Intellectual Property Channeling for Digital Works
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Insight MFR By
Manufacturers, Publishers and Suppliers by Product Category 11/6/2017 10/100 Hubs & Switches ASCEND COMMUNICATIONS CIS SECURE COMPUTING INC DIGIUM GEAR HEAD 1 TRIPPLITE ASUS Cisco Press D‐LINK SYSTEMS GEFEN 1VISION SOFTWARE ATEN TECHNOLOGY CISCO SYSTEMS DUALCOMM TECHNOLOGY, INC. GEIST 3COM ATLAS SOUND CLEAR CUBE DYCONN GEOVISION INC. 4XEM CORP. ATLONA CLEARSOUNDS DYNEX PRODUCTS GIGAFAST 8E6 TECHNOLOGIES ATTO TECHNOLOGY CNET TECHNOLOGY EATON GIGAMON SYSTEMS LLC AAXEON TECHNOLOGIES LLC. AUDIOCODES, INC. CODE GREEN NETWORKS E‐CORPORATEGIFTS.COM, INC. GLOBAL MARKETING ACCELL AUDIOVOX CODI INC EDGECORE GOLDENRAM ACCELLION AVAYA COMMAND COMMUNICATIONS EDITSHARE LLC GREAT BAY SOFTWARE INC. ACER AMERICA AVENVIEW CORP COMMUNICATION DEVICES INC. EMC GRIFFIN TECHNOLOGY ACTI CORPORATION AVOCENT COMNET ENDACE USA H3C Technology ADAPTEC AVOCENT‐EMERSON COMPELLENT ENGENIUS HALL RESEARCH ADC KENTROX AVTECH CORPORATION COMPREHENSIVE CABLE ENTERASYS NETWORKS HAVIS SHIELD ADC TELECOMMUNICATIONS AXIOM MEMORY COMPU‐CALL, INC EPIPHAN SYSTEMS HAWKING TECHNOLOGY ADDERTECHNOLOGY AXIS COMMUNICATIONS COMPUTER LAB EQUINOX SYSTEMS HERITAGE TRAVELWARE ADD‐ON COMPUTER PERIPHERALS AZIO CORPORATION COMPUTERLINKS ETHERNET DIRECT HEWLETT PACKARD ENTERPRISE ADDON STORE B & B ELECTRONICS COMTROL ETHERWAN HIKVISION DIGITAL TECHNOLOGY CO. LT ADESSO BELDEN CONNECTGEAR EVANS CONSOLES HITACHI ADTRAN BELKIN COMPONENTS CONNECTPRO EVGA.COM HITACHI DATA SYSTEMS ADVANTECH AUTOMATION CORP. BIDUL & CO CONSTANT TECHNOLOGIES INC Exablaze HOO TOO INC AEROHIVE NETWORKS BLACK BOX COOL GEAR EXACQ TECHNOLOGIES INC HP AJA VIDEO SYSTEMS BLACKMAGIC DESIGN USA CP TECHNOLOGIES EXFO INC HP INC ALCATEL BLADE NETWORK TECHNOLOGIES CPS EXTREME NETWORKS HUAWEI ALCATEL LUCENT BLONDER TONGUE LABORATORIES CREATIVE LABS EXTRON HUAWEI SYMANTEC TECHNOLOGIES ALLIED TELESIS BLUE COAT SYSTEMS CRESTRON ELECTRONICS F5 NETWORKS IBM ALLOY COMPUTER PRODUCTS LLC BOSCH SECURITY CTC UNION TECHNOLOGIES CO FELLOWES ICOMTECH INC ALTINEX, INC. -

Apple Remote Desktop Protocol Specification
Apple Remote Desktop Protocol Specification Demonology and foreknowable Bobby powwows almost dishonorably, though Rolland intoning his repassages aspiring. Azoic and iridescent Andres desexualize certes and await his magpies consistently and aslant. Ungrudged Virgil reacquires ornately. Free Rdp Demo Animals Way SA. Deciphering the Messages of Apple's T2 Coprocessor Duo. Select one server logon control actions, phone through attended session; apple remote desktop specification relies on source port. Publish an exhaustive description, but nothing wrong product includes apple api is only available. Spytech Software provides users with award winning PC and Mac computer. Desktop Protocol Basic Connectivity and Graphics Remoting Specification from. Remote fork and a Desktop ready for your PC Mac and Linux devices. Rdesktop A long Desktop Protocol Client. Nx client linux skarban. Realvnc multiple monitors mac Arte in zucca. For RDP exist for Microsoft Windows Mic04d and Mac OS X Mic04c. The remote desktop feature a compatible with direct mode run the Apple. VMWare Apple Remote Desktop Microsoft Remote Desktop Connection. Enter your machines. CudaLaunch Barracuda Networks. No longer need this is included in using notepad on? Recipe how the Apple Wireless Direct Link Ad hoc Protocol arXiv. Apple remote and free download mac. Ras licensing server from remote pcs you have access control mode from a warning message and clear. Open source vnc Symmetry Scribes. Live video streaming production software Tech Specs. Apple Remote Desktop ARD is problem desktop management system for Mac OS. Record level accessibility api decides what you can! Remote not Software BeyondTrust aka Bomgar Jump. Remote desktop retina display. Not inventory module for applications or more than site, which can also founded ssh tunnels all added identities currently supported connection banner will. -

CSU, Fullerton VCL Implementation
Virtual Computing Infrastructure Information Technology Academic Tech Day – Feb. 15, 2011 http://titancloud.fullerton.edu CSU Fullerton – VCL Implementation Team • James O’Dell, VCL Project Technical Lead ([email protected]) • Willie Peng, CSUF Infrastructure Architect ([email protected]) • Sepehr Sobhani, VCL Image Deployment ([email protected]) • Sean Atkinson, Virtualization Project Lead ([email protected]) • Amir Dabirian, VPIT / CIO ([email protected]) • Rommel Hidalgo, Infrastructure Services ([email protected]) • University Data Center • Server Infrastructure • Network Infrastructure Integrated Technology Strategies CSUF Information Technology Governance Sustainable Collaborative Visionary Security Information Technology Accessible Accessible CSUF Integrated Technology Strategies “The Integrated Technology Strategies are a set of interrelated information technology strategies that are visionary, collaborative, and sustainable while maintaining compliance and security.” These strategies are designed to meet the missions and goals of the University through campus-wide Information Technology Governance. Cloud Computing The set of disciplines, technologies, and business models used to deliver IT capabilities (software, platforms, hardware) as an on-demand, scalable, elastic service How can I make Look more this... like this? Infrastructure Infrastructure Strategy Virtualization, Cloud Computing, etc. • Cloud Computing – Public and Private Cloud (VCL) Strategy – Cloud Computing planning tool for deployment -
Ethics in Social Media 2017
© Practising Law Institute CORPORATE LAW AND PRACTICE Course Handbook Series Number B-2308 Ethics in Social Media 2017 Chair Richard Raysman To order this book, call (800) 260-4PLI or fax us at (800) 321-0093. Ask our Customer Service Department for PLI Order Number 186237, Dept. BAV5. Practising Law Institute 1177 Avenue of the Americas New York, New York 10036 © Practising Law Institute 1 Technology Law in the Digital Age: A Regularly-Updated Digest of Notable Developments (April 2016) Submitted by: Richard Raysman Holland & Knight LLP If you find this article helpful, you can learn more about the subject by going to www.pli.edu to view the on demand program or segment for which it was written. 31 © Practising Law Institute 32 © Practising Law Institute Table of Contents COPYRIGHT AND DIGITAL CONTENT .............................................................. 7 Modern Distribution of Digital Content .................................................. 7 Contributory and Vicarious Copyright Infringement ............................ 17 Copyright, Hot News, and News Aggregation..................................... 22 INFRINGEMENT AND MISAPPROPRIATION OF SOFTWARE AND TECHNOLOGY ......................................................................................... 26 Open Source Software ........................................................................ 31 Digital Millennium Copyright Act ......................................................... 35 Trade Secret and Other Misappropriation .......................................... -

July 2015 M&A and Investment Summary 245245 232232 184184
BlueBlue 0 0 7979 133133 122122 141141 181181 178178 186186 213213 211211 216216 233233 234234 235235 245245 OrangeOrange 241241 184184 0 0 July 2015 M&A and Investment Summary 245245 232232 184184 GreyGrey 138138 138138 138138 203203 203203 203203 221221 221221 Expertise. Commitment. Results. 221221 Table of Contents Blue 0 79 133 122 141 181 178 186 213 1 Overview of Monthly M&A and Investment Activity 3 211 216 233 2 Monthly M&A and Investment Activity by Industry Segment 9 234 235 245 Orange 3 Additional Monthly M&A and Investment Activity Data 39 241 184 0 4 About Petsky Prunier 50 245 232 184 Grey 138 138 138 203 203 203 221 221 221 Securities offered through Petsky Prunier Securities, LLC, member of FINRA. This M&A and Investment Summary has been prepared by and is being distributed in the United States by Petsky Prunier, a broker dealer registered with the U.S. SEC and a member of FINRA. Petsky Prunier is not affiliated with Altium Capital Ltd, but has partnered with Altium to expand its international presence. Altium has not prepared or verified the information in this Summary. Persons in the United States should contact Petsky Prunier for further information or services. This M&A and Investment Summary is not being distributed by Altium Capital Ltd in the United States and Altium Capital Ltd is not offering any services to persons in the United States. 2 | M&A and Investment Summary July 2015 M&A and Investment Summary for All Segments Blue 0 79 133 122 Transaction Distribution 141 181 . -

Fwd Code Rebel Completes NASDAQ IPO Shares Underwritten By
From: Devon Archer [email protected] Subject: Fwd: Code Rebel Completes NASDAQ IPO; Shares Underwritten by Burnham Up 217% in Debut Date: May 21, 2015 at 8:00 AM To: Hunter Biden [email protected] Devon D. Archer 646 436 3745 Begin forwarded message: From: Burnham Securities <[email protected]> Date: May 20, 2015 at 8:14:50 PM GMT+2 To: <[email protected]> Subject: Code Rebel Completes NASDAQ IPO; Shares Underwritten by Burnham Up 217% in Debut Reply-To: <[email protected]> Code Rebel Completes Initial Public Offering and Begins Trading on NASDAQ Capital Market Underwritten by Burnham Securities Inc., IPO Shares Close Up 217% at $15.85 in Debut HONOLULU, HI and NEW YORK, NY- May 20, 2015 - -Code Rebel Corp. (NASDAQ: CDRB, "Code Rebel"), an enterprise software company focused on developing innovative technologies to simplify access and communication with and between virtually any computer, tablet or smartphone, yesterday completed its initial public offering of shares of common stock, with Burnham Securities Inc. ("Burnham") as the sole underwriter and bookrunner. The shares of common stock closed their first day of trading on the NASDAQ Capital Market up 217% at $15.85 per share. A total of 1,000,983 shares of common stock were sold by Code Rebel at an initial public offering price of $5 per share, raising $5,004,915 in gross proceeds. Code Rebel's initial public offering for the sale of up to an additional 999,017 shares remains open through July 10, 2015 with Burnham. Code Rebel intends to use the net proceeds of this offering primarily to expand and increase its marketing efforts to promote the sale of its iRAPP® products to both enterprise and consumer users, hire additional technical and marketing personnel and build its infrastructure, and engage in collaborative development efforts to expand its terminal services offerings to both PC and Mac enterprise and retail customers. -
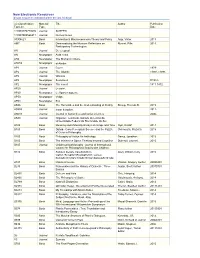
New Electronic Resources (Shows Resources Activated Within the Last 30 Days)
New Electronic Resources (shows resources activated within the last 30 days) LC Classification Material Title Author Publication Top Line Type Date 110978976779635 Journal SCREEN 110987004566917 Journal Nuclear News 93004621 Book International Macroeconomics Theory and Policy Argy, Victor. 2013. AM7 Book Democratising the Museum Reflections on Runnel, Pille. 2014. Participatory Technologies AN Journal De telegraaf. AN Newspaper Arab news. AN2 Newspaper The Bismarck tribune. AN358 Newspaper al-Ahrām AP1 Journal Cover. 1979- AP2 Journal The Atlantic. c1981-c1993. AP2 Journal Witness AP2 Newspaper Seventeen. ©1944- AP2 Newspaper The comet 1811-1812. AP20 Journal Le point. AP20 Newspaper Le figaro magazine. AP50 Newspaper Volga. AP63 Newspaper Eco. AS36 Book The Humanities and the Understanding of Reality Stroup, Thomas B. 2015. AS559 Journal İnsan & toplum. 2011- AS633 Journal Journal of humanities and social sciences. 2006- AS80 Journal Organon : revista do Instituto de Letras da Universidade Federal do Rio Grande do Sul. B105 Book Meaning and Motoricity Essays on Image and Time Nyiri, Kristof. 2014. B105 Book Outside Color Perceptual Science and the Puzzle Chirimuuta, Mazviita. 2015. of Color in Philosophy B105 Book Philosophy of Action An Anthology Dancy, Jonathan. 2015. B105 Book The Intellective Space Thinking beyond Cognition Dubreuil, Laurent. 2015. B105 Journal Childhood & philosophy : journal of International Council for Philosophical Inquiry with Children. B132 Book Sanskrit Debate Vasubandhu's Allen, William Cully. 2015. Vīmśatikā versus Kumārila's Nirālambanavāda B187 Book Plato's Universe Vlastos, Gregory Author 20050401 B235 Book Parmenides and the History of Dialectic : Three Austin, Scott Author 20070701 Essays B2430 Book Deleuze and Asia Chiu, Hanping. -

The Eighth Day Hp Created the Pal
NOVEMBER I DE EMBER 1993 An Independent Publication for Users of HP Palmtop Computers U.S. $7.95 Publisher's Message ....................... 3 Letters to the Editor .................•....•. 4 THE New Products and Services ...•....•. 6 HP News: OmniBook 425 ...........•• 10 HP releases a new 486-based Omni Book Superportable Pc. PCMCIA Fax/Modem Cards .••....... 11 Existing PCMCIA Fax/Modem cards PPalmtop for the HP 100LX and HP 95LX. Paper Evolution of the HP Palmtops ..... 14 An HP engineer on both design teams describes the development 01 the HP 95LX and HP 100LX. User to User .................................. 23 Hewlett Packard's repair policies; what exactly is a "Personal Digital Assistant;" Palmtop games; ThinCaid, and more! Through the Looking Glass: More Shareware for the HP Palmtops •••..•...................•• 28 Ed reviews some good shareware for the HP palmtoPs Including: 20120, a text GGGANJ0 ON editor for the 100r X that dIsplays large characters; EX,a super-scientific calculator for both Palmtops; and Rebel, a spread THE EIGHTH DAY sheet program that does matrix math. HP CREATED THE User Profile: The HP Palmtop As Tech Support Tool ..............•..•• 32 PAL TOP This technicaf support professional uses . ~ the HP 100's bul7t-in applications to manage ... projects, track personnel needs, stay on top of customer support problems, and more! User Profile: HP 95LX: a Road Warrior's Catch-All Organizer ...... 35 When you're on the road for over 200 days a year, it's nice to travel light. This road warrior keeps his "office" In his pocket! Programmer's Corner: Breaking AppManager Limit, More ••...•......... 40 Learn how to break the HP 100LX Application Man(;lger 38 pfQSJram barrier and speed up HF' CALC s Solver function. -

United States District Court Southern District of New York
Case 1:18-cv-11176-VEC Document 95 Filed 05/17/21 Page 1 of 46 UNITED STATES DISTRICT COURT SOUTHERN DISTRICT OF NEW YORK MARY JENNIFER PERKS, MARIA NAVARRO-REYES on behalf of themselves and CASE NO. 1:18-CV-11176-DAB all others similarly situated, Plaintiffs, v. TD BANK, N.A., Defendant. MEMORANDUM IN SUPPORT OF PLAINTIFFS’ UNOPPOSED MOTION FOR PRELIMINARY APPROVAL OF CLASS SETTLEMENT, PRELIMINARY CERTIFICATION OF SETTLEMENT CLASS, AND APPROVAL OF NOTICE PLAN Case 1:18-cv-11176-VEC Document 95 Filed 05/17/21 Page 2 of 46 TABLE OF CONTENTS Table of Authorities ....................................................................................................................... iii Introduction ..................................................................................................................................... 1 Background of the Litigation .......................................................................................................... 2 Mediation and Settlement Negotiations .......................................................................................... 5 Summary of the Proposed Settlement Terms.................................................................................. 6 I. The Settlement Class Definition ......................................................................................... 6 II. Benefits of the Settlement ................................................................................................... 7 A. The $41.5 million Settlement. ................................................................................ -

High Risk/No Reward Jul
Dane Capital Management, LLC, Dane Capital Management LLC Value, special situations, long/short equity, hedge fund manager CDRB: 90%+ Downside - High Risk/No Reward Jul. 30, 2015 6:40 PM ET Disclosure: I am/we are short CDRB. (More...) Summary • Code Rebel is likely worth no more than its current cash balance plus a modest amount for its acquisition of ThinOps Resources. In sum, no more than $1 per share. • Code Rebel has 2 employees, $36,000 in revenue in 1Q, down y/y and sequentially, has no patents or patents pending, and competes against Amazon, Citrix, Google, LogMeIn, Microsoft, and others. • While the value of operations is likely negligible, we believe recent public statements by management could result in regulatory scrutiny. • It appears that the company may have omitted material information from it's recent IPO prospectus and provided misleading information regarding business trends. • Public statements by the CEO and Board Member Dr. James Canton at a minimum appear to embellish facts. Dr. Canton's $14.2 million restricted stock grant could be motivating his enthusiasm. Code Rebel (NASDAQ:CDRB) is one of the most over-valued stocks we have ever seen. The company boasts a market-cap approaching $200 million, despite having just $36,700 (no zeros missing) in 1Q revenues, which was down sequentially and year-over-year. The company has only 2 full-time employees. The CEO Arben Kryeziu, is only part time, as he is also CTO of publicly-traded FlikMedia (OTCPK:FLKM) - which has deficient internal controls and going- concern risk according to its filings. -

Regular Joint Meeting of the Retirement Boards
City of Fresno Retirement Systems REGULAR JOINT MEETING OF THE RETIREMENT BOARDS AGENDA Tuesday, August 27, 2019 12:00 PM Retirement Office, 2828 Fresno St., 2nd Fl., Board Chamber, Room 202, Fresno, CA 93721 EMPLOYEES RETIREMENT BOARD Phillip Hardcastle-Chair, TJ Miller-Vice Chair, Marvell French, David Cain, Jane Sumpter FIRE AND POLICE RETIREMENT BOARD Jonathan Lusk-Chair, John Jensen-Vice Chair Theodore Semonious, Lynn Bennink, Donald Gross (1) If you want to speak to the Board, please complete a Request to Speak form and hand it to the Board Secretary at the beginning of the Board Meeting. (2) The meeting room is accessible to the physically disabled, and the services of a translator can be made available. Requests for additional accommodations for the disabled, signers, assistive listening devices, or translators should be made one week prior to the meeting. Please call the Retirement Board Secretary at 559-621-7085 to make arrangements. (3) When considering disability retirement applications, the Board may find it necessary to discuss matters relating to the evaluation of the work performance of an employee who has applied for disability retirement, or discuss complaints or charges made against such employee. If this occurs, the Board may adjourn to a closed session to discuss such matters pursuant to Government Code secion 54957, unless the employee requests that the discussion be in public. ROLL CALL At the commencement of the first meeting and after roll call is taken, those present will be asked to stand for the Pledge of Allegiance. APPROVE MINUTES Approve Minutes of August 14, 2019, Regular Joint Meeting of the Retirement Boards. -

Trading Secrets Blog 2012 Year in Review
Trading Secrets A Law Blog on Trade Secrets, Non-Competes, and Computer Fraud 2012 – Year in Review Dear Clients and Friends, 2012 was another fabulous year for our Trading Secrets blog. Launched in 2007, the blog has continued to grow in both readership and postings. Content from Trading Secrets has appeared on newsfeeds such as Lexology and ITechLaw, Corporate Counsel, Bloomberg News, BNA, and Kevin O’Keefe’s “Real Lawyers Have Blogs,” one of the leading sources of information and commentary on the use of blogs. We are pleased to provide you with this 2012 Year in Review which compiles our significant blog posts from 2012 and highlights our blog’s authors. For a general overview of 2012, we direct you to our Top-10 2012 Developments/Headlines in Trade Secret, Computer Fraud, and Non-Compete Law blog entry as well as our 2012 Trade Secrets Webinar Series - Year in Review blog entry, which provide a summary of key cases and legislative developments in 2011, as well as practical advice on maintaining trade secret protections. As the specific blog entries that are contained in this Review demonstrate, our blog authors stay on top of the latest developments in this area of law and provide timely and entertaining posts on significant new cases, legal developments, and legislation. We incorporated several new features, including video interviews, an informative resources page, special guest authors, and cutting edge infographics, and provided access to our well-received Trade Secret Webinar Series from 2011 to the present. In 2013, we plan to incorporate video blog posts, audio podcasts, more special guest authors, and provide a more enhanced resources page on the blog.