Risk Analysis of Mobile Devices with Special Concern of Malware Contamination
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

SGIM Forum Template
Society of General Internal Medicine SGIM TO PROMOTE IMPROVED PATIENT CARE, RESEARCH, AND EDUCATION IN PRIMARY CARE AND FORUM GENERAL INTERNAL MEDICINE Volume 26 • Number 2 • February 2003 2003 ANNUAL MEETING GENERALIST PHYSICIANS AS AGENTS FOR CHANGE: EDUCATION AND RESEARCH, PRACTICE AND POLICY Helen Burstin, MD, MPH and Linda Headrick, MD, MS he SGIM Annual Meeting is rap- can serve as agents for change at every idly shaping up to be an innovative point where we interface with the health Tinternational meeting for general care system. Against a background of in- internists from the U.S., Canada, and creasing concerns with the loss of physi- many other countries. In addition to the cian autonomy, the erosion of profession- Contents exciting venue of Vancouver, British Co- alism, and the inability of the health care lumbia, we are also collaborating with our system to address problems of quality and 1 Generalist Physicians as Agents for colleagues from the Canadian Society of access, the knowledge and skills of gen- Change: Education and Research, Internal Medicine (CSIM) for the first eral internists are ideally suited to provide Practice and Policy time. Vancouver is an incredibly entic- leadership, change and improvement. ing locale and our conference facilities are In Education: Generalists are the 2 Career Support Task Force Update at the epicenter of an amazing range of backbone of clinical training for medical activities for you and your family. With students, residents, and fellows. As we 3 President’s Column the mountains only 30 minutes from embrace 21st century health care, we can Vancouver, outdoor activities include vis- use our role as change agents to ensure 4 Research Funding Corner its to Grouse Mountain or the Capilano that we are offering medical education Extension Bridge. -

Mobiliųjų Telefonų Modeliai, Kuriems Tinka Ši Programinė Įranga
Mobiliųjų telefonų modeliai, kuriems tinka ši programinė įranga Telefonai su BlackBerry operacinė sistema 1. Alltel BlackBerry 7250 2. Alltel BlackBerry 8703e 3. Sprint BlackBerry Curve 8530 4. Sprint BlackBerry Pearl 8130 5. Alltel BlackBerry 7130 6. Alltel BlackBerry 8703e 7. Alltel BlackBerry 8830 8. Alltel BlackBerry Curve 8330 9. Alltel BlackBerry Curve 8530 10. Alltel BlackBerry Pearl 8130 11. Alltel BlackBerry Tour 9630 12. Alltel Pearl Flip 8230 13. AT&T BlackBerry 7130c 14. AT&T BlackBerry 7290 15. AT&T BlackBerry 8520 16. AT&T BlackBerry 8700c 17. AT&T BlackBerry 8800 18. AT&T BlackBerry 8820 19. AT&T BlackBerry Bold 9000 20. AT&T BlackBerry Bold 9700 21. AT&T BlackBerry Curve 22. AT&T BlackBerry Curve 8310 23. AT&T BlackBerry Curve 8320 24. AT&T BlackBerry Curve 8900 25. AT&T BlackBerry Pearl 26. AT&T BlackBerry Pearl 8110 27. AT&T BlackBerry Pearl 8120 28. BlackBerry 5810 29. BlackBerry 5820 30. BlackBerry 6210 31. BlackBerry 6220 32. BlackBerry 6230 33. BlackBerry 6280 34. BlackBerry 6510 35. BlackBerry 6710 36. BlackBerry 6720 37. BlackBerry 6750 38. BlackBerry 7100g 39. BlackBerry 7100i 40. BlackBerry 7100r 41. BlackBerry 7100t 42. BlackBerry 7100v 43. BlackBerry 7100x 1 44. BlackBerry 7105t 45. BlackBerry 7130c 46. BlackBerry 7130e 47. BlackBerry 7130g 48. BlackBerry 7130v 49. BlackBerry 7210 50. BlackBerry 7230 51. BlackBerry 7250 52. BlackBerry 7270 53. BlackBerry 7280 54. BlackBerry 7290 55. BlackBerry 7510 56. BlackBerry 7520 57. BlackBerry 7730 58. BlackBerry 7750 59. BlackBerry 7780 60. BlackBerry 8700c 61. BlackBerry 8700f 62. BlackBerry 8700g 63. BlackBerry 8700r 64. -

HTC SPV MDA G1 Zdalny Unlock Kodem Po IMEI - Również DESIRE
GSM-Support ul. Bitschana 2/38, 31-420 Kraków mobile +48 608107455, NIP PL9451852164 REGON: 120203925 www.gsm-support.net HTC SPV MDA G1 zdalny unlock kodem po IMEI - również DESIRE Jest to usługa pozwalająca na zdjęcie simlocka z telefonów HTC / SPV / QTEK / MDA / G1-Google / Xperia poprzez kod - łącznie z najnowszą bazą! Kod podawany jest na podstawie numeru IMEI, modelu oraz sieci, w której jest simlock. Numer IMEI można sprawdzić w telefonie poprzez wybranie na klawiaturze *#06#. Do każdego numeru IMEI przyporządkowany jest jeden kod. W polu na komentarz prosimy podać model, IMEI oraz kraj i nazwę sieci, w której jest załozony simlock. Czas oczekiwania na kod to średnio 2h. Nie zdejmujemy simlocków kodem z HTC Touch HD z sieci Play, HTC Touch Pro z Orange Polska i innych, które wyraźnie są wymienione na samym dole opisu! Usługa obejmuje modele: DOPOD 310 (HTC Oxygen) DOPOD 535 (HTC Voyager) DOPOD 565 (HTC Typhoon) DOPOD 566 (HTC Hurricane) DOPOD 575 (HTC Feeler) DOPOD 577W (HTC Tornado) DOPOD 585 (HTC Amadeus) DOPOD 586 (HTC Hurricane) DOPOD 586W (HTC Tornado) DOPOD 595 (HTC Breeze) DOPOD 686 (HTC Wallaby) DOPOD 696 (HTC Himalaya) DOPOD 696i (HTC Himalaya) DOPOD 699 (HTC Alpine) DOPOD 700 (HTC Blueangel) DOPOD 710 (HTC Startrek) DOPOD 710+ (HTC Startrek) DOPOD 818 (HTC Magician) DOPOD 818 Pro (HTC Prophet) DOPOD 818C (HTC Wave) DOPOD 828 (HTC Magician) DOPOD 828+ (HTC Magician) DOPOD 830 (HTC Prophet) DOPOD 838 (HTC Wizard) DOPOD 838 Pro (HTC Hermes) DOPOD 900 (HTC Universal) DOPOD C500 (HTC Vox) DOPOD C720 (HTC Excalibur) DOPOD C720W -

Hp Jornada 560 Series Personal Digital Assistant User's Guide
hp jornada 560 series personal digital assistant User’s Guide Printed in Singapore Edition 1 Copyright The information contained in this document is provided “as is” and is subject to change without notice. Hewlett-Packard Company makes no warranty of any kind with regard to this manual, including, but not limited to, the implied warranties of merchantability and fitness for a particular purpose. Hewlett-Packard Co. shall not be liable for any errors contained herein or for incidental or consequential damages in connection with the furnishing, performance, or use of this manual or the examples herein. © Hewlett-Packard Company 2001. This document contains proprietary information that is protected by copyright. All rights are reserved. No part of this document may be photocopied, reproduced, adapted, or translated to another language without the prior written consent of Hewlett-Packard Co., except as allowed under the copyright laws. The programs that control this product are copyrighted and all rights are reserved. Reproduction, adaptation, or translation of those programs without prior written permission of Hewlett-Packard Co. is also prohibited. Microsoft, ActiveSync, MSN, Outlook, Windows, Windows Media, Windows NT, and the Windows logo are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries. Microsoft products are licensed to OEMs by Microsoft Licensing, Inc., a wholly owned subsidiary of Microsoft Corporation. All other brand names and product names used in this document are trade names, service marks, trademarks, or registered trademarks of their respective owners. Hewlett-Packard Singapore (Pte) Ltd. Asia Pacific Personal Computer Division 452 Alexandra Road Singapore 119961 Contents 1 | Welcome ............................................................................ -
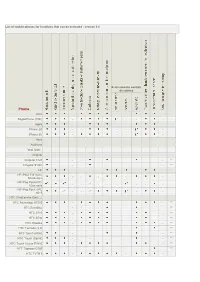
List of Mobile Phones for Functions That Can Be Activated - Version 5.4
List of mobile phones for functions that can be activated - version 5.4 Scaricamento contatti da rubrica Phone Amoi SkypePhone (TRE) - - - - Apple iPhone 2G - - - - - iPhone 3G - - - - Asus Audiovox Vedi Qtek... Cingular Cingular 8125 - - - ** Cingular SYNC - - - ** HP HP iPAQ 514 Voice - - - - - Messenger HP iPaq Pocket PC - - -* - - - - - - 63xx serie HP iPaq Pocket PC -* - - -* - - 6515 HTC (Vedi anche Qtek....) HTC Advantage X7500 - - ** HTC Excalibur - - - ** HTC S710 - - ** HTC S730 - - ** HTC Shadow - - ** HTC Tornado (2.0) ** HTC Touch (Alltel) - - - ** HTC Touch (Sprint) - - - - ** HTC Touch Cruise P3650 - - ** HTC Typhoon C500 ** HTC TyTN II - - - HTC Wizard ** Qteck/HTC P3300 - - - - - - - Qteck/HTC Touch Diamond - - - i-Mate Vedi Qtek LG LG CU500 - - ** LG KE850 - - - - - - - - LG KE850 Prada - - - ** LG KG800 (Chocolate) - - - - - - - - ** LG KS20 - - ** LG KU990 - - - ** LG KU800 - - - - - - - - - ** LG Shine (CU720) N N N ** LG Trax (CU575) N N N N N N ** LG U8550 - - - - -* LG U880 - - - - - - - - LG U900 - - - - - - - - Motorola Motorola A830/ - - - - A835 Motorola A1000 - - - - -* - Motorola A1200 Ming N ** Motorola E1000 - Motorola E398 - - - Motorola i615 N ** Motorola i880 N ** Motorola KRZR K1 - Motorola MPX220 - - - - - - Motorola RAZR2V9/ KRZR K3/ RAZR V3xx/ RAZR - MaxxV6 Motorola RAZR V3i/V3r ** Motorola RAZR V3t ** Motorola RAZR V6 Maxx ** Motorola RIZR Z3 - Motorola ROKR E6 N N ** Motorola Sidekick Slide N N N N ** Motorola SLVR L6 - Motorola SLVR L7 - Motorola U9 N N ** Motorola RAZR V3 - - Motorola V8 - - Motorola -

Kinh Nghiem Uprom Dong May HTC V.07.10.07
Kinh nghi ệm uprom dòng máy HTC: b ắt ñầu t ừ ñâu? Mở ñầu: Sau khi mua máy Pocket PC phone, ñiều ñầu tiên là tôi lao vào các di ễn ñàn ñể tìm thông tin, m ột m ặt là tìm hi ểu v ề ph ần m ềm dùng trên PPC m ặc khác là tìm hi ểu v ề chuy ện UPROM nó ra làm sao?. Tuy nhiên, sau khi ñọc m ột lo ạt các thông tin, tôi b ắt ñầu th ấy có 2 ñiều ñáng s ợ. 1. Sợ là vì b ỏ ti ền ra mua máy khoảng 10-12 tri ệu ñồng nh ưng sau khi ham vui UPROM xong thì máy thành “c ục g ạch” ch ặn gi ấy ñen ngòm mà không bi ết ph ải làm sao? Vậy mà sau khi ki ếm ñủ thông tin thì tôi v ẫn còn s ợ. 2. Cái s ợ th ứ 2: là ñã có ñủ thông tin, nh ưng ña s ố bài vi ết ch ỉ mô t ả b ằng ch ữ là chính mà không có hình ảnh. Cái này nó gi ống nh ư là h ọc sinh ti ểu h ọc nghe th ầy giáo mô t ả “con trâu” nh ưng ch ưa bao gi ờ th ấy con trâu ra làm sao?. ðiều này th ật s ự ñáng s ợ. Tuy nhiên sau m ột h ồi tìm ki ếm, thì c ũng có m ột s ố di ễn ñàn h ọ mô t ả vi ệc upROM b ằng hình ảnh, ñiều này th ật s ự h ữu ích cho nh ững ng ười m ới b ắt ñầu. -

EASY USE Lagerprodukte Aktualisiert Donnerstag, Den 19
EASY USE Lagerprodukte Aktualisiert Donnerstag, den 19. März 2020 um 16:07 Uhr EASY USE - Produkt-/ Lagerliste Stand: 15.03.2020 ( Preisanpassungen vorbehalten ) Alle Preise inkl. MwSt., zzgl. Versand Aktuelle Lager-Artikel - bestellbar per Mail an [email protected] oder Tel.: 08551 9139319 Artikelnr. Kurztext Matchcode HPDOCKU565 HP USB Docking Cradle f. Jornada 560 Serie (565,568) mit USB-Kabel F2903A FXC371BATCE Batteriefachabdeckung f. iPAQ rx3715 verwendet mit extended AkkuFXC371BATCE FXC65COVT HP Screen Protector f. iPAQ hw6000 Serie (hw6510, hw6515, hw6910, 398326-001 hw6915) HP39XACR HP Netzteil f. iPAQ h3800, h3900, h1900, h2200, h6300, hx4700, 389145-021 hx2000, rz1700, 253628-021 rx3700, hw6000, h5000 FXC221IRC Ersatzteil : Abdeckung schwarz über Infrarot Port f. iPAQ h2200 FXC221IRCSerie (h2210, h2215) HP651DOCK HP Docking Cradle USB f. hw6000 Serie (hw6510, hw6515, hw6910, 383749-001 hw6915) 366854-005 370526-007 1 / 94 EASY USE Lagerprodukte Aktualisiert Donnerstag, den 19. März 2020 um 16:07 Uhr RPL19XBAT HP Standard Akku f. iPAQ h1900 Serie (h1910,h1930,h1940) 900mAh FA114A Li-Ion 311315-B21 311340-001 311349 HP170PENS HP 3er Pack Stifte f. iPAQ hx2000, rz1710, rx3715, hx4700, hw6000 FA261A Serien 367202-001 FXCHX241BATCE Batteriefachabdeckung f. iPAQ hx2000 Serie verwendet mit extended FXCHX241BATCE Akku HPGLANUSB3A HP USB 3.0 kompatibel 2.0 an Gigabit LAN RJ45 Adapter N7P47AA 829834-001 829941-001 HPSP65BLTC HP Gürtelhalterung mit Clip schwarz f. iPAQ hw6000 Serie (hw6510, 383744-001 hw6515, hw6910, hw6915) HPNB4720KITL HP Tastatur international / US Englisch f. ProBook4720s 598692-B31 HPSP65HEADP HP Headphone mit Mikrophonef. hw6000 Serie + Voice Messenger 383748-001 514 445667-001 2 / 94 EASY USE Lagerprodukte Aktualisiert Donnerstag, den 19. -
Internet Scanner® 7.0 SP2 Asset & Operating System Identification
An ISS White Paper Internet Scanner® 7.0 SP2 Asset & Operating System Identification Technical Whitepaper 6303 Barfield Road • Atlanta, GA 30328 Tel: 404.236.2600 • Fax: 404.236.2626 Internet Scanner 7.0 Overview The following document contains information on the system identification used by Internet Scanner 7.0 SP2. Background SP2 updates the NMAP database that is used for system fingerprinting to the 3.75 version. This update includes 20% more fingerprints than the previous version and numerous updates to existing fingerprints. With this update we can now identify 1,353 different systems with an extremely high degree of accuracy. This is accomplished by the combination of data from the NMAP database along with IS specific scan results such as banner’s, open port grouping, available services, NetBIOS probes, etc. More information can be found in the “Discovery Engine” section of the Internet Scanner 7.0 Technical Overview whitepaper. More information on classical OS Fingerprinting can be found in “Remote OS detection via TCP/IP Stack FingerPrinting” at http://www.insecure.org/nmap/nmap-fingerprinting-article.html. User Defined OS Fingerprint Extensions Service Pack 2 adds the ability for users to add their own custom fingerprints for Internet Scanner to use. Information on how to add these can be found in the issSensors\scanner_1\discovery\user-os-fingerprints file. More information on much of the fingerprint format can also be found on the Nmap website (www.insecure.org/nmap). Operating Systems Identified – Summary Internet Scanner 7.0 SP2 is able to identify nearly 700 different Operating Systems down to the update level. -
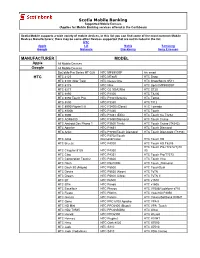
Supported Devices
Scotia Mobile Banking Supported Mobile Devices (Applies for Mobile Banking services offered in the Caribbean) Scotia Mobile supports a wide variety of mobile devices, in this list you can find some of the most common Mobile Devices Manufacturers; there may be some other Devices supported that are not included in the list. HTC Apple LG Nokia Samsung Google Motorola Blackberry Sony Ericsson MANUFACTURER MODEL Apple All Mobile Devices Google All Mobile Devices DoCoMo Pro Series HT-02A HTC MP6950SP htc smart HTC HTC 2125 HTC MTeoR HTC Snap HTC 3100 (Star Trek) HTC Nexus One HTC Snap/Sprint S511 HTC 6175 HTC Nike HTC Sprint MP6900SP HTC 6277 HTC O2 XDA2Mini HTC ST20 HTC 6850 HTC P3300 HTC T8290 HTC 6850 Touch Pro HTC P3301/Artemis HTC Tattoo HTC 8500 HTC P3350 HTC Tilt 2 HTC 8900/Pilgrim/Tilt HTC P3400i (Gene) HTC Tornado HTC 8900b HTC P3450 HTC Touch HTC 9090 HTC P3451 (Elfin) HTC Touch 3G T3232 HTC ADR6300 HTC P3490/Diamond HTC Touch Cruise HTC Android Dev Phone 1 HTC P3600 Trinity HTC Touch Cruise (T4242) HTC Apache HTC P3651 HTC Touch Diamond HTC Artist HTC P3700/Touch Diamond HTC Touch Diamond2 (T5353) HTC P3702/Touch HTC Atlas Diamond/Victor HTC Touch HD HTC Breeze HTC P4000 HTC Touch HD T8285 HTC Touch Pro (T7272/TyTn HTC Cingular 8125 HTC P4350 III) HTC Cleo HTC P4351 HTC Touch Pro/T7373 HTC Corporation Touch2 HTC P4600 HTC Touch Viva HTC Dash HTC P5310BM HTC Touch_Diamond HTC Dash 3G (Maple) HTC P5500 HTC TouchDual HTC Desire HTC P5530 (Neon) HTC TyTN HTC Dream HTC P5800 (Libra) HTC TyTN II HTC Elf HTC P6500 HTC v1510 HTC Elfin HTC -

SGIM Forum Template
Society of General Internal Medicine SGIM TO PROMOTE IMPROVED PATIENT CARE, RESEARCH, AND EDUCATION IN PRIMARY CARE AND FORUM GENERAL INTERNAL MEDICINE Volume 26 • Number 3 • March 2003 ANNUAL MEETING PRECOURSES OFFER EXCITING OPPORTUNITIES Eric Whitaker, MD his year’s precourses represent a and “The Immigrant Experience: Caring range of topics that we hope will fill for Patients New to this Country.” Each Tthe needs and interests of many new represents an example of how primary care and veteran SGIM members. Out of a physicians can be on the forefront of our record number of 55 submissions, 35 half- changing world of medicine. and full-day precourses were accepted for On the clinical front, precourses in presentation in Vancouver. The excep- this year’s program include “See One, Do tional quality of the submissions made this One, Teach One: A Practical Approach a challenging task for the committee. We to the Medical Orthopedic Exam for the are grateful to the efforts of all of those Academic Internist,” “Update on Anti- who submitted precourse proposals. The coagulation and Thromboembolism” or results are a remarkable range of content “Controversies in Chronic Pain Manage- and teaching approaches. ment” and “Sports Medicine.” We also thank the committee of ten For those interested in learning more Contents SGIM members, from a range of back- about certain research methods, courses grounds, who put in their time and ex- such as “HCUP: Data to Generate Evi- 1 Annual Meeting Precourses Offer pertise to review and select this year’s dence for Change,” “Meta-Analysis” and Exciting Opportunities precourses. -

Ebook - Informations About Operating Systems Version: September 3, 2016 | Download
eBook - Informations about Operating Systems Version: September 3, 2016 | Download: www.operating-system.org AIX Operating System (Unix) Internet: AIX Operating System (Unix) AmigaOS Operating System Internet: AmigaOS Operating System Android operating system Internet: Android operating system Aperios Operating System Internet: Aperios Operating System AtheOS Operating System Internet: AtheOS Operating System BeIA Operating System Internet: BeIA Operating System BeOS Operating System Internet: BeOS Operating System BSD/OS Operating System Internet: BSD/OS Operating System CP/M, DR-DOS Operating System Internet: CP/M, DR-DOS Operating System Darwin Operating System Internet: Darwin Operating System Debian Linux Operating System Internet: Debian Linux Operating System eComStation Operating System Internet: eComStation Operating System Symbian (EPOC) Operating System Internet: Symbian (EPOC) Operating System FreeBSD Operating System (BSD) Internet: FreeBSD Operating System (BSD) Gentoo Linux Operating System Internet: Gentoo Linux Operating System Haiku Operating System Internet: Haiku Operating System HP-UX Operating System (Unix) Internet: HP-UX Operating System (Unix) GNU/Hurd Operating System Internet: GNU/Hurd Operating System Inferno Operating System Internet: Inferno Operating System IRIX Operating System (Unix) Internet: IRIX Operating System (Unix) JavaOS Operating System Internet: JavaOS Operating System LFS Operating System (Linux) Internet: LFS Operating System (Linux) Linspire Operating System (Linux) Internet: Linspire Operating -

13. Handheld Computers and Windows CE
FOR 240 Introduction to Computing in Natural Resources 13. Handheld Computers and Windows CE There are many types of handheld computers and versions of Windows CE available. This section will give you more information about handheld computers and Windows CE. Before you get started in the details about the features and capabilities of these devices, you may need to look at 13.1 - Glossary explains some of the new terms used to describe them. 13.1 Glossary of Terms Wireless Ethernet - A wireless local area network protocol which allows high speed access to network resources. It operates at 11, 5.5, 2 and 1 megabits per second depending on distance. It uses the 2.4 ghz spectrum using direct sequence spectrum (DSS). ActiveSync - The desktop software that the Handheld PC, Palm-size PC and Pocket PC use to synchronize with. The latest version is ActiveSync 3.7. Cable Modem - Provides high speed access to the internet at receive rates from 1,544k or faster. The upload rate is much slower usually 256 or 512k. Each cable company uses different standards for their cable modem. CHAP - A security (authentication) protocol used with PPP. It sends an encrypted hash of the password to the client for comparison to the password entered. It does not send the password over the PPP connection. Windows CE and the Pocket PC do not support encrypted CHAP password authentication. CF, CompactFlash - A non-volatile secondary storage card which is compatible with the Pocket PC and Windows CE originally designed by Sandisk. CompactFlash uses flash memory so it does not require very much power to work.