Branch Prediction 9 Philip G
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Branch Prediction Side Channel Attacks
Predicting Secret Keys via Branch Prediction Onur Ac³i»cmez1, Jean-Pierre Seifert2;3, and C»etin Kaya Ko»c1;4 1 Oregon State University School of Electrical Engineering and Computer Science Corvallis, OR 97331, USA 2 Applied Security Research Group The Center for Computational Mathematics and Scienti¯c Computation Faculty of Science and Science Education University of Haifa Haifa 31905, Israel 3 Institute for Computer Science University of Innsbruck 6020 Innsbruck, Austria 4 Information Security Research Center Istanbul Commerce University EminÄonÄu,Istanbul 34112, Turkey [email protected], [email protected], [email protected] Abstract. This paper presents a new software side-channel attack | enabled by the branch prediction capability common to all modern high-performance CPUs. The penalty payed (extra clock cycles) for a mispredicted branch can be used for cryptanalysis of cryptographic primitives that employ a data-dependent program flow. Analogous to the recently described cache-based side-channel attacks our attacks also allow an unprivileged process to attack other processes running in parallel on the same processor, despite sophisticated partitioning methods such as memory protection, sandboxing or even virtualization. We will discuss in detail several such attacks for the example of RSA, and experimentally show their applicability to real systems, such as OpenSSL and Linux. More speci¯cally, we will present four di®erent types of attacks, which are all derived from the basic idea underlying our novel side-channel attack. Moreover, we also demonstrate the strength of the branch prediction side-channel attack by rendering the obvious countermeasure in this context (Montgomery Multiplication with dummy-reduction) as useless. -

BRANCH PREDICTORS Mahdi Nazm Bojnordi Assistant Professor School of Computing University of Utah
BRANCH PREDICTORS Mahdi Nazm Bojnordi Assistant Professor School of Computing University of Utah CS/ECE 6810: Computer Architecture Overview ¨ Announcements ¤ Homework 2 release: Sept. 26th ¨ This lecture ¤ Dynamic branch prediction ¤ Counter based branch predictor ¤ Correlating branch predictor ¤ Global vs. local branch predictors Big Picture: Why Branch Prediction? ¨ Problem: performance is mainly limited by the number of instructions fetched per second ¨ Solution: deeper and wider frontend ¨ Challenge: handling branch instructions Big Picture: How to Predict Branch? ¨ Static prediction (based on direction or profile) ¨ Always not-taken ¨ Target = next PC ¨ Always taken ¨ Target = unknown clk direction target ¨ Dynamic prediction clk PC + ¨ Special hardware using PC NPC 4 Inst. Memory Instruction Recall: Dynamic Branch Prediction ¨ Hardware unit capable of learning at runtime ¤ 1. Prediction logic n Direction (taken or not-taken) n Target address (where to fetch next) ¤ 2. Outcome validation and training n Outcome is computed regardless of prediction ¤ 3. Recovery from misprediction n Nullify the effect of instructions on the wrong path Branch Prediction ¨ Goal: avoiding stall cycles caused by branches ¨ Solution: static or dynamic branch predictor ¤ 1. prediction ¤ 2. validation and training ¤ 3. recovery from misprediction ¨ Performance is influenced by the frequency of branches (b), prediction accuracy (a), and misprediction cost (c) Branch Prediction ¨ Goal: avoiding stall cycles caused by branches ¨ Solution: static or dynamic branch predictor ¤ 1. prediction ¤ 2. validation and training ¤ 3. recovery from misprediction ¨ Performance is influenced by the frequency of branches (b), prediction accuracy (a), and misprediction cost (c) ��� ���� ��� 1 + �� ������� = = 234 = ��� ���� ���567 1 + 1 − � �� Problem ¨ A pipelined processor requires 3 stall cycles to compute the outcome of every branch before fetching next instruction; due to perfect forwarding/bypassing, no stall cycles are required for data/structural hazards; every 5th instruction is a branch. -

MIPS® Architecture for Programmers Volume I-B: Introduction to the Micromips32™ Architecture, Revision 5.03
MIPS® Architecture For Programmers Volume I-B: Introduction to the microMIPS32™ Architecture Document Number: MD00741 Revision 5.03 Sept. 9, 2013 Unpublished rights (if any) reserved under the copyright laws of the United States of America and other countries. This document contains information that is proprietary to MIPS Tech, LLC, a Wave Computing company (“MIPS”) and MIPS’ affiliates as applicable. Any copying, reproducing, modifying or use of this information (in whole or in part) that is not expressly permitted in writing by MIPS or MIPS’ affiliates as applicable or an authorized third party is strictly prohibited. At a minimum, this information is protected under unfair competition and copyright laws. Violations thereof may result in criminal penalties and fines. Any document provided in source format (i.e., in a modifiable form such as in FrameMaker or Microsoft Word format) is subject to use and distribution restrictions that are independent of and supplemental to any and all confidentiality restrictions. UNDER NO CIRCUMSTANCES MAY A DOCUMENT PROVIDED IN SOURCE FORMAT BE DISTRIBUTED TO A THIRD PARTY IN SOURCE FORMAT WITHOUT THE EXPRESS WRITTEN PERMISSION OF MIPS (AND MIPS’ AFFILIATES AS APPLICABLE) reserve the right to change the information contained in this document to improve function, design or otherwise. MIPS and MIPS’ affiliates do not assume any liability arising out of the application or use of this information, or of any error or omission in such information. Any warranties, whether express, statutory, implied or otherwise, including but not limited to the implied warranties of merchantability or fitness for a particular purpose, are excluded. Except as expressly provided in any written license agreement from MIPS or an authorized third party, the furnishing of this document does not give recipient any license to any intellectual property rights, including any patent rights, that cover the information in this document. -

18-741 Advanced Computer Architecture Lecture 1: Intro And
Computer Architecture Lecture 10: Branch Prediction Prof. Onur Mutlu ETH Zürich Fall 2017 25 October 2017 Mid-Semester Exam November 30 In class Questions similar to homework questions 2 High-Level Summary of Last Week SIMD Processing Array Processors Vector Processors SIMD Extensions Graphics Processing Units GPU Architecture GPU Programming 3 Agenda for Today & Tomorrow Control Dependence Handling Problem Six solutions Branch Prediction Other Methods of Control Dependence Handling 4 Required Readings McFarling, “Combining Branch Predictors,” DEC WRL Technical Report, 1993. Required T. Yeh and Y. Patt, “Two-Level Adaptive Training Branch Prediction,” Intl. Symposium on Microarchitecture, November 1991. MICRO Test of Time Award Winner (after 24 years) Required 5 Recommended Readings Smith and Sohi, “The Microarchitecture of Superscalar Processors,” Proceedings of the IEEE, 1995 More advanced pipelining Interrupt and exception handling Out-of-order and superscalar execution concepts Recommended Kessler, “The Alpha 21264 Microprocessor,” IEEE Micro 1999. Recommended 6 Control Dependence Handling 7 Control Dependence Question: What should the fetch PC be in the next cycle? Answer: The address of the next instruction All instructions are control dependent on previous ones. Why? If the fetched instruction is a non-control-flow instruction: Next Fetch PC is the address of the next-sequential instruction Easy to determine if we know the size of the fetched instruction If the instruction that is fetched is a control-flow -

State of the Art Regarding Both Compiler Optimizations for Instruction Fetch, and the Fetch Architectures for Which We Try to Optimize Our Applications
¢¡¤£¥¡§¦ ¨ © ¡§ ¦ £ ¡ In this work we are trying to increase fetch performance using both software and hardware tech- niques, combining them to obtain maximum performance at the minimum cost and complexity. In this chapter we introduce the state of the art regarding both compiler optimizations for instruction fetch, and the fetch architectures for which we try to optimize our applications. The first section introduces code layout optimizations. The compiler can influence instruction fetch performance by selecting the layout of instructions in memory. This determines both the conflict rate of the instruction cache, and the behavior (taken or not taken) of conditional branches. We present an overview of the different layout algorithms proposed in the literature, and how our own algorithm relates to them. The second section shows how instruction fetch architectures have evolved from pipelined processors to the more aggressive wide issue superscalars. This implies increasing fetch perfor- mance from a single instruction every few cycles, to one instruction per cycle, to a full basic block per cycle, and finally to multiple basic blocks per cycle. We emphasize the description of the trace cache, as it will be the reference architecture in most of our work. 2.1 Code layout optimizations The mapping of instruction to memory is determined by the compiler. This mapping determines not only the code page where an instruction is found, but also the cache line (or which set in a set associative cache) it will map to. Furthermore, a branch will be taken or not taken depending on the placement of the successor basic blocks. By mapping instructions in a different order, the compiler has a direct impact on the fetch engine performance. -

Branch Prediction for Network Processors
BRANCH PREDICTION FOR NETWORK PROCESSORS by David Bermingham, B.Eng Submitted in partial fulfilment of the requirements for the Degree of Doctor of Philosophy Dublin City University School of School of Electronic Engineering Supervisors: Dr. Xiaojun Wang Prof. Lingling Sun September 2010 I hereby certify that this material, which I now submit for assessment on the programme of study leading to the award of Doctor of Philosophy is entirely my own work, that I have exercised reasonable care to ensure that the work is original, and does not to the best of my knowledge breach any law of copy- right, and has not been taken from the work of others save and to the extent that such work has been cited and acknowledged within the text of my work. Signed: David Bermingham (Candidate) ID: Date: TABLE OF CONTENTS Abstract vii List of Figures ix List of Tables xii List of Acronyms xiv List of Peer-Reviewed Publications xvi Acknowledgements xviii 1 Introduction 1 1.1 Network Processors . 1 1.2 Trends Within Networks . 2 1.2.1 Bandwidth Growth . 2 1.2.2 Network Technologies . 3 1.2.3 Application and Service Demands . 3 1.3 Network Trends and Network Processors . 6 1.3.1 The Motivation for This Thesis . 7 1.4 Research Objectives . 9 1.5 Thesis Structure . 10 iii 2 Technical Background 12 2.1 Overview . 12 2.2 Networks . 13 2.2.1 Network Protocols . 13 2.2.2 Network Technologies . 14 2.2.3 Router Architecture . 17 2.3 Network Processors . 19 2.3.1 Intel IXP-28XX Network Processor . -

Trends in Processor Architecture
A. González Trends in Processor Architecture Trends in Processor Architecture Antonio González Universitat Politècnica de Catalunya, Barcelona, Spain 1. Past Trends Processors have undergone a tremendous evolution throughout their history. A key milestone in this evolution was the introduction of the microprocessor, term that refers to a processor that is implemented in a single chip. The first microprocessor was introduced by Intel under the name of Intel 4004 in 1971. It contained about 2,300 transistors, was clocked at 740 KHz and delivered 92,000 instructions per second while dissipating around 0.5 watts. Since then, practically every year we have witnessed the launch of a new microprocessor, delivering significant performance improvements over previous ones. Some studies have estimated this growth to be exponential, in the order of about 50% per year, which results in a cumulative growth of over three orders of magnitude in a time span of two decades [12]. These improvements have been fueled by advances in the manufacturing process and innovations in processor architecture. According to several studies [4][6], both aspects contributed in a similar amount to the global gains. The manufacturing process technology has tried to follow the scaling recipe laid down by Robert N. Dennard in the early 1970s [7]. The basics of this technology scaling consists of reducing transistor dimensions by a factor of 30% every generation (typically 2 years) while keeping electric fields constant. The 30% scaling in the dimensions results in doubling the transistor density (doubling transistor density every two years was predicted in 1975 by Gordon Moore and is normally referred to as Moore’s Law [21][22]). -

MIPS32™ Architecture for Programmers Volume I: Introduction to the MIPS32™ Architecture
MIPS32™ Architecture For Programmers Volume I: Introduction to the MIPS32™ Architecture Document Number: MD00082 Revision 0.95 March 12, 2001 MIPS Technologies, Inc. 1225 Charleston Road Mountain View, CA 94043-1353 Copyright © 2001 MIPS Technologies, Inc. All rights reserved. Unpublished rights reserved under the Copyright Laws of the United States of America. This document contains information that is proprietary to MIPS Technologies, Inc. (“MIPS Technologies”). Any copying, modifyingor use of this information (in whole or in part) which is not expressly permitted in writing by MIPS Technologies or a contractually-authorized third party is strictly prohibited. At a minimum, this information is protected under unfair competition laws and the expression of the information contained herein is protected under federal copyright laws. Violations thereof may result in criminal penalties and fines. MIPS Technologies or any contractually-authorized third party reserves the right to change the information contained in this document to improve function, design or otherwise. MIPS Technologies does not assume any liability arising out of the application or use of this information. Any license under patent rights or any other intellectual property rights owned by MIPS Technologies or third parties shall be conveyed by MIPS Technologies or any contractually-authorized third party in a separate license agreement between the parties. The information contained in this document constitutes one or more of the following: commercial computer software, commercial -

MCST~8 Assembly Language Programming Manual PRELIMINARY EDITION
INTEL CORP. 3065 Bowers Avenue, Santa Clara, California 95051 • (408) 246-7501 MCST~8 Assembly Language Programming Manual PRELIMINARY EDITION November 1973 © Intel Corporation 1973 -- TABLE OF CONTENTS -- 8008 PROGRAMMING MANUAL Page No. 1.0 INTRODUCTION 1-1 2.0 COMPUTER ORGANIZATION 2-1 2.1 THE CENTRAL PROCESSING UNIT 2-3 2.1.1 WORKING REGISTERS 2-3 2. 1 .2 THE STACK 2-5 2.1.3 ARITHMETIC AND LOGIC UNIT 2-7 2.2 MEMORY 2-8 2.3 COMPUTER PROGRAM REPRESENTATION IN MEMORY 2-8 2.4 MEMORY ADDRESSING 2-10 2.4.1 DIRECT ADDRESSING 2-11 2 .4 .2 INDEXED ADDRESSING 2-13 2.4.3 INDIRECT ADDRESSING 2-13 2.4.4 IMMEDIATE ADDRESSING 2-14 2.4.5 SUBROUTINES AND USE OF THE STACK FOR ADDRESSING 2-15 2.5 CONDITION BITS 2-18 2.5.1 CARRY BIT 2-18 2 .5 • 2 SIGN BIT 2-19 2 .5 . 3 ZERO BIT 2-19 2 • 5 . 4 PARITY BIT 2-20 3.{) THE 8008 INSTRUCTION SET 3-1 3.1 ASSEMBLY LANG UAGE 3-1 3.1.1 HOW ASSEMBLY LANGUAGE IS USED 3-1 3.1.2 STATEMENT MNEMONICS 3-4 3 • 1. 3 LABEL FIELD 3-5 3.1.4 CODE FIELD 3-7 3 • 1 .5 OPERAND FIELD 3-7 3.1.6 COMMENT FIELD 3-15 i Page No. 3.2 DATA STATEMENTS 3-15 3.2.1 TWO'S COMPLEMENT 3-16 3.2.2 DB DEFINE BYTE(S) OF DATA 3-20 3.2.3 DW DEFINE WORD (TWO BYTES) OF DATA 3-21 3.2.4 DS DEFINE STORAGE (BYTES) 3-22 3.3 SINGLE REGISTER INSTRUCTIONS 3-23 3.3.1 INR INCREMENT REGISTER 3-24 3.3.2 DCR DECREMENT REGISTER 3-24 3.4 MOV INSTRUCTION 3-25 3.5 REGISTER OR MEMORY TO ACCUMULATOR INSTRUCTIONS 3-28 3.5.1 ADD ADD REGISTER OR MEMORY TO ACCUMULATOR 3-29 3.5.2 ADC ADD REGISTI:R OR MEMORY TO ACCUMULATOR WITH CARRY 3-31 3.5.3 SUB SUBTRACT REGISTER OR MEMORY -

Notes on Usage of the RX Family C/C++ Compiler V.1.00 Release 01 and Corrections in the User's Manual
R0C5RX00XSW01R-ERN100630 Notes on Usage of the RX Family C/C++ Compiler V.1.00 Release 01 and Corrections in the User's Manual There are notes on usage of the RX Family C/C++ compiler V.1.00 Release 01 and corrections to be made in the bundled user's manual (REJ10J2062-0100) as listed below. 1. Notes on Usage 1.1 Note on a Case of the C1804 Message [C/C++ Compiler] When the int_to_short option is specified and a file including a C standard header is compiled as C++ or EC++, the compiler may show the C1804(W) message. In this case, simply ignore the message because there are no problems. [NOTE] In compilation of C++ or EC++, the int_to_short option will be invalid. Data that are shared between C and C++ (EC++) program must be declared as the long or short type rather than as the int type. 1.2 Note on using MVTC or POPC instructions [Assembler] In the assembly language, the program counter (PC) cannot be specified for MVTC or POPC instructions. 1.3 Note on the delete Option for Linkage [Optimizing linkage editor] When a function symbol is removed by the delete option, its following function in the source program is not allowed to have a breakpoint at its function name on the editor in your debugging. If you would like to set a breakpoint at the function entrance, set the breakpoint via the Label window or at the prologue code of the function. 1.4 Notes of Paths Name and File Name [Optimizing linkage editor] In the specification of the optimizing linkage editor, the parentheses "(" and ")" signs for the path names and file names cannot be used because these signs are used for the option descriptions. -
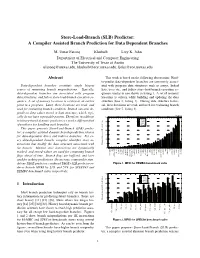
(SLB) Predictor: a Compiler Assisted Branch Prediction for Data Dependent Branches
Store-Load-Branch (SLB) Predictor: A Compiler Assisted Branch Prediction for Data Dependent Branches M. Umar Farooq Khubaib Lizy K. John Department of Electrical and Computer Engineering The University of Texas at Austin [email protected], [email protected], [email protected] Abstract This work is based on the following observation: Hard- to-predict data-dependent branches are commonly associ- Data-dependent branches constitute single biggest ated with program data structures such as arrays, linked source of remaining branch mispredictions. Typically, lists, trees etc., and follow store-load-branch execution se- data-dependent branches are associated with program quence similar to one shown in listing 1. A set of memory data structures, and follow store-load-branch execution se- locations is written while building and updating the data quence. A set of memory locations is written at an earlier structure (line 2, listing 1). During data structure traver- point in a program. Later, these locations are read, and sal, these locations are read, and used for evaluating branch used for evaluating branch condition. Branch outcome de- condition (line 7, listing 1). pends on data values stored in data structure, which, typi- 52 50 53 cally do not have repeatable pattern. Therefore, in addition 35 Gshare to history-based dynamic predictor, we need a different kind 30 YAGS BiMode of predictor for handling such branches. TAGE 25 This paper presents Store-Load-Branch (SLB) predic- 20 tor; a compiler-assisted dynamic branch prediction scheme for data-dependent direct and indirect branches. For ev- 15 ery data-dependent branch, compiler identifies store in- 10 5 structions that modify the data structure associated with Mispredictions per 1K instructions the branch. -

Energy Efficient Branch Prediction
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by University of Hertfordshire Research Archive Energy Efficient Branch Prediction Michael Andrew Hicks A thesis submitted in partial fulfilment of the requirements of the University of Hertfordshire for the degree of Doctor of Philosophy December 2007 To my family and friends. Contents 1 Introduction 1 1.1 Thesis Statement . 1 1.2 Motivation and Energy Efficiency . 1 1.3 Branch Prediction . 3 1.4 Contributions . 4 1.5 Dissertation Structure . 5 2 Energy Efficiency in Modern Processor Design 7 2.1 Transistor Level Power Dissipation . 7 2.1.1 Static Dissipation . 8 2.1.2 Dynamic Dissipation . 9 2.1.3 Energy Efficiency Metrics . 9 2.2 Transistor Level Energy Efficiency Techniques . 10 2.2.1 Clock Gating and Vdd Gating . 10 2.2.2 Technology Scaling . 11 2.2.3 Voltage Scaling . 11 2.2.4 Logic Optimisation . 11 2.3 Architecture & Software Level Efficiency Techniques . 11 2.3.1 Activity Factor Reduction . 12 2.3.2 Delay Reduction . 12 2.3.3 Low Power Scheduling . 12 2.3.4 Frequency Scaling . 13 2.4 Branch Prediction . 13 2.4.1 The Branch Problem . 13 2.4.2 Dynamic and Static Prediction . 14 2.4.3 Dynamic Predictors . 15 2.4.4 Power Consumption . 18 2.5 Summary . 18 3 Related Techniques 20 3.1 The Prediction Probe Detector (Hardware) . 20 3.1.1 Implementation . 20 3.1.2 Pipeline Gating . 22 i 3.2 Software Based Approaches . 23 3.2.1 Hinting and Hint Instructions .