Electronic Frontier Foundation
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

English Regional Dialect Lexis in the Names and Occupations of the Gloucestershire Cotswolds: a Reassessment of the Relationship Between Names and Dialects
English regional dialect lexis in the names and occupations of the Gloucestershire Cotswolds: a reassessment of the relationship between names and dialects Item Type Article Authors Parkin, Harry Citation Parkin, H. (2015), ‘English regional dialect lexis in the names and occupations of the Gloucestershire Cotswolds: a reassessment of the relationship between names and dialects’, Dialectologia et Geolinguistica 23, 1, pp. 24–37. DOI 10.1515/dialect-2015-0002 Publisher De Gruyter Journal Dialectologia et Geolinguistica Rights Attribution-NonCommercial-NoDerivatives 4.0 International Download date 24/09/2021 11:02:04 Item License http://creativecommons.org/licenses/by-nc-nd/4.0/ Link to Item http://hdl.handle.net/10034/621769 English regional dialect lexis in the names and occupations of the Gloucestershire Cotswolds: A reassessment of the relationship between names and dialects David Harry Parkin Abstract A number of surname-based studies have presented a relationship between medieval regional dialect lexis and the distribution of associated modern-day surnames. However, by carrying out localised research, it appears that the two might not be so closely linked as previously thought, with discrepancies in the distribution of regionally specific names and equivalent occupational descriptions. As a result, there seems to be a need to reconsider the connection between regional lexicons and corresponding name stocks, which may have been less closely related, at a period of non-hereditary by-naming, than current knowledge suggests. 1. Surnames and dialect It has been widely recognised that the regional distribution of certain by-names and surnames,1 from the medieval period up to the present day, can represent regional distinctions in Middle English (ME) dialect lexis and phonology. -

Executive Branch
EXECUTIVE BRANCH THE PRESIDENT BARACK H. OBAMA, Senator from Illinois and 44th President of the United States; born in Honolulu, Hawaii, August 4, 1961; received a B.A. in 1983 from Columbia University, New York City; worked as a community organizer in Chicago, IL; studied law at Harvard University, where he became the first African American president of the Harvard Law Review, and received a J.D. in 1991; practiced law in Chicago, IL; lecturer on constitutional law, University of Chicago; member, Illinois State Senate, 1997–2004; elected as a Democrat to the U.S. Senate in 2004; and served from January 3, 2005, to November 16, 2008, when he resigned from office, having been elected President; family: married to Michelle; two children: Malia and Sasha; elected as President of the United States on November 4, 2008, and took the oath of office on January 20, 2009. EXECUTIVE OFFICE OF THE PRESIDENT 1600 Pennsylvania Avenue, NW., 20500 Eisenhower Executive Office Building (EEOB), 17th Street and Pennsylvania Avenue, NW., 20500, phone (202) 456–1414, http://www.whitehouse.gov The President of the United States.—Barack H. Obama. Special Assistant to the President and Personal Aide to the President.— Anita Decker Breckenridge. Director of Oval Office Operations.—Brian Mosteller. OFFICE OF THE VICE PRESIDENT phone (202) 456–1414 The Vice President.—Joseph R. Biden, Jr. Assistant to the President and Chief of Staff to the Vice President.—Bruce Reed, EEOB, room 276, 456–9000. Deputy Assistant to the President and Chief of Staff to Dr. Jill Biden.—Sheila Nix, EEOB, room 200, 456–7458. -

1 Catherine E. Weaver
Catherine E. Weaver Associate Professor, LBJ School of Public Affairs Distinguished Scholar and Research Coordinator, Robert S. Strauss Center for International Security and Law The University of Texas at Austin 2315 Red River Street, SRH 3.358 Austin, Texas 78712 email: [email protected] Strauss Center main phone: (512) 471-6267 Office Phone: (512) 232-3443 Education Ph.D., Political Science May 2003 University of Wisconsin, Madison BA, Political Science and Russian April 1994 University of Michigan Academic Positions Associate Professor, LBJ School of Public Affairs, September 2010 – present University of Texas at Austin Assistant Professor, LBJ School of Public Affairs, January 2009 – August 2010 University of Texas at Austin Assistant Professor of Political Science August 2002 – December 2008 University of Kansas Research Fellow, Brookings Institution August 2001-2002 Washington, D.C. Publications Books: Catherine Weaver. 2008. Hypocrisy Trap: The World Bank and the Poverty of Reform. Princeton, NJ: Princeton University Press. ~Co-recipient of the Chadwick Alger Prize for best book on International Organizations and Multilateralism, International Studies Association, 2009. (Co-recipient with Benjamin Schiff) ~Winner of the Society of Policy Scientists 2009 Harold D. Lasswell Prize. Catherine Weaver and Nicola Phillips, eds. 2010. International Political Economy and the Transatlantic Divide. London, UK: Routledge Press. 1 Articles and Book Chapters (* = in peer review journal or reviewed as part of book project): *Catherine Weaver and Susan Park. Forthcoming 2012.“The Anatomy of IO Agency: Anticorruption and Environmental Reform at the World Bank.” In Joel Oestreich, ed. Agency in International Organizations. London: Routledge Press. *Catherine Weaver. 2010. "The Politics of Performance Evaluation: Independent Evaluation at the International Monetary Fund" Review of International Organizations, September 2010, pp.365-385. -
Official List of Houston County Qualified Voters State of Alabama Houston County
OFFICIAL LIST OF HOUSTON COUNTY QUALIFIED VOTERS STATE OF ALABAMA HOUSTON COUNTY As directed by the Code of Alabama, I, PATRICK H. DAVENPORT, Judge of Probate, hereby certify that the within constitutes a full and correct list of all qualified electors, as the same appears from the returns of the Board of Registrars, on file in this office, and who will be entitled to vote in any election held in said county. Notice is hereby given to any voter duly registered whose name has been inadvertently, or through mistake, omitted from the list of qualified voters herein published, and who is legally entitled to vote, shall have ten days from the date of thispublication to have his or her name entered upon the list of qualified voters, upon producing proof to the Board of Registrars of said County that his or her name should be added to said list. This list does not include names of persons who registered after Jan 16, 2020. A supplement list will be published on or before Feb 25, 2020. PATRICK H. DAVENPORT Judge of Probate ANDREW BELLE ANNETTE BURKS DELISA THOMAS CUNNINGHAM KYLE JACOB EDWARDS MICHAEL WAYNE GOODWIN SHARRON ANNELLE COMM CENTER BLACK MORRIS K BURNEY HANSEL CURETON JAMES T EDWARDS MICHELLE MAIRE GOOLSBY KIMBERLY SHANEDRA ABBOTT CLARISSE ANN BLACK NATASHA LYNETTE BURNSED ROBERT AUSTIN III CURLIN STACY DENISE EIKER REBECCA GORDON MAE EVELYN ABBOTT EARL LEIGHTON III BLACK SARAH FRANCIS BURROUGHS APRIL ANTRONN CURRY ANTHONY DWAYNE ELLARD GRANADA IRENE GORLAND KIMBERLY DARLINE ADAMS CHANEY ALEDIA BLACKBURN MICHAEL EDWARD BURROUGHS KHAALIS -

Office of Fiscal & Monitoring Services Bureau of County Finance And
Office of Fiscal & Monitoring Services Bureau of County Finance and Technical Assistance County Points of Contact for BCFTA Help Desk REGION 1 COUNTY SERVICE LOCATION LAST NAME FIRST NAME E‐MAIL CONTACT Champaign LAA11, LAC11, LAP11 Bacon Martha [email protected] Stewart Holly [email protected] LAC21 Bowens Joyce [email protected] Delaware Gray Adeana [email protected] LAA21, LAP21 Schonauer Jacqueline [email protected] Walters Jacqueline [email protected] Fairfield LAA23, LAC23, LAP23 Brown Carri [email protected] McCoy Amy [email protected] Fayette LAA24, LAC24, LAP24 Cave Abby [email protected] Williamson Faye [email protected] Franklin LAC25 Jittkarunrat Sirina [email protected] Okafor Emeka [email protected] Knox LAA42, LAC42, LAP42 Feltman Andrea [email protected] Myers Jacqueline [email protected] LAC45 Bryan Cynthia [email protected] Licking LAA45, LAP45 Mitchell Erica [email protected] Spangler Jamie [email protected] LAA46, LAC46 Fay Sandra [email protected] Logan Fogle Cheryl [email protected] LAP46 Nease Shoan [email protected] Pugh Kathy [email protected] Madison LAA49, LAC49, LAP49 Kaifas Steve [email protected] Vickers Donna [email protected] LAA51, LAC51 Chapman Melissa [email protected] Marion Harless Julie [email protected] LAP51 Downes Patrick [email protected] Spencer Becky [email protected] Morrow LAA59, LAC59, LAP59 Keeran -
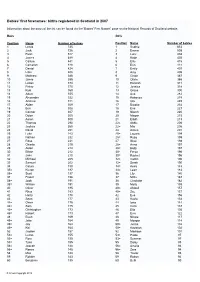
Babies' First Forenames: Births Registered in Scotland in 2007
Babies' first forenames: births registered in Scotland in 2007 Information about the basis of the list can be found via the 'Babies' First Names' page on the National Records of Scotland website. Boys Girls Position Name Number of babies Position Name Number of babies 1 Lewis 735 1 Sophie 653 2 Jack 726 2 Emma 508 3 Ryan 517 3 Lucy 438 4 James 489 4 Katie 435 5 Callum 441 5 Ellie 415 6 Cameron 428 6 Erin 414 7 Daniel 424 7 Emily 407 8 Liam 406 8 Amy 405 9 Matthew 386 9 Chloe 387 10 Jamie 385 10 Olivia 386 11 Logan 374 11 Hannah 371 12 Finlay 370 12 Jessica 318 13 Kyle 369 13 Grace 300 14 Adam 355 14 Ava 282 15 Alexander 322 15 Rebecca 274 16 Andrew 311 16 Isla 249 17 Aiden 309 17 Brooke 234 18 Ben 308 18 Eva 227 19 Connor 307 19 Niamh 220 20 Dylan 305 20 Megan 215 21 Aaron 300 21 Eilidh 213 22 Thomas 290 22= Abbie 206 23 Joshua 260 22= Mia 206 24 David 251 24 Aimee 201 25 Luke 243 25= Lauren 199 26 Nathan 232 25= Ruby 199 27 Ross 231 27 Skye 198 28 Charlie 219 28= Anna 197 29 Aidan 214 28= Holly 197 30 Ethan 212 30= Freya 196 31 John 210 30= Rachel 196 32 Michael 205 32= Caitlin 190 33 Samuel 202 32= Sarah 190 34 Calum 199 34= Keira 183 35= Kieran 197 34= Leah 183 35= Scott 197 36 Lily 180 37 Fraser 196 37 Millie 167 38= Josh 191 38 Charlotte 162 38= William 191 39 Molly 159 40 Oliver 185 40= Abigail 157 41 Rhys 183 40= Zoe 157 42 Harry 178 42 Eve 156 43 Sean 177 43 Kayla 154 44= Owen 175 44 Iona 144 44= Sam 175 45 Cara 137 46= Christopher 173 46 Ella 136 46= Robert 173 47 Evie 122 48 Euan 169 48 Nicole 117 49= Jake 164 49 Morgan 114 49= -

الجريمة اإللكرتونية يف املجتمع الخليجي وكيفية مواجهتها Cybercrimes in the Gulf Society and How to Tackle Them
مسابقة جائزة اﻷمير نايف بن عبدالعزيز للبحوث اﻷمنية لعام )2015م( الجريمة اﻹلكرتونية يف املجتمع الخليجي وكيفية مواجهتها Cybercrimes in the Gulf Society and How to Tackle Them إعـــــداد رامـــــــــــــي وحـــــــــــــيـد مـنـصــــــــــور باحـــــــث إســـتراتيجي في الشــــــئون اﻷمـــنـــية واﻻقتصـــــــــاد الســــــــياسـي -1- أ ت جملس التعاون لدول اخلليج العربية. اﻷمانة العامة 10 ج إ الجريمة اﻹلكترونية في المجتمع الخليجي وكيفية مواجهتها= cybercrimes in the Gulf:Society and how to tackle them إعداد رامي وحيد منصور ، البحرين . ـ الرياض : جملس التعاون لدول اخلليج العربية ، اﻷمانة العامة؛ 2016م. 286 ص ؛ 24 سم الرقم املوحد ملطبوعات اجمللس : 0531 / 091 / ح / ك/ 2016م. اجلرائم اﻹلكرتونية / / جرائم املعلومات / / شبكات احلواسيب / / القوانني واللوائح / / اجملتمع / مكافحة اجلرائم / / اجلرائم احلاسوبية / / دول جملس التعاون لدول اخلليج العربية. -2- قائمة املحتويات قائمة احملتويات .......................................................................................................... 3 قائمــة اﻷشــكال ........................................................................................................10 مقدمــة الباحــث ........................................................................................................15 مقدمة الدراســة .........................................................................................................21 الفصل التمهيدي )اﻹطار النظري للدراسة( موضوع الدراســة ...................................................................................................... 29 إشــكاليات الدراســة ................................................................................................ -

Perspectives from Hazards, Disaster, and Emergency Management
CARRI Research Report 1 COMMUNITY AND REGIONAL RESILIENCE: PERSPECTIVES FROM HAZARDS, DISASTERS, AND EMERGENCY MANAGEMENT Susan L. Cutter,* Lindsey Barnes, Melissa Berry, Christopher Burton, Elijah Evans, Eric Tate, and Jennifer Webb Hazards and Vulnerability Research Institute Department of Geography University of South Carolina Columbia, South Carolina *Carolina Distinguished Professor and Director of the Hazards and Vulnerability Research Institute Date Published: September 2008 Community and Regional Resilience Initiative RESEARCH FINDINGS ABOUT COMMUNITY AND REGIONAL RESILIENCE One of the commitments of the Community and Regional Resilience Initiative (CARRI) is to understand what resilience is and how to get there, based on research evidence. As one resource for this effort, CARRI has commissioned a number of summaries of existing knowledge about resilience, arising from a number of different research traditions. This paper is one in a series of such summaries, which will be integrated with new resilience explorations in several CARRI partner cities and with further discussions with the research community and other stakeholders to serve as the knowledge base for the initiative. For further information about CARRI’s research component, contact Thomas J. Wilbanks, [email protected], or Sherry B. Wright, [email protected]. CARRI Research Report 1 iii Community and Regional Resilience Initiative COMMUNITY AND REGIONAL RESILIENCE INITIATIVE Oak Ridge National Laboratory’s (ORNL) Community and Regional Resilience Initiative (CARRI) -

Department of State Key Officers List
United States Department of State Telephone Directory This customized report includes the following section(s): Key Officers List (UNCLASSIFIED) 1/17/2017 Provided by Global Information Services, A/GIS Cover UNCLASSIFIED Key Officers of Foreign Service Posts Afghanistan RSO Jan Hiemstra AID Catherine Johnson CLO Kimberly Augsburger KABUL (E) Great Massoud Road, (VoIP, US-based) 301-490-1042, Fax No working Fax, INMARSAT Tel 011-873-761-837-725, ECON Jeffrey Bowan Workweek: Saturday - Thursday 0800-1630, Website: EEO Erica Hall kabul.usembassy.gov FMO David Hilburg IMO Meredith Hiemstra Officer Name IPO Terrence Andrews DCM OMS vacant ISO Darrin Erwin AMB OMS Alma Pratt ISSO Darrin Erwin Co-CLO Hope Williams DCM/CHG Dennis W. Hearne FM Paul Schaefer Algeria HRO Dawn Scott INL John McNamara ALGIERS (E) 5, Chemin Cheikh Bachir Ibrahimi, +213 (770) 08- MGT Robert Needham 2000, Fax +213 (21) 60-7335, Workweek: Sun - Thurs 08:00-17:00, MLO/ODC COL John Beattie Website: http://algiers.usembassy.gov POL/MIL John C. Taylor Officer Name SDO/DATT COL Christian Griggs DCM OMS Sharon Rogers, TDY TREAS Tazeem Pasha AMB OMS Carolyn Murphy US REP OMS Jennifer Clemente Co-CLO Julie Baldwin AMB P. Michael McKinley FCS Nathan Seifert CG Jeffrey Lodinsky FM James Alden DCM vacant HRO Dana Al-Ebrahim PAO Terry Davidson ICITAP Darrel Hart GSO William McClure MGT Kim D'Auria-Vazira RSO Carlos Matus MLO/ODC MAJ Steve Alverson AFSA Pending OPDAT Robert Huie AID Herbie Smith POL/ECON Junaid Jay Munir CLO Anita Kainth POL/MIL Eric Plues DEA Craig M. -

Tensões Em Rede: Os Limites E Possibilidades Da Cidadania Na Internet Universidade Metodista De São Paulo
Tensões em rede: os limiTes e possibilidades da cidadania na inTerneT Universidade Metodista de São Paulo Conselho Diretor Paulo Roberto Lima Bruhn (presidente), Nelson Custódio Fer (vice-presidente), Osvaldo Elias de Almeida (secretário) Titulares: Aires Ademir Leal Clavel, Augusto Campos de Rezende, Aureo Lidio Moreira Ribeiro, Carlos Alberto Ribeiro Simões Junior, Kátia de Mello Santos, Marcos Vinícius Sptizer, Oscar Francisco Alves Suplentes: Regina Magna Araujo, Valdecir Barreros Reitor: Marcio de Moraes Pró-Reitora de Graduação: Vera Lúcia Gouvêa Stivaletti Pró-Reitor de Pós-Graduação e Pesquisa: Fabio Botelho Josgrilberg Faculdade de Comunicação Diretor: Paulo Rogério Tarsitano Conselho de Política Editorial Marcio de Moraes (presidente), Almir Martins Vieira, Fulvio Cristofoli, Helmut Renders, Isaltino Marcelo Conceição, Mário Francisco Boratti, Peri Mesquida (repre sen tante externo), Rodolfo Carlos Martino, Roseli Fischmann, Sônia Maria Ribeiro Jaconi Comissão de Publicações Almir Martins Vieira (presidente), Helmut Renders, José Marques de Melo, Marcelo Módolo, Maria Angélica Santini, Rafael Marcus Chiuzi, Sandra Duarte de Souza Editora executiva Léia Alves de Souza UMESP São Bernardo do Campo, 2012 Dados Internacionais de Catalogação na Publicação (CIP) (Biblioteca Central da Universidade Metodista de São Paulo) T259 Tensões em rede: os limites e possibilidades da cidadania na internet / organização de Sérgio Amadeu da Silveira, Fábio Botelho Josgrilberg. São Bernardo do Campo : Universidade Metodista de São Paulo, 2012. -

1 Before the U.S. COPYRIGHT OFFICE, LIBRARY of CONGRESS
Before the U.S. COPYRIGHT OFFICE, LIBRARY OF CONGRESS In the Matter of Exemption to Prohibition on Circumvention of Copyright Protection Systems for Access Control Technologies Under 17 U.S.C. §1201 Docket No. 2014-07 Reply Comments of the Electronic Frontier Foundation 1. Commenter Information Mitchell L. Stoltz Corynne McSherry Kit Walsh Electronic Frontier Foundation 815 Eddy St San Francisco, CA 94109 (415) 436-9333 [email protected] The Electronic Frontier Foundation (EFF) is a member-supported, nonprofit public interest organization devoted to maintaining the traditional balance that copyright law strikes between the interests of rightsholders and the interests of the public. Founded in 1990, EFF represents over 25,000 dues-paying members, including consumers, hobbyists, artists, writers, computer programmers, entrepreneurs, students, teachers, and researchers, who are united in their reliance on a balanced copyright system that ensures adequate incentives for creative work while promoting innovation, freedom of speech, and broad access to information in the digital age. In filing these reply comments, EFF represents the interests of the many people in the U.S. who have “jailbroken” their cellular phone handsets and other mobile computing devices—or would like to do so—in order to use lawfully obtained software of their own choosing, and to remove software from the devices. 2. Proposed Class 16: Jailbreaking – wireless telephone handsets Computer programs that enable mobile telephone handsets to execute lawfully obtained software, where circumvention is accomplished for the sole purposes of enabling interoperability of such software with computer programs on the device or removing software from the device. 1 3. -

Wireless Evolution •..••••.•.•...•....•.•..•.•••••••...••••••.•••.••••••.••.•.••.••••••• 4
Department of Justice ,"'''''''''<11 Bureau of Investigation ,Operational Technology Division WIRELESS EVDLUTIDN IN THIS Iselil-it:: .. WIRELESS EVOLUTIDN I!I TECH BYTES • LONG TERM EVOLUTIQN ill CLDUD SERVICES • 4G TECHNOLOGY ill GESTURE-RECOGNITION • FCC ON BROADBAND • ACTIVITY-BASED NAVIGATION 'aw PUIi! I' -. q f. 8tH'-.1 Waa 8RI,. (!.EIi/RiW81 R.d-nl)) - 11 - I! .el " Ij MESSAGE FROM MANAGEMENT b7E he bou~~aries of technology are constantly expanding. develop technical tools to combat threats along the Southwest Recognizing the pathway of emerging technology is Border. a key element to maintaining relevance in a rapidly changing technological environment. While this The customer-centric approach calls for a high degree of T collaboration among engineers, subject matter experts (SMEs), proficiency is fundamentally important in developing strategies that preserve long-term capabilities in the face of emerging and the investigator to determine needs and requirements. technologies, equally important is delivering technical solutions To encourage innovation, the technologists gain a better to meet the operational needs of the law enforcement understanding of the operational and investigative needs customer in a dynamic 'threat' environment. How can technical and tailor the technology to fit the end user's challenges. law enforcement organizations maintain the steady-state Rather than developing solutions from scratch, the customer production of tools and expertise for technical collection, while centric approach leverages and modifies the technoloe:v to infusing ideas and agility into our organizations to improve our fit the customer's nFlFlrt~.1 ability to deliver timely, relevant, and cutting edge tools to law enforcement customers? Balancing these two fundamentals through an effective business strategy is both a challenge and an opportunity for the Federal Bureau of Investigation (FBI) and other Federal, state, and local law enforcement agencies.