Using Processes to Improve the Reliability of Browser-Based Applications
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Testing in Webkit-EFL from 0% to 99% in 6 Months
Testing in WebKit-EFL From 0% to 99% in 6 months Leandro Pereira ProFUSION Embedded Systems http://profusion.mobi February 04, 2012 WebKit WebKit I Good standards compliance I Comprised of WebCore, JavaScriptCore, one WebKit for each port WebKit I Heart of Epiphany, Chromium, Safari, Konqueror, and Eve I Comprised of WebCore, JavaScriptCore, one WebKit for each port WebKit I Heart of Epiphany, Chromium, Safari, Konqueror, and Eve I Good standards compliance , JavaScriptCore, one WebKit for each port WebKit I Heart of Epiphany, Chromium, Safari, Konqueror, and Eve I Good standards compliance I Comprised of WebCore , one WebKit for each port WebKit I Heart of Epiphany, Chromium, Safari, Konqueror, and Eve I Good standards compliance I Comprised of WebCore, JavaScriptCore WebKit I Heart of Epiphany, Chromium, Safari, Konqueror, and Eve I Good standards compliance I Comprised of WebCore, JavaScriptCore, one WebKit for each port WebKit I Heart of Epiphany, Chromium, Safari, Konqueror, and Eve I Good standards compliance I Comprised of WebCore, JavaScriptCore, one WebKit for each port, and WTF. I New feature ! new test I Over 9000 28000 tests I Some imported from other test suites (W3C, Mozilla, etc) I Some written by WebKit contributors I One of the reasons WebKit repo is so large (1.8GiB just for tests and expected results) I Most tests are port-independent I Test results are mostly port-dependent Testing in WebKit I Bug fixed ! new test I Over 9000 28000 tests I Some imported from other test suites (W3C, Mozilla, etc) I Some written by WebKit -

Flash Player and Linux
Flash Player and Linux Ed Costello Engineering Manager Adobe Flash Player Tinic Uro Sr. Software Engineer Adobe Flash Player 2007 Adobe Systems Incorporated. All Rights Reserved. Overview . History and Evolution of Flash Player . Flash Player 9 and Linux . On the Horizon 2 2007 Adobe Systems Incorporated. All Rights Reserved. Flash on the Web: Yesterday 3 2006 Adobe Systems Incorporated. All Rights Reserved. Flash on the Web: Today 4 2006 Adobe Systems Incorporated. All Rights Reserved. A Brief History of Flash Player Flash Flash Flash Flash Linux Player 5 Player 6 Player 7 Player 9 Feb 2001 Dec 2002 May 2004 Jan 2007 Win/ Flash Flash Flash Flash Flash Flash Flash Mac Player 3 Player 4 Player 5 Player 6 Player 7 Player 8 Player 9 Sep 1998 Jun 1999 Aug 2000 Mar 2002 Sep 2003 Aug 2005 Jun 2006 … Vector Animation Interactivity “RIAs” Developers Expressive Performance & Video & Standards Simple Actions, ActionScript Components, ActionScript Filters, ActionScript 3.0, Movie Clips, 1.0 Video (H.263) 2.0 Blend Modes, New virtual Motion Tween, (ECMAScript High-!delity machine MP3 ed. 3), text, Streaming Video (ON2) video 5 2007 Adobe Systems Incorporated. All Rights Reserved. Widest Reach . Ubiquitous, cross-platform, rich media and rich internet application runtime . Installed on 98% of internet- connected desktops1 . Consistently reaches 80% penetration within 12 months of release2 . Flash Player 9 reached 80%+ penetration in <9 months . YUM-savvy updater to support rapid/consistent Linux penetration 1. Source: Millward-Brown September 2006. Mature Market data. 2. Source: NPD plug-in penetration study 6 2007 Adobe Systems Incorporated. All Rights Reserved. -

What Is Konqueror the Problem Solution
http://www.linuxhowtos.org/Network/fastkonqueror.pdf What is Konqueror Konqueror is the default browser/file manager for KDE. As time of this writing this is one of only 4 browsers who correctly display the acid2 test (http://www.webstandards.org/act/acid2/) correctly. The Problem One problem of this browser is the lack of an internal dns cache, that means for every http request (each image on a web page) it sends a dns query. Depending on your internet connection and speed of your dns servers, this can slow things down. Solution pdnsd pdnsd is a tiny dns proxy. pdnsd should be available on most distributions. Just install the tool via apt-get, rpm, emerge or whatever your distribution uses. configuring you can use the default example configuration and modify the cache size and dns server ip. My config reads this: global { perm_cache=2048; # cachesize in kB. cache_dir="/var/cache/pdnsd"; run_as="pdnsd"; server_ip = 127.0.0.1; status_ctl = on; paranoid=on; min_ttl=900; # store cache at least 15 minutes. max_ttl=604800; # store cache maximum one week. timeout=10; } server { label= "myisp"; ip = 192.168.0.1; # enter IP of your dns server proxy_only=on; timeout=4; uptest=if; interface=eth0; interval=600; purge_cache=off; } modify /etc/resolv domain yourdomain server 127.0.0.1 start the dns proxy /etc/init.d/pdnsd start page 1 of 2 http://www.linuxhowtos.org/Network/fastkonqueror.pdf check if the server works by pinging a server ping www.linuxhowtos.org if everything works, add the pdnsd to the started services and you are done. -

Actionscript 3.0 from the Ground up Tour
Adobe Presents Colin Moock’s ActionScript 3.0 From the Ground Up Tour Materials provided by O’Reilly Media, Inc. Welcome Key Learning Welcome to the ActionScript 3.0: From the Ground Up Tour! In collaboration with Colin Moock, FITC Design and Technology The following table lists some of today’s most important concepts. Events, O’Reilly, and participating academic institutions around the world, Adobe is thrilled to bring you this world-class day of training. Following the tradition of Flex Camp (http://flex.org/camp/) and the onAIR bus tour (http://onair.adobe.com/), this Concept Example lecture is an important part of Adobe’s ongoing initiative to bring knowledge to the development community. Classes are blueprints for objects. class VirtualPet { At Adobe, we understand that a tool is only useful when you know how to use it. And we’re committed to helping you gain that knowledge. So sit back, get ready for a high-paced day of learning, and most of all have fun! } Objects (or instances) are the things in a program, new VirtualPet() Links and Resources such as a number, a car, a button, a point in time The entire set of notes for today’s lecture are available at: Some classes are built into ActionScript, others are MovieClip, TextField, Sound, String custom-made. http://moock.org/lectures/groundUpAS3 A package contains a class so its name doesn’t package zoo { The code for the virtual zoo application can be obtained at: conflict with other names. class VirtualPet { http://moock.org/eas3/examples/moock_eas3_examples/virtualzoo_final } For a prose version of today’s lecture in book form, see Colin Moock’s Essential ActionScript 3.0 (O’Reilly, 2007). -

Copyrighted Material
05_096970 ch01.qxp 4/20/07 11:27 PM Page 3 1 Introducing Cascading Style Sheets Cascading style sheets is a language intended to simplify website design and development. Put simply, CSS handles the look and feel of a web page. With CSS, you can control the color of text, the style of fonts, the spacing between paragraphs, how columns are sized and laid out, what back- ground images or colors are used, as well as a variety of other visual effects. CSS was created in language that is easy to learn and understand, but it provides powerful control over the presentation of a document. Most commonly, CSS is combined with the markup languages HTML or XHTML. These markup languages contain the actual text you see in a web page — the hyperlinks, paragraphs, headings, lists, and tables — and are the glue of a web docu- ment. They contain the web page’s data, as well as the CSS document that contains information about what the web page should look like, and JavaScript, which is another language that pro- vides dynamic and interactive functionality. HTML and XHTML are very similar languages. In fact, for the majority of documents today, they are pretty much identical, although XHTML has some strict requirements about the type of syntax used. I discuss the differences between these two languages in detail in Chapter 2, and I also pro- vide a few simple examples of what each language looks like and how CSS comes together with the language to create a web page. In this chapter, however, I discuss the following: ❑ The W3C, an organization that plans and makes recommendations for how the web should functionCOPYRIGHTED and evolve MATERIAL ❑ How Internet documents work, where they come from, and how the browser displays them ❑ An abridged history of the Internet ❑ Why CSS was a desperately needed solution ❑ The advantages of using CSS 05_096970 ch01.qxp 4/20/07 11:27 PM Page 4 Part I: The Basics The next section takes a look at the independent organization that makes recommendations about how CSS, as well as a variety of other web-specific languages, should be used and implemented. -

Optimizing Actionscript Bytecode Using LLVM
Optimizing ActionScript Bytecode using Replace with LLVM a graphic White Master 5.5” Tall & 4.3” Wide 10/2/2009 Scott Petersen Adobe Systems, Inc. Copyright 2009 Adobe Systems Incorporated. All rights reserved. Adobe confidential. 1 ActionScript 3 . Adobe Flash/AIR app development language . EcmaScript based – “JavaScript with classes and types” . var x; // implicitly a variant – JS style . var x:int; // x is an int! . var x:*; // explicitly a variant . ActionScript Bytecode (ABC) reminiscent of JVM bytecode . Verified . Stack oriented . Object oriented ® Copyright 2009 Adobe Systems Incorporated. All rights reserved. Adobe confidential. 2 ActionScript 3 . JIT compiler + interpreter + garbage collector + basic support library in around 1.5M uncompressed, 600k compressed for x86 . Open Source Tamarin Project http://www.mozilla.org/projects/tamarin . Straightforward AS3 compiler . Effectively non-optimizing ® Copyright 2009 Adobe Systems Incorporated. All rights reserved. Adobe confidential. 3 ActionScript 3 Performance . Performance for AS => AS3 compiler + Tamarin JIT . Roughly 1.2% of native optimized C (Scimark2 numeric benchmark) . Performance for C => C/LLVM based frontend (Alchemy) + Tamarin JIT . Roughly 30% of native optimized C (Scimark2 numeric benchmark) . Performance for Java => javac + JRE 6 . Roughly 60% of native optimized C (Scimark2 numeric benchmark) ® Copyright 2009 Adobe Systems Incorporated. All rights reserved. Adobe confidential. 4 ActionScript 3 Performance . C code running on the Tamarin JIT is >20x faster than AS3! . Why is C code so fast on Tamarin? . Why is AS3 code so slow on Tamarin? . Alchemy generated code . Avoids some known performance pitfalls in Tamarin . AS3 has a variant type – boxing and unboxing is expensive – Alchemy avoids this . AS3 often does many object allocations, taxing the GC – Alchemy uses a single “ram” object with fast access opcodes . -
Dashboard Comparing To: Site
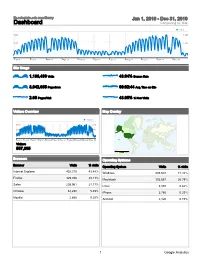
lib.colostate.edu non-library Jan 1, 2010 - Dec 31, 2010 Dashboard Comparing to: Site Visits 7,000 7,000 3,500 3,500 0 0 Jan 4 Feb 6 Mar 11 Apr 13 May 16 Jun 18 Jul 21 Aug 23 Sep 25 Oct 28 Nov 30 Site Usage 1,133,439 Visits 43.94% Bounce Rate 3,042,655 Pageviews 00:02:44 Avg. Time on Site 2.68 Pages/Visit 43.05% % New Visits Visitors Overview Map Overlay Visitors 5,000 5,000 2,500 2,500 0 0 Jan 4 Feb 6 Mar 11 Apr 13 May 16 Jun 18 Jul 21 Aug 23 Sep 25 Oct 28 Nov 30 Visitors 507,395 Visits 1 1,041,862 Browsers Operating Systems Browser Visits % visits Operating System Visits % visits Internet Explorer 492,315 43.44% Windows 808,603 71.34% Firefox 329,946 29.11% Macintosh 303,667 26.79% Safari 239,961 21.17% Linux 9,330 0.82% Chrome 62,280 5.49% iPhone 3,780 0.33% Mozilla 2,866 0.25% Android 2,120 0.19% 1 Google Analytics Screen Resolutions All Traffic Sources Screen Resolution Visits % visits Source/Medium Visits % visits 1280x800 484,793 42.77% (direct) / (none) 472,874 41.72% 1024x768 130,790 11.54% google / organic 230,016 20.29% 1280x1024 118,462 10.45% colostate.edu / referral 195,328 17.23% 1440x900 100,667 8.88% search.colostate.edu / referral 32,475 2.87% 1366x768 63,310 5.59% bing / organic 17,244 1.52% Keywords Top Content Keyword Visits % visits Page Pageviews % visits csu library 45,783 17.07% / 1,089,490 35.81% colorado state university library 15,477 5.77% /databases/ 246,518 8.10% csu libraries 6,841 2.55% /databases/path-to-existing- 192,972 6.34% colostate library 4,943 1.84% /404.html?page=/databases/pat 88,922 2.92% lib.colostate.edu -

Tion Thomas EA Graphics Lunch Presentation
Tion Thomas EA Graphics Lunch Presentation Software Engineering Intern Central Technology Group – Apt Purdue University – MS ‘09 Mentor: Anand Kelkar Manager: Fazeel Gareeboo EA Company Overview Founded in 1982 Largest 3rd party game publisher in the world Net revenue of $3.67 billion in FY 2008 #1 mobile game publisher (acquired JAMDAT) Multi-Platform philosophy Has/owns development studios all over the globe: Bioware/Pandemic (Bioshock, Mercenaries) Criterion (Burnout, Black) Digital Illusions (Battlefield series) Tiburon (Madden) Valve (Half-Life) Crytek (Crysis) EA Company Overview cont… 4 Major Brands/Divisions: EA Sports (FIFA, Madden, NBA, NFL, Tiger Woods, NASCAR) EA Sports Freestyle (NBA Street, NFL Street, FIFA Street, SSX) EA (Medal of Honor, C&C, Need For Speed, SIMS, Spore, Dead Space) POGO (Casual web based games) Currently has 4 entries on the top selling franchises of all time list: #3 - Sims (100 million) #5 - Need For Speed (80 million) #7 – Madden (70 million) #9 - FIFA (65 million) EA Is Unique Sheer size breaks the traditional game developer paradigm Bound by multi-platform technology Long history with titles on almost every console that ever existed Most studios have annual cycles that cannot be broken Both developer and publisher with ownership in many huge studios Origin Of Tiburon Founded by 3 programmers in Longwood, FL First title was MechWarrior for SNES First Madden title was Madden 96 for Genesis, SNES Acquired by EA in 1998 How Tiburon Got Madden Originally, EA contracted Visual -

VULNERABLE by DESIGN: MITIGATING DESIGN FLAWS in HARDWARE and SOFTWARE Konoth, R.K
VU Research Portal VULNERABLE BY DESIGN: MITIGATING DESIGN FLAWS IN HARDWARE AND SOFTWARE Konoth, R.K. 2020 document version Publisher's PDF, also known as Version of record Link to publication in VU Research Portal citation for published version (APA) Konoth, R. K. (2020). VULNERABLE BY DESIGN: MITIGATING DESIGN FLAWS IN HARDWARE AND SOFTWARE. General rights Copyright and moral rights for the publications made accessible in the public portal are retained by the authors and/or other copyright owners and it is a condition of accessing publications that users recognise and abide by the legal requirements associated with these rights. • Users may download and print one copy of any publication from the public portal for the purpose of private study or research. • You may not further distribute the material or use it for any profit-making activity or commercial gain • You may freely distribute the URL identifying the publication in the public portal ? Take down policy If you believe that this document breaches copyright please contact us providing details, and we will remove access to the work immediately and investigate your claim. E-mail address: [email protected] Download date: 07. Oct. 2021 VULNERABLE BY DESIGN: MITIGATING DESIGN FLAWS IN HARDWARE AND SOFTWARE PH.D. THESIS RADHESH KRISHNAN KONOTH VRIJE UNIVERSITEIT AMSTERDAM, 2020 Faculty of Science The research reported in this dissertation was conducted at the Faculty of Science — at the Department of Computer Science — of the Vrije Universiteit Amsterdam This work was supported by the MALPAY consortium, consisting of the Dutch national police, ING, ABN AMRO, Rabobank, Fox-IT, and TNO. -

Move Your Ie Favorites to Firefox Bookmarks
MOVE YOUR IE FAVORITES TO FIREFOX BOOKMARKS If you are moving to Linux from Windows, you will likely want to keep at least some of your Internet Explorer (IE) "Favorites." Here is how to move them to "Bookmarks" for the Firefox and Konqueror browsers on your Linux PC. (If you have been using Firefox under Windows, see this article instead.) Export Your IE Favorites To start, you will need to export the favorites as an HTML file. 1. From the IE File menu, select Import/Export. (If you are using IE 7 and you don't see the menu bar, just tap the <Alt>key once to make it appear.) 2. When the Import Export Wizard launches, click Next. 3. Select Export Favorites and click Next. 4. Select the folder you wish to export and click Next. 5. Choose to export to a file. (Use the default "bookmark.htm" and save it in My Documents.) 6. Click Next. 7. Click Finish to close the wizard. 8. Copy the file to a CD or other media that you can open on your Linux system. Import Your Bookmarks Next, you import the bookmarks into Firefox or Konqueror using the file bookmark.htm file. Firefox 1. In Firefox, select the Bookmarks menu, then Organize Bookmarks. 2. In the Bookmarks Manager select File, Import. 3. Choose From File, then click Next. 4. Select the file from the CD or other location where you put it, and click Open to complete the import. Konqueror 1. In Konqueror, select the Bookmarks menu, then Edit Bookmarks. 2. -

Giant List of Web Browsers
Giant List of Web Browsers The majority of the world uses a default or big tech browsers but there are many alternatives out there which may be a better choice. Take a look through our list & see if there is something you like the look of. All links open in new windows. Caveat emptor old friend & happy surfing. 1. 32bit https://www.electrasoft.com/32bw.htm 2. 360 Security https://browser.360.cn/se/en.html 3. Avant http://www.avantbrowser.com 4. Avast/SafeZone https://www.avast.com/en-us/secure-browser 5. Basilisk https://www.basilisk-browser.org 6. Bento https://bentobrowser.com 7. Bitty http://www.bitty.com 8. Blisk https://blisk.io 9. Brave https://brave.com 10. BriskBard https://www.briskbard.com 11. Chrome https://www.google.com/chrome 12. Chromium https://www.chromium.org/Home 13. Citrio http://citrio.com 14. Cliqz https://cliqz.com 15. C?c C?c https://coccoc.com 16. Comodo IceDragon https://www.comodo.com/home/browsers-toolbars/icedragon-browser.php 17. Comodo Dragon https://www.comodo.com/home/browsers-toolbars/browser.php 18. Coowon http://coowon.com 19. Crusta https://sourceforge.net/projects/crustabrowser 20. Dillo https://www.dillo.org 21. Dolphin http://dolphin.com 22. Dooble https://textbrowser.github.io/dooble 23. Edge https://www.microsoft.com/en-us/windows/microsoft-edge 24. ELinks http://elinks.or.cz 25. Epic https://www.epicbrowser.com 26. Epiphany https://projects-old.gnome.org/epiphany 27. Falkon https://www.falkon.org 28. Firefox https://www.mozilla.org/en-US/firefox/new 29. -

Web Browsers
WEB BROWSERS Page 1 INTRODUCTION • A Web browser acts as an interface between the user and Web server • Software application that resides on a computer and is used to locate and display Web pages. • Web user access information from web servers, through a client program called browser. • A web browser is a software application for retrieving, presenting, and traversing information resources on the World Wide Web Page 2 FEATURES • All major web browsers allow the user to open multiple information resources at the same time, either in different browser windows or in different tabs of the same window • A refresh and stop buttons for refreshing and stopping the loading of current documents • Home button that gets you to your home page • Major browsers also include pop-up blockers to prevent unwanted windows from "popping up" without the user's consent Page 3 COMPONENTS OF WEB BROWSER 1. User Interface • this includes the address bar, back/forward button , bookmarking menu etc 1. Rendering Engine • Rendering, that is display of the requested contents on the browser screen. • By default the rendering engine can display HTML and XML documents and images Page 4 HISTROY • The history of the Web browser dates back in to the late 1980s, when a variety of technologies laid the foundation for the first Web browser, WorldWideWeb, by Tim Berners-Lee in 1991. • Microsoft responded with its browser Internet Explorer in 1995 initiating the industry's first browser war • Opera first appeared in 1996; although it have only 2% browser usage share as of April 2010, it has a substantial share of the fast-growing mobile phone Web browser market, being preinstalled on over 40 million phones.