Digital Rights Management Technologies Versus End-User Privacy
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Electronic Arts Reports Q2 Fy11 Financial Results
ELECTRONIC ARTS REPORTS Q2 FY11 FINANCIAL RESULTS Reports Q2 Non-GAAP Revenue and EPS Ahead of Expectations Reaffirms Full-Year Non-GAAP EPS and Net Revenue Guidance FIFA 11 Scores With 8.0 Million Units Sold In Need For Speed Hot Pursuit with Autolog, Ships November 16 REDWOOD CITY, CA – November 2, 2010 – Electronic Arts Inc. (NASDAQ: ERTS) today announced preliminary financial results for its second fiscal quarter ended September 30, 2010. “We had another strong quarter, beating expectations both top and bottom line,” said John Riccitiello, Chief Executive Officer. “We credit our results to blockbusters like FIFA 11 and to innovative digital offerings like The Sims 3 Ambitions and Madden NFL 11 on the iPad.” “EA reaffirms its FY11 non-GAAP guidance,” said Eric Brown, Chief Financial Officer. “EA is the world’s #1 publisher calendar year-to-date and our portfolio is focused on high- growth platforms -- high definition consoles, PC, and mobile.” Selected Quarterly Operating Highlights and Metrics: EA is the #1 publisher on high-definition consoles with 25% segment share calendar year-to date, two points higher than the same period a year ago. In North America and Europe, the high-definition console software market is growing strongly with the combined PlayStation®3 and Xbox 360® segments up 23% calendar year-to-date. The PlayStation 3 software market is up 36% calendar year-to-date. EA is the #1 PC publisher with 27% segment share at retail calendar year-to-date and strong growth in digital downloads of full-game software. For the quarter, EA had six of the top 20 selling games in Western markets with FIFA 11, Madden NFL 11, NCAA® Football 11, NHL®11, Battlefield: Bad Company™ 2 and FIFA 10. -

Bonus Card Infernus 6 2 16Cdcapc002 30 Day
Lot of games for PC and Console Law Court of Bolzano Bankruptcy N. 57/2014 Total Value: 35.698 EUR Prog. Article Description Quantity 1 16CDACDS117 DS GTA CHINATOWN WARS - BONUS CARD INFERNUS 6 2 16CDCAPC002 30 DAY GAME TIME CARD 6 3 16CDCAPC003 60 DAY GAME TIME CARD 2 4 16CDDS169 DS PROFESSOR LAYTON COUNTRY D.MIST *** 3 5 16CDP3083 PS3 NBA 2K9 1 6 16CDP3101 PS3 BLITZ THE LEAGUE II 2 7 16CDPC497 MySims PC 6 8 16CDPP101 PSP FIFA 09 1 9 16CDSW3D004 3DS Nintendogs + Cats And POODLES 3 10 16CDSW3D005 3DS Pilotwings Resort 1 11 16CDSW3D006 3DS SUPER STREET FIGHTER 4 3D EDIT 2 12 16CDSW3D010 3DS RESIDENT EVIL: THE MERCENARIES 8 13 16CDSW3D023 3DS TETRIS 1 14 16CDSW3D024 3DS SUPER POKEMON RUMBLE 2 15 16CDSWDS185 DS DON KING BOXING 3 16 16CDSWDS192 DS RHYTHM PARADISE 1 17 16CDSWDS198 DS MySims Agents 2 18 16CDSWDS273 DS Pokemon SoulSilver + ACCESSORY POKEWAL 8 19 16CDSWDS282 FIFA 10 SPECIAL PRICE 1 20 16CDSWDS302 DS FACE TRAINING DSI 2 21 16CDSWDS311 DS Professor Layton and the Unwound Future 7 22 16CDSWDS320 DS POKEMON BLACK VERSION 6 23 16CDSWDS321 DS POKEMON WHITE VERSION 5 24 16CDSWDS331 DS DRAGON QUEST MONSTERS - JOKER 3 25 16CDSWP2224 BOOGIE 1 26 16CDSWP2340 ROCK BAND 5 27 16CDSWP3040 PS3 TOP SPIN 3 1 28 16CDSWP3118 PS3 F.E.A.R. 2 PROJECT ORIGIN 1 29 16CDSWP3127 PS3 WANTED WEAPONS OF FATE 1 30 16CDSWP3136 PS3 FIGHT NIGHT ROUND 4 1 31 16CDSWP3138 PS3 RED FACTION: GUERRILLA 2 32 16CDSWP3151 PS3 THE BEATLES ROCK BAND 6 33 16CDSWP3152 PS3 WATCHMEN 1 34 16CDSWP3162 PS3 LEGO ROCK BAND 4 35 16CDSWP3163 PS3 Where the Wild Things Are 2 36 16CDSWP3187 BIOSHOCK 2 4 37 16CDSWP3188 BIOSHOCK 2 SPECIAL EDITION 1 38 16CDSWP3194 PS3 SCENE IT? TAKE! TURNS! 2 39 16CDSWP3195 FIFA WORLD CUP SOUTH AFRICA 2010 4 40 16CDSWP3206 GREEN DAY ROCK BAND 4 41 16CDSWP3209 PS3 LEGO HARRY POTTER YEARS 1-4 1 42 16CDSWP3216 PS3 Mafia II 2 43 16CDSWP3223 PS3 L.A. -

Electronic Arts Reports Q1 Fy11 Financial Results
ELECTRONIC ARTS REPORTS Q1 FY11 FINANCIAL RESULTS Reports Q1 FY11 Non-GAAP Net Revenue and EPS Ahead of Expectations Reaffirms Full-Year Non-GAAP EPS and Net Revenue Guidance Q1 Non-GAAP Digital Revenue was $188 Million 2010 FIFA World Cup South Africa Sells-In 3 Million Units To Date Madden NFL 11, With Breakthrough “GameFlow” Feature, Launches August 10 REDWOOD CITY, CA – August 3, 2010 – Electronic Arts Inc. (NASDAQ: ERTS) today announced preliminary financial results for its first fiscal quarter ended June 30, 2010. “We had a solid first quarter, exceeding expectations both top and bottom line.” said John Riccitiello, Chief Executive Officer. “Top quality titles like 2010 FIFA World Cup South Africa, innovative digital offerings for titles like Battlefield: Bad Company 2 and Scrabble on the Apple iPad are driving the business.” “EA is well-positioned for the year ahead and reaffirms its FY11 non-GAAP guidance,” said Eric Brown, Chief Financial Officer. “Digital revenue is expected to grow approximately 30% year over year, to $750 million in the fiscal year.” Q1 FY11 Financial Highlights: Non-GAAP net revenue of $539 million exceeded guidance of $460 million to $500 million. Non- GAAP EPS of ($0.24) exceeded guidance of ($0.35) to ($0.40). As expected, non-GAAP net revenue in Q1 fiscal 11 was lower compared to Q1 fiscal 10 due to a reduced title slate, which went from 10 major titles in Q1 fiscal 10 to six in Q1 fiscal 11. This was somewhat offset by strong digital revenue growth. Quarter Quarter Ended Ended (in millions of $ except -

RENAUD TERNYNCK Mobile Game Exploration & Prototyping Simcity – Cities of Tomorrow Simcity PROFILE EXPERIENCE
RENAUD TERNYNCK Piedmont, CA 415.297.2185 [email protected] PROFILE 15 years of game and interactive design experience with focus on UI/UX. Strong skills in creating, producing and managing team projects as well as creative problem solving, meeting tight deadlines and taking projects from concept to completion. Strong design process, from interfacing with the design and engineering teams to flow diagramming, concept iterations, prototyping, icon design and in-game implementation. Expertise in key production software for interactive design, image manipulation, 2D and 3D motion graphics, 3D modeling, flow diagrams and wireframing. EXPERIENCE EA/Maxis Over 11 years of user experience work for several AAA PC titles. Includes: User flow diagramming, Interactive prototyping, UI Tech research and evaluation. UI tool design, Artist management, Presentation. Mobile Game Exploration & Prototyping [2014 to Present] Director/Senior UI Designer Worked on several UX/UI game prototypes for unreleased mobile title. SimCity – Cities of Tomorrow [2009 to 2013] Lead Senior UI Designer In charge of the SimCity expansion pack user interface. Game Intro Animation. SimCity [2009 to 2013] Co-Lead Senior UI Designer Prototyping, Icon design, Interfacing with Engineering team for in-game implementation. Game Intro Animation. !1 of !3 ”MUiLE” Internal UI Tool [2009 to 2014] Feature and UI Designer Main customer and UX/UI designer for the SimCity home brewed UI tool, developed in EA Webkit. Darkspore [2010 to 2011] Senior UI Designer Co-led the design and implementation of the Darkspore user interface in Scaleform. Spore Galactic Adventures [2008 to 2009] Lead UI Designer Led the design and implementation of the Spore user interface. -

Frequently Asked Questions
Frequently Asked Questions +Collect Windows log files Windows log files can be used to troubleshoot and diagnose issues you may encounter while playing games and watching videos. You may be asked by technical support to provide various log files so they can further help you to solve the problem. Here's how to obtain some of the most commonly used files: DirectX Diagnostic files System Information files Windows System and Application Event log files Installation log files DirectX Diagnostic files DirectX is a programming interface that handles Windows tasks related to multimedia, especially game programming and video. The DirectX Diagnostic file contains information about this interface and its current status. Here’s how to generate a DirectX Diagnostic file: 1. Hold down the Windows key and press R. 2. In the Run dialog box, type DXDIAG and then click OK. This opens the DirectX diagnostic tool. 3. On the bottom of the DirectX Diagnostic Tool window, click Save All Information. 4. When prompted, save the file to your Desktop with the file name DXDIAG. 5. Click Save. 6. Attach the file when you reply to Support. System Information files The Microsoft System Information tool collects system information, such as devices installed on your computer and any associated device drivers. To generate a System Information file: 1. Hold down the Windows key and press R. 2. In the Run dialog box, type MSINFO32 and then click OK. This opens the System Information diagnostic panel. 3. In the menu bar on the left, click File, and then click Save. This will prompt you to choose a location to save the file. -

Troubleshooting Guide
TROUBLESHOOTING GUIDE Solved - Issue with USB devices after Windows 10 update KB4074588 Logitech is aware of a Microsoft update (OS Build 16299.248) which is reported to affect USB support on Windows 10 computers. Support statement from Microsoft "After installing the February 13, 2018 security update, KB4074588 (OS Build 16299.248), some USB devices and onboard devices, such as a built-in laptop camera, keyboard or mouse, may stop working for some users." If you are using Microsoft Windows 10, (OS Build 16299.248) and are having USB-related issues. Microsoft has released a new update KB4090913 (OS Build 16299.251) to resolve this issue. We recommend you follow Microsoft Support recommendations and install the latest Microsoft Windows 10 update: https://support.microsoft.com/en-gb/help/4090913/march5- 2018kb4090913osbuild16299-251. This update was released by Microsoft on March 5th in order to address the USB connection issues and should be downloaded and installed automatically using Windows Update. For instructions on installing the latest Microsoft update, please see below: If you have a working keyboard/mouse If you have a non-working keyboard/mouse If you have a working keyboard/mouse: 1. Download the latest Windows update from Microsoft. 2. If your operating system is 86x-based, click on the second option. If your operating system is 64x-based, click on the third option. 3. Once you have downloaded the update, double-click on the downloaded file and follow the on-screen instructions to complete the update installation. NOTE: If you wish to install the update manually, you can download the 86x and 64x versions of the update from http://www.catalog.update.microsoft.com/Search.aspx?q=KB4090913 If you currently have no working keyboard/mouse: For more information, see the Microsoft article on how to start and use the Windows 10 Recovery Environment (WinRE): https://support.microsoft.com/en-us/help/4091240/usb-devices-may-stop-working-after- installing-the-february-13-2018-upd Do the following: 1. -

Darkspore, a New Breed of Online Action-RPG, Now Available
Darkspore, a New Breed of Online Action-RPG, Now Available PC Exclusive Released Worldwide From April 26 REDWOOD CITY, Calif.--(BUSINESS WIRE)-- Dive into epic levels of customization, vast hero collection, and intense combat where every choice changes the fight! MaxisTM, an Electronic Arts Inc. (NASDAQ:ERTS) studio, today announced that DarksporeTM is available at retail on Windows PC in stores throughout North America and via digital download. Darkspore is an online* action RPG in which players battle co-operatively across alien worlds against a deadly foe, as well as test their skills in multiplayer matches against players around the globe. "The team set out with the goal of bringing something new and unique to the action RPG genre, and Darkspore has accomplished that," said Lucy Bradshaw, General Manager of Maxis Studio. "Darkspore's Creature Creator technology, a first for the genre, provides players with unprecedented creative control over the look of their heroes while also determining in- game strengths and weaknesses. The gameplay experience is different for each person based on the individual choices that are made. The Creature Creator technology, combined with dynamic enemy AI and both co-op multiplayer and a number of PvP options, has resulted in one our most exciting offerings to date. We can't wait to see what players do with the game now that it's in their hands." Unlike any other action RPG, Darkspore enables players to collect an arsenal of living weapons - genetic heroes with different combat abilities - and upgrade them with tens of thousands of collectible body parts and armor. -

Electronic Arts – Simcity in Flames
CORPORATE BRAND MANAGEMENT AND REPUTATION MASTER CASES Game Over? Electronic Arts – SimCity in Flames By: Martin Behm Oskar Leander Dominik Weber First Edition Student Case Papers 2015 Corporate Brand Management and Reputation: Master’s Cases The “Corporate Brand Management and Reputation: Master’s cases” is a case series for applying the case method of teaching and learning in higher education. The cases are relevant to brand strategists in private and public sector organizations, as well as academics and students at universities, business schools, and executive education. The cases are written by groups of master’s students as a course project. The specially developed case format is defined as: “A management decision case describes a real business situation leading up to a question(s) that requires assessment, analysis, and a decision reached by discussion in class. The alternative approaches and recommendations from the class discussion are followed by a description of the choices made by the case company. This description is then discussed by the class.” The student groups select the topics of their case providing updated and relevant insights into the corporate brand management. The cases can be used as “written cases” (handed out and read in advance, later to be discussed in class) and/or as “live case” (presented by the teacher following a discussion in class). Each case includes teaching notes, visuals with speaker’s notes, learning objectives, board plans, and references. The mission of the series is “to develop cases for discussion providing insights into the theory and practice of corporate brand management and reputation, with the intent of bridging the gap between academic teaching and managerial practice.” The series is a result of co-creation between students and teachers at the elective course Corporate Brand Management (BUSN35 – five-credit course/eight-week half-time studies), part of the master’s program International Marketing and Brand Management at Lund School of Economics and Management, Sweden. -
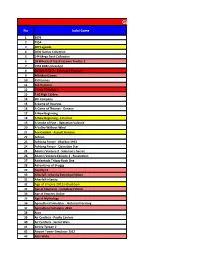
Gara Game No Judul Game
Gara Game No Judul Game 1 3079 2 7554 3 007 Legends 4 1000 Games Collection 5 144 Mega Dash Collection 6 18 Wheels of Steel Extreme Trucker 2 7 1953 KGB Unleashed 8 3d Sex Villa 2 - Everlust [ English ] 9 400 Mini Games 10 450 Games 11 4x4 Hummer 12 7 sins [ English ] 13 7.62 High Calibre 14 9th Company 15 A Game of Dwarves 16 A Game of Thrones - Genesis 17 A New Beginning 18 A New Beginning - Final Cut 19 A Stroke of Fate - Operation Valkyrie 20 A Valley Without Wind 21 Ace Combat - Assault Horizon 22 Achron 23 Achtung Panzer - Kharkov 1943 24 Achtung Panzer - Operation Star 25 Adam's Venture 2 - Solomon's Secret 26 Adam's Venture Episode 3 - Revelations 27 Adelantado Trilogy Book One 28 Adventures of Shuggy 29 Aerofly FS 30 Afterfall - InSanity Extended Edition 31 Afterfall InSanity 32 Age of Empire 2013 Hd edition 33 Age of Empire III - Complete Edition 34 Age of Empires Online 35 Age of Mythology 36 Agricultural Simulator - Historical Farming 37 Agricultural Simulator 2013 38 Aion 39 Air Conflicts - Pacific Carriers 40 Air Conflicts - Secret Wars 41 Airline Tycoon 2 42 Airport Tower Simulator 2012 43 Alan Wake 44 Alan Wake's American Nightmare 45 Alcatraz 46 Alea Jacta Est 47 Alice - Madness Returns 48 Alien Arena 2011 49 Alien Breed 3 - Descent 50 Alien Colonial Marines 51 Aliens Vs. Predator 52 Aliens Vs. Predator 2010 53 All Zombies Must Die 54 Alpha Polaris 55 Alpha Protocol 56 Alternativa 57 Ambulance Simulator 2012 58 American Conquest 59 American Lowriders 60 Amnesia - The Dark Descent 61 Amorous Professor Cherry 62 Angels -

Alexander Peck 1174 Midway Court Novato, CA 94947 Cell (415) 250-4241 [email protected]
Alexander Peck 1174 Midway Court Novato, CA 94947 Cell (415) 250-4241 [email protected] Skills Languages ● C / C++ ● Numerous scripting languages including Lua, Python, Perl, and Javascript ● Java, C# ● Assembly language for various architectures back to 6502 Platforms ● Windows ● Unreal Engine 4 ● some MacOS, web, console and mobile development Experience 2016-present ILMxLAB and Lucasfilm Advanced San Francisco, CA Development Group Engineering manager for ILMxLAB and the Lucasfilm Advanced Development Group. Manage over a dozen engineers, advise on technology, management, and production issues including project bids. Senior programmer on Ralph Breaks VR, a location-based entertainment experience for The VOID. Programmed combat and NPC behavior. Senior programmer on Carne y Arena, a unique high-end VR experience for a museum installation authored with a modified Unreal Engine. Created interactive elements, supported the technical artists, and generally kept development moving smoothly. 2015-2016 Linden Research San Francisco, CA Senior programmer on Project Sansar, a platform for allowing users to create and host virtual worlds. Led a team to create the world editor. Raised the level of project planning on Sansar by proving a team could set and deliver goals over the course of a release. Helped to integrate advanced planning software into the development process and improve communication between the engineering and product teams. 2005-2015 Maxis / Electronic Arts Emeryville, CA Senior Programmer on Spore, a game about the evolution of a single- celled lifeform to a galaxy-spanning empire. Wrote game simulation, locomotion, and pathfinding code for the civilization stage of the game. Also worked on Galactic Adventures, an expansion pack allowing users to create their own missions for the game. -
Biopower and Play: Bodies, Spaces, and Nature in Digital Games
Rutherford & Bose • Biopower and Play 1 Biopower and Play: Bodies, Spaces, and Nature in Digital Games Stephanie Rutherford & Pablo S. Bose Trent University & University of Vermont Abstract This paper takes up as its focus the ongoing fascination with narratives of nature and discourses of control in the worlds of digital games and gaming culture. In a range of gaming genres and franchises we see nature as plot device, as backdrop, as a menacing or chaotic environment in need of management and regulation, and as a rich set of malleable materials ripe for human manipulation. Our attention is on two titles and franchises in particular: BioShock and Spore. Both are representative of narrative tropes concerning nature that have become common to digital games across many genres, platforms and styles. We examine two different aspects of these games: the relationship between their discursive representations of nature and the affective dimensions of their gameplay. A close analysis of these two elements allow us to explore how the immersive qualities of these games offers a biopolitical simulation in which the gamer manages relationships between the human and nonhuman and scripts the conditions of possibility for encountering the natural world. We assert that these digital games offer therefore a unique insight into contemporary understandings of nature, where anxieties and desires about environmental crises are acted out, managed, and temporarily reconciled. Aether Vol. xii, x–x, July 2013 © Copyright 2013, The Center for Geographic Studies • California State University, Northridge 2 Aether: The Journal of Media Geography • Summer 2013 Introduction “How will you create the universe?” This is the question that the developers of Spore, a PC game released in 2008, pose to the gamer. -

Nama Game 1 Sins of a Solar Empire
NAMA GAME 1 SINS OF A SOLAR EMPIRE - REBELLION 2 SLEEPING DOG LIMITED EDITION 3 TOWER WARS 4 SPELLFORCE 2 - FAITH IN DESTINY 5 TRANSFORMERS FALL OF CYBERTRON 6 DARK SOULS - PREPARE TO DIE 7 DARKSIDERS II 8 7554 9 GALAXY ON FIRE 2 10 DEAD ISLAND GAME OF THE YEAR 11 THE ELDER SCROLLS V SKYRIM DAWNDUARD DLC 12 ENDLESS SPACE 13 JAGGED ALLIANCE CROSSFIRE 14 IRON BRIGADE 15 MAGICKA COMPLETE EDITION 16 MAFIA II COMPLETE EDITION 17 ORCS MUST DIE 2 18 PAYDAY THE HEIST DLC 19 MAX PAYNE 3 PATCH V1.0.0.49+DLC 20 LEGEND OF PEGASUS 21 PROTOTYPE 2 22 FINAL FANTASY VII 23 HITMAN SNIPER CHALLENGE 24 THE AMAZING SPIDERMAN 25 EXPANDABLES 2 VIDEO GAME 26 DRIVING SIMULATOR 12 27 THE WALKING DEAD EPISODE 1-3 28 AFTERFALL INSANITY EXTENDED 29 DAMAGE INC PACIFIC SQUADRON WWII 30 THE SIMS 3 SUPERNATURAL 31 I AM ALIVE 32 INQUISITOR 33 TOTAL WAR BATTLES SHOGUN 34 DARKSIDERS II UPDATE 3 35 PRO EVOLUTION SOCCER 2013 36 F1 2012 37 TONY HAWKS PRO SKATER HD 38 BORDERLANDS 2 39 BLACK MESA SOURCE 40 UPRISING 44 41 SECRET FILES 3 42 TRYST 43 THE WALKING DEAD EPISODE 4 44 TORCHLIGHT II 45 R.A.W: Realms of Ancient War 46 Babel Rising 47 Worms Revolution 48 FIFA 13 49 The Testament of Sherlock Holmes 50 Crashtime 5 Undercover 51 NBA 2K13 52 PESEdit.com 2013 Patch 1.0-2.0 53 PESEdit.com 2013 Patch 2.0-2.3.1 54 Borderlands 2 Update 4 incl DLC-SKIDROW 55 Edna and Harvey Harveys New Eyes 56 Doom 3 (2012) BFG Edition 57 Mark of the Ninja 58 Chivalry Medieval Warfare 59 Borderlands 2 Captain Scarlett DLC 60 Lucius 61 Viking Battle for Asgard 62 Giana Sisters Twisted 63 Rocksmith