MAC OS X Forensics: Password Discovery
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mac OS X: an Introduction for Support Providers
Mac OS X: An Introduction for Support Providers Course Information Purpose of Course Mac OS X is the next-generation Macintosh operating system, utilizing a highly robust UNIX core with a brand new simplified user experience. It is the first successful attempt to provide a fully-functional graphical user experience in such an implementation without requiring the user to know or understand UNIX. This course is designed to provide a theoretical foundation for support providers seeking to provide user support for Mac OS X. It assumes the student has performed this role for Mac OS 9, and seeks to ground the student in Mac OS X using Mac OS 9 terms and concepts. Author: Robert Dorsett, manager, AppleCare Product Training & Readiness. Module Length: 2 hours Audience: Phone support, Apple Solutions Experts, Service Providers. Prerequisites: Experience supporting Mac OS 9 Course map: Operating Systems 101 Mac OS 9 and Cooperative Multitasking Mac OS X: Pre-emptive Multitasking and Protected Memory. Mac OS X: Symmetric Multiprocessing Components of Mac OS X The Layered Approach Darwin Core Services Graphics Services Application Environments Aqua Useful Mac OS X Jargon Bundles Frameworks Umbrella Frameworks Mac OS X Installation Initialization Options Installation Options Version 1.0 Copyright © 2001 by Apple Computer, Inc. All Rights Reserved. 1 Startup Keys Mac OS X Setup Assistant Mac OS 9 and Classic Standard Directory Names Quick Answers: Where do my __________ go? More Directory Names A Word on Paths Security UNIX and security Multiple user implementation Root Old Stuff in New Terms INITs in Mac OS X Fonts FKEYs Printing from Mac OS X Disk First Aid and Drive Setup Startup Items Mac OS 9 Control Panels and Functionality mapped to Mac OS X New Stuff to Check Out Review Questions Review Answers Further Reading Change history: 3/19/01: Removed comment about UFS volumes not being selectable by Startup Disk. -
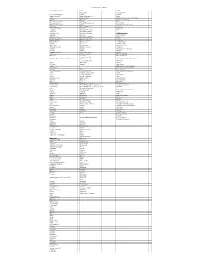
Software List (1-3-2017)
Software List (1-3-2017) Information Commons BU 104 LLCD Adobe Flash Academic online JVC Pro HD Manager Chrome Acrobat Adobe Reader DC Adobe Photoshop CS6 Adobe Itunes Adobe Reader XI Comprehensive Medical Terminology Maple 16 Drive M:\ Glencoe Keyboarding Microsoft Office 2016 Firefox Itunes Microsoft Publisher Irwin/GDP Keyboarding Kurzeil 3000 MS visual studio 2015 Itunes Microsoft Office Suite 2007 Quicktime Kurzweil 3000 v.12 Quick time SPSS for Windows Maple 16 Skills bank real player Microsoft Office 2016 Vista 3-Scanners MS platform installer Windows 7 & 10 Microsoft Visio 2016 Wellington Center sharepoint MS SQL Internet Explorer XPS viewer MS Visual Studio 2015 ITunes Express for desktop Quicken deluxe 2014 McAfee Express for Web VLC Media Player Quicktime MS silverlight Windows 10 " " Media Player Statdisk Scanner Mozilla Firefox Skype 2016 MS silverlight Adobe Reader XI windows dvd maker wolfram cdf player Windows 8 Onedrive Filezilla Microsoft Office Suite 2013 notepad++ Gimp 2 Maple 16 respounds/lockdown opera mobile emulator Statdisk 3D builder VM ware/ vsphere Wolfram CDF Player MS Azure wire shark VLC Media Player cisco packet tracker MACS Software (Information Commons) 3D builder Brunswick Front Desk Computers java development kit Windows 7 System project 2016 Adobe 9 Developer notepad++ Apple Itunes Utilities IBM Iseries access for windows Time Machine Intel Management and Security TextEdit UC 222 Iseries navigator System Preferences Acrobat Reader XI Malware Bytes Anti Malware Stickies Adult Clinical Simulation Mcaffe -

Ipad Educational Apps This List of Apps Was Compiled by the Following Individuals on Behalf of Innovative Educator Consulting: Naomi Harm Jenna Linskens Tim Nielsen
iPad Educational Apps This list of apps was compiled by the following individuals on behalf of Innovative Educator Consulting: Naomi Harm Jenna Linskens Tim Nielsen INNOVATIVE 295 South Marina Drive Brownsville, MN 55919 Home: (507) 750-0506 Cell: (608) 386-2018 EDUCATOR Email: [email protected] Website: http://naomiharm.org CONSULTING Inspired Technology Leadership to Transform Teaching & Learning CONTENTS Art ............................................................................................................... 3 Creativity and Digital Production ................................................................. 5 eBook Applications .................................................................................... 13 Foreign Language ....................................................................................... 22 Music ........................................................................................................ 25 PE / Health ................................................................................................ 27 Special Needs ............................................................................................ 29 STEM - General .......................................................................................... 47 STEM - Science ........................................................................................... 48 STEM - Technology ..................................................................................... 51 STEM - Engineering ................................................................................... -

Macintosh System 7.5 Upgrade Guide 1994.Pdf
Macintosh ••••••••••••••••••••••••••• Upgrade Guide <-»·' c:_ 1 - '--~ I · · ····~ f~··~~ \ ,{"&.--;:... (}.. ... Macintosh • • • Upgrade Guide • Apple Compute.r, Inc. © 1994 Apple Computer, Inc. All rights reserved . Under the copyright laws. this manual may not be copied, in whole or in part. wi thout the written consent of Apple. Your rights to the software are governed by the accompanying soft ware li cense agreement. The Apple logo is a trademark of Apple Computer, Inc., registered in !he U.S. and olher count ries. Use of the "keybomd" Apple logo (Option-Shi 1"1 -K) for commercial purposes witJwut the prior wrillen consenl of Apple may constitule lrademark infringement and unfair compel ilion in violation or federal and state laws. Every efforl has been made to ensure tlult the informati on in this manual is accurate. Apple is not responsib le for printi ng or clerical errors. Apple Computer. Inc. I Infinite Loop Cuperti no. CA 950 14-2084 (408) 996- 10 I0 Apple, the Apple logo, AppleTalk, LaserWritcr, Mac intosh. and PowerBook are trademarks of Apple Computer. Inc., registered in the U.S. and other countries. AppleMail. AppleScri pt. At Ease. Balloon Help, ColorSync, Finder. Plai nTalk, PowerShare, PowerTalk, Quick Draw. QuickTime, and TrucTypc arc trademarks of Apple Computer. Inc. Adobe, Adobe Ill ustrator. Adobe Photoshop. Adobe Type Manager. and PostScript are trademarks of Adobe Systems Incorporated, which may be registered in certain jurisdict ions. Exposure is a registered tmdemark of Preferred Publi shers, Inc. Helvetica and Times are regislered trademarks of Linotype Company. QMS is a registered lrademark of QMS. Inc. Quark X Press is a registered trademark of Quark, Inc. -

Latex on Macintosh
LaTeX on Macintosh Installing MacTeX and using TeXShop, as described on the main LaTeX page, is enough to get you started using LaTeX on a Mac. This page provides further information for experienced users. Tips for using TeXShop Forward and Inverse Search If you are working on a long document, forward and inverse searching make editing much easier. • Forward search means jumping from a point in your LaTeX source file to the corresponding line in the pdf output file. • Inverse search means jumping from a line in the pdf file back to the corresponding point in the source file. In TeXShop, forward and inverse search are easy. To do a forward search, right-click on text in the source window and choose the option "Sync". (Shortcut: Cmd-Click). Similarly, to do an inverse search, right-click in the output window and choose "Sync". Spell-checking TeXShop does spell-checking using Apple's built in dictionaries, but the results aren't ideal, since TeXShop will mark most LaTeX commands as misspellings, and this will distract you from the real misspellings in your document. Below are two ways around this problem. • Use the spell-checking program Excalibur which is included with MacTeX (in the folder / Applications/TeX). Before you start spell-checking with Excalibur, open its Preferences, and in the LaTeX section, turn on "LaTeX command parsing". Then, Excalibur will ignore LaTeX commands when spell-checking. • Install CocoAspell (already installed in the Math Lab), then go to System Preferences, and open the Spelling preference pane. Choose the last dictionary in the list (the third one labeled "English (United States)"), and check the box for "TeX/LaTeX filtering". -

OS X Mountain Lion Includes Ebook & Learn Os X Mountain Lion— Video Access the Quick and Easy Way!
Final spine = 1.2656” VISUAL QUICKSTA RT GUIDEIn full color VISUAL QUICKSTART GUIDE VISUAL QUICKSTART GUIDE OS X Mountain Lion X Mountain OS INCLUDES eBOOK & Learn OS X Mountain Lion— VIDEO ACCESS the quick and easy way! • Three ways to learn! Now you can curl up with the book, learn on the mobile device of your choice, or watch an expert guide you through the core features of Mountain Lion. This book includes an eBook version and the OS X Mountain Lion: Video QuickStart for the same price! OS X Mountain Lion • Concise steps and explanations let you get up and running in no time. • Essential reference guide keeps you coming back again and again. • Whether you’re new to OS X or you’ve been using it for years, this book has something for you—from Mountain Lion’s great new productivity tools such as Reminders and Notes and Notification Center to full iCloud integration—and much, much more! VISUAL • Visit the companion website at www.mariasguides.com for additional resources. QUICK Maria Langer is a freelance writer who has been writing about Mac OS since 1990. She is the author of more than 75 books and hundreds of articles about using computers. When Maria is not writing, she’s offering S T tours, day trips, and multiday excursions by helicopter for Flying M Air, A LLC. Her blog, An Eclectic Mind, can be found at www.marialanger.com. RT GUIDE Peachpit Press COVERS: OS X 10.8 US $29.99 CAN $30.99 UK £21.99 www.peachpit.com CATEGORY: Operating Systems / OS X ISBN-13: 978-0-321-85788-0 ISBN-10: 0-321-85788-7 BOOK LEVEL: Beginning / Intermediate LAN MARIA LANGER 52999 AUTHOR PHOTO: Jeff Kida G COVER IMAGE: © Geoffrey Kuchera / shutterstock.com ER 9 780321 857880 THREE WAYS To learn—prINT, eBOOK & VIDEO! VISUAL QUICKSTART GUIDE OS X Mountain Lion MARIA LANGER Peachpit Press Visual QuickStart Guide OS X Mountain Lion Maria Langer Peachpit Press www.peachpit.com To report errors, please send a note to [email protected]. -

APD Catalog ANZ Revised 171212 Clean Copy
Apple Professional Development Catalogue February 2013 Table of Contents Get the most from your Apple products .............................2 Foundations .........................................................................4 iOS Devices .......................................................................................4 iOS Creativity ...................................................................................5 iOS Productivity ..............................................................................6 iOS for Administrators .................................................................7 OS X .....................................................................................................8 iLife ......................................................................................................9 iWork ................................................................................................10 iBooks Author ...............................................................................11 iTunes U Course Manager ........................................................12 Workflow for Teaching and Learning ..................................13 Curriculum ..........................................................................14 Language Development and Literacy ...............................14 Language Arts ..............................................................................16 Mathematics .................................................................................18 Science ............................................................................................19 -

Tao Huang and Tielei Wang About Us
Towards Discovering Remote Code Execution Vulnerabilities in Apple FaceTime Tao Huang and Tielei Wang About us • Tao Huang • Senior researcher at Pangu Lab • Focusing on iOS/macOS vulnerability discovery • Tielei Wang • PhD, co-founder of Team Pangu, organizer of MOSEC • Leading iOS/macOS security research at Pangu Lab • Regularly present research at BlackHat, POC, etc Motivation • Messaging apps are becoming a hot security research target • Google Project 0 released a series of blog posts about fuzzing messaging apps, including WhatsApp, FaceTime • We decided to take a look at FaceTime Scope of the talk • This talk will cover • Code execution flows while making a FaceTime call • Attack surfaces and vulnerabilities along with the code execution flows • This talk will NOT cover • FaceTime protocol families (e.g., SIP, STUN, RTP/SRTP, etc) • Stream encryption, decryption, and storage • https://blog.quarkslab.com/resources/2013-10-17_imessage-privacy/slides/ iMessage_privacy.pdf Outline • Reverse-engineering FaceTime • Attack surface and vulnerabilities analysis • Conclusion 0 0 0 FaceTime All Missed Input xxx-xxx-xxxx xxx-xxx-xxxx xxx-xxx-xxxx xxx-xxx-xxxx xxx-xxx-xxxx xxx-xxx-xxxx xxx-xxx-xxxx FaceTime is not a single application FaceTime 0 0 0 FaceTime All Missed Input xxx-xxx-xxxx xxx-xxx-xxxx FaceTime.app provides • xxx-xxx-xxxx the basic UI framework FaceTime.App xxx-xxx-xxxx xxx-xxx-xxxx xxx-xxx-xxxx xxx-xxx-xxxx 0 0 0 FaceTime All Missed Input • Manage the call status of xxx-xxx-xxxx FaceTime xxx-xxx-xxxx Respond to UI triggered • xxx-xxx-xxxx -

Apple and Student Assessment 2020
Apple and Student Assessment iPad and Mac are powerful learning devices that you can use for all forms of assessment, including secure exams that can be automatically configured using assessment mode. Approved for standardized assessments in all states, iPad and Mac offer an array of formative learning apps for evaluating students’ progress long-term as they prepare for statewide testing. iPad for state testing As iPad transforms the classroom and expands the possibilities for teaching and learning, educators have also come to rely on iPad for daily learning and student assessment. Schools can disable certain hardware and software features during online assessments to meet test security requirements and prevent test takers from circumventing the assessment and invalidating test results. Assessment mode on iPad Set up iPad for state testing Setup and management for testing on iPad is streamlined and With assessment mode, you can set up iPad for testing in just one simple. Here are just a few of the benefits of assessment on iPad: step: installing your state testing app on iPad. No further setup or management is required. Your state testing app will automatically lock • Compliant. All state summative and interim assessments support and configure iPad for testing each time the app is launched. After a iPad, including Cambium (SBAC) and ACT Aspire. iPad meets student completes the test and signs out from the testing app, iPad hardware and comparability standards and can be configured to automatically returns to general use settings. provide a secure test environment. Check with your state testing agency for their guidelines. Check with your testing provider to confirm assessment mode support. -

Macbook Tips & Tricks
MacBook Tips & Tricks Let’s take a tour USB 3 Headphones MegSafe 2 Dual Microphones MagSafe 2 power port: Charge your notebook. If you accidentally trip over the power cord, it cleanly breaks away. ••USB 3 and Thunderbolt 2 ports: Transfer data at lightning-fast speeds and connect displays like the Apple Thunderbolt Display. ••Headphone port: Connect speakers or headphones. ••Dual microphones: Talk with friends or record audio ThunderBolt 2 USB 3 SDXC card slot (13-inch model only) • SDXC card slot: Transfer photos and videos from your digital camera. SDXC card slot available on 13- inch model only. Note: You can use the cable that came with your camera or a USB card reader to transfer photos and videos to your 11-inch MacBook Air. MacBook Tips & Tricks 1 03-08-16 KB Desktop The desktop is the first thing you see when you turn on your laptop. It has the Apple menu at the top and the Dock at the bottom. Dock MacBook Tips & Tricks 2 03-08-16 KB Launchpad Launchpad makes your desktop look and act like an iPad. All your apps will be available from here. Finder Finder is your file management system. Use it to organize your files or access network drives like your H: drive. System Preferences Two places where you can access system preferences MacBook Tips & Tricks 3 03-08-16 KB Trackpad and Gestures The trackpad replaces the external mouse and utilizes gestures to perform actions on the computer. You can make customize to your style. Keyboard Shortcut link https://support.apple.com/en-us/HT201236 Keyboard shortcuts o Shift + Control + Power -

Mac RAM Analysis
Mac RAM Analysis Written by Catherine Stamm The Senator Patrick Leahy Center for Digital Investigation Champlain College July 17, 2012 Patrick Leahy Center for Digital Investigation (LCDI) Contents 1 Introduction ........................................................................................................................................... 2 1.1 Research Problem ......................................................................................................................... 2 1.2 Field of Research .......................................................................................................................... 2 1.3 Research Questions ....................................................................................................................... 2 1.4 Contributions ................................................................................................................................. 2 1.5 Report Overview ........................................................................................................................... 2 2 Literature Review .................................................................................................................................. 3 3 Methodology and Methods ................................................................................................................... 3 3.1 Tools ............................................................................................................................................. 3 3.2 Overarching Methodology…………..………………………………………...……………….. -

Lab 12 - Introduction to Mac OS X
Lab 12 - Introduction to Mac OS X Z Wikipedii, wolnej encyklopedii. Spis treści 1 MAC OS X 2 Desktop 2.1 Menu Bar 2.2 Dock 3 Windows in MAC OS X 4 Exposé 5 Basic system navigation 5.1 Keyboard layout 5.2 Capturing screen view 6 System Preferences 6.1 Changing system language 7 Terminal 8 Finder 9 Folders structure 10 User management 11 Tasks 12 Useful links MAC OS X Mac OS X is a family of computer operating systems developed, marketed, and sold by Apple Inc., starting March 2001. Since 2002 has been included with all new Macintosh computer systems and it's designed to run exclusively on them. Version 10.5 “Leopard” introduced new graphical user interface, followed until current version - 10.8 “Mountain Lion”, released June 25, 2012. Mac OS X, whose "X" represents the Roman numeral for "10" and is a prominent part of its brand identity, is a Unix-based operating system, built on technologies developed at NeXT between the second half of the 1980s and Apple's purchase of the company in late 1996. Its sixth release Mac OS X v10.5 "Leopard" gained UNIX 03 certification while running on Intel processors. Mac OS X's core is a POSIX compliant operating system (OS) built on top of the XNU kernel, with standard Unix facilities available from the command line interface. Apple released this set of software as a free and open source operating system named Darwin. On top of Darwin, Apple layered a number of components, including the Aqua interface and the Finder, to complete the GUI-based operating system which is Mac OS X.