Persistent Memory
Workload Analysis and Acceleration Using NVDIMMs and Software Brett Williams, Micron Per Brashers, Enmotus Infrastructure Now enabled for Persistent Memory Backup Triggers OS support SAVE_N Linux (native) RESET_N Windows Server 2016 (native) I2C Command Debug tools DSM, etc Memory controller support Motherboard support Controller functions Intel, Supermicro, Tyan, ASUS, Gigabyte, BAEBI spec ASRock, etc. System Support Driver support HPE, Dell, Supermicro Pmem, etc. © 2018 SNIA Persistent Memory Summit. All Rights Reserved. Applications & Workloads are Not All Equal Customer Application impact Requires lower latency / higher How much does my application performance performance improve with PM? Effort to rewrite application to enable byte NVDIMM (byte mode) provides the mode is beyond scope (time & cost) lowest latency and best performance Effort/time/expertise to rearchitect storage to add NVDIMM (block mode) NVDIMM (block mode) fits in his Unclear what/how to allocate to fast tier current storage solution © 2018 SNIA Persistent Memory Summit. All Rights Reserved. 2018 – The year of “Workload Focus” Encourages tool capabilities Evaluate workloads – executing analytics Identify Hot, Cool, Cold data categories Automatic promotion of data to match workload use model Enables “Memory/Storage” Advisory Analyze workload for possible latency/performance improvements Optimize Memory/Storage for specific workload (capacity, performance, price) Incorporate workload learning into architecture development © 2018 SNIA Persistent Memory Summit. All Rights Reserved. Workload Analysis and Acceleration Using NVDIMMs and Software Brett Williams, Micron Per Brashers, Enmotus NVDIMM Adoption Applications are not universally byte accessible aware …. yet Will take many years before standard Linux and Windows can adopt NVDIMMs across the board Not universally available to all software and application developers Capacity limits applications from taking advantage w/o rearchitecting NVDIMM’s are being deployed in specialized areas (e.g. -

Thunder N3600qe /// S4980 Version 1.0
Thunder n3600QE /// S4980 Version 1.0 Copyright Copyright © TYAN Computer Corporation, 2007. All rights reserved. No part of this manual may be reproduced or translated without prior written consent from TYAN Computer Corp. Trademark All registered and unregistered trademarks and company names contained in this manual are property of their respective owners including, but not limited to the following. TYAN, Thunder n3600QE are trademarks of TYAN Computer Corporation. AMD, Opteron, and combinations thereof are trademarks of AMD Corporation. AMI, AMIBIOS are trademarks of AMI Software Incorporated. Microsoft, Windows are trademarks of Microsoft Corporation. Nvidia and nForce are trademarks of Nvidia Corporation Microsoft, Windows are trademarks of Microsoft Corporation. SuSE,is a trademark of SuSE AG. Linux is a trademark of Linus Torvalds IBM, PC, AT, and PS/2 are trademarks of IBM Corporation. Winbond is a trademark of Winbond Electronics Corporation. Notice Information contained in this document is furnished by TYAN Computer Corporation and has been reviewed for accuracy and reliability prior to printing. TYAN assumes no liability whatsoever, and disclaims any express or implied warranty, relating to sale and/or use of TYAN products including liability or warranties relating to fitness for a particular purpose or merchantability. TYAN retains the right to make changes to product descriptions and/or specifications at any time, without notice. In no event will TYAN be held liable for any direct or indirect, incidental or consequential -

Thunder & Tempest Platforms
Thunder & Tempest Platforms HPC / Cloud Computing / Storage / Embedded Products TYAN® Business Unit USA 3288 Laurelview Court, Fremont, CA 94538 United States TEL: +1-510-651-8868 Pre-Sales: +1-510-651-8868 FAX: +1-510-440-8808 Email: [email protected] Taiwan No.200, Wen Hwa 2nd Rd., Kuei Shan Dist., Taoyuan City 33383, Taiwan TEL: +886-3-327-5988 #2873 Johnson Chang FAX: +886-3-327-6312 Email: [email protected] China No.213 Jiang Chang San Road, Zha Bei District,Shanghai (200436) Shanghai TEL: +86-021-61431188 #1361 Beijing TEL: +86-010-62381108 #2485 & #2013 Email: [email protected] Japan Yasuda Shibaura 2nd Building 3F Kaigan 3-chome 2-12, Minato-ku, Tokyo 108-0022, Japan TEL: +81-3-3769-8311 FAX: +81-3-3769-8328 Email: [email protected] EMEA Tewkesbury, Gloucestershire England TEL: +44 07540328523 Robin Daunter Email: [email protected] [email protected] World Class Server Platforms Please contact your sales representative or TYAN authorized distributors. Rev.1 Specifications are subject to change without notice. Items pictures may only be representative. Product Catalog 2018 Please visit our website for the latest product information. Industry leading hardware manufacturer, providing servers, technical workstations, and supercomputing clusters through world- wide distribution channels. About TYAN MiTAC Global Presence & TYAN Branch Offices TYAN is a world class provider of server motherboards and server platforms. MiTAC Europe Ltd. Founded in California’s Silicon Valley in 1989, TYAN has been bringing innovation MiTAC Technology UK Ltd. MiTAC Benelux N.V. and reliability to the server industry for nearly 30 years. -

CAN Line Card
Product Line Card ® CABLES DESKTOP & AIOs Lian Li Corsair InWin OWC Accell ASUS MSI Crucial iStarUSA PNY Kensington ECS Noctua Kingston LEPA Samsung LSI (Broadcom) Intel NZXT Micron Phanteks SanDisk (Western Digital) Microchip (Adaptec) Loop Phanteks Netlist Rosewill Seagate OWC MSI Raijintek PNY Seasonic Synology Rosewill Pi-Top Rosewill Solid Gear Western Digital SIIG Shuttle StarTech.com MOTHERBOARDS Sparkle Power StarTech.com ZOTAC Supermicro ASUS Thermaltake STEM/EDUCATION SYBA Thermaltake ASRock Rack DJI Tripp Lite DISPLAYS & MOUNTS Vantec ECS PROJECTORS/ Obsbot AG Neovo EVGA SCREENS pi-top CAMERAS & GIMBALS AOC GAMING CHAIRS GIGABYTE LG Adesso ASUS Akracing Intel ViewSonic STORAGE Creative Labs Elo Arozzi MSI XGIMI PLATFORMS Cougar DJI GIGABYTE Supermicro HGST (Western Digital) eMeet Huawei MSI Tyan ROBOTICS Thermaltake Enabot LG Electronics Obsbot STORAGE SYSTEMS FLIR MSI NETWORKING Richtech HARD DRIVES D-Link Hasselblad Phillips ASUS Fujitsu ADATA Insta360 SIIG Broadcom (formerly LSI) G-Technology HGST (Western Digital) SCANNERS Kandao StarTech.com D-Link Adesso HGST (Western Digital) Seagate Logitech Tripp Lite Edgecore Kodak Huawei Synology OBSBOT ViewSonic Edimax OWC Vizta Toshiba PGYTECH EnGenius SECURITY & QNAP Western Digital Finisar Vantec SURVEILLANCE ViewSonic DISPLAYS/ LARGE Hiro ACTi USB DRIVES, YI-Technology HEADPHONES & Huawei FORMAT D-Link ACCESSORIES & AG Neovo SPEAKERS Intel Enabot ADAPTERS CASES Huawei 1MORE Kensington EnGenius ADATA Antec LG Adesso Mellanox EZVIZ Kingston Apex Optoma ASUS Microchip Hikvision -

Intel-Based Platforms
Intel-Based Platforms ● Cloud Platforms ● HPC / GPU Platforms ● Embedded & SMB Platforms MITAC INTERNATIONAL CORP. TYAN® Business Unit USA 3288 Laurelview Court, Fremont, CA 94538 United States Tel: +1-510-651-8868 Pre-Sales: +1-510-651-8868 x5120 Fax: +1-510-651-7688 Email:[email protected] Taiwan 5F, Building B, No. 209, Sec. 1, Nan Gang Rd., Nan Gang Dist., Taipei 11568, Taiwan Tel:+886-2-2652-5888 Fax:+886-2-2652-5805 Email:[email protected] Japan Yasuda 8th Building 6F Kaigan 3-chome 3-8, Minato-ku , Tokyo, 108-0022 , Japan Tel:+81-3-3769-8311 Fax:+81-3-3769-8328 Email: [email protected] Europe Z5 Mollem 318 1730 Asse (Mollem) Belgium Sales: +32 2456 1721 Sales Email: [email protected] Technical Support: +32 2456 1722 RMA Group [email protected] China No.213,Jiang Chang San Road, Zha Bei District,Shanghai,China Zip code:200436 Beijing Tel:+86-010-62381108#2043 Shanghai Tel: +86-021-61431194 Email:[email protected] Rev.1 Product Catalog 2011 Specifications are subject to change without notice. Items pictured may only be representative. To be the leader in providing servers, techni- cal workstations and supercomputer clusters through worldwide channels. Your First Choice About TYAN MiTAC Global Presence & TYAN Branch Offices Created in 1989, TYAN designs, manufactures and markets advanced x86 server/workstation platforms. TYAN’s products are sold to OEMs, MiTAC UK Ltd. VARs, System Integrators, and Resellers around the world for a wide Mio Technology UK Ltd. range of applications. As a leading server brand asset owned by MiTAMio Technology Benelux N.V. -

1- in the United States District Court for the District Of
Case 1:16-cv-11252 Document 1 Filed 06/24/16 Page 1 of 39 IN THE UNITED STATES DISTRICT COURT FOR THE DISTRICT OF MASSACHUSETTS PRESIDENT AND FELLOWS OF ) HARVARD COLLEGE ) COMPLAINT ) Plaintiff, ) ) Civil Action No. ___________ v. ) ) GLOBALFOUNDRIES U.S., INC. ) ) JURY TRIAL DEMANDED Defendant. ) ) Defendant. ) ) ) COMPLAINT Plaintiff, President and Fellows of Harvard College (“Harvard”), by and through its counsel, Pepper Hamilton LLP, for its Complaint against Defendant GlobalFoundries U.S., Inc. (“GlobalFoundries”), alleges as follows: THE PARTIES 1. Plaintiff Harvard is an educational institution and charitable corporation organized under the laws of the Commonwealth of Massachusetts with its principal place of business at Massachusetts Hall, Cambridge, MA 02138. 2. Upon information and belief, Defendant GlobalFoundries is a Delaware corporation with its principal place of business at 2600 Great America Way, Santa Clara, CA 95054. JURISDICTION AND VENUE 3. This is an action for patent infringement arising under the Patent Laws of the United States, 35 U.S.C. § 1 et. seq. This Court has jurisdiction over the subject matter of this action pursuant to 28 U.S.C. §§ 1331 and 1338(a). -1- Case 1:16-cv-11252 Document 1 Filed 06/24/16 Page 2 of 39 4. This Court has personal jurisdiction over GlobalFoundries based, at least, upon GlobalFoundries’ contacts with the forum and the nature of the infringing activity alleged herein. Upon information and belief, GlobalFoundries regularly does or solicits business, engages in other persistent courses of conduct, and/or derives substantial revenue from products and/or services provided to individuals in the Commonwealth of Massachusetts.