Concurrent Kleene Algebra
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Symbolic Algorithms for Language Equivalence and Kleene Algebra with Tests Damien Pous
Symbolic Algorithms for Language Equivalence and Kleene Algebra with Tests Damien Pous To cite this version: Damien Pous. Symbolic Algorithms for Language Equivalence and Kleene Algebra with Tests. POPL 2015: 42nd ACM SIGPLAN-SIGACT Symposium on Principles of Programming Languages, Jan 2015, Mumbai, India. hal-01021497v2 HAL Id: hal-01021497 https://hal.archives-ouvertes.fr/hal-01021497v2 Submitted on 1 Nov 2014 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Symbolic Algorithms for Language Equivalence and Kleene Algebra with Tests Damien Pous ∗ Plume team – CNRS, ENS de Lyon, Universite´ de Lyon, INRIA, UMR 5668, France [email protected] Abstract 1. Introduction We propose algorithms for checking language equivalence of finite A wide range of algorithms in computer science build on the abil- automata over a large alphabet. We use symbolic automata, where ity to check language equivalence or inclusion of finite automata. In the transition function is compactly represented using (multi- model-checking for instance, one can build an automaton for a for- terminal) binary decision diagrams (BDD). The key idea consists mula and an automaton for a model, and then check that the latter is in computing a bisimulation by exploring reachable pairs symboli- included in the former. -
Deterministic Finite Automata 0 0,1 1
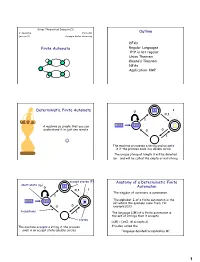
Great Theoretical Ideas in CS V. Adamchik CS 15-251 Outline Lecture 21 Carnegie Mellon University DFAs Finite Automata Regular Languages 0n1n is not regular Union Theorem Kleene’s Theorem NFAs Application: KMP 11 1 Deterministic Finite Automata 0 0,1 1 A machine so simple that you can 0111 111 1 ϵ understand it in just one minute 0 0 1 The machine processes a string and accepts it if the process ends in a double circle The unique string of length 0 will be denoted by ε and will be called the empty or null string accept states (F) Anatomy of a Deterministic Finite start state (q0) 11 0 Automaton 0,1 1 The singular of automata is automaton. 1 The alphabet Σ of a finite automaton is the 0111 111 1 ϵ set where the symbols come from, for 0 0 example {0,1} transitions 1 The language L(M) of a finite automaton is the set of strings that it accepts states L(M) = {x∈Σ: M accepts x} The machine accepts a string if the process It’s also called the ends in an accept state (double circle) “language decided/accepted by M”. 1 The Language L(M) of Machine M The Language L(M) of Machine M 0 0 0 0,1 1 q 0 q1 q0 1 1 What language does this DFA decide/accept? L(M) = All strings of 0s and 1s The language of a finite automaton is the set of strings that it accepts L(M) = { w | w has an even number of 1s} M = (Q, Σ, , q0, F) Q = {q0, q1, q2, q3} Formal definition of DFAs where Σ = {0,1} A finite automaton is a 5-tuple M = (Q, Σ, , q0, F) q0 Q is start state Q is the finite set of states F = {q1, q2} Q accept states : Q Σ → Q transition function Σ is the alphabet : Q Σ → Q is the transition function q 1 0 1 0 1 0,1 q0 Q is the start state q0 q0 q1 1 q q1 q2 q2 F Q is the set of accept states 0 M q2 0 0 q2 q3 q2 q q q 1 3 0 2 L(M) = the language of machine M q3 = set of all strings machine M accepts EXAMPLE Determine the language An automaton that accepts all recognized by and only those strings that contain 001 1 0,1 0,1 0 1 0 0 0 1 {0} {00} {001} 1 L(M)={1,11,111, …} 2 Membership problem Determine the language decided by Determine whether some word belongs to the language. -

On Kleene Algebras and Closed Semirings
On Kleene Algebras and Closed Semirings y Dexter Kozen Department of Computer Science Cornell University Ithaca New York USA May Abstract Kleene algebras are an imp ortant class of algebraic structures that arise in diverse areas of computer science program logic and semantics relational algebra automata theory and the design and analysis of algorithms The literature contains several inequivalent denitions of Kleene algebras and related algebraic structures In this pap er we establish some new relationships among these structures Our main results are There is a Kleene algebra in the sense of that is not continuous The categories of continuous Kleene algebras closed semirings and Salgebras are strongly related by adjunctions The axioms of Kleene algebra in the sense of are not complete for the universal Horn theory of the regular events This refutes a conjecture of Conway p Righthanded Kleene algebras are not necessarily lefthanded Kleene algebras This veries a weaker version of a conjecture of Pratt In Rovan ed Proc Math Found Comput Scivolume of Lect Notes in Comput Sci pages Springer y Supp orted by NSF grant CCR Intro duction Kleene algebras are algebraic structures with op erators and satisfying certain prop erties They have b een used to mo del programs in Dynamic Logic to prove the equivalence of regular expressions and nite automata to give fast algorithms for transitive closure and shortest paths in directed graphs and to axiomatize relational algebra There has b een some disagreement -

1 Alphabets and Languages
1 Alphabets and Languages Look at handout 1 (inference rules for sets) and use the rules on some exam- ples like fag ⊆ ffagg fag 2 fa; bg, fag 2 ffagg, fag ⊆ ffagg, fag ⊆ fa; bg, a ⊆ ffagg, a 2 fa; bg, a 2 ffagg, a ⊆ fa; bg Example: To show fag ⊆ fa; bg, use inference rule L1 (first one on the left). This asks us to show a 2 fa; bg. To show this, use rule L5, which succeeds. To show fag 2 fa; bg, which rule applies? • The only one is rule L4. So now we have to either show fag = a or fag = b. Neither one works. • To show fag = a we have to show fag ⊆ a and a ⊆ fag by rule L8. The only rules that might work to show a ⊆ fag are L1, L2, and L3 but none of them match, so we fail. • There is another rule for this at the very end, but it also fails. • To show fag = b, we try the rules in a similar way, but they also fail. Therefore we cannot show that fag 2 fa; bg. This suggests that the state- ment fag 2 fa; bg is false. Suppose we have two set expressions only involving brackets, commas, the empty set, and variables, like fa; fb; cgg and fa; fc; bgg. Then there is an easy way to test if they are equal. If they can be made the same by • permuting elements of a set, and • deleting duplicate items of a set then they are equal, otherwise they are not equal. -

Context Free Languages II Announcement Announcement
Announcement • About homework #4 Context Free Languages II – The FA corresponding to the RE given in class may indeed already be minimal. – Non-regular language proofs CFLs and Regular Languages • Use Pumping Lemma • Homework session after lecture Announcement Before we begin • Note about homework #2 • Questions from last time? – For a deterministic FA, there must be a transition for every character from every state. Languages CFLs and Regular Languages • Recall. • Venn diagram of languages – What is a language? Is there – What is a class of languages? something Regular Languages out here? CFLs Finite Languages 1 Context Free Languages Context Free Grammars • Context Free Languages(CFL) is the next • Let’s formalize this a bit: class of languages outside of Regular – A context free grammar (CFG) is a 4-tuple: (V, Languages: Σ, S, P) where – Means for defining: Context Free Grammar • V is a set of variables Σ – Machine for accepting: Pushdown Automata • is a set of terminals • V and Σ are disjoint (I.e. V ∩Σ= ∅) •S ∈V, is your start symbol Context Free Grammars Context Free Grammars • Let’s formalize this a bit: • Let’s formalize this a bit: – Production rules – Production rules →β •Of the form A where • We say that the grammar is context-free since this ∈ –A V substitution can take place regardless of where A is. – β∈(V ∪∑)* string with symbols from V and ∑ α⇒* γ γ α • We say that γ can be derived from α in one step: • We write if can be derived from in zero –A →βis a rule or more steps. -

Foundations of Relations and Kleene Algebra
Introduction Foundations of Relations and Kleene Algebra Aim: cover the basics about relations and Kleene algebras within the framework of universal algebra Peter Jipsen This is a tutorial Slides give precise definitions, lots of statements Decide which statements are true (can be improved) Chapman University which are false (and perhaps how they can be fixed) [Hint: a list of pages with false statements is at the end] September 4, 2006 Peter Jipsen (Chapman University) Relation algebras and Kleene algebra September 4, 2006 1 / 84 Peter Jipsen (Chapman University) Relation algebras and Kleene algebra September 4, 2006 2 / 84 Prerequisites Algebraic properties of set operation Knowledge of sets, union, intersection, complementation Some basic first-order logic Let U be a set, and P(U)= {X : X ⊆ U} the powerset of U Basic discrete math (e.g. function notation) P(U) is an algebra with operations union ∪, intersection ∩, These notes take an algebraic perspective complementation X − = U \ X Satisfies many identities: e.g. X ∪ Y = Y ∪ X for all X , Y ∈ P(U) Conventions: How can we describe the set of all identities that hold? Minimize distinction between concrete and abstract notation x, y, z, x1,... variables (implicitly universally quantified) Can we decide if a particular identity holds in all powerset algebras? X , Y , Z, X1,... set variables (implicitly universally quantified) These are questions about the equational theory of these algebras f , g, h, f1,... function variables We will consider similar questions about several other types of algebras, a, b, c, a1,... constants in particular relation algebras and Kleene algebras i, j, k, i1,.. -

Kleene Algebra with Tests and Coq Tools for While Programs Damien Pous
Kleene Algebra with Tests and Coq Tools for While Programs Damien Pous To cite this version: Damien Pous. Kleene Algebra with Tests and Coq Tools for While Programs. Interactive Theorem Proving 2013, Jul 2013, Rennes, France. pp.180-196, 10.1007/978-3-642-39634-2_15. hal-00785969 HAL Id: hal-00785969 https://hal.archives-ouvertes.fr/hal-00785969 Submitted on 7 Feb 2013 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Kleene Algebra with Tests and Coq Tools for While Programs Damien Pous CNRS { LIP, ENS Lyon, UMR 5668 Abstract. We present a Coq library about Kleene algebra with tests, including a proof of their completeness over the appropriate notion of languages, a decision procedure for their equational theory, and tools for exploiting hypotheses of a certain kind in such a theory. Kleene algebra with tests make it possible to represent if-then-else state- ments and while loops in most imperative programming languages. They were actually introduced by Kozen as an alternative to propositional Hoare logic. We show how to exploit the corresponding Coq tools in the context of program verification by proving equivalences of while programs, correct- ness of some standard compiler optimisations, Hoare rules for partial cor- rectness, and a particularly challenging equivalence of flowchart schemes. -

Context-Free Languages ∗
Chapter 17: Context-Free Languages ¤ Peter Cappello Department of Computer Science University of California, Santa Barbara Santa Barbara, CA 93106 [email protected] ² Please read the corresponding chapter before attending this lecture. ² These notes are not intended to be complete. They are supplemented with figures, and material that arises during the lecture period in response to questions. ¤Based on Theory of Computing, 2nd Ed., D. Cohen, John Wiley & Sons, Inc. 1 Closure Properties Theorem: CFLs are closed under union If L1 and L2 are CFLs, then L1 [ L2 is a CFL. Proof 1. Let L1 and L2 be generated by the CFG, G1 = (V1;T1;P1;S1) and G2 = (V2;T2;P2;S2), respectively. 2. Without loss of generality, subscript each nonterminal of G1 with a 1, and each nonterminal of G2 with a 2 (so that V1 \ V2 = ;). 3. Define the CFG, G, that generates L1 [ L2 as follows: G = (V1 [ V2 [ fSg;T1 [ T2;P1 [ P2 [ fS ! S1 j S2g;S). 2 4. A derivation starts with either S ) S1 or S ) S2. 5. Subsequent steps use productions entirely from G1 or entirely from G2. 6. Each word generated thus is either a word in L1 or a word in L2. 3 Example ² Let L1 be PALINDROME, defined by: S ! aSa j bSb j a j b j Λ n n ² Let L2 be fa b jn ¸ 0g defined by: S ! aSb j Λ ² Then the union language is defined by: S ! S1 j S2 S1 ! aS1a j bS1b j a j b j Λ S2 ! aS2b j Λ 4 Theorem: CFLs are closed under concatenation If L1 and L2 are CFLs, then L1L2 is a CFL. -

Formal Languages We’Ll Use the English Language As a Running Example
Formal Languages We’ll use the English language as a running example. Definitions. Examples. A string is a finite set of symbols, where • each symbol belongs to an alphabet de- noted by Σ. The set of all strings that can be constructed • from an alphabet Σ is Σ ∗. If x, y are two strings of lengths x and y , • then: | | | | – xy or x y is the concatenation of x and y, so the◦ length, xy = x + y | | | | | | – (x)R is the reversal of x – the kth-power of x is k ! if k =0 x = k 1 x − x, if k>0 ! ◦ – equal, substring, prefix, suffix are de- fined in the expected ways. – Note that the language is not the same language as !. ∅ 73 Operations on Languages Suppose that LE is the English language and that LF is the French language over an alphabet Σ. Complementation: L = Σ L • ∗ − LE is the set of all words that do NOT belong in the english dictionary . Union: L1 L2 = x : x L1 or x L2 • ∪ { ∈ ∈ } L L is the set of all english and french words. E ∪ F Intersection: L1 L2 = x : x L1 and x L2 • ∩ { ∈ ∈ } LE LF is the set of all words that belong to both english and∩ french...eg., journal Concatenation: L1 L2 is the set of all strings xy such • ◦ that x L1 and y L2 ∈ ∈ Q: What is an example of a string in L L ? E ◦ F goodnuit Q: What if L or L is ? What is L L ? E F ∅ E ◦ F ∅ 74 Kleene star: L∗. -

Finite-State Automata and Algorithms
Finite-State Automata and Algorithms Bernd Kiefer, [email protected] Many thanks to Anette Frank for the slides MSc. Computational Linguistics Course, SS 2009 Overview . Finite-state automata (FSA) – What for? – Recap: Chomsky hierarchy of grammars and languages – FSA, regular languages and regular expressions – Appropriate problem classes and applications . Finite-state automata and algorithms – Regular expressions and FSA – Deterministic (DFSA) vs. non-deterministic (NFSA) finite-state automata – Determinization: from NFSA to DFSA – Minimization of DFSA . Extensions: finite-state transducers and FST operations Finite-state automata: What for? Chomsky Hierarchy of Hierarchy of Grammars and Languages Automata . Regular languages . Regular PS grammar (Type-3) Finite-state automata . Context-free languages . Context-free PS grammar (Type-2) Push-down automata . Context-sensitive languages . Tree adjoining grammars (Type-1) Linear bounded automata . Type-0 languages . General PS grammars Turing machine computationally more complex less efficient Finite-state automata model regular languages Regular describe/specify expressions describe/specify Finite describe/specify Regular automata recognize languages executable! Finite-state MACHINE Finite-state automata model regular languages Regular describe/specify expressions describe/specify Regular Finite describe/specify Regular grammars automata recognize/generate languages executable! executable! • properties of regular languages • appropriate problem classes Finite-state • algorithms for FSA MACHINE Languages, formal languages and grammars . Alphabet Σ : finite set of symbols Σ . String : sequence x1 ... xn of symbols xi from the alphabet – Special case: empty string ε . Language over Σ : the set of strings that can be generated from Σ – Sigma star Σ* : set of all possible strings over the alphabet Σ Σ = {a, b} Σ* = {ε, a, b, aa, ab, ba, bb, aaa, aab, ...} – Sigma plus Σ+ : Σ+ = Σ* -{ε} Strings – Special languages: ∅ = {} (empty language) ≠ {ε} (language of empty string) . -

Transducers and Rational Relations
Transducers and Rational Relations A. Anil & K. Sutner Carnegie Mellon University Spring 2018 1 Rational Relations Properties of Rat Wisdom 3 The author (along with many other people) has come recently to the conclusion that the func- tions computed by the various machines are more important–or at least more basic–than the sets accepted by these devices. D. Scott, “Some Definitional Suggestions for Automata Theory,” 1967 Quoi? 4 Acceptor A machine that checks membership in some language L Σ? ⊆ (a machine that solves a decision problem). Transducer A machine that computes a function f :Σ? Σ? → or a relation R Σ? Σ? ⊆ × We will focus on relations (functions are just a special kind). Example: Lexicographic Order 5 How do we check whether a word u is lexicographically less than v? Find the longest common prefix x (so u = xu0 and v = xv0). Handle the case where u0 = ε or v0 = ε. Otherwise, compare u10 and v10 . Insight: We scan the input once, left-to-right; our decisions require no extra memory. This looks just like a DFA, except there are two inputs. Two-Tape DFA 6 Y a b c a a b ℳ b b a a b a c a N Details? 7 We will not give a careful definition of how a k-tape DFA works and appeal to your intuition instead. The main idea is to use transitions of the form x/y p q −→ where the labels are in the following form: a/b and a/ε and ε/b. You can think of this as the transducer checking for an a on the first tape, and a b on the second tape. -

Kleene Algebras and Logic: Boolean and Rough Set Representations, 3
Kleene Algebras and Logic: Boolean and Rough Set Representations, 3-valued, Rough and Perp Semantics Arun Kumar and Mohua Banerjee Department of Mathematics and Statistics, Indian Institute of Technology, Kanpur 208016, India [email protected], [email protected] Abstract. A structural theorem for Kleene algebras is proved, showing that an element of a Kleene algebra can be looked upon as an ordered pair of sets. Further, we show that negation with the Kleene property (called the ‘Kleene negation’) always arises from the set theoretic com- plement. The corresponding propositional logic is then studied through a 3-valued and rough set semantics. It is also established that Kleene negation can be considered as a modal operator, and enables giving a perp semantics to the logic. One concludes with the observation that all the semantics for this logic are equivalent. Key words: Kleene algebras, Rough sets, 3-valued logic, Perp semantics. 1 Introduction Algebraists, since the beginning of work on lattice theory, have been keenly in- terested in representing lattice-based algebras as algebras based on set lattices. Some such well-known representations are the Birkhoff representation for finite lattices, Stone representation for Boolean algebras, or Priestley representation for distributive lattices. It is also well-known that such representation theorems for classes of lattice-based algebras play a key role in studying set-based se- mantics of logics ‘corresponding’ to the classes. In this paper, we pursue this line of investigation, and focus on Kleene algebras and their representations. We then move to the corresponding propositional logic, denoted LK , and define a arXiv:1511.07165v1 [math.LO] 23 Nov 2015 3-valued, rough set and perp semantics for it.