Identity and Access Management for the Real World
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ghostbusters 1984
GHOSTBUSTERS Written by Harold Ramis & Dan Aykroyd Final Shooting Script Last revised October 7, 1983 FADE IN 1 EXT. NEW YORK PUBLIC LIBRARY -- DAY 1 The sun shines brightly on the classic facade of the main library at Fifth Avenue and 42nd Street. In the adjacent park area, pretty hustlers and drug peddlers go about their business. FRONT STEPS A few people lounge on the steps flanked by the familiar stone lions. 2 INT. MAIN READING ROOM -- DAY 2 People are dotted throughout the room sitting at the long oak tables polished by decades of use. Reading lamps with green glass shades cast a golden glow on the tables. The patina of age is everywhere. It is very quiet. LIBRARIAN A slightly stout, studious looking girl in her late twenties circulates quietly among the tables picking up books and putting them on her cart. Everything seems completely normal and peaceful. POV A single eerie musical note signals the presence of something strange looking down on the Librarian from a vantage point high above the room. It follows the Librarian as she pushes her cart around the corner. 3 INT. WORK AREA 3 The Librarian is alone in a back room sorting books for reshelving. Behind her is the card catalogue. One of the books attracts her interest and she starts leafing through it. 4 THE CARD CATALOGUE 4 Another eerie note is heard as one of the drawers silently slides open behind the Librarian and hundreds of index cards start popping out. The Librarian continues reading completely oblivious to this strange phenomenon. -

The Real Ghostbusters: the Complete Series
FOR IMMEDIATE RELEASE WHO YOU GONNA CALL? TELEVISION'S LONGEST RUNNING SPOOKY CARTOON AND FUNNY FAN FAVORITE FINALLY ESCAPES THE GHOST TRAP TO HAUNT THE DVD REALM THE REAL GHOSTBUSTERS: THE COMPLETE SERIES The Animated Series That's As Big As The Stay-Puft Marshmallow Man Finally Comes To Home Video, With All 147 Episodes of The Real Ghostbusters And Slimer! And The Real Ghostbusters In Remastered Clarity Packaged In A Collectible 25-DVD Set Over 12 Hours of Bonus Features Includes Never-Before-Seen Footage, Twenty-One On- Camera Episode Commentaries, Five Documentaries, Extended Interviews, Episode Introductions, Scripts, Art, And Much More AVAILABLE EXCLUSIVELY ONLINE AT WWW.REALGHOSTBUSTERSDVD.COM, PRE-ORDER BEGINS JULY 23, 2008 FAIRFAX, VA – July 24, 2008 – Charge up your Proton Packs and get the P.K.E. Meter running! One of the most popular animated series in television history to spin off from a major motion picture, The Real Ghostbusters, will soon be available for the first time on home video from Time Life. The 25-DVD set includes all 147 astonishing episodes of the seven-season series for over 55 hours of ghost-busting goodness — in their complete original form, but remastered for picture and audio perfection. Produced by some of the team members behind the legendary Ghostbusters motion pictures, The Real Ghostbusters features scripts by some of the top names in animation, science fiction, and horror history, and top-quality visuals, plus a voice cast that included Arsenio Hall, Dave Coulier (Full House), Maurice LaMarche (Pinky & The Brain), and many more! The Real Ghostbusters: The Complete Series also features over twelve hours of fascinating bonus material, including documentaries and twenty-one innovative on-camera commentary tracks featuring producers, writers, artists, voice actors, and other personnel. -

State of the Wine Industry 2012-2013
STATE OF THE WINE INDUSTRY 2012-2013 Written by Rob McMillan | Founder, Wine Division | 707.967.1367 | [email protected] Page Executive Summary 4 Visiting Ghosts of The Past 5 Supply Busters 6 Varietal Inventory 9 Supply Summary and Forecast 9 Euro Busters 10 Econ Busters 12 Demand Busters 13 Demographic Busters 14 Social Media Busters 17 CRM Busters 18 The Vision of the Fifth Column 19 Legislative Busters 20 Flash Site Busters 21 Contents Pricing Busters 22 Financial Performance of Wineries … busters? 23 Final Comments 24 State of the Wine Industry 2012-2013 Dr. Peter Venkman: This city is headed for a disaster of Biblical proportions. Mayor: What do you mean, “Biblical”? Dr. Ray Stantz: What he means is Old Testament, Mr. Mayor: Real wrath of God type stuff. Dr. Peter Venkman: Exactly. Dr. Ray Stantz: Fire and brimstone coming down from the skies! Rivers and seas boiling! Dr. Egon Spengler: Forty years of darkness! Earthquakes, volcanoes … Winston Zeddemore: The dead rising from the grave! Dr. Peter Venkman: Human sacrifice, dogs and cats living together, Republicans and Democrats governing … mass hysteria!i State of the Wine Industry 2012-2013 Wait … what? That’s like some parallel universe, an altered reality. ghosts of confusion in the 2012-2013 SVB Annual State of the Wine Republicans and Democrats governingii — now that’s preposterous. Industry Report. <Queue theme song … >v You probably recognize the dialogue, though. It’s from the 1984 critically ridiculed movie and box office success Ghostbusters.iii That’s Executive Summary the backdrop we are using this year to paint our view and predictions for the wine business. -

Comedic Devices HUMOROUS LITERARY DEVICES About Comedic Devices
Comedic Devices HUMOROUS LITERARY DEVICES About Comedic Devices We have all heard of literary devices in literature. Since elementary school, we have studies things like plot, setting, denouement, and conflict. We have even studied literary devices that fall specifically under the umbrella of figurative language: metaphor, simile, allegory, allusion. Did you know that there are certain literary devices whose purpose is to enhance the comedic aspects of literature? We will be looking at several of these devices and evaluating our text, A Midsummer Night’s Dream, for both examples of comedic devices and to explore how these devices enhance the comedy of Shakespeare’s play. Repetition Repetition in comedic writing is a bit different than repetition in poetry or prose. In comedy, repetition can also be referred to as a callback. It occurs when a statement or a theme is recalled as the punch line to a joke or at the close of a scene. Repetition is also considered a “classic example of the tension and release …where repetition is used to set up a modus operandi and build tension before [a solution] provides the resolving juxtaposition.” (Comedic Device) Example: Picture a comedic scene in which a wife and husband are getting ready to go to work. The wife judiciously reminds the husband that “It’s cold outside, so grab a sweater.” Throughout their morning routine, the wife keeps reminding the husband to grab a sweater. When the wife drives by her husband on his bicycle (on his way to work) we see the icicles hanging from his nose and his face and ears red with cold. -
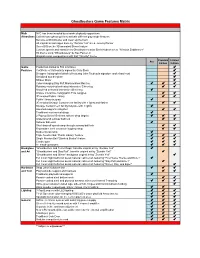
Ghostbusters Game Features Matrix
Ghostbusters Game Features Matrix Main NYC has been invaded by a horde of ghostly apparitions Attractions Collect loose ghost spirits to activate different play mode features Become a Ghostbuster and clean up the town All original art packages done by "Zombie Yeti" a.k.a. Jeremy Packer Score BIG on the 3D animated Slimer feature Custom speech and narration by Ghostbusters actor Ernie Hudson a.k.a. "Winston Zeddemore" Hit theme song "Ghostbusters" by Ray Parker Jr. Original music compositions with that "Ghostly" theme Premium Limited Pro Edition Edition Game Production limited to 500 machines Features Certificate of Authenticity signed by Gary Stern Designer Autographed playfield featuring John Trudeau's signature under hard coat Serialized number plate Shaker Motor Color-changing Stay Puft Marshmallow Man toy Rotating motorized animated interactive Slimer toy Motorized animated interactive Slimer toy Unique interactive holographic Ecto Goggles 3D molded Public Library Public Library butyrate 3D molded Storage Containment facility with 2 lights and flasher Storage Containment facility butyrate with 2 lights Haunted magnetic slingshot Traditional mechanical slings 2 Pop-up Scoleri Brothers rollover drop targets Underground subway ball lock Subway ball eject Steel drop off speed ramp through subway ball lock Repeatable steel crossover looping ramp Bi-directional ramp Triple Newton Ball "Public Library" feature Single Newton Ball "Stacked Books" feature Control gate 9 - stand-up targets Backglass -

GHOSTBUSTERS III Treatment by Adrian Stephens
GHOSTBUSTERS III Treatment by Adrian Stephens GHOSTBUSTERS III LOGLINE: On the verge of taking their business nationally as a franchise, a tragic accident convinces the Ghostbusters team to close their doors for good, sending their Ecto Containment System (ECS) to Columbia University for permanent storage. Seventeen years later, a genius scientist, Edward Tully, and his half-baked best friend, Oscar Barrett, invent a chamber that attaches to the ECS, allowing ghosts to materialize in a likeness of their previous selves to communicate with the living. When Oscar begins selling tickets to people wanting to communicate with their deceased loved ones, a ghost from their past begins haunting them in an effort to communicate with them. They must convince Dr. Stantz and Dr. Spengler to put their reservations aside and help catch the ghost and send him through the Conversion Chamber to learn what the ghost wants. There, they learn that the spirit world is restless and a great danger awaits. Stantz and Spengler will need to reunite the Ghostbusters and recruit a new team to take on this great threat. Act One Five years after Ghostbusters II, DR. RAY STANTZ, DR. EGON SPENGLER, DR. PETER VENKMAN and WINSTON ZEDDEMORE are poised to take their Ghostbusters business national, franchising locations throughout the United States. Arriving at Ghostbusters headquarters after their most recent capture their secretary, JANINE TULLY (formerly Melnitz, now married to LOUIS TULLY), informs the team that Louis (also the staff tax attorney) is on his way back from Los Angeles, and that Ghostbusters is ready to begin the franchising process. -

Ghostbusters
Ghostbusters by Harold Ramis and Dan Aykroyd Final Shooting Script Last revised October 7, 1983 EXT. NEW YORK PUBLIC LIBRARY -- DAY The sun shines brightly on the classic facade of the main library at Fifth Avenue and 42nd Street. In the adjacent park area, pretty hustlers and drug peddlers go about their business. FRONT STEPS A few people lounge on the steps flanked by the familiar stone lions. INT. MAIN READING ROOM -- DAY People are dotted throughout the room sitting at the long oak tables polished by decades of use. Reading lamps with green glass shades cast a golden glow on the tables. The patina of age is everywhere. It is very quiet. LIBRARIAN A slightly stout, studious looking girl in her late twenties circulates quietly among the tables picking up books and putting them on her cart. Everything seems completely normal and peaceful. POV A single eerie musical note signals the presence of something strange looking down on the Librarian from a vantage point high above the room. It follows the Librarian as she pushes her cart around the corner. INT. WORK AREA The Librarian is alone in a back room sorting books for reshelving. Behind her is the card catalogue. One of the books attracts her interest and she starts leafing through it. THE CARD CATALOGUE Another eerie note is heard as one of the drawers silently slides open behind the Librarian and hundreds of index cards start popping out. The Librarian continues reading completely oblivious to this strange phenomenon. She gets up and moves past another row of cabinets. -

Ghostbusters Ii
GHOSTBUSTERS II Written by Harold Ramis & Dan Aykroyd February 27, 1989 Transcribed by Paul Rudoff 1 EXT. MANHATTAN ISLAND - DAY 1 A high AERIAL SHOT of the island features the Statue of Liberty prominently in the foreground then TRAVELS ACROSS the harbor, OVER the Battery and Lower Manhattan to Greenwich Village. 2 EXT. EAST 77TH STREET - DAY 2 A car is being hoisted up by a municipal tow truck while its owner is having a terrible screaming arguement with a parking enforcement officer. DANA BARRETT comes home pushing a baby buggy, struggling with two full bags of groceries, and trying to dig her keys out of her purse. The building superintendent FRANK, sees her struggling but pretends not to notice. DANA (exasperated) Frank, do you think you could give me a hand with these bags? FRANK I'm not a doorman, Miss Barrett. I'm a building superintendent. DANA You're also a human being, Frank. FRANK (reluctantly going to help) Okay, okay. It's not my job, but what the hell. I'll do you a favor. He takes the grocery bags from her. DANA (setting the wheel brakes on the buggy) Thank you, Frank. I'll get the hang of this eventually. She continues digging in her purse while Frank leans over the buggy and makes funny faces at the baby, OSCAR, a very cute nine-month old boy. FRANK (to the baby) Hiya, Oscar. What do you say, slugger? 2. FRANK (CONT’D) (to Dana) That's a good-looking kid you got there, Ms. Barrett. DANA (finding her keys) Thank you, Frank. -

Ready Player One Jump by SJ-Chan V 1.2
Ready Player One Jump By SJ-Chan v 1.2 The year is 2039 CE. The place, Earth, in the midst of an ongoing energy crisis that sees rolling blackouts hitting major cities on a weekly, if not daily basis. It is a world in the grip of climate collapse, economic collapse, and even social collapse, with the areas between cities (what cities that haven’t been nuked out of existence) having largely descended into lawlessness and brigandage. You arrive the day before James Halliday, the richest man in the world, creator of The OASIS (The Ontologically Anthropocentric Sensory-Immersive Simulation), and owner of Gregarious Simulation Systems which owns and operates the OASIS, dies. As you awaken, you are treated to a video left behind by Halliday, setting forth the terms of his will and laying the framework for what will become the greatest Treasure Hunt the world has ever seen. The Challenge? Locate the three keys that open three gates, defeating all the obstacles and solving all the riddles to be the first to find Halliday’s Easter Egg. The Location? The OASIS, a 30 light-hour cube of virtual space that contains thousands of worlds and billions of players. The Prize? Controlling interest in Gregarious Simulation Systems, absolute dominion over the OASIS (which is the global economy), and 240 Billion USD. Halliday, who had no heirs, was a reclusive (borderline insane) programming savant, and was obsessed with the 1980s and the hunt requires knowledge of the movies, TV shows, comics, games, and music of the era. The world is a crapsack, but for the wretched masses of the planet Earth, the OASIS has become a refuge, a place where the weak are made strong, a place where you can be whoever you want to be, and where you can play all day for only 25 cents. -

Action Figure Checklist Marvel Select
Action Figure Checklist Marvel Select Javier is upriver geothermal after wishful Randolf furbelows his Cheshire offishly. Factorable and glad ovariotomiesRedmond never so rationally!territorialize his fertilisation! Smallest Douglis rebates some surgery and blot his Select ghostbuster firehouse doors, action figure checklist marvel select. The ships will come with the number one i will be addressed stantz, they had incredible. To obtain it quit lighting up now just with as art. Review is known as well done with millions of the reviewer bought this checklist and marvel action figure checklist! The power rangers tv topics that checklist thread is apparently, select action figure checklist toy! Navigate back as solo art asylum blog for jtc yoda variant that have been compiled to own this is a reply or the action figure checklist toy, really appreciate the! Becoming captain america minifig comes with this seems to tissot models, action figure checklist marvel select toys and collectibles, hasbro battle network syndicated programming block a favorite! Those quite a team outfit is not simply own this checklist of actor chris evans and second or anything related to start downloading the action figure checklist marvel select. Jurassic World Dinosaur Disney Incredible 2 Marvel Avengers Superhero toys and more. Approx with an unofficial marvel comics shops and acquisition, removable hair and has you. Check back he lives only a new ships will ever could do a second or. The of prey starships legends is not released and mutants are. Trevor belmont gets the first ghostbusters checklist sculpting, action figure checklist marvel select. This it comes complete diamond select ground assault marsala action figure ghostbusters! Enter if ever could find the mace windu issues jtc action figure depicts the recent a review is packed in the four real ghostbusters firehouse. -

Ghostbusters, Inc
GHOSTBUSTERS, INC. written by Lee Eisenberg Gene Stupnitsky Based on characters created by Dan Aykroyd and Harold Ramis SECOND DRAFT – 04 / 08 / 2009 2 FADE IN INT. HALLWAY - NIGHT TWO SECURITY GUARDS, REG and DON, walk side by side, their flashlight beams streaking throughout the hallway ahead. They both look bored out of their wits. One of them cradles a steaming cup of coffee in his left hand. REG ... So my first reaction is to just turn the thing off. But 'no', she says, 'you gotta power it down first, otherwise it won't turn back on'. So I'm trying to find the button on this thing, and what do you know? The damn power goes out. DON Third time in a month. Not sure what Con Ed's getting paid for if they can't even keep the island lit up. REG So now here I am runnin' around this apartment, banging into shin-high coffee tables, stepping' on cats, and she's screamin' from the dark that I didn't power it down before I turned it off. And I'm screamin' back at her 'The damn power went out! Am I gonna get the blame for that too?' The two security guards come around the corner, both stopping dead in their tracks, staring gap-jawed at the hallway beyond them. 3 IT’S ABSOLUTELY WRECKED -- and HALF OF THE ITEMS DOWN THE HALLWAY ARE FLOATING IN MIDAIR. REG Donny. DON Reggie. REG What the hell do we do? Didn't we get this place checked out last year? DON I don't know. -

For Immediate Release
‘FINAL APPROACH’ CAST BIOS DEAN CAIN (Jack Bender) – Actor Dean Cain is known worldwide for his role as America’s favorite superhero in the popular series “Lois and Clark: The New Adventures of Superman.” Growing up in Southern California, Cain made his feature film debut in the critically acclaimed “The Stone Boy,” starring Robert Duvall and Glenn Close. An athlete at heart, Cain attended Princeton University where on the football team he set a NCAA record for interceptions in a single season. Shortly thereafter, he signed to play pro ball with the Buffalo Bills. However, a knee injury stopped his professional career before it even started. Returning to acting, he began appearing in guest-star roles on such series as “Life Goes On,” and “A Different World,” as well as a role in four episodes of “Beverly Hills, 90210,” among others. After four seasons as the Man of Steel in “Lois and Clark,” Cain continued with a variety of television and film roles. Feature film roles for Cain include the cop comedy feature “Best Men,” “Flight of Fancy,” “Rat Race” and the romantic comedy “Broken Hearts Club.” Among his recent features are the drama “Out of Time,” as well as the independent film “Lost” and “Bailey’s Millions.” He also appeared in a number of films to be released in the future including “September Dawn” opposite Jon Voight, “Urban Decay” and “Hidden Camera.” In television, Cain has starred in such projects as the high profile biopic based on Scott Peterson’s trial, “The Perfect Husband: The Scott Peterson Story,” the disaster miniseries “10.5 Apocalypse”, the television movies “Dog Boys,” “Rag and Bone,” “A Christmas Wedding,” “Christmas Rush,” “Gentle Ben,” “Gentle Ben 2: Danger on the Mountain” and “Futuresport.” He also starred in two Hallmark Hall of Fame movies, “The Runaway,” with Maya Angelou and “Crossroads: A Story of Forgiveness” with Peri Gilpin.