Powertrace for NEXUS Samples All Trace Messages Output Via the NEXUS Auxiliary Output Port E.G
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Fill Your Boots: Enhanced Embedded Bootloader Exploits Via Fault Injection and Binary Analysis
IACR Transactions on Cryptographic Hardware and Embedded Systems ISSN 2569-2925, Vol. 2021, No. 1, pp. 56–81. DOI:10.46586/tches.v2021.i1.56-81 Fill your Boots: Enhanced Embedded Bootloader Exploits via Fault Injection and Binary Analysis Jan Van den Herrewegen1, David Oswald1, Flavio D. Garcia1 and Qais Temeiza2 1 School of Computer Science, University of Birmingham, UK, {jxv572,d.f.oswald,f.garcia}@cs.bham.ac.uk 2 Independent Researcher, [email protected] Abstract. The bootloader of an embedded microcontroller is responsible for guarding the device’s internal (flash) memory, enforcing read/write protection mechanisms. Fault injection techniques such as voltage or clock glitching have been proven successful in bypassing such protection for specific microcontrollers, but this often requires expensive equipment and/or exhaustive search of the fault parameters. When multiple glitches are required (e.g., when countermeasures are in place) this search becomes of exponential complexity and thus infeasible. Another challenge which makes embedded bootloaders notoriously hard to analyse is their lack of debugging capabilities. This paper proposes a grey-box approach that leverages binary analysis and advanced software exploitation techniques combined with voltage glitching to develop a powerful attack methodology against embedded bootloaders. We showcase our techniques with three real-world microcontrollers as case studies: 1) we combine static and on-chip dynamic analysis to enable a Return-Oriented Programming exploit on the bootloader of the NXP LPC microcontrollers; 2) we leverage on-chip dynamic analysis on the bootloader of the popular STM8 microcontrollers to constrain the glitch parameter search, achieving the first fully-documented multi-glitch attack on a real-world target; 3) we apply symbolic execution to precisely aim voltage glitches at target instructions based on the execution path in the bootloader of the Renesas 78K0 automotive microcontroller. -

Radare2 Book
Table of Contents introduction 1.1 Introduction 1.2 History 1.2.1 Overview 1.2.2 Getting radare2 1.2.3 Compilation and Portability 1.2.4 Compilation on Windows 1.2.5 Command-line Flags 1.2.6 Basic Usage 1.2.7 Command Format 1.2.8 Expressions 1.2.9 Rax2 1.2.10 Basic Debugger Session 1.2.11 Contributing to radare2 1.2.12 Configuration 1.3 Colors 1.3.1 Common Configuration Variables 1.3.2 Basic Commands 1.4 Seeking 1.4.1 Block Size 1.4.2 Sections 1.4.3 Mapping Files 1.4.4 Print Modes 1.4.5 Flags 1.4.6 Write 1.4.7 Zoom 1.4.8 Yank/Paste 1.4.9 Comparing Bytes 1.4.10 Visual mode 1.5 Visual Disassembly 1.5.1 2 Searching bytes 1.6 Basic Searches 1.6.1 Configurating the Search 1.6.2 Pattern Search 1.6.3 Automation 1.6.4 Backward Search 1.6.5 Search in Assembly 1.6.6 Searching for AES Keys 1.6.7 Disassembling 1.7 Adding Metadata 1.7.1 ESIL 1.7.2 Scripting 1.8 Loops 1.8.1 Macros 1.8.2 R2pipe 1.8.3 Rabin2 1.9 File Identification 1.9.1 Entrypoint 1.9.2 Imports 1.9.3 Symbols (exports) 1.9.4 Libraries 1.9.5 Strings 1.9.6 Program Sections 1.9.7 Radiff2 1.10 Binary Diffing 1.10.1 Rasm2 1.11 Assemble 1.11.1 Disassemble 1.11.2 Ragg2 1.12 Analysis 1.13 Code Analysis 1.13.1 Rahash2 1.14 Rahash Tool 1.14.1 Debugger 1.15 3 Getting Started 1.15.1 Registers 1.15.2 Remote Access Capabilities 1.16 Remoting Capabilities 1.16.1 Plugins 1.17 Plugins 1.17.1 Crackmes 1.18 IOLI 1.18.1 IOLI 0x00 1.18.1.1 IOLI 0x01 1.18.1.2 Avatao 1.18.2 R3v3rs3 4 1.18.2.1 .intro 1.18.2.1.1 .radare2 1.18.2.1.2 .first_steps 1.18.2.1.3 .main 1.18.2.1.4 .vmloop 1.18.2.1.5 .instructionset 1.18.2.1.6 -

AVR32 EVK1105 Evaluation Kit
Your Electronic Engineering Resource ATMEL - ATEVK1105 - AVR32 EVK1105 Evaluation Kit Product Overview: The AVR32 EVK1105 is an evaluation kit for the AT32UC3A3256 which combines Atmel’s state of art AVR32 microcontroller with an unrivalled selection of communication interface like USB device including On-The-Go functionality, SDcard, NAND flash with ECC and stereo 16-bit DAC. The AVR32 EVK1105 is an evaluation kit for the AT32UC3A0512 which demonstrates Atmel’s state-of-the-art AVR32 microcontroller in Hi-Fi audio decoding and streaming applications. Kit Contents: The kit contains reference hardware and software for generic MP3 player docking stations. Key Features: High Performance, Low Power AVR®32 UC 32-Bit Microcontroller Multi-Layer Bus System Internal High-Speed Flash Internal High-Speed SRAM Interrupt Controller Power and Clock Manager Including Internal RC Clock and One 32KHz Oscillator Two Multipurpose Oscillators and Two Phase-Lock-Loop (PLL), Watchdog Timer, Real-Time Clock Timer External Memories MultiMediaCard (MMC), Secure-Digital (SD), SDIO V1.1 CE-ATA, FastSD, SmartMedia, Compact Flash Memory Stick: Standard Format V1.40, PRO Format V1.00, Micro IDE Interface One Advanced Encryption System (AES) for AT32UC3A3256S, AT32UC3A3128S and AT32UC3A364S Universal Serial Bus (USB) One 8-channel 10-bit Analog-To-Digital Converter, multiplexed with Digital IOs. Legal Disclaimer: The content of the pages of this website is for your general information and use only. It is subject to change without notice. From time to time, this website may also include links to other websites. These links are provided for your convenience to provide further information. They do not signify that we endorse the website(s). -

Schedule 14A Employee Slides Supertex Sunnyvale
UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 SCHEDULE 14A Proxy Statement Pursuant to Section 14(a) of the Securities Exchange Act of 1934 Filed by the Registrant Filed by a Party other than the Registrant Check the appropriate box: Preliminary Proxy Statement Confidential, for Use of the Commission Only (as permitted by Rule 14a-6(e)(2)) Definitive Proxy Statement Definitive Additional Materials Soliciting Material Pursuant to §240.14a-12 Supertex, Inc. (Name of Registrant as Specified In Its Charter) Microchip Technology Incorporated (Name of Person(s) Filing Proxy Statement, if other than the Registrant) Payment of Filing Fee (Check the appropriate box): No fee required. Fee computed on table below per Exchange Act Rules 14a-6(i)(1) and 0-11. (1) Title of each class of securities to which transaction applies: (2) Aggregate number of securities to which transaction applies: (3) Per unit price or other underlying value of transaction computed pursuant to Exchange Act Rule 0-11 (set forth the amount on which the filing fee is calculated and state how it was determined): (4) Proposed maximum aggregate value of transaction: (5) Total fee paid: Fee paid previously with preliminary materials. Check box if any part of the fee is offset as provided by Exchange Act Rule 0-11(a)(2) and identify the filing for which the offsetting fee was paid previously. Identify the previous filing by registration statement number, or the Form or Schedule and the date of its filing. (1) Amount Previously Paid: (2) Form, Schedule or Registration Statement No.: (3) Filing Party: (4) Date Filed: Filed by Microchip Technology Incorporated Pursuant to Rule 14a-12 of the Securities Exchange Act of 1934 Subject Company: Supertex, Inc. -

Reverse Software Engineering As a Project-Based Learning Tool
Paper ID #33764 Reverse Software Engineering as a Project-Based Learning Tool Ms. Cynthia C. Fry, Baylor University CYNTHIA C. FRY is currently a Senior Lecturer of Computer Science at Baylor University. She worked at NASA’s Marshall Space Flight Center as a Senior Project Engineer, a Crew Training Manager, and the Science Operations Director for STS-46. She was an Engineering Duty Officer in the U.S. Navy (IRR), and worked with the Naval Maritime Intelligence Center as a Scientific/Technical Intelligence Analyst. She was the owner and chief systems engineer for Systems Engineering Services (SES), a computer systems design, development, and consultation firm. She joined the faculty of the School of Engineering and Computer Science at Baylor University in 1997, where she teaches a variety of engineering and computer science classes, she is the Faculty Advisor for the Women in Computer Science (WiCS), the Director of the Computer Science Fellows program, and is a KEEN Fellow. She has authored and co- authored over fifty peer-reviewed papers. Mr. Zachary Michael Steudel Zachary Steudel is a 2021 graduate of Baylor University’s computer science department. In his time at Baylor, he worked as a Teaching Assistant under Ms. Cynthia C. Fry. As part of the Teaching Assistant role, Zachary designed and created the group project for the Computer Systems course. Zachary Steudel worked as a Software Developer Intern at Amazon in the Summer of 2019, a Software Engineer Intern at Microsoft in the Summer of 2020, and begins his full-time career with Amazon in the summer of 2021 as a software engineer. -

Reassembleable Disassembling
Reassembleable Disassembling Shuai Wang, Pei Wang, and Dinghao Wu College of Information Sciences and Technology The Pennsylvania State University fszw175, pxw172, [email protected] Abstract struction level to enforce certain security policies. To ensure program control-flow integrity (CFI, meaning that Reverse engineering has many important applications in program execution is dictated to a predetermined control- computer security, one of which is retrofitting software flow graph) [1,4, 43, 17, 29, 37] without source code, the for safety and security hardening when source code is not original control-flow graph must be recovered from a bi- available. By surveying available commercial and aca- nary executable and the binary must be retrofitted with demic reverse engineering tools, we surprisingly found the CFI enforcement facility embedded [50, 49]. Sym- that no existing tool is able to disassemble executable bolic taint analysis [34] on binaries must recover assem- binaries into assembly code that can be correctly assem- bly code and data faithfully. The defending techniques bled back in a fully automated manner, even for simple against return-oriented programming (ROP) attacks also programs. Actually in many cases, the resulted disas- rely on binary analysis and reconstruction to identify and sembled code is far from a state that an assembler ac- eliminate ROP gadgets [44,9, 47, 22, 39]. cepts, which is hard to fix even by manual effort. This Despite the fact that many security hardening tech- has become a severe obstacle. People have tried to over- niques are highly dependent on reverse engineering, flex- come it by patching or duplicating new code sections for ible and easy-to-use binary manipulation itself remains retrofitting of executables, which is not only inefficient an unsolved problem. -
Local, Compressed
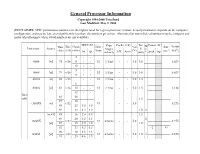
General Processor Information Copyright 1994-2000 Tom Burd Last Modified: May 2, 2000 (DISCLAIMER: SPEC performance numbers are the highest rated for a given processor version. Actual performance depends on the computer configuration, and may be less, even significantly less than, the numbers given here. Also note that non-italicized numbers may be company esti- mates of perforamnce when actual numbers are not available) SPEC-92 Pipe Cache (i/d) Tec Power (W) Date Bits Clock Units / Vdd M Size Xsistor Processor Source Stages h e (ship) (i/d) (MHz) Issue (V) (mm2) (106) int fp int/ldst/fp kB Assoc (um) t peak typ 5 - - 8086 [vi] 78 v/16 8 - - 1/1 1/1/na - - 5.0 3.0 0.029 10 - - 5 - - 8088 [vi] 79 v/16 1/1 1/1/na - - 5.0 3.0 0.029 8 - - 80186 [vi] 82 v/16 - - 1/1 1/1/na - - 5.0 1.5 6 - - 80286 [vi] 82 v/16 10 - - 1/1 1/1/na - - 5.0 1.5 0.134 12 - - Intel 85 16 x86 1.5 87 20 i386DX [vi] v/32 1/1 - - 5.0 0.275 88 25 6.5 1.9 89 33 8.4 3.0 1.0 2 [vi,41] 88 16 2.4 0.9 1.5 89 20 3.5 1.3 2 i386SX v/32 1/1 4/na/na - - 5.0 0.275 [vi] 89 25 4.6 1.9 1.0 92 33 6.2 3.3 ~2 43 90 20 3.5 1.3 i386SL [vi] v/32 1/1 4/na/na - - 5.0 1.0 2 0.855 91 25 4.6 1.9 SPEC-92 Pipe Cache (i/d) Tec Power (W) Date Bits Clock Units / Vdd M Size Xsistor Processor Source Stages h e (ship) (i/d) (MHz) Issue (V) (mm2) (106) int fp int/ldst/fp kB Assoc (um) t peak typ [vi] 89 25 14.2 6.7 1.0 2 i486DX [vi,45] 90 v/32 33 18.6 8.5 2/1 5/na/5? 8 u. -

A Survey of Reverse Engineering Tools for the 32-Bit Microsoft Windows Environment
A Survey of Reverse Engineering Tools for the 32-Bit Microsoft Windows Environment RAYMOND J. CANZANESE, JR., MATTHEW OYER, SPIROS MANCORIDIS, and MOSHE KAM College of Engineering Drexel University, Philadelphia, PA, USA Reverse engineering is defined by Chikosfky and Cross as the process of analyzing a subject system to identify the system's components and their relationships, and to create representations of the system in another form or at a higher level of abstraction. The process of reverse engineering is accomplished using specific tools that, for the 32-bit Microsoft Windows environment, are categorized as hex editors, disassemblers/debuggers, decompilers, or related technologies such as code obfuscators, unpackers, and PE editors. An evaluation of each tool is provided that identifies its domain of applicability and usability. Categories and Subject Descriptors: A.1 [General]: Introductory and Survey; D.2.5 [Software Engineering]: Testing and Debugging General Terms: Security, Documentation Additional Key Words and Phrases: Reverse Engineering, Disassemblers, Debuggers, Decompilers, Code Obfuscators, PE Editors Unpackers, Hex Editors 1. INTRODUCTION 1.1 The Reverse Engineering Process Software engineers are sometimes asked to understand the behavior of a program given that program's binary executable file. If they have access to the appropriate reverse engineering tools, they might choose to adhere to the following process. First, a general disassembler/debugger is used to determine the basic functionality of the program. If disassembly and debugging shows that the binary code has been obfuscated, the next step would be to determine whether the obfuscator used is a common commercial obfuscator or a custom protection scheme. A PE editor would be used to make this determination. -

M32R Family Software Manual MITSUBISHI 32-BIT SINGLE-CHIP MICROCOMPUTER
To our customers, Old Company Name in Catalogs and Other Documents On April 1st, 2010, NEC Electronics Corporation merged with Renesas Technology Corporation, and Renesas Electronics Corporation took over all the business of both companies. Therefore, although the old company name remains in this document, it is a valid Renesas Electronics document. We appreciate your understanding. Renesas Electronics website: http://www.renesas.com April 1st, 2010 Renesas Electronics Corporation Issued by: Renesas Electronics Corporation (http://www.renesas.com) Send any inquiries to http://www.renesas.com/inquiry. Notice 1. All information included in this document is current as of the date this document is issued. Such information, however, is subject to change without any prior notice. Before purchasing or using any Renesas Electronics products listed herein, please confirm the latest product information with a Renesas Electronics sales office. Also, please pay regular and careful attention to additional and different information to be disclosed by Renesas Electronics such as that disclosed through our website. 2. Renesas Electronics does not assume any liability for infringement of patents, copyrights, or other intellectual property rights of third parties by or arising from the use of Renesas Electronics products or technical information described in this document. No license, express, implied or otherwise, is granted hereby under any patents, copyrights or other intellectual property rights of Renesas Electronics or others. 3. You should not alter, modify, copy, or otherwise misappropriate any Renesas Electronics product, whether in whole or in part. 4. Descriptions of circuits, software and other related information in this document are provided only to illustrate the operation of semiconductor products and application examples. -

Microprocessor Training
Microprocessors and Microcontrollers © 1999 Altera Corporation 1 Altera Confidential Agenda New Products - MicroController products (1 hour) n Microprocessor Systems n The Embedded Microprocessor Market n Altera Solutions n System Design Considerations n Uncovering Sales Opportunities © 2000 Altera Corporation 2 Altera Confidential Embedding microprocessors inside programmable logic opens the door to a multi-billion dollar market. Altera has solutions for this market today. © 2000 Altera Corporation 3 Altera Confidential Microprocessor Systems © 1999 Altera Corporation 4 Altera Confidential Processor Terminology n Microprocessor: The implementation of a computer’s central processor unit functions on a single LSI device. n Microcontroller: A self-contained system with a microprocessor, memory and peripherals on a single chip. “Just add software.” © 2000 Altera Corporation 5 Altera Confidential Examples Microprocessor: Motorola PowerPC 600 Microcontroller: Motorola 68HC16 © 2000 Altera Corporation 6 Altera Confidential Two Types of Processors Computational Embedded n Programmable by the end-user to n Performs a fixed set of functions that accomplish a wide range of define the product. User may applications configure but not reprogram. n Runs an operating system n May or may not use an operating system n Program exists on mass storage n Program usually exists in ROM or or network Flash n Tend to be: n Tend to be: – Microprocessors – Microcontrollers – More expensive (ASP $193) – Less expensive (ASP $12) n Examples n Examples – Work Station -

Embedded Electronic Coding System
1 GUARD FOR BLIND PEOPLE GUARD FOR BLIND PEOPLE ELECTRONICS AND COMMUNICATION LITAM 2 GUARD FOR BLIND PEOPLE ABSTRACT Aim of this project is to design and develop the electronic guard for blind people on embedded plat form. This project was developed for keep the right way for blind people. It has two important units; they are object detecting sensor unit and micro-controller alarm unit. The object detecting sensor is sense the opposite objects, if the blind person is going to hit any object, the sensor sense that object and given to controller. The controller activates the driver circuit; it will produce the alarm sound, now the people easily identify the opposite object. ELECTRONICS AND COMMUNICATION LITAM 3 GUARD FOR BLIND PEOPLE CHAPTER 1 INTRODUCTION ELECTRONICS AND COMMUNICATION LITAM 4 GUARD FOR BLIND PEOPLE 1.1 METHODOLOGY OF STUDY An embedded based electronic code locking system is designed and implemented using PIC Micro controller to make security. The entire project was developed under embedded systems. EMBEDDED SYSTEMS: A system is something that maintains its existence and functions as a whole through the interaction of its parts. E.g. Body, Mankind, Access Control, etc A system is a part of the world that a person or group of persons during some time interval and for some purpose choose to regard as a whole, consisting of interrelated components, each component characterized by properties that are selected as being relevant to the purpose. • Embedded System is a combination of hardware and software used to achieve a single specific task. • Embedded systems are computer systems that monitor, respond to, or control an external environment. -

Technical Report
Technical Report Department of Computer Science University of Minnesota 4-192 EECS Building 200 Union Street SE Minneapolis, MN 55455-0159 USA TR 97-030 Hardware and Compiler-Directed Cache Coherence in Large-Scale Multiprocessors by: Lynn Choi and Pen-Chung Yew Hardware and Compiler-Directed Cache Coherence 1n Large-Scale Multiprocessors: Design Considerations and Performance Study1 Lynn Choi Center for Supercomputing Research and Development University of Illinois at Urbana-Champaign 1308 West Main Street Urbana, IL 61801 Email: lchoi@csrd. uiuc. edu Pen-Chung Yew 4-192 EE/CS Building Department of Computer Science University of Minnesota 200 Union Street, SE Minneapolis, MN 55455-0159 Email: [email protected] Abstract In this paper, we study a hardware-supported, compiler-directed (HSCD) cache coherence scheme, which can be implemented on a large-scale multiprocessor using off-the-shelf micro processors, such as the Cray T3D. The scheme can be adapted to various cache organizations, including multi-word cache lines and byte-addressable architectures. Several system related issues, including critical sections, inter-thread communication, and task migration have also been addressed. The cost of the required hardware support is minimal and proportional to the cache size. The necessary compiler algorithms, including intra- and interprocedural array data flow analysis, have been implemented on the Polaris parallelizing compiler [33]. From our simulation study using the Perfect Club benchmarks [5], we found that in spite of the conservative analysis made by the compiler, the performance of the proposed HSCD scheme can be comparable to that of a full-map hardware directory scheme. Given its compa rable performance and reduced hardware cost, the proposed scheme can be a viable alternative for large-scale multiprocessors such as the Cray T3D, which rely on users to maintain data coherence.