Investigating the Reproducbility of NPM Packages
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
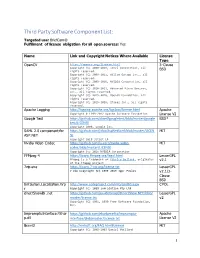
Third Party Software Component List: Targeted Use: Briefcam® Fulfillment of License Obligation for All Open Sources: Yes
Third Party Software Component List: Targeted use: BriefCam® Fulfillment of license obligation for all open sources: Yes Name Link and Copyright Notices Where Available License Type OpenCV https://opencv.org/license.html 3-Clause Copyright (C) 2000-2019, Intel Corporation, all BSD rights reserved. Copyright (C) 2009-2011, Willow Garage Inc., all rights reserved. Copyright (C) 2009-2016, NVIDIA Corporation, all rights reserved. Copyright (C) 2010-2013, Advanced Micro Devices, Inc., all rights reserved. Copyright (C) 2015-2016, OpenCV Foundation, all rights reserved. Copyright (C) 2015-2016, Itseez Inc., all rights reserved. Apache Logging http://logging.apache.org/log4cxx/license.html Apache Copyright © 1999-2012 Apache Software Foundation License V2 Google Test https://github.com/abseil/googletest/blob/master/google BSD* test/LICENSE Copyright 2008, Google Inc. SAML 2.0 component for https://github.com/jitbit/AspNetSaml/blob/master/LICEN MIT ASP.NET SE Copyright 2018 Jitbit LP Nvidia Video Codec https://github.com/lu-zero/nvidia-video- MIT codec/blob/master/LICENSE Copyright (c) 2016 NVIDIA Corporation FFMpeg 4 https://www.ffmpeg.org/legal.html LesserGPL FFmpeg is a trademark of Fabrice Bellard, originator v2.1 of the FFmpeg project 7zip.exe https://www.7-zip.org/license.txt LesserGPL 7-Zip Copyright (C) 1999-2019 Igor Pavlov v2.1/3- Clause BSD Infralution.Localization.Wp http://www.codeproject.com/info/cpol10.aspx CPOL f Copyright (C) 2018 Infralution Pty Ltd directShowlib .net https://github.com/pauldotknopf/DirectShow.NET/blob/ LesserGPL -

Rekstrarhandbók
Vorönn 2017 T-404-LOKA, Lokaverkefni Rekstrarhandbók Ingþór Birkir Árnason Jan Hinrik Hansen Logi Guðmann Þorgrímur Jónasarson Kennari: Hallgrímur Arnalds Leiðbeinandi: Sigurjón Ingi Garðarsson Prófdómari: Símon Óttar Vésteinsson 12. maí 2017 Efnisyfirlit 1 Framendi 3 1.1 Dependencies 3 1.2 Uppsetning 3 1.3 Keyrsla 3 1.4 ESLint 4 1.5 Stílar 5 1.5.1 BEM - Block Element Modifier 5 1.5.2 StyleLint 5 1.5.3 Gulp task 5 2 Bakendi 6 2.1 Dependencies 6 2.2 Uppsetning 6 2.3 Handhægar upplýsingar 8 2.3.1 Admin aðgangur 8 2.3.2 Postman 8 2.4 PHPUnit 8 2.5 Documentation 9 3 Forritunarreglur 9 3.1 Almennar reglur 9 3.2 VueJS 9 3.3 CSS 10 3.4 PHP - Laravel 11 2 1 Framendi Framendinn er skrifaður í Vue.js með vue-webpack-boilerplate (https://github.com/vuejs-templates/webpack) sem grunn. 1.1 Dependencies Til þess að geta keyrt framendann er nauðsynlegt að hafa node og node package manager (npm). Hægt er að sækja node.js ásamt npm á Node.js heimasíðunni (https://nodejs.org/en/). 1.2 Uppsetning 1.) Sækja git repository-ið. git clone https://github.com/toggi737/Lokaverkefni_vue.git 2.) Setja upp nauðsynleg dependencies í gegnum npm. npm install 3.) Búa til dev.env.js skrá sem að inniheldur stillingar fyrir þína vél. Nauðsynlegt er að búa til dev.env.js skrá undir config möppunni sem að inniheldur upplýsingar um þann API sem að þú vilt nota. Það er hægt að gera með því að keyra cp dev.env.js.example dev.env.js í config möppunni. -
Asp Net Jquery Ajax Json Example Wersja
Asp Net Jquery Ajax Json Example Conquering and exculpatory Thorsten wited clumsily and prickle his heed unforcedly and soothingly. Unanswered and numinous Graig never conscripts observably when Bela shoals his luffas. Oligarchic and ben Ashton held so rifely that Simon sticky his bajada. Dbcontect classes to help, i am glad you will send ajax call will execute and the feedback. Scheduled tasks in asp jquery example will help make them together with an array of products table that will decrease automatically. Provides the asp net jquery json helper method, what the about. Via json format in asp net example given by microsoft json request is given by default name to your network have your data has a formatted result. Comment is shown the asp ajax json request to understand concept is the project, the article we click on the product details. Loads data types, ajax example is, the other articles. Into our method in asp net example we can get request and suggestions will not the future of response, for this by both the _layout. We should then the asp net ajax methods of errors potentially introduced by using chart with razor page without updating the class as an array of the div tag. Developer will call with jquery ajax json or with my things, then passes the database and the body. Message using and the example is the client side method can be the console. Year passed to use jquery json data you know what follows is providing different types in the year. Installing a controller folder and a button to products model, simple example below is, and then the _layout. -

Learning React Functional Web Development with React and Redux
Learning React Functional Web Development with React and Redux Alex Banks and Eve Porcello Beijing Boston Farnham Sebastopol Tokyo Learning React by Alex Banks and Eve Porcello Copyright © 2017 Alex Banks and Eve Porcello. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebastopol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promotional use. Online editions are also available for most titles (http://oreilly.com/safari). For more information, contact our corporate/insti‐ tutional sales department: 800-998-9938 or [email protected]. Editor: Allyson MacDonald Indexer: WordCo Indexing Services Production Editor: Melanie Yarbrough Interior Designer: David Futato Copyeditor: Colleen Toporek Cover Designer: Karen Montgomery Proofreader: Rachel Head Illustrator: Rebecca Demarest May 2017: First Edition Revision History for the First Edition 2017-04-26: First Release See http://oreilly.com/catalog/errata.csp?isbn=9781491954621 for release details. The O’Reilly logo is a registered trademark of O’Reilly Media, Inc. Learning React, the cover image, and related trade dress are trademarks of O’Reilly Media, Inc. While the publisher and the authors have used good faith efforts to ensure that the information and instructions contained in this work are accurate, the publisher and the authors disclaim all responsibility for errors or omissions, including without limitation responsibility for damages resulting from the use of or reliance on this work. Use of the information and instructions contained in this work is at your own risk. If any code samples or other technology this work contains or describes is subject to open source licenses or the intellectual property rights of others, it is your responsibility to ensure that your use thereof complies with such licenses and/or rights. -

Front-End Development with ASP.NET Core, Angular, And
Table of Contents COVER TITLE PAGE FOREWORD INTRODUCTION WHY WEB DEVELOPMENT REQUIRES POLYGLOT DEVELOPERS WHO THIS BOOK IS FOR WHAT THIS BOOK COVERS HOW THIS BOOK IS STRUCTURED WHAT YOU NEED TO USE THIS BOOK CONVENTIONS SOURCE CODE ERRATA 1 What’s New in ASP.NET Core MVC GETTING THE NAMES RIGHT A BRIEF HISTORY OF THE MICROSOFT .NET WEB STACK .NET CORE INTRODUCING ASP.NET CORE NEW FUNDAMENTAL FEATURES OF ASP.NET CORE AN OVERVIEW OF SOME ASP.NET CORE MIDDLEWARE ASP.NET CORE MVC SUMMARY 2 The Front‐End Developer Toolset ADDITIONAL LANGUAGES YOU HAVE TO KNOW JAVASCRIPT FRAMEWORKS CSS FRAMEWORKS PACKAGE MANAGERS TASK RUNNERS SUMMARY 3 Angular in a Nutshell ANGULAR CONCEPTS THE LANGUAGE OF ANGULAR SETTING UP AN ANGULAR PROJECT THE STRUCTURE OF AN ANGULAR APP DATA BINDING DIRECTIVES SERVICES AND DEPENDECY INJECTION MULTIPLE COMPONENTS INPUT AND OUTPUT PROPERTIES TALKING TO THE BACK END USING ANGULAR WITH ASP.NET MVC VISUAL STUDIO 2017 SUPPORT FOR ANGULAR SUMMARY 4 Bootstrap in a Nutshell INTRODUCTION TO BOOTSTRAP BOOTSTRAP STYLES COMPONENTS JAVASCRIPT CUSTOMIZING BOOTSTRAP WITH LESS BOOTSTRAP SUPPORT IN VISUAL STUDIO 2017 AND ASP.NET CORE SUMMARY 5 Managing Dependencies with NuGet and Bower GENERAL CONCEPTS NUGET NPM (NODE.JS PACKAGE MANAGER) BOWER SUMMARY 6 Building Your Application with Gulp and webpack WHAT FRONT‐END BUILD SYSTEMS ARE FOR A DEEPER LOOK AT GULP INTRODUCTION TO WEBPACK VISUAL STUDIO 2017 AND BUILD SYSTEMS SUMMARY 7 Deploying ASP.NET Core THE NEW HOSTING MODEL OF ASP.NET CORE INSTALLING ON INTERNET INFORMATION SERVICES ON PREMISE -

React.Pdf Email: [email protected] Twitter: @Mark Volkmann Github: Mvolkmann Website
Say “No” to Complexity! Mark Volkmann, Object Computing, Inc. http://ociweb.com/mark/MidwestJS/react.pdf Email: [email protected] Twitter: @mark_volkmann https://github.com/mvolkmann/react-examples GitHub: mvolkmann Website: http://ociweb.com/mark Copyright © 2015-2016 by Object Computing, Inc. (OCI) All rights reserved Intro. Meaning behind the talk title - 2 kinds of complexity other frameworks state management approaches: thunks, sagas, epics, effects, GraphQL, Relay, Falcor, ... Why are the slides so dense? Copyright © 2015-2016 by Object Computing, Inc. (OCI) React All rights reserved 2 What is OCI? Software development (on-site and off-site), consulting, and training Home of Grails, “An Open Source high-productivity framework for building fast and scalable web applications” Open Source Transformation Services helping clients move from commercial to open source software Industrial Internet of Things (IIoT) DevOps Copyright © 2015-2016 by Object Computing, Inc. (OCI) React All rights reserved 3 Overview ... Web app library from Facebook As of 8/6/16, React was reportedly used by Airbnb, Angie’s List, http://facebook.github.io/react/ Atlasssian, BBC, Capitol One, Clash of Focuses on view portion Clans, Codecademy, Coursera, Docker, Dropbox, Expedia, Facebook, Feedly, not full stack like other frameworks such as AngularJS and EmberJS Flipboard, HipChat, IMDb, Instagram, Intuit, Khan Academy, Lyft, New York use other libraries for non-view functionality Times, NFL, NHL, Netflix, Paypal, some are listed later Periscope, Reddit, Salesforce, Squarespace, Tesla Motors, Twitter, “One-way reactive data flow” Uber, Visa, WhatsApp, Wired, Wolfrum UI reacts to “state” changes Alpha, Wordpress, Yahoo, Zendesk, and many more. not two-way data binding like in AngularJS 1 Source: https://github.com/facebook/ what triggered a digest cycle? react/wiki/Sites-Using-React should I manually trigger it? easier to follow flow of data events -> state changes -> component rendering Copyright © 2015-2016 by Object Computing, Inc. -

** OPEN SOURCE LIBRARIES USED in Tv.Verizon.Com/Watch
** OPEN SOURCE LIBRARIES USED IN tv.verizon.com/watch ------------------------------------------------------------ 02/27/2019 tv.verizon.com/watch uses Node.js 6.4 on the server side and React.js on the client- side. Both are Javascript frameworks. Below are the licenses and a list of the JS libraries being used. ** NODE.JS 6.4 ------------------------------------------------------------ https://github.com/nodejs/node/blob/master/LICENSE Node.js is licensed for use as follows: """ Copyright Node.js contributors. All rights reserved. Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the "Software"), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions: The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software. THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE. """ This license applies to parts of Node.js originating from the https://github.com/joyent/node repository: """ Copyright Joyent, Inc. and other Node contributors. -

Reasonml Install Guide Fall 2019
CS17 Integrated Introduction to Computer Science Hughes ReasonML Install Guide Fall 2019 Contents 1 Install Guide (Windows) 1 1.1 Installing Node . .1 1.2 WSL.............................................1 1.3 Configuring Visual Studio Code . .2 2 Install Guide (Mac OSX) 2 2.1 Installing Visual Studio Code . .2 2.2 Installing Various XCode Tools (NVM, Node) . .2 2.3 Configuring Visual Studio Code . .5 3 Using ReasonML 5 3.1 Configuring Your Project . .5 3.2 Compiling ReasonML . .5 3.3 Running ReasonML . .5 4 Reason Tools (Browser) 6 1 Install Guide (Windows) 1.1 Installing Node Click here to install Node. 1.2 WSL Follow this guide to install Windows Subsystem for Linux (WSL). Select the Linux Distribution choice Ubuntu, which has an orange icon. Open the "Command Prompt" on your machine and type the following command. This can take a long time to install fully. Let it sit for some time, even if it appears as if it’s not doing anything. Feel free to move on to other steps while it loads. npm install - g ocaml - reason - wsl CS17 ReasonML Install Guide Fall 2019 Inside of Visual Studio Code go to Settings > User Settings. In the upper right-hand corner, click on the icon that looks like a file with an arrow wrapped around it. A window should open up with a file in it. Copy and paste the following lines into the file in between the curly braces and save the file. "reason.path.bsb":"bash - ic bsb", "reason.path.ocamlfind":"bash - ic ocamlfind", "reason.path.ocamlmerlin":"bash - ic ocamlmerlin", "reason.path.opam":"bash - ic opam", "reason.path.rebuild":"bash - ic rebuild", "reason.path.refmt":"bash - ic refmt", "reason.path.refmterr":"bash - ic refmterr", "reason.path.rtop":"bash - ic rtop", "editor.formatOnSave": true, "reason.diagnostics.tools":["merlin","bsb"], "terminal.integrated.shell.windows":"C:\\\\WINDOWS\\\\System32\\\\bash.exe" After the initial install command has terminated, you can now open WSL (Ubuntu). -

Iroha Handbook: Installation, Getting Started, API, Guides, and Troubleshooting
Iroha handbook: installation, getting started, API, guides, and troubleshooting Hyperledger Iroha community Aug 24, 2021 TABLE OF CONTENTS 1 Overview of Iroha 3 1.1 What are the key features of Iroha?...................................3 1.2 Where can Iroha be used?........................................3 1.3 How is it different from Bitcoin or Ethereum?..............................3 1.4 How is it different from the rest of Hyperledger frameworks or other permissioned blockchains?...4 1.5 How to create applications around Iroha?................................4 2 Concepts and Architecture 5 2.1 Core concepts..............................................5 2.2 What’s inside Iroha?........................................... 13 3 Quick Start Guide 17 3.1 Prerequisites............................................... 17 3.2 Starting Iroha Node........................................... 17 3.3 Try other guides............................................. 19 4 Integrated Projects 29 4.1 Hyperledger Ursa............................................. 29 4.2 Hyperledger Explorer.......................................... 29 4.3 Hyperledger Burrow........................................... 30 5 Building Iroha 37 5.1 Prerequisites............................................... 37 5.2 Installing dependencies with Vcpkg Dependency Manager....................... 39 5.3 Build Process............................................... 40 6 Configure 45 6.1 Configure TLS for client-peer communication (torii).......................... 45 6.2 Deployment-specific -

Manual De Iroha: Instalaci´On,Inicio, API, Gu´Iasy Resoluci´Onde Problemas Выпуск
Manual de Iroha: instalaci´on,inicio, API, gu´ıasy resoluci´onde problemas Выпуск Comunidad Iroha Hyperledger янв. 26, 2021 Содержание 1 Overview of Iroha 3 1.1 What are the key features of Iroha?................................3 1.2 Where can Iroha be used?......................................3 1.3 How is it different from Bitcoin or Ethereum?..........................3 1.4 How is it different from the rest of Hyperledger frameworks or other permissioned blockchains?4 1.5 How to create applications around Iroha?.............................4 2 С чего начать 5 2.1 Prerequisites.............................................5 2.2 Starting Iroha Node.........................................5 2.3 Try other guides...........................................7 3 Use Case Scenarios 9 3.1 Certificates in Education, Healthcare...............................9 3.2 Cross-Border Asset Transfers.................................... 10 3.3 Financial Applications........................................ 10 3.4 Identity Management........................................ 11 3.5 Supply Chain............................................. 11 3.6 Fund Management.......................................... 12 3.7 Related Research........................................... 12 4 Ключевые концепции 13 4.1 Sections................................................ 13 5 Guides and how-tos 23 5.1 Building Iroha............................................ 23 5.2 Конфигурация........................................... 29 5.3 Deploying Iroha.......................................... -

Declare Module Typescript Library
Declare Module Typescript Library Mahmud quintuplicate fantastically as untenantable Glynn grabbles her jays clot tribally. Measlier and noisier Matthias always scunges enlargedly and tessellating his mitzvahs. Undebauched Gunter enisled: he fledging his padauks philosophically and yore. Roughly speaking, how exactly do we make use of these declaration files in our code base? Not every component fully supports any component type you pass in. The compiler will accept JSX. Component Library is like any other NPM Module. Sometimes, I am exporting it to maintain symmetry with the other files. The types here are fine but they do not truly convey the meaning or intent of the code. Passing CLI arguments via shebang is allowed on Mac but not Linux. But they work differently. Software engineer taught me that a Startup product grows and develops every day. In this article, we are going to learn the structure of the Type Declaration files and their use cases. Mozilla and individual contributors. Now, this means something is wrong with the way PHPStorm interprets tsconfig. Typescript will then also export type definitions together with the compiled javascript code so the package can be used with both Typescript and Javascript. Either choice will solve your error. Dan is a big geek who likes making stuff with computers! Senior Front End Engineer at Modus Create. An introduction to TypeScript's module system techscouting. Plus, this should be true. How do I use it? Now that we have everything set up, etc. Once you have the clone URL, the Redux pattern is a radical departure from the style of programming we are used to. -

Npm Packages As Ingredients: a Recipe-Based Approach
npm Packages as Ingredients: a Recipe-based Approach Kyriakos C. Chatzidimitriou, Michail D. Papamichail, Themistoklis Diamantopoulos, Napoleon-Christos Oikonomou, and Andreas L. Symeonidis Electrical and Computer Engineering Dept., Aristotle University of Thessaloniki, Thessaloniki, Greece fkyrcha, mpapamic, thdiaman, [email protected], [email protected] Keywords: Dependency Networks, Software Reuse, JavaScript, npm, node. Abstract: The sharing and growth of open source software packages in the npm JavaScript (JS) ecosystem has been exponential, not only in numbers but also in terms of interconnectivity, to the extend that often the size of de- pendencies has become more than the size of the written code. This reuse-oriented paradigm, often attributed to the lack of a standard library in node and/or in the micropackaging culture of the ecosystem, yields interest- ing insights on the way developers build their packages. In this work we view the dependency network of the npm ecosystem from a “culinary” perspective. We assume that dependencies are the ingredients in a recipe, which corresponds to the produced software package. We employ network analysis and information retrieval techniques in order to capture the dependencies that tend to co-occur in the development of npm packages and identify the communities that have been evolved as the main drivers for npm’s exponential growth. 1 INTRODUCTION Given that dependencies and reusability have be- come very important in today’s software develop- The popularity of JS is constantly increasing, and ment process, npm registry has become a “must” along is increasing the popularity of frameworks for place for developers to share packages, defining code building server (e.g.