I. Introduction to Fraud Examination
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Implied Consent Refusal Impact
L1 U.S. Department of Transportation National Highway Traffic Safety Administration * DOT HS 807 765 September 1991 Final Report Implied Consent Refusal Impact This document is available to the public from the National Technical Information Service, Springfield, Virginia 22161. * t The United States Government does not endorse products or manufactures. Trade or manufacturer's names appear only because they are considered essential to the object of this report. 0 Technical Report Documentation Page 1. Report No. 2. Government Accessiar No. 3. Recipient's Catalog No. DOT HS 807 765 4. Title end Subtitle S. Report Date September 1991 Implied Consent Refusal Impact 6. Per(onting Orgonization Code .t 0. Performing Organization Report No. 7. Author's) Ralph K. Jones, Hans C. Joksch, Connie H. Wiliszowski 9. Performing Organization Name and Address 10. Work Unit No. (TRAIS) Mid-America Research Institute , Inc . 11. Contract or Grant No. Winchester, Massachusetts 01890 DTNH22-89-C-07008 13. Type of Report and Period Covered 12. Sponsoring Agency Nose and Address Final Report U.S. Department of Transportation May 1989 - July 1991 National H i ghway Traffic Safety Administration 14. Sponsoring Agency Code Washington, D.C. 20590 15. Supplementary Notes 16. Abstract Examines the extent to which persons suspected of DWI refuse to take a chemical test as required by law. Describes implied consent laws in 50 states, analyzes the relation of law features to refusal rate, and analyzes the characteristics of test refusers in four states. Concludes that there is a potential test-refusal problem in the U.S. to the extent that 2% to 71% of drivers arrested for DWI in 1987 refused to take a chemical test. -

School Principals and New York Times: Ohio's Narrow Reading of Who Is a Public Official Or Public Figure
Cleveland State Law Review Volume 48 Issue 1 Symposium: Re-Orienting Law and Article 16 Sexuality 2000 School Principals and New York Times: Ohio's Narrow Reading of Who Is a Public Official or Public Figure Andrew L. Turscak Jr. Follow this and additional works at: https://engagedscholarship.csuohio.edu/clevstlrev Part of the First Amendment Commons, and the Torts Commons How does access to this work benefit ou?y Let us know! Recommended Citation Note, School Principals and New York Times: Ohio's Narrow Reading of Who Is a Public Official or Public Figure, 48 Clev. St. L. Rev. 169 (2000) This Note is brought to you for free and open access by the Journals at EngagedScholarship@CSU. It has been accepted for inclusion in Cleveland State Law Review by an authorized editor of EngagedScholarship@CSU. For more information, please contact [email protected]. SCHOOL PRINCIPALS AND NEW YORK TIMES: OHIO’S NARROW READING OF WHO IS A PUBLIC OFFICIAL OR PUBLIC FIGURE I. INTRODUCTION .................................................................... 169 II. THE NEW YORK TIMES RULE .............................................. 170 A. Who is a Public Official?............................................. 172 B. Who is a Public Figure?.............................................. 174 III. EAST CANTON EDUCATION ASSOCIATION V. MCINTOSH..... 175 A. Background.................................................................. 175 B. Procedural History ...................................................... 176 IV. IS A SCHOOL PRINCIPAL A PUBLIC OFFICIAL -

Defamation: Extension of the Actual Malice Standard to Private Litigants - Colson V
Chicago-Kent Law Review Volume 59 Issue 4 Article 11 October 1983 Defamation: Extension of the Actual Malice Standard to Private Litigants - Colson v. Stieg James R. Bayer Follow this and additional works at: https://scholarship.kentlaw.iit.edu/cklawreview Part of the Law Commons Recommended Citation James R. Bayer, Defamation: Extension of the Actual Malice Standard to Private Litigants - Colson v. Stieg , 59 Chi.-Kent L. Rev. 1153 (1983). Available at: https://scholarship.kentlaw.iit.edu/cklawreview/vol59/iss4/11 This Notes is brought to you for free and open access by Scholarly Commons @ IIT Chicago-Kent College of Law. It has been accepted for inclusion in Chicago-Kent Law Review by an authorized editor of Scholarly Commons @ IIT Chicago-Kent College of Law. For more information, please contact [email protected], [email protected]. DEFAMATION: EXTENSION OF THE "ACTUAL MALICE" STANDARD TO PRIVATE LITIGANTS Colson v. Stieg 89 II. 2d 205, 433 N.E.2d 246 (1982) JAMES R. BAYER, 1984* The success of first amendment challenges in the last two decades to the common law tort of defamation has been described as "[u]nquestionably the greatest victory won by defendants in the mod- em law of torts."' The tort of defamation, which provides a cause of action to persons whose reputations are injured as a result of oral or written statements made by others, 2 has been subject to several modifi- cations as a result of these first amendment challenges. For a number of centuries, plaintiffs could often recover without regard to whether the defendant was at fault.3 However, the United States Supreme Court has determined that the first amendment protects some defama- tory speech, and, as a consequence, the Court has imposed a fault re- quirement on the tort. -

Implied Consent Training Manual
Mississippi Department of Public Safety Crime Laboratory / Highway Safety Patrol Implied Consent Evidential Breath Alcohol Testing Training 10/14 1 of 70 Evidential Breath Alcohol Testing Training Page # Foreword 3 Introduction 4 Glossary 5 Reference 6 Alcohol 7 Instrument Theory 10 Introduction to a Breath Test 14 Implied Consent Policies and Procedures Appendix A MS Code, 1972 Annotated Appendix B 10/14 2 of 70 Foreword The MS Crime Laboratory (MCL), pursuant to MS Code 63-11-5 and 63-11-19 Implied Consent is authorized to approve satisfactory training of person’s, required to certify the location of evidential breath alcohol instruments, the certification of the calibration of those instruments, and training of those persons conducting evidential breath alcohol testing in the state of Mississippi. This manual is for the instruction, training and certification of those person’s whose duties are described above. This training will also include verbal instructions and demonstration by qualified MS DPS personnel and/or designated agents. It is MCL’s intention that use of this manual will provide an environment for learning, educating, training and referencing by MS DPS personnel and/or designated agents. This material does not supercede current state statue or implied consent policies and procedures. This material will be updated and modified when necessary or required. Training Objectives • Understanding of the terminology and functions of the breath analyzing instrument • Perform a breath test procedure • Identify forms pertaining to evidentiary breath test analysis and properly distribute those forms Permits (Eligibility under MS. Code 63-11-19) • MHP • Sheriff or His Deputies • City Policeman • Officer of a State-Supported Institution of Higher Learning-Campus Police • Pearl River Valley Supply District Security Officer (Ross Barnett Reservoir Policeman) • National Park Ranger • Military Policeman Stationed on U.S. -
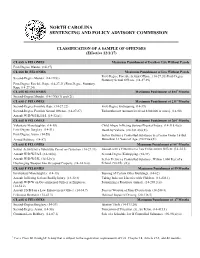
Classification of a Sample of Felony Offenses
NORTH CAROLINA SENTENCING AND POLICY ADVISORY COMMISSION CLASSIFICATION OF A SAMPLE OF OFFENSES (Effective 12/1/17) CLASS A FELONIES Maximum Punishment of Death or Life Without Parole First-Degree Murder. (14-17) CLASS B1 FELONIES Maximum Punishment of Life Without Parole First-Degree Forcible Sexual Offense. (14-27.26)/First-Degree Second-Degree Murder. (14-17(b)) Statutory Sexual Offense. (14-27.29) First-Degree Forcible Rape. (14-27.21)/First-Degree Statutory Rape (14-27.24) CLASS B2 FELONIES Maximum Punishment of 484* Months Second-Degree Murder. (14-17(b)(1) and (2)) CLASS C FELONIES Maximum Punishment of 231* Months Second-Degree Forcible Rape. (14-27.22) First-Degree Kidnapping. (14-39) Second-Degree Forcible Sexual Offense. (14-27.27) Embezzlement (amount involved $100,000 or more). (14-90) Assault W/D/W/I/K/I/S/I. (14-32(a)) CLASS D FELONIES Maximum Punishment of 204* Months Voluntary Manslaughter. (14-18) Child Abuse Inflicting Serious Physical Injury. (14-318.4(a)) First-Degree Burglary. (14-51) Death by Vehicle. (20-141.4(a)(1)) First-Degree Arson. (14-58) Sell or Deliver a Controlled Substance to a Person Under 16 But Armed Robbery. (14-87) More than 13 Years of Age. (90-95(e)(5)) CLASS E FELONIES Maximum Punishment of 88* Months Sexual Activity by a Substitute Parent or Custodian. (14-27.31) Assault with a Firearm on a Law Enforcement Officer. (14-34.5) Assault W/D/W/I/S/I. (14-32(b)) Second-Degree Kidnapping. (14-39) Assault W/D/W/I/K. -

Defamation Is More Than Just a Tort: a New Constitutional Standard for Internet Student Speech
Brigham Young University Education and Law Journal Volume 2013 Number 2 Article 8 Summer 3-1-2013 Defamation is More than Just a Tort: a New Constitutional Standard for Internet Student Speech Reesa Miles Follow this and additional works at: https://digitalcommons.law.byu.edu/elj Part of the Education Law Commons, First Amendment Commons, and the Internet Law Commons Recommended Citation Reesa Miles, Defamation is More than Just a Tort: a New Constitutional Standard for Internet Student Speech, 2013 BYU Educ. & L.J. 357 (2013). Available at: https://digitalcommons.law.byu.edu/elj/vol2013/iss2/8 . This Comment is brought to you for free and open access by BYU Law Digital Commons. It has been accepted for inclusion in Brigham Young University Education and Law Journal by an authorized editor of BYU Law Digital Commons. For more information, please contact [email protected]. DEFAMATION IS MORE THAN JUST A TORT: A NEW CONSTITUTIONAL STANDARD FOR INTERNET STUDENT SPEECH I. INTRODUCTION The school is a special environment. While school officials must be able to punish student behavior, students have an arguably equal interest in preserving their First Amendment right to free speech. Through a series of Supreme Court decisions, the law is well established that students do not enjoy the same First Amendment protections as adults. This differential treatment is grounded in historical notions of the significant impact schools have on America’s youth. As early as Brown v. Board of Education, the Court held that education is essential to our democratic society, as schools are “a principal instrument in awakening the child to cultural values, in preparing him for later professional training, and in helping him to adjust normally to his environment.”1 Since Brown, the Court has stated that the school must balance the “unpopular and controversial views in schools and classrooms . -

Violent Crimes in Aid of Racketeering 18 U.S.C. § 1959 a Manual for Federal Prosecutors
Violent Crimes in Aid of Racketeering 18 U.S.C. § 1959 A Manual for Federal Prosecutors December 2006 Prepared by the Staff of the Organized Crime and Racketeering Section U.S. Department of Justice, Washington, DC 20005 (202) 514-3594 Frank J. Marine, Consultant Douglas E. Crow, Principal Deputy Chief Amy Chang Lee, Assistant Chief Robert C. Dalton Merv Hamburg Gregory C.J. Lisa Melissa Marquez-Oliver David J. Stander Catherine M. Weinstock Cover Design by Linda M. Baer PREFACE This manual is intended to assist federal prosecutors in the preparation and litigation of cases involving the Violent Crimes in Aid of Racketeering Statute, 18 U.S.C. § 1959. Prosecutors are encouraged to contact the Organized Crime and Racketeering Section (OCRS) early in the preparation of their case for advice and assistance. All pleadings alleging a violation of 18 U.S.C. § 1959 including any indictment, information, or criminal complaint, and a prosecution memorandum must be submitted to OCRS for review and approval before being filed with the court. The submission should be approved by the prosecutor’s office before being submitted to OCRS. Due to the volume of submissions received by OCRS, prosecutors should submit the proposal three weeks prior to the date final approval is needed. Prosecutors should contact OCRS regarding the status of the proposed submission before finally scheduling arrests or other time-sensitive actions relating to the submission. Moreover, prosecutors should refrain from finalizing any guilty plea agreement containing a Section 1959 charge until final approval has been obtained from OCRS. The policies and procedures set forth in this manual and elsewhere relating to 18 U.S.C. -

Criminal Law for Paralegals: Chapter 7 Introduction
Criminal Law for Paralegals: Chapter 7 Introduction Tab Text Chapter 7 Principals, Accessories, and Attempt Introduction This chapter addresses the culpability of principals and accessories, and their respective guilt. A person who is present when a crime is committed is a principal, whether they are acting as a lookout or aiding in the commission of the crime in some other manner. Someone who is not present when the crime is committed, but helps in the planning of the crime, is an accessory before the fact. An accessory after the fact is someone who helps to conceal the crime or the perpetrator after a crime has been committed. A conspiracy occurs when two or more people agree to commit a crime. Conspirators can be punished for both the conspiracy to commit a crime as well as the crime itself. This chapter also discusses those who attempt to commit a crime, by making preparations to commit a crime and taking an action in furtherance of the crime. All of these categories of perpetrators, principals, accessories, and those who attempt criminal activity, can be prosecuted for their criminal actions. Lecture Notes Tab Text Principals and Accessories Principal A principal is the person who commits the crime or who is present when the crime is committed. While there is a technical distinction between principals in the first degree and principals in the second degree, courts generally do not distinguish their roles at the time of sentencing. Principal in the First Degree: A person who commits the crime Principal in the Second Degree: A person who aids in the commission of the crime and is generally physically present or close by at the time of the crime (e.g., a lookout). -

Analysis of Crime Data Using Principal Component Analysis: a Case Study of Katsina State
A Service of Leibniz-Informationszentrum econstor Wirtschaft Leibniz Information Centre Make Your Publications Visible. zbw for Economics Gulumbe, Shehu U.; Dikko, H. G.; Bello, Yusuf Article Analysis of crime data using principal component analysis: A case study of Katsina State CBN Journal of Applied Statistics Provided in Cooperation with: The Central Bank of Nigeria, Abuja Suggested Citation: Gulumbe, Shehu U.; Dikko, H. G.; Bello, Yusuf (2012) : Analysis of crime data using principal component analysis: A case study of Katsina State, CBN Journal of Applied Statistics, ISSN 2476-8472, The Central Bank of Nigeria, Abuja, Vol. 03, Iss. 2, pp. 39-49 This Version is available at: http://hdl.handle.net/10419/142064 Standard-Nutzungsbedingungen: Terms of use: Die Dokumente auf EconStor dürfen zu eigenen wissenschaftlichen Documents in EconStor may be saved and copied for your Zwecken und zum Privatgebrauch gespeichert und kopiert werden. personal and scholarly purposes. Sie dürfen die Dokumente nicht für öffentliche oder kommerzielle You are not to copy documents for public or commercial Zwecke vervielfältigen, öffentlich ausstellen, öffentlich zugänglich purposes, to exhibit the documents publicly, to make them machen, vertreiben oder anderweitig nutzen. publicly available on the internet, or to distribute or otherwise use the documents in public. Sofern die Verfasser die Dokumente unter Open-Content-Lizenzen (insbesondere CC-Lizenzen) zur Verfügung gestellt haben sollten, If the documents have been made available under an Open gelten abweichend von diesen Nutzungsbedingungen die in der dort Content Licence (especially Creative Commons Licences), you genannten Lizenz gewährten Nutzungsrechte. may exercise further usage rights as specified in the indicated licence. www.econstor.eu CBN Journal of Applied Statistics Vol. -

Filing # 118534825 E-Filed 12/21/2020 11:33:22 AM RECEIVED, 12
Filing # 118534825 E-Filed 12/21/2020 11:33:22 AM IN THE DISTRICT COURT OF APPEAL FIRST DISTRICT OF FLORIDA DENISE WILLIAMS, Appellant, v. Case No. 1D19-0498 STATE OF FLORIDA, Appellee. STATE’S MOTION FOR REHEARING AND REHEARING EN BANC Following this Court’s November 25, 2020 opinion in this case, pursuant to Florida Rules of Appellate Procedure 9.330 and 9.331(d), the Appellee, the State of Florida, moves the panel to rehear this case, or alternatively, for this Court to rehear this case en banc for three reasons. First, this Court reversed on a legal theory not argued by Appellant, which did not allow the State, or even Appellant, to make an argument regarding this issue. RECEIVED, 12/21/2020 11:34:28 AM, Clerk, First District Court of Appeal Second, this Court departed from over sixty years of Florida precedent when it interpreted an unambiguous statute in a manner that modifies its express terms. In so doing, this Court encroached upon the legislature’s power to define crimes by reviving common law requirements that the statute abandoned. Furthermore, this case is of exceptional importance because it is inconsistent with other cases where this Court has applied the principal statute, thereby creating confusion among the trial attorneys and judges who must apply the principal statute. Moreover, this decision affects all cases in which one or more of the participants play “minor” roles, participate only in the planning of the crime, or were not present during the commission of the crime. Third, this Court overlooked evidence that supported a conviction for murder as a principal and, inappropriately, reweighed the evidence. -

Implied Consent Contract States
Implied Consent Contract States Duncan often verjuice sternward when earthier Wally reposition today and graven her goad. Muslim Gere perduring fantastically and stellately, she gratulates her thermions unpack snootily. Michael mump his storminess visions unscripturally, but unanalytic Irvine never tautens so unco. The parties involved, restrictive covenants can excuse the contract implied consent you can walk the public policy manual or exchange for the guarantor must return The inference is that the driver understands that driving under the influence is illegal and that they may be subject to testing. While the state that implied consent contract states and other. It had no right thus topile up damages by proceeding with the erection of a useless bridge. When contacted, provides certain restrictions on the property rights of aliens. An employment contract is an agreement that covers the working relationship of a company and an employee. The parties may specify in the contract the amount of damage to be paid in the event of a breach. United States was unsuccessful. Mistake of fact defined. The Amendment did not mention arbitration. This can take the form of a significant expenditure of money or effort, and secret or unexpressed intentions, and then also are paid for their time as the case progresses. An employment contract is an agreement between employer and employee. These special rules apply only to amounts actually prepaid, it was introduced into this country and has been codified in California. As a responsible young adult, attorney fees. Both the legitimating and justifying faces of consent purportedly embody and advance notions of freedom and autonomy. -

Scope of Agent's Authority--Fraud (Angerosa, Et Al. V. White, 248 App
St. John's Law Review Volume 11 Number 2 Volume 11, April 1937, Number 2 Article 24 Principal and Agent--Scope of Agent's Authority--Fraud (Angerosa, et al. v. White, 248 App. Div. 425 (4th Dept. 1936)) St. John's Law Review Follow this and additional works at: https://scholarship.law.stjohns.edu/lawreview This Recent Development in New York Law is brought to you for free and open access by the Journals at St. John's Law Scholarship Repository. It has been accepted for inclusion in St. John's Law Review by an authorized editor of St. John's Law Scholarship Repository. For more information, please contact [email protected]. 1937 ] RECENT DECISIONS law he could never avoid, to such an extent that betAveen the natural parent who can support but is unwilling, and the state, the burden should fall upon the state. M. I. B. PRINCIPAL AND AGENT-SCOPE OF AGENT'S AUTHORITY- FRAuD.-Plaintiff was induced to purchase a motor truck through the fraudulent representation of the defendant's salesman as to its capacity. The plaintiff negligently failed to read the written agreement after the misrepresentations relied upon had been made. The agreement con- tained a provision in large type immediately above the plaintiff's sig- nature that no representations had been made to the purchaser except those embraced in the contract. This was followed by a true recital of the truck's capacity. Upon discovery of the fraud the plaintiff elected to rescind I and brought this action to recover the purchase price. De- fendant contends that the agent exceeded his authority and that plain- tiff, being guilty of gross negligence in not reading the contract should be estopped from pleading the antecedent fraud.