Network, Intranet & Internet
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

From Forgotten Intranet to Successful Wiki
Library Faculty Publications Library Faculty/Staff Scholarship & Research 11-5-2010 From forgotten intranet to successful wiki Darcy C. Del Bosque University of Nevada, Las Vegas, [email protected] Kristen Costello University of Nevada, Las Vegas, [email protected] Follow this and additional works at: https://digitalscholarship.unlv.edu/lib_articles Part of the Library and Information Science Commons, Organizational Communication Commons, and the Work, Economy and Organizations Commons Repository Citation Del Bosque, D. C., Costello, K. (2010). From forgotten intranet to successful wiki. Brick and Click Libraries: Proceedings of an Academic Library Symposium 77-82. Northwest Missouri State University. https://digitalscholarship.unlv.edu/lib_articles/48 This Conference Proceeding is protected by copyright and/or related rights. It has been brought to you by Digital Scholarship@UNLV with permission from the rights-holder(s). You are free to use this Conference Proceeding in any way that is permitted by the copyright and related rights legislation that applies to your use. For other uses you need to obtain permission from the rights-holder(s) directly, unless additional rights are indicated by a Creative Commons license in the record and/or on the work itself. This Conference Proceeding has been accepted for inclusion in Library Faculty Publications by an authorized administrator of Digital Scholarship@UNLV. For more information, please contact [email protected]. From Forgotten Intranet to Successful Wiki: Best Practices for Implementing an Academic Library Staff Wiki Kristen Costello Systems Librarian University of Nevada, Las Vegas Darcy Del Bosque Emerging Technologies Librarian University of Nevada, Las Vegas Abstract Communication within an academic library can be challenging. -
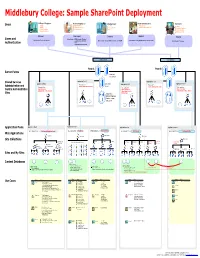
Visio-MIDD Sharepoint Architecture Design Sample.Vsd
College Colleagues Remote Employees Internal Users Farm Administrators Customers Trustees Work from Home Web Services Faculty Parents Alumni Affiliated Institutions Systems & Network Services Current Students Prospective Students External Professors Schools Abroad Staff Local Community Prospective Students Global Community Extranet Remotenet Intranet Adminet Internet Authentication = NTLM (Integrated Windows) Authentication = forms authentication using ISA Server 2006 SSO Authentication = Integrated Windows (Kerberos or NTLM) Authentication = Integrated Windows (Kerberos or NTLM) Authentication = Anonymous —or— Forms with an LDAP provider Application Pool 1 Application Pool 7 Application Pool 2 Application Pool 3 Application Pool 8 Web application: Web application: Central Administration Site Central Administration Site Web application: Web application: Web application: Shared Services Shared Services Shared Services Administration Site—Default Administration Site— Administration Site—Default PartnerWeb Application Pool 4 Application Pool 5 Application Pool 6 Application Pool 9 Web application: Intranet Applications Web application: My Sites Web application: Team Sites Web application: Intraweb Web application: Internet Site http://team <varies> http://my http://web http://www Team1 Team2 Team3 Delivered http://my/personal/<user> Handbook HR Policies Library Authoring Site Staging Site Production Site Content Collection Collection Collection HR Project from Events Management Banner, Registration Segue, etc Admissions Academics Athletics Database settings: Target size per database = TBD Database settings: Database settings: Database settings: Site size limits per site = TBD Target size per database = TBD Content Deployment Site level warning = 0 Site level warning = 0 Content Deployment Maximum number of sites = flexible Storage quota per site = TBD Maximum number of sites = 1 (one site collection per database). Maximum number of sites = 1 (one site collection per database). -

Internet Censorship and Circumvention Briefing Note
Internet Censorship and Circumvention Briefing Note Madeline Bersch and Matthew Wallin - June 2014 What types of information Key Takeaways: are censored on the Internet? • There are a variety of direct and Who does this censoring? What indirect forms of online censorship. tools exist to circumvent this • Foreign governments employ several of these techniques to enforce online censorship? censorship. Interact • Several types of tools are available for Join the discussion on censorship at #ASPcensorship censorship circumvention. Discuss circumvention with the authors at • The U.S. is a major force in promoting @MaddyBersch and @MatthewRWallin anti-censorship tools. Learn more about ASP and our work in diplomacy at @amsecproject Introduction Types of Censorship Recent news of the failed “Cuban Twitter” and There are four main categories of information increased censorship in Turkey have reignited the blocking online: attention paid to how the United States promotes its ideals abroad. Around the world, thousands of 1. Services, such as email or the web; websites such as those focused on social media, 2. Content, such as that of political opposition political opposition, and human rights are blocked websites, independent news sites, or human from public view, preventing the dissemination of rights organizations; great volumes of important information. 3. Users, or blocking content by specific Though U.S. public diplomacy should not rely persons, such as human rights advocates or on the internet, it is increasingly becoming an political dissidents; important foreign policy tool. Recognizing this, the U.S. supports a variety of key tools allowing users to 4. Search engines, preventing search results circumvent political censorship online. -

Internet: Intranet: Extranet ARPANET Network
S P SHARMA CLASSES www.spsharmag.com 9910707562 Internet: Internet is a network of networks. The Internet is a global system of interconnected computer networks that use the standard Internet Protocol Suite (TCP/IP) to serve billions of users worldwide. Intranet: An intranet is a private computer network that uses Internet Protocol technologies to securely share any part of an organization's information or operational systems within that organization. Extranet An extranet is a private network that uses Internet protocols, network connectivity. An extranet can be viewed as part of a company's intranet that is extended to users outside the company, usually via the Internet. ARPANET The precursor to the Internet, ARPANET was a large wide-area network created by the United States Defense Advanced Research Project Agency (ARPA). Established in 1969, ARPANET served as a tested for new networking technologies, linking many universities and research centers. The first two nodes that formed the ARPANET were UCLA (University of California, Los Angeles) and the Stanford Research Institute, followed shortly thereafter by the University of Utah. ARPANET completed its transition to TCP/IP on January 2, 1983, was later replaced by NSFNET in 1990, and then decommissioned on February 28, 1990. Network A network is defined as a group of two or more computer systems linked together. There are many types of computer networks, including the following: Local-Area Networks (LANs): The computers are geographically close together (that is, in the same building). Wide-Area Networks (WANs): The computers are farther apart and are connected by telephone lines or radio waves. -

The Internet, Intranets, and Extranets What Is the Internet What Is The
C H A P T E R The Internet, 7 Intranets, and Extranets What is the Internet • Millions of computers, all linked together on a computer network. § A home computer usually links to the Internet using a phone line and a modem that talks to an Internet Service Provider (ISP) or Online Service § A business computer has a NIC that connects to a LAN that connects to an ISP using a broadband connection. What is the Internet cont’d. Those ISPs then connect to larger ISPs which maintain fiber-optic backbones Every computer on the Internet is thus connected to every other computer on the Internet. 1 How do your packets find the correct computer? • On a LAN, every packet is seen by every computer. • This process would bring the Internet (and every computer on it) to a standstill. • Enter the Router: § A device or, in some cases, software in a computer, that determines the next network point to which a packet should be forwarded toward its destination. The Role of the Router • Joins two networks, passing information from one to the other § Determines the best route (packet-switching) § Prevents unnecessary traffic from spilling over to the other network § Enforces security Packet Switching • Routing packets via the best available route using configuration tables § Routers communicate with each other § Balances the load on the Internet § Avoids problems with certain routes § tracert www.csus.edu http://www.visualware.com/visualroute/lived emo.html • Denial of Service Attacks 2 Internet Service Providers (ISPs) • Internet Service Provider (ISP) § Any company that provides individuals or companies with access to the Internet. -

Managing Intranet Content: a Good Practice Guide
publishing Quality content news user-generated strategy lifecycle Managing Intranet Content: A Good Practice Guide A report for IBF members only Confidential Managing Intranet Content: A Good Practice Guide Other recent IBF research Reports Measuring Intranets This 45 page report considers what should be measured across the intranet estate, and which metrics are useful and important for intranet managers. It describes strategies for justifying and managing intranet measurement. And it looks at how metrics can be turned into actionable insight, by understanding the goals and benefits of services within the intranet, making decisions and setting targets. Intranet Love Affairs It may seem obvious that being passionate about intranets is a good thing. However, analysis shows that passion can have can have both a positive and a negative effect on the intranet programme, so it needs careful nurturing and use. This report is based on in-depth interviews with intranet practitioners from American Electric Power (AEP), IKEA, Pacific Gas & Electric (PG&E), SCANA Corp., and Verizon, about the role of passion in their intranet achievements. Strategy and Governance: a good practice guide This report identifies some of the current trends in intranet strategy, governance and senior sponsorship, particularly among organizations which are currently under-performing. Drawing on IBF’s “Strategy & Governance” benchmarking model and a specially-comm- issioned survey of intranet managers, it then highlights relevant examples of good practice which may give you some ideas to apply to your organization. Finally, it documents the experience of three case study organizations: Shell, Duke Energy and BSI Group. Briefing paper Now playing on an intranet near you This research briefing discusses why and how to use intranet video. -

Special Report on the Situation of Freedom of Expression in Cuba
OEA/SER.L/V/II CIDH/RELE/INF.21/18 31 December 2018 Original: Spanish SPECIAL REPORT ON THE SITUATION OF FREEDOM OF EXPRESSION IN CUBA Office of the Special Rapporteur for Freedom of Expression of the Inter-American Commission on Human Rights Edison Lanza Special Rapporteur for Freedom of Expression 2018 OAS CATALOGING-IN-PUBLICATION DATA INTER-AMERICAN COMMISSION ON HUMAN RIGHTS. OFFICE OF THE SPECIAL RAPPORTEUR FOR FREEDOM OF EXPRESSION. SPECIAL REPORT ON THE SITUATION OF FREEDOM OF EXPRESSION IN CUBA. V. ; CM. (OAS. OFFICIAL RECORDS ; OEA/SER.L/V/II) ISBN 978-0-8270-6837-7 1. FREEDOM OF EXPRESSION--CUBA. 2. FREEDOM OF INFORMATION--CUBA. I. LANZA, EDISON. II. TITLE. III. SERIES. OEA/SER.L/V/II CIDH/RELE/INF.21/18 INTER-AMERICAN COMMISSION ON HUMAN RIGHTS Members Margarette May Macaulay Esmeralda Arosemena de Troitiño Francisco José Eguiguren Praeli Luis Ernesto Vargas Silva Joel Hernández García Antonia Urrejola Flávia Piovesan Executive Secretary Paulo Abrão Assistant Executive Secretary for Monitoring, Promotion and Technical Cooperation Maria Claudia Pulido Chief of Staff of the Executive Secretary of the IACHR Marisol Blanchard Vera SPECIAL REPORT ON THE SITUATION OF FREEDOM OF EXPRESSION IN CUBA TABLE OF CONTENTS INTRODUCTION .......................................................................................................................................................11 A. Background and purpose of the report ..........................................................................................11 B. International legal -

The Social Intranet Insights on Managing and Sharing Knowledge Internally
2016 Using Technology Series The Social Intranet Insights on Managing and Sharing Knowledge Internally Ines Mergel Syracuse University Using Technology Series 2016 The Social Intranet: Insights on Managing and Sharing Knowledge Internally Dr. Ines Mergel Associate Professor of Public Administration Maxwell School of Citizenship and Public Affairs Syracuse University THE SOCIAL INTRANET: INSIGHTS ON MANAGING AND SHARING KNOWLEDGE INTERNALLY www.businessofgovernment.org Table of Contents Foreword . 4 Executive Summary . 6 Introduction to Social Intranets in Government . 7 Components of a Social Intranet Site . 9 Benefits of Using Social Intranets . 9 Case Studies: Social Intranet Platforms in Four Government Organizations . 13 Introduction . 13 Case Study One: Corridor at the Department of State . 13 Background . 13 Organizational Location of Corridor . 14 Components of the Lightweight Collaboration Tool Suite . 16 Implementing Corridor . 17 Current Status of Corridor . .. 18 Case Study Two: NASA’s Goddard Space Flight Center’s Spacebook . 18 Background . 18 Collaboration Features of Spacebook . 19 Implementing Spacebook . 19 Current Status of Spacebook . 20 Case Study Three: Intelligence Community’s i-Space (intelligence space) . 21 Background . 21 Implementing i-Space . 21 Current Status of i-Space . 24 Case Study Four: Government of Canada’s GCconnex . 24 Background . 24 Components of GCconnex . 24 Implementing GCconnex . 26 Current Status of GCconnex . 27 Insights: Successfully Implementing Social Intranets in Government . 28 Insight -

78.9 Million PRESS FREEDOM 2013 STATUS
FREEDOM ON THE NET 2013 1 IRAN 2012 2013 POPULATION: 78.9 million NOT NOT INTERNET FREEDOM STATUS INTERNET PENETRATION 2012: 26 percent FREE FREE SOCIAL MEDIA/ICT APPS BLOCKED: Yes Obstacles to Access (0-25) 21 22 POLITICAL/SOCIAL CONTENT BLOCKED: Yes Limits on Content (0-35) 32 32 BLOGGERS/ICT USERS ARRESTED: Yes Violations of User Rights (0-40) 37 37 PRESS FREEDOM 2013 STATUS: Not Free Total (0-100) 90 91 * 0=most free, 100=least free KEY DEVELOPMENTS: MAY 2012 – APRIL 2013 In a bid to increase domestic speeds and decrease international data costs, authorities throttled encrypted traffic from outside connections and set out to transfer Iranian content to domestically-hosted servers (see OBSTACLES TO ACCESS). Blogs and news sites which support President Ahmadinejad were blocked as part of a larger conflict between conservative factions due to the June 2013 presidential election (see LIMITS ON CONTENT). The government has moved to more sophisticated instruments for blocking text messages, filtering content, and preventing the use of circumvention tools in anticipation of the election (see LIMITS ON CONTENT). Sattar Beheshti, a prominent blogger and critic of Ahmadinejad, was killed while in police custody (see VIOLATIONS OF USER RIGHTS). IRAN FREEDOM ON THE NET 2013 2 EDITOR’S NOTE ON RECENT DEVELOPMENTS This report covers events between May 1, 2012 and April 30, 2013. On June 14, 2013, Iranians took to the polls to elect a new president for the first time since the deeply-flawed presidential elections of 2009, which led to large-scale protests and a violent crackdown on supporters of the opposition “Green Movement.” With an eye on preventing a repeat of 2009, authorities waged an aggressive campaign of filtering websites, blogs, and even text messages that expressed support of certain political candidates. -

Iran: Tightening the Net 2020 After Blood and Shutdowns
Iran: Tightening the Net 2020 After Blood and Shutdowns. First published by ARTICLE 19, September 2020 ARTICLE 19 Free Word Centre 60 Farringdon Road London EC1R 3GA United Kingdom www.ARTICLE 19.org Text and analysis Copyright ARTICLE 19, September 2020 (Creative Commons License 3.0) Typesetting, Ana Z. ARTICLE 19 works for a world where all people everywhere can freely express themselves and actively engage in public life without fear of discrimination. We do this by working on two interlocking freedoms, which set the foundation for all our work. The Freedom to Speak concerns everyone’s right to express and disseminate opinions, ideas and information through any means, as well as to disagree from, and question power- holders. The Freedom to Know concerns the right to demand and receive information by power-holders for transparency good governance and sustainable development. When either of these freedoms comes under threat, by the failure of power-holders to adequately protect them, ARTICLE 19 speaks with one voice, through courts of law, through global and regional organisations, and through civil society wherever we are present. About Creative Commons License 3.0: This work is provided under the Creative Commons Attribution- Non-Commercial-ShareAlike 2.5 license. You are free to copy, distribute and display this work and to make derivative works, provided you: 1) give credit to ARTICLE 19; 2) do not use this work for commercial purposes; 3) distribute any works derived from this publication under a license identical to this one. To -

The Growth of Global Internet Censorship and Circumvention: a Survey
Communications of the IIMA Volume 11 Issue 2 Article 6 2011 The Growth of Global Internet Censorship and Circumvention: A Survey Ramesh Subramanian Quinnipiac University Follow this and additional works at: https://scholarworks.lib.csusb.edu/ciima Recommended Citation Subramanian, Ramesh (2011) "The Growth of Global Internet Censorship and Circumvention: A Survey," Communications of the IIMA: Vol. 11 : Iss. 2 , Article 6. Available at: https://scholarworks.lib.csusb.edu/ciima/vol11/iss2/6 This Article is brought to you for free and open access by CSUSB ScholarWorks. It has been accepted for inclusion in Communications of the IIMA by an authorized editor of CSUSB ScholarWorks. For more information, please contact [email protected]. The Growth of Global Internet Censorship and Circumvention: A Survey Subramanian The Growth of Global Internet Censorship and Circumvention: A Survey Ramesh Subramanian Quinnipiac University, USA [email protected] ABSTRACT The Internet has, within a period of twenty years, become the primary medium of information exchange in the world. It is also arguably the primary source of information in the world. Search engines such as Google and Yahoo have made the vast trove of information available and accessible to everybody. Email and social network applications such as Facebook and Twitter have enabled people all over the world to meet, collaborate and participate in joint activities. The Internet has also gradually become a tool of dissidence in repressed nations all over the world - to spread information, plan and organize activists and conduct protests. Not surprisingly, repressive regimes see the Internet as a threat. Under the guise of protecting their citizens from the negative effects of the Internet (such as pornography and hate speech), they have, and are, actively curbed Internet use by their citizens by adopting various censorship measures and blockades. -

The Geopolitics Behind the Routes Data Travels: a Case Study of Iran Loqman Salamatian, Frederick Douzet, Kevin Limonier, Kavé Salamatian
The geopolitics behind the routes data travels: a case study of Iran Loqman Salamatian, Frederick Douzet, Kevin Limonier, Kavé Salamatian I ) Introduction: The global expansion of the Internet has brought many challenges to the field of geopolitics. According to the definition of Yves Lacoste, geopolitics studies rivalries of power and influence over a territory at various levels of analysis [Lacoste 1993]. It analyses the dynamics of a conflict over a territory, the contradictory representations and strategies of the stakeholders to assert control and appropriation of the territory, and how these stakeholders defend their interests within this territory. On the one hand, it is clear that cyberspace has become a relevant object of study for the field of geopolitics. Multiple actors have been empowered by the speed, ubiquity and anonymity provided by the low-cost and widely accessible technology for better—the multiple benefits to our societies— and for worse [Douzet 2014]. Cyberspace has indeed become a space of conflict and a strategic priority for many states. In 2016, at the Warsaw Summit, NATO allied nations recognized cyberspace as a new “operational domain in which NATO must defend itself as effectively as it does in the air, on land and at sea” [Brent 2019], thus following the United States and a wide range of countries that have identified cyberspace as a new military domain. The digital space is indeed used as a vector of attacks to perpetrate crime and conduct operations of sabotage, disruption, espionage or subversion [Rid 2013; Maurer 2018]. Cyberspace can therefore be regarded as a new dimension of most geopolitical conflicts and a new space of confrontation that lends itself to a geopolitical analysis.