Nubeva SKI Documentation
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Windows® 10 Iot Enterprise Nel Dettaglio
Windows 10 IoT Enterprise | Il nuovo S.O. Microsoft per applicazioni industriali Windows 10 IoT Enterprise Il nuovo S.O. Microsoft per applicazioni industriali Windows 10 IoT Enterprise Il nuovo S.O. Microsoft per applicazioni industriali Indice PAG 2 White_Paper | Windows 10 IoT © 2019 FEC Italia Windows 10 IoT Enterprise | Il nuovo S.O. Microsoft per applicazioni industriali Introduzione Windows 10 è una piattaforma composta da diversi sistemi operativi suddivisi in due categorie: Windows 10 per applicazioni consumer e office automation e Windows 10 IoT per applicazioni industriali. Windows 10 Windows 10 IoT — Enterprise — Enterprise — Education — Mobile Enterprise — Pro — Core — Home Un unico sistema operativo, molti vantaggi Windows 10 IoT Enterprise è stato progettato per applicazioni industriali moderne e sicure e fornisce tutte le usuali funzionalità di Windows 10 con in aggiunta le funzionalità avanzate di sicurezza incluse nelle versioni precedentemente denominate Embedded (Safety&Locking). Sistemi operativi precedenti Windows 10 IoT Enterprise Standard fully featured PRO Language packs (MUI) Standard&Industrial fully featured Industrial Safety&Locking Safety&Locking Language packs (MUI) Language packs (MUI) Embedded PAG 3 White_Paper | Windows 10 IoT © 2019 FEC Italia Windows 10 IoT Enterprise | Il nuovo S.O. Microsoft per applicazioni industriali Sicurezza e Funzionalità Lockdown Ecco solo alcune delle features che Windows IoT Enterprise offre in termini di sicurezza: » Le ultime tecnologie e funzionalità rivolte alla sicurezza e protezione dei dati azien- dali e delle credenziali di accesso ai dispositivi, con alta resistenza a malware di ultima generazione » Accesso solo a dispositivi autorizzati » Esecuzione solo di applicazioni autorizzate » Lockdown features (UWF, USB filters, AppLocker..) — UWF Unified Write Filter di tasti, quale ad esempio lo swipe da destra Questo filtroprotegge il disco da cambia- che attiva l’Action Center onde evitare accessi menti indesiderati. -
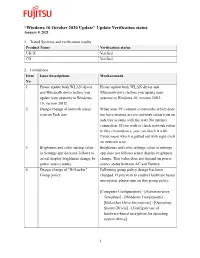
“Windows 10 October 2020 Update” Update Verification Status January 8, 2021
“Windows 10 October 2020 Update” Update Verification status January 8, 2021 1. Tested Systems and verification results Product Name Verification status UH-X Verified CH Verified 2. Limitations Item Issue descriptions Workarounds No 1 Please update both WLAN driver Please update both WLAN driver and and Bluetooth driver before you Bluetooth driver before you update your update your systems to Windows systems to Windows 10, version 20H2. 10, version 20H2. 2 Design change of network status When your PC connect to networks which does icon on Task tray. not have internet access, network status icon on task tray is same with the state No internet connection. If you wish to check network status in this circumstance, you can check it with flyout menu which is pulled out with right click on network icon. 3 Brightness and color setting value Brightness and color settings value in settings in Settings app does not follows to app does not follows actual display brightness actual display brightness change by change. This value does not depend on power power source status. source status between AC and Battery. 4 Design change of "BitLocker" Following group policy design has been Group policy. changed. If you wish to enable Hardware based encryption, please turn on this group policy. [Computer Configuration] - [Administrative Templates] - [Windows Components] - [BitLocker Drive Encryption] - [Operating System Drives] - [Configure use of hardware-based encryption for operating system drives] 1 Previous design: If the policy is not enabled, Hardware based encryption is enabled as default. New design: If the policy is not enabled, Software based encryption is enabled as default. -

WIN-911 7.17 & WEB-911 Xtools 7.13 System Requirements
WIN-911 7.17 & WEB-911 XTools 7.13 System Requirements WIN-911 • Personal computer with 2.1 GHz Pentium 4 processor or higher • Microsoft Windows XP Service Pack 3, Microsoft Windows Server 2003 Service Pack 1 or later, Microsoft Windows 2003 R2, Microsoft Windows 7 Service Pack 1, Microsoft Windows Server 2008 Service Pack 2, Microsoft Server 2008 R2 Service Pack 1, Microsoft Windows 8 & 8.1, Microsoft Server 2012, Microsoft Server 2012 R2, Windows 10. (Only US Versions of Windows) *** TAPI Voice Calls are NOT SUPPORTED in Windows 10 Version 1903 *** • 2GB of RAM. Additional RAM is recommended if additional programs are to be run simultaneously. • 2 GB of hard disk space • Optional Notification Hardware: Dial-out Paging Data fax modem and a dedicated analog phone line Voice Dial-outs/ins Dialogic telephonic card or a TAPI voice modem and a dedicated analog phone line. *** TAPI is NOT SUPPORTED in Windows 10 Version 1903 *** SMS Text Messaging GSM, CDMA or HSPA modem with an activated cellular account. Email Broadband always-on internet connection. Local Announcer Sound card and audio output source. Printing Dot Matrix printer or a printer capable of printing a "line-at-a-time" is recommended. WEB-911 Service • Must be installed on the same machine as WIN-911 • Microsoft .NET 4.0 and Internet Information Services (IIS) are also required • Microsoft Windows XP Service Pack 3, Microsoft Windows Server 2003 Service Pack 1 or later, Microsoft Windows 2003 R2, Microsoft Windows 7 Service Pack 1, Microsoft Windows Server 2008 Service Pack 2, Microsoft Server 2008 R2 Service Pack 1, Microsoft Windows 8 & 8.1, Microsoft Server 2012, Microsoft Server 2012 R2, Windows 10. -

Administrative Guide for Windows 10 and Windows Server Fall Creators Update (1709)
Operational and Administrative Guidance Microsoft Windows 10 and Windows Server Common Criteria Evaluation for Microsoft Windows 10 and Windows Server Version 1903 (May 2019 Update) General Purpose Operating System Protection Profile © 2019 Microsoft. All rights reserved. Microsoft Windows 10 GP OS Administrative Guidance Copyright and disclaimer The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial VLicense (which allows redistribution of the work). To view a copy of this license, visithttp://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious. No association with any real company, organization, product, person or event is intended or should be inferred. -

Reference & Manual
DynaPDF 4.0 Reference & Manual API Reference Version 4.0.59 September 16, 2021 Legal Notices Copyright: © 2003-2021 Jens Boschulte, DynaForms GmbH. All rights reserved. DynaForms GmbH Burbecker Street 24 D-58285 Gevelsberg, Germany Trade Register HRB 9770, District Court Hagen CEO Jens Boschulte Phone: ++49 23 32-666 78 37 Fax: ++49 23 32-666 78 38 If you have questions please send an email to [email protected], or contact us by phone. This publication and the information herein is furnished as is, is subject to change without notice, and should not be construed as a commitment by DynaForms GmbH. DynaForms assumes no responsibility or liability for any errors or inaccuracies, makes no warranty of any kind (express, implied or statutory) with respect to this publication, and expressly disclaims any and all warranties of merchantability, fitness for particular purposes and no infringement of third-party rights. Adobe, Acrobat, and PostScript are trademarks of Adobe Systems Inc. AIX, IBM, and OS/390, are trademarks of International Business Machines Corporation. Microsoft, Windows, and Windows NT are trademarks of Microsoft Corporation. Apple, Mac OS, and Safari are trademarks of Apple Computer, Inc. registered in the United States and other countries. TrueType is a trademark of Apple Computer, Inc. Unicode and the Unicode logo are trademarks of Unicode, Inc. UNIX is a trademark of The Open Group. Solaris is a trademark of Sun Microsystems, Inc. Tru64 is a trademark of Hewlett-Packard. Linux is a trademark of Linus Torvalds. Other company product and service names may be trademarks or service marks of others. -

Metasys Server Installation and Upgrade Instructions Code No
Metasys Server Installation and Upgrade Instructions Code No. LIT-12012162 Software Release 10.0 Issued April 15, 2019 Welcome.....................................................................................................................................3 Getting Started...........................................................................................................................3 Summary of Changes.........................................................................................................................4 Prerequisite Software Checklist for Installation and Upgrade.......................................................4 Recommended OS and SQL Server Combinations.........................................................................7 Upgrade Pre-Work Checklist..............................................................................................................8 Metasys Server Installation.....................................................................................................10 Installing Unified Metasys Server on Desktop Computer.............................................................10 Installing Unified Metasys Server on Server Computer................................................................12 Installing Unified Metasys Server and SCT on Desktop Computer.............................................14 Installing Unified Metasys Server and SCT on Server Computer................................................17 Installing a Split Metasys Server and SCT.....................................................................................20 -

Microsoft Windows Server 2019 Version 1809 Hyper-V
Operational and Administrative Guidance Microsoft Windows Server, Microsoft Windows 10 version 1909 (November 2019 Update), Microsoft Windows Server 2019 version 1809 Hyper-V Common Criteria Evaluation under the Protection Profile for Virtualization, including the Extended Package for Server Virtualization Revision date: January 15, 2021 © 2021 Microsoft. All rights reserved. Microsoft Windows Server and Windows 10 Hyper-V Administrative Guidance Copyright and disclaimer The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial VLicense (which allows redistribution of the work). To view a copy of this license, visithttp://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious. -

Surface Hub 2S Admin Guide
Surface Hub 2S Admin Guide Surface Hub 2S coming soon; Pre-release products shown; products and features subject to regulatory certification/approval, may change, and may vary by country/region. Surface Hub 2S has not yet been authorized under U.S. Federal Communications Commission (FCC) rules; actual sale and delivery is contingent on compliance with applicable FCC requirements. This documentation is an early release of the final documentation, which may be changed prior to final commercial release and is confidential and proprietary information of Microsoft Corporation. This document is provided for informational purposes only and Microsoft makes no warranties, either express or implied, in this document. © 2019. Microsoft Corporation. All rights reserved Introduction .................................................................................................................................................. 1 Welcome to Surface Hub 2S ......................................................................................................................... 1 New User Experience and Features ........................................................................................................................ 1 Microsoft Teams ..................................................................................................................................................... 1 New form factor and hardware changes ................................................................................................................ 2 Surface -

SECURITY ADVISORY Volume 2017-160
Security Advisory | Volume 2017‐160 PRODUCT DESCRIPTION AFFECTED VERSIONS OTHER INFORMATION Microsoft Edge Remote Chakra Scripting Engine Memory Corruption Vulnerability - CVE-2017- Published - May 12, 2017 0223 CVE-2017-0223 Microsoft Edge Remote Chakra Scripting The Chakra JavaScript engine in Microsoft Edge on Windows 10 version 1703, does not properly CVSS - 7.5 Version(s): <=Windows Ver Engine Memory Corruption Vulnerability - render when handling objects in memory, making it prone to a remote code execution vulnerability. Vendor's Advisory - https://www.microsoft.com/en- 10. CVE-2017-0223 A remote attacker could exploit this issue to cause memory corruption and execute arbitrary code us/windows/microsoft-edge in the context of the current user. To exploit this issue the attacker would have to entice the victim http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2017- to visit a maliciously crafted web site or to open a maliciously crafted file. 0223 Published - May 12, 2017 Linux Kernel 4.11.1 and Earlier Local DoS or Other Impact due to Use-After-Free Error - CVE-2017- CVE-CVE-2017-7487 Linux Kernel 4.11.1 and Earlier Local DoS 7487 CVSS - 7.2 or Other Impact due to Use-After-Free The ipxitf_ioctl function in net/ipx/af_ipx.c in the Linux kernel through 4.11.1 mishandles reference Version(s): <=4.11.1 Vendor's Advisory - Error - CVE-2017-7487 counts, which allows local users to cause a denial of service (use-after-free) or possibly have http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2017- unspecified other impact via a failed SIOCGIFADDR ioctl call for an IPX interface. -

Microsoft Windows Common Criteria Evaluation Security Target
Microsoft Common Criteria Security Target Microsoft Windows Common Criteria Evaluation Microsoft Windows 10 version 1803 (April 2018 Update) Microsoft Windows Server version 1803 (April 2018 Update) Security Target Document Information Version Number 0.03 Updated On October 11, 2018 Microsoft © 2018 Page 1 of 119 Microsoft Common Criteria Security Target Version History Version Date Summary of changes 0.01 June 27, 2018 Initial draft 0.02 September 7, 2018 Updates from security target evaluation 0.03 October 11, 2018 Updates from testing, CAVS certificates 0.04 Microsoft © 2018 Page 2 of 119 Microsoft Common Criteria Security Target This is a preliminary document and may be changed substantially prior to final commercial release of the software described herein. The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs- NonCommercial License (which allows redistribution of the work). To view a copy of this license, visit http://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. -

Download Win 10 Version 1809
download win 10 version 1809 How to Manually Install Windows 10 1809 October 2018 Update (Updated) Microsoft released Windows 10 October 2018 Update version 1809 and if you don’t want to get it via Windows Update you can manually install it. Microsoft recently announced that the latest Windows 10 feature update, Windows 10 October 2018 update Version 1809, is now available. In addition to security and performance improvements, this version also includes several new features. In addition, there are improvements to the UI, including Dark Mode for File Explorer, the new Your Phone app, a new screenshot tool, and a lot more. Just like previous feature updates, this one will roll out over Windows Update in staggered phases depending on the system you’re running it on. But some of you might want to install it or do a clean install manually. Manually Install Windows 10 1809. An easy way to manually install the new feature update is to use Microsoft’s own utility. To get started, head to the Windows 10 Download page and click the Update now button to download the Update Assistant tool. From this point on, the process of upgrading is straightforward. Launch the tool, and it will check your system for compatibility and download the update. Note that doing it this way, your current files, apps, and settings will be kept. It’s also worth mentioning that you can cancel the update by clicking in mind you can cancel the update while it’s running if you have second thoughts while it’s running. -

Windows 10 Insider Preview Build 17763 the Final!
Windows 10 Insider Preview Build 17763 The Final! 1 / 5 Windows 10 Insider Preview Build 17763 The Final! 2 / 5 3 / 5 Windows 10 Insider Preview Build 17763 ... that Microsoft is “beginning the phase of checking in final code to prepare for the final release,” in Microsoft's words. Windows 10 Insider Preview Build 17763 will be RTM version ... the final release of Windows Server 2019, Version 1809, #LTSC and #SAC .... on announcement of insider 18298, I installed it. ... Insiders in the Slow ring running older builds need to update to Build 17763 (the final build for the ... -windows-10-insider-preview-build-18290/#JXQz3xoIzbTegKMH.97 ... Build 17763 is released version of Win 10 and you can download ISO from here.. and i roll back to 16232. Windows 10 Insider Preview 16251.0 (rs3_release) (2) error Last failed install attempt on 7/28/2017 - 0x80070643.. Windows 10 October 2018 Update: Could build 17763 be the final ... The latest Windows 10 Insider Preview for version 1809 or Redstone 5 is .... Microsoft will reportedly give Windows 10 preview 17763 to OEMs as the final build ... in conjunction with Windows 10 Insider Preview (Build 17763 or greater). Assassin’s Creed 3 PC Games Download Yet another preview of Windows 10 October 2018 Update (build 17763) outs to Insiders with more fixes to stabilize the final version. Avatar for ... Bullies Children Acting Out: The Rebellion of Attention Seeking Disorder CSS – a guide for the unglued Nero Burning ROM 2018 19.0.00800 Full Crack Serial Number Download Another week, another Insider Preview build for those in the Fast ring! Today's build is 17763, and is one of the last builds Insiders are going to ..