Javascript Frameworks for Modern Web Development the Essential Frameworks, Libraries, and Tools to Learn Right Now Second Edition
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
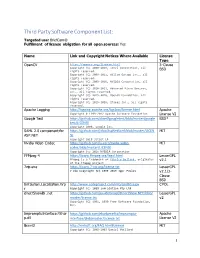
Third Party Software Component List: Targeted Use: Briefcam® Fulfillment of License Obligation for All Open Sources: Yes
Third Party Software Component List: Targeted use: BriefCam® Fulfillment of license obligation for all open sources: Yes Name Link and Copyright Notices Where Available License Type OpenCV https://opencv.org/license.html 3-Clause Copyright (C) 2000-2019, Intel Corporation, all BSD rights reserved. Copyright (C) 2009-2011, Willow Garage Inc., all rights reserved. Copyright (C) 2009-2016, NVIDIA Corporation, all rights reserved. Copyright (C) 2010-2013, Advanced Micro Devices, Inc., all rights reserved. Copyright (C) 2015-2016, OpenCV Foundation, all rights reserved. Copyright (C) 2015-2016, Itseez Inc., all rights reserved. Apache Logging http://logging.apache.org/log4cxx/license.html Apache Copyright © 1999-2012 Apache Software Foundation License V2 Google Test https://github.com/abseil/googletest/blob/master/google BSD* test/LICENSE Copyright 2008, Google Inc. SAML 2.0 component for https://github.com/jitbit/AspNetSaml/blob/master/LICEN MIT ASP.NET SE Copyright 2018 Jitbit LP Nvidia Video Codec https://github.com/lu-zero/nvidia-video- MIT codec/blob/master/LICENSE Copyright (c) 2016 NVIDIA Corporation FFMpeg 4 https://www.ffmpeg.org/legal.html LesserGPL FFmpeg is a trademark of Fabrice Bellard, originator v2.1 of the FFmpeg project 7zip.exe https://www.7-zip.org/license.txt LesserGPL 7-Zip Copyright (C) 1999-2019 Igor Pavlov v2.1/3- Clause BSD Infralution.Localization.Wp http://www.codeproject.com/info/cpol10.aspx CPOL f Copyright (C) 2018 Infralution Pty Ltd directShowlib .net https://github.com/pauldotknopf/DirectShow.NET/blob/ LesserGPL -

CRISPR/Cas9-Mediated Trp53 and Brca2 Knockout
Published OnlineFirst August 16, 2016; DOI: 10.1158/0008-5472.CAN-16-1272 Cancer Tumor and Stem Cell Biology Research CRISPR/Cas9-Mediated Trp53 and Brca2 Knockout to Generate Improved Murine Models of Ovarian High-Grade Serous Carcinoma Josephine Walton1,2, Julianna Blagih3, Darren Ennis1, Elaine Leung1, Suzanne Dowson1, Malcolm Farquharson1, Laura A. Tookman4, Clare Orange5, Dimitris Athineos3, Susan Mason3, David Stevenson3, Karen Blyth3, Douglas Strathdee3, Frances R. Balkwill2, Karen Vousden3, Michelle Lockley4, and Iain A. McNeish1,4 Abstract – – There is a need for transplantable murine models of ovarian ating novel ID8 derivatives that harbored single (Trp53 / )or – – – – high-grade serous carcinoma (HGSC) with regard to mutations in double (Trp53 / ;Brca2 / ) suppressor gene deletions. In these the human disease to assist investigations of the relationships mutants, loss of p53 alone was sufficient to increase the growth between tumor genotype, chemotherapy response, and immune rate of orthotopic tumors with significant effects observed on the microenvironment. In addressing this need, we performed whole- immune microenvironment. Specifically, p53 loss increased exome sequencing of ID8, the most widely used transplantable expression of the myeloid attractant CCL2 and promoted the model of ovarian cancer, covering 194,000 exomes at a mean infiltration of immunosuppressive myeloid cell populations into – – – – depth of 400Â with 90% exons sequenced >50Â. We found no primary tumors and their ascites. In Trp53 / ;Brca2 / mutant functional mutations in genes characteristic of HGSC (Trp53, cells, we documented a relative increase in sensitivity to the PARP Brca1, Brca2, Nf1, and Rb1), and p53 remained transcriptionally inhibitor rucaparib and slower orthotopic tumor growth – – active. Homologous recombination in ID8 remained intact in compared with Trp53 / cells, with an appearance of intratumoral þ functional assays. -

THE FUTURE of SCREENS from James Stanton a Little Bit About Me
THE FUTURE OF SCREENS From james stanton A little bit about me. Hi I am James (Mckenzie) Stanton Thinker / Designer / Engineer / Director / Executive / Artist / Human / Practitioner / Gardner / Builder / and much more... Born in Essex, United Kingdom and survived a few hair raising moments and learnt digital from the ground up. Ok enough of the pleasantries I have been working in the design field since 1999 from the Falmouth School of Art and onwards to the RCA, and many companies. Ok. less about me and more about what I have seen… Today we are going to cover - SCREENS CONCEPTS - DIGITAL TRANSFORMATION - WHY ASSETS LIBRARIES - CODE LIBRARIES - COST EFFECTIVE SOLUTION FOR IMPLEMENTATION I know, I know, I know. That's all good and well, but what does this all mean to a company like mine? We are about to see a massive change in consumer behavior so let's get ready. DIGITAL TRANSFORMATION AS A USP Getting this correct will change your company forever. DIGITAL TRANSFORMATION USP-01 Digital transformation (DT) – the use of technology to radically improve performance or reach of enterprises – is becoming a hot topic for companies across the globe. VERY DIGITAL CHANGING NOT VERY DIGITAL DIGITAL TRANSFORMATION USP-02 Companies face common pressures from customers, employees and competitors to begin or speed up their digital transformation. However they are transforming at different paces with different results. VERY DIGITAL CHANGING NOT VERY DIGITAL DIGITAL TRANSFORMATION USP-03 Successful digital transformation comes not from implementing new technologies but from transforming your organisation to take advantage of the possibilities that new technologies provide. -

The Jungle Through Javascript Frameworks
The jungle through Javascript frameworks. Jonatan Karlsson Henrik Ölund Web Programming Web Programming 2013, BTH, Blekinge institute of 2013, BTH, Blekinge institute of technology technology Advanced topic in Web development, PA1426 Advanced topic in Web development, PA1426 HT15 HT15 Karlskrona, Sweden Karlskrona, Sweden [email protected] [email protected] PA1426 Revision C, Advanced topic in Web development 2015-11-05 Abstract In this article we have planned to dive into Javascripts world where new framework comes out “every day”. We will take the reader into a world where nothing are for granted and everything is a non-standard. In the current situation, there is a [3] tremendous amount of Javascript frameworks and that makes it difficult for a layman to choose the right framework, for the right task and this is something we will try figure out and explain to the reader. Keywords: Javascript, Framework, MV*, Client-side, React, Mithril, Backbone.js, Ember.js 1 PA1426 Revision C, Advanced topic in Web development 2015-11-05 Abstract 1. Introduction 1.1 Background 1.2 Intention 1.3 Method First part Does the framework follow the MV*-pattern? Is the framework popular on google? Have the framework risen in popularity since 2013? Does the framework have any corporation that backs them? Second part 2. Result 2.1 Which frameworks did we select? 2.2 Not included 2.3 React What philosophies have pushed this framework forward? What kind of problem does this framework solve? Which famous products has been created with this framework? -

Glen R. Goodwin [email protected] Laurel, Maryland
Glen R. Goodwin [email protected] Laurel, Maryland https://arei.net Experience August 2019 to Director of Software Engineering / Lead Engineer, Whitebox Technology, Present Baltimore, Maryland • Lead day to day operations of entire Engineering Directorate including growing team from 5 engineers to 18 engineers. • Designed and implemented entire Engineering department’s communication and process and company culture of Software excellence. • Mentored entire team and individual developers in communication, architecture, engineering best practices, and software quality. • Served as Lead Engineer for Systems Team, responsible for implementing innovative systems to deliver faster, more efficently, and at scale • Served as Lead Experience Engineer fostering and implementing consistent cross product common solutions to better enhance the company brand and the end user expereience. • Designed and delivered technical solutions across the entire company on everything from visualizations to automated conveyance systems. July 2018 to Founder, The Awesome Engineering Company, Laurel, Maryland August 2019 • Started The Awesome Engineering Company to productize personally developed open source solutions. • Developed open source products for NodeJS and modern browsers. October 2013 to Distinguished Software Engineer & Chief Architect for CyberSecurity, SAS July 2018 Institute inc, Ellicott City, Maryland • Chief Architect for the SAS Cybersecurity product line overseeing technical (Converted from VSTI vision from inception to release. employee to parent SAS company in October 2013) • Served as Engineering Lead for User Interface, Services (API), Persistence (ElasticSearch), and Enrichment teams structured around technical layers. • Acted as Lead Researcher for new implementations and technology experiments advising senior management on feasibility and direction • Designed and implemented backend and frontend technologies for the entire product from conception to delivery in multiple languages/frameworks. -

** OPEN SOURCE LIBRARIES USED in Tv.Verizon.Com/Watch
** OPEN SOURCE LIBRARIES USED IN tv.verizon.com/watch ------------------------------------------------------------ 02/27/2019 tv.verizon.com/watch uses Node.js 6.4 on the server side and React.js on the client- side. Both are Javascript frameworks. Below are the licenses and a list of the JS libraries being used. ** NODE.JS 6.4 ------------------------------------------------------------ https://github.com/nodejs/node/blob/master/LICENSE Node.js is licensed for use as follows: """ Copyright Node.js contributors. All rights reserved. Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the "Software"), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions: The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software. THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE. """ This license applies to parts of Node.js originating from the https://github.com/joyent/node repository: """ Copyright Joyent, Inc. and other Node contributors. -

From GWT to Angular: an Experiment Report on Migrating a Legacy Web
From GWT to Angular: An Experiment Report on Migrating a Legacy Web Application Benoit Verhaeghe, Anas Shatnawi, Abderrahmane Seriai, Anne Etien, Nicolas Anquetil, Mustapha Derras, Stephane Ducasse To cite this version: Benoit Verhaeghe, Anas Shatnawi, Abderrahmane Seriai, Anne Etien, Nicolas Anquetil, et al.. From GWT to Angular: An Experiment Report on Migrating a Legacy Web Application. IEEE Software, Institute of Electrical and Electronics Engineers, In press, 10.1109/MS.2021.3101249. hal-03313462 HAL Id: hal-03313462 https://hal.archives-ouvertes.fr/hal-03313462 Submitted on 4 Aug 2021 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Department: Head Editor: Name, xxxx@email From GWT to Angular: An Experiment Report on Migrating a Legacy Web Application B. Verhaeghe Berger-Levrault, France Université de Lille, CNRS, Inria, Centrale Lille, UMR 9189 – CRIStAL, France A. Shatnawi Berger-Levrault, France A. Seriai Berger-Levrault, France A. Etien Université de Lille, CNRS, Inria, Centrale Lille, UMR 9189 – CRIStAL, France N. Anquetil Université de Lille, CNRS, Inria, Centrale Lille, UMR 9189 – CRIStAL, France M. Derras Berger-Levrault, France S. Ducasse Université de Lille, CNRS, Inria, Centrale Lille, UMR 9189 – CRIStAL, France Abstract—Berger-Levrault is an international company that developed applications in GWT for more than 10 years. -

Analysing the Use of Outdated Javascript Libraries on the Web
Updated in September 2017: Require valid versions for library detection throughout the paper. The vulnerability analysis already did so and remains identical. Modifications in Tables I, III and IV; Figures 4 and 7; Sections III-B, IV-B, IV-C, IV-F and IV-H. Additionally, highlight Ember’s security practices in Section V. Thou Shalt Not Depend on Me: Analysing the Use of Outdated JavaScript Libraries on the Web Tobias Lauinger, Abdelberi Chaabane, Sajjad Arshad, William Robertson, Christo Wilson and Engin Kirda Northeastern University {toby, 3abdou, arshad, wkr, cbw, ek}@ccs.neu.edu Abstract—Web developers routinely rely on third-party Java- scripts or HTML into vulnerable websites via a crafted tag. As Script libraries such as jQuery to enhance the functionality of a result, it is of the utmost importance for websites to manage their sites. However, if not properly maintained, such dependen- library dependencies and, in particular, to update vulnerable cies can create attack vectors allowing a site to be compromised. libraries in a timely fashion. In this paper, we conduct the first comprehensive study of To date, security research has addressed a wide range of client-side JavaScript library usage and the resulting security client-side security issues in websites, including validation [30] implications across the Web. Using data from over 133 k websites, we show that 37 % of them include at least one library with a and XSS ([17], [36]), cross-site request forgery [4], and session known vulnerability; the time lag behind the newest release of fixation [34]. However, the use of vulnerable JavaScript libraries a library is measured in the order of years. -

MASTER THESIS Javascript Frameworks a Qualitative
MASTER THESIS JavaScript Frameworks A qualitative evaluation and comparison of the dominant factors in Angular and React Abdul Kadir Yorulmaz MSc. in Computer Science & Informatics Supervised by Anders Lassen Department of Computer Science & Informatics June 2, 2020 Abstract The rising number of JavaScript libraries and frameworks that have been developed during the years, gives the experienced and inexperienced practitioners complexity when wanting to commit to a frame- work. Today, a more concrete and analysed evaluation process is lacking for developers in order to make sure a framework fit their needs for the given project’s purpose and size. This thesis explores an evaluation process that can help practitioners determine which framework or library fit their needs for their project, but also choosing the framework that fits best with their experience and preferences when building applications. This study is build on an experiment, where two Todo-list applications were developed via Angular and React. Based on the development process of each application, the framework and library were evaluated via relevant factors that give insights to what to expect from the framework and library in terms of how fast one can learn it, the quality of the documentation, the helpfulness of their communities and the frequency of updates. Through the evaluations, the dominant factors were found for Angular and React, which gave the base for doing the comparative analysis in order to find the differences and similarities between them. By conducting the comparative analysis of the dominant factors within Angular and React, this study gives the indication that Angular gives clear directions when developing and therefore can be well-suited to both experienced developers but also beginners. -

Npm Packages As Ingredients: a Recipe-Based Approach
npm Packages as Ingredients: a Recipe-based Approach Kyriakos C. Chatzidimitriou, Michail D. Papamichail, Themistoklis Diamantopoulos, Napoleon-Christos Oikonomou, and Andreas L. Symeonidis Electrical and Computer Engineering Dept., Aristotle University of Thessaloniki, Thessaloniki, Greece fkyrcha, mpapamic, thdiaman, [email protected], [email protected] Keywords: Dependency Networks, Software Reuse, JavaScript, npm, node. Abstract: The sharing and growth of open source software packages in the npm JavaScript (JS) ecosystem has been exponential, not only in numbers but also in terms of interconnectivity, to the extend that often the size of de- pendencies has become more than the size of the written code. This reuse-oriented paradigm, often attributed to the lack of a standard library in node and/or in the micropackaging culture of the ecosystem, yields interest- ing insights on the way developers build their packages. In this work we view the dependency network of the npm ecosystem from a “culinary” perspective. We assume that dependencies are the ingredients in a recipe, which corresponds to the produced software package. We employ network analysis and information retrieval techniques in order to capture the dependencies that tend to co-occur in the development of npm packages and identify the communities that have been evolved as the main drivers for npm’s exponential growth. 1 INTRODUCTION Given that dependencies and reusability have be- come very important in today’s software develop- The popularity of JS is constantly increasing, and ment process, npm registry has become a “must” along is increasing the popularity of frameworks for place for developers to share packages, defining code building server (e.g. -

Choosing the Right Javascript Framework for Your Next Web
Choosing the Right JavaScript Framework for Your Next Web Application by Brandon Satrom © 2017 Progress. All Rights Reserved. All Rights © 2017 Progress. 2018 WHITEPAPER Table of Contents The Current State of Web Frameworks / 3 Tooling Considerations / 22 Evaluation Criteria / 5 UI & Component Libraries / 22 Ecosystem Considerations / 7 IDE & Tooling Support / 23 History & Longevity / 7 Companion & CLI Tools / 24 Popularity / 9 Enterprise Considerations / 26 Corporate Support / 11 Licensing / 26 Community & Ecosystem / 12 Support & Upgrade Paths / 27 Framework Considerations / 13 Security / 29 Getting Started Experience / 13 Talent Pool & Resources / 30 Skill Requirements / 15 Making a Choice / 33 Completeness of Offering / 17 Size & Performance / 18 Beyond the Browser Options / 21 © 2018 Progress. All Rights Reserved. All Rights © 2018 Progress. Progress / Kendo UI 2 The state of web application development has changed drastically in the past ten years. These changes have been spurred on by greater bandwidth for many, more powerful and feature-rich browsers. The result is a thriving web ecosystem with sites, apps and experiences that would have been hard to imagine a decade ago. And yet, for many developers, this ecosystem often feels like a bazaar, stuffed with libraries and frameworks that do anything and everything one could imagine. For every need there are a dozen options to choose from, and with new stalls (libraries) opening every day, it’s no wonder many of us pine for the days when starting a new project was as simple as dropping jQuery in a script tag. The Current State of Web Frameworks There’s no doubt that the web has grown in complexity, and our development tooling options have grown along with it. -

Enhancement of a Vulnerability Checker for Software Libraries with Similarity Metrics Based on File-Hashes
Gottfried Wilhelm Leibniz Universität Hannover Faculty of Electrical Engineering and Computer Science Institute of Practical Computer Science Software Engineering Group Enhancement of a Vulnerability Checker for Software Libraries with Similarity Metrics based on File-Hashes Bachelor Thesis in Computer Science by Huu Kim Nguyen First Examiner: Prof. Dr. Kurt Schneider Second Examiner: Dr. Jil Klünder Supervisor: M.Sc. Fabien Patrick Viertel Hannover, March 19, 2020 ii Declaration of Independence I hereby certify that I have written the present bachelor thesis independently and without outside help and that I have not used any sources and aids other than those specified in the work. The work has not yet been submitted to any other examination office in the same or similar form. Hannover, March 19, 2020 _____________________________________ Huu Kim Nguyen iii iv Abstract This bachelor thesis presents a software which checks a software project for libraries that have security vulnerabilities so the user is notified to update them. External software libraries and frameworks are used in websites and other software to provide new functionality. Using outdated and vulnerable libraries poses a large risk to developers and users. Finding vulnerabilities should be part of the software development. Manually finding vulnerable libraries is a time consuming process. The solution presented in this thesis is a vulnerability checker which scans the project library for any libraries that contain security vulnerabilities provided that the software project is written in Java or in JavaScript. It uses hash signatures obtained from these libraries to check against a database that has hash signatures of libraries that are known to have security vulnerabilities.