The WEKA Workbench
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Interstellar Transport of Galactic Cosmic Rays
Washington University in St. Louis Washington University Open Scholarship All Theses and Dissertations (ETDs) 5-24-2012 The nI terstellar Transport of Galactic Cosmic Rays Kelly Lave Washington University in St. Louis Follow this and additional works at: https://openscholarship.wustl.edu/etd Recommended Citation Lave, Kelly, "The nI terstellar Transport of Galactic Cosmic Rays" (2012). All Theses and Dissertations (ETDs). 707. https://openscholarship.wustl.edu/etd/707 This Dissertation is brought to you for free and open access by Washington University Open Scholarship. It has been accepted for inclusion in All Theses and Dissertations (ETDs) by an authorized administrator of Washington University Open Scholarship. For more information, please contact [email protected]. WASHINGTON UNIVERSITY IN ST. LOUIS Department of Physics Dissertation Examination Committee: Martin H. Israel, Chair W. Robert Binns James H. Buckley Ramanath Cowsik Bruce Fegley Jr. Henric Krawczynski Douglas A. Wiens The Interstellar Transport of Galactic Cosmic Rays by Kelly A. Lave A dissertation presented to the Graduate School of Arts and Sciences of Washington University in partial fulfillment of the requirements for the degree of Doctor of Philosophy August 2012 Saint Louis, Missouri c Copyright 2012 by Kelly A. Lave Abstract Using the Cosmic Ray Isotope Spectrometer (CRIS) onboard the Advanced Com- position Explorer (ACE) spacecraft, new and improved high-precision measurements of the elemental composition and energy spectra of galactic cosmic rays with energies from ∼50-550 MeV/nucleon and nuclear charge 5≤Z≤28 are reported here. These results cover observations during two solar minimum periods of the solar cycle, the most recent of which exhibited very low levels of solar activity and the highest galactic cosmic-ray intensities of the space era. -
Information Summaries
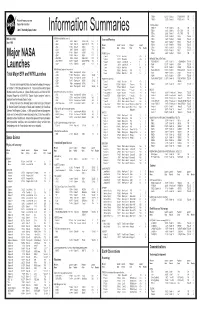
TIROS 8 12/21/63 Delta-22 TIROS-H (A-53) 17B S National Aeronautics and TIROS 9 1/22/65 Delta-28 TIROS-I (A-54) 17A S Space Administration TIROS Operational 2TIROS 10 7/1/65 Delta-32 OT-1 17B S John F. Kennedy Space Center 2ESSA 1 2/3/66 Delta-36 OT-3 (TOS) 17A S Information Summaries 2 2 ESSA 2 2/28/66 Delta-37 OT-2 (TOS) 17B S 2ESSA 3 10/2/66 2Delta-41 TOS-A 1SLC-2E S PMS 031 (KSC) OSO (Orbiting Solar Observatories) Lunar and Planetary 2ESSA 4 1/26/67 2Delta-45 TOS-B 1SLC-2E S June 1999 OSO 1 3/7/62 Delta-8 OSO-A (S-16) 17A S 2ESSA 5 4/20/67 2Delta-48 TOS-C 1SLC-2E S OSO 2 2/3/65 Delta-29 OSO-B2 (S-17) 17B S Mission Launch Launch Payload Launch 2ESSA 6 11/10/67 2Delta-54 TOS-D 1SLC-2E S OSO 8/25/65 Delta-33 OSO-C 17B U Name Date Vehicle Code Pad Results 2ESSA 7 8/16/68 2Delta-58 TOS-E 1SLC-2E S OSO 3 3/8/67 Delta-46 OSO-E1 17A S 2ESSA 8 12/15/68 2Delta-62 TOS-F 1SLC-2E S OSO 4 10/18/67 Delta-53 OSO-D 17B S PIONEER (Lunar) 2ESSA 9 2/26/69 2Delta-67 TOS-G 17B S OSO 5 1/22/69 Delta-64 OSO-F 17B S Pioneer 1 10/11/58 Thor-Able-1 –– 17A U Major NASA 2 1 OSO 6/PAC 8/9/69 Delta-72 OSO-G/PAC 17A S Pioneer 2 11/8/58 Thor-Able-2 –– 17A U IMPROVED TIROS OPERATIONAL 2 1 OSO 7/TETR 3 9/29/71 Delta-85 OSO-H/TETR-D 17A S Pioneer 3 12/6/58 Juno II AM-11 –– 5 U 3ITOS 1/OSCAR 5 1/23/70 2Delta-76 1TIROS-M/OSCAR 1SLC-2W S 2 OSO 8 6/21/75 Delta-112 OSO-1 17B S Pioneer 4 3/3/59 Juno II AM-14 –– 5 S 3NOAA 1 12/11/70 2Delta-81 ITOS-A 1SLC-2W S Launches Pioneer 11/26/59 Atlas-Able-1 –– 14 U 3ITOS 10/21/71 2Delta-86 ITOS-B 1SLC-2E U OGO (Orbiting Geophysical -

Calibration Method and Uncertainty for the Primordial Inflation Explorer
Prepared for submission to JCAP Calibration Method and Uncertainty for the Primordial Inflation Explorer (PIXIE) A. Kogut1 and D.J. Fixsen1;2 1Code 665, Goddard Space Flight Center, Greenbelt, MD 20771 USA 2University of Maryland, College Park, MD 20742 USA E-mail: [email protected], [email protected] Abstract. The Primordial Inflation Explorer (PIXIE) is an Explorer-class mission con- cept to measure cosmological signals from both linear polarization of the cosmic microwave background and spectral distortions from a perfect blackbody. The targeted measurement arXiv:2002.00976v2 [astro-ph.IM] 4 Mar 2021 sensitivity is 2{4 orders of magnitude below competing astrophysical foregrounds, placing stringent requirements on instrument calibration. An on-board blackbody calibrator presents a polarizing Fourier transform spectrometer with a known signal to enable conversion of the sampled interference fringe patterns from telemetry units to physical units. We describe the instrumentation and operations needed to calibrate PIXIE, derive the expected uncertainty for the intensity, polarization, and frequency scales, and show the effect of calibration uncer- tainty in the derived cosmological signals. In-flight calibration is expected to be accurate to a few parts in 106 at frequencies dominated by the CMB, and a few parts in 104 at higher frequencies dominated by the diffuse dust foreground. Keywords: CMBR experiments, CMBR polarisation 1 Introduction The cosmic microwave background (CMB) provides a unique window to the early universe. Its blackbody spectrum points to a hot, dense phase in the early universe, while spatial maps of small temperature perturbations about the blackbody mean provide detailed information on the geometry, constituents, and evolution of the universe. -

Photographs Written Historical and Descriptive
CAPE CANAVERAL AIR FORCE STATION, MISSILE ASSEMBLY HAER FL-8-B BUILDING AE HAER FL-8-B (John F. Kennedy Space Center, Hanger AE) Cape Canaveral Brevard County Florida PHOTOGRAPHS WRITTEN HISTORICAL AND DESCRIPTIVE DATA HISTORIC AMERICAN ENGINEERING RECORD SOUTHEAST REGIONAL OFFICE National Park Service U.S. Department of the Interior 100 Alabama St. NW Atlanta, GA 30303 HISTORIC AMERICAN ENGINEERING RECORD CAPE CANAVERAL AIR FORCE STATION, MISSILE ASSEMBLY BUILDING AE (Hangar AE) HAER NO. FL-8-B Location: Hangar Road, Cape Canaveral Air Force Station (CCAFS), Industrial Area, Brevard County, Florida. USGS Cape Canaveral, Florida, Quadrangle. Universal Transverse Mercator Coordinates: E 540610 N 3151547, Zone 17, NAD 1983. Date of Construction: 1959 Present Owner: National Aeronautics and Space Administration (NASA) Present Use: Home to NASA’s Launch Services Program (LSP) and the Launch Vehicle Data Center (LVDC). The LVDC allows engineers to monitor telemetry data during unmanned rocket launches. Significance: Missile Assembly Building AE, commonly called Hangar AE, is nationally significant as the telemetry station for NASA KSC’s unmanned Expendable Launch Vehicle (ELV) program. Since 1961, the building has been the principal facility for monitoring telemetry communications data during ELV launches and until 1995 it processed scientifically significant ELV satellite payloads. Still in operation, Hangar AE is essential to the continuing mission and success of NASA’s unmanned rocket launch program at KSC. It is eligible for listing on the National Register of Historic Places (NRHP) under Criterion A in the area of Space Exploration as Kennedy Space Center’s (KSC) original Mission Control Center for its program of unmanned launch missions and under Criterion C as a contributing resource in the CCAFS Industrial Area Historic District. -

Abundances 164 ACE (Advanced Composition Explorer) 1, 21, 60, 71
Index abundances 164 CIR (corotating interaction region) 3, ACE (Advanced Composition Explorer) 1, 14À15, 32, 36À37, 47, 62, 108, 151, 21, 60, 71, 170À171, 173, 175, 177, 254À255 200, 251 energetic particles 63, 154 SWICS 43, 86 Climax neutron monitor 197 ACRs (anomalous cosmic rays) 10, 12, 197, CME (coronal mass ejection) 3, 14À15, 56, 258À259 64, 86, 93, 95, 123, 256, 268 CIRs 159 composition 268 pickup ions 197 open flux 138 termination shock 197, 211 comets 2À4, 11 active longitude 25 ComptonÀGetting effect 156 active region 25 convection equation tilt 25 diffusion 204 activity cycle (see also solar cycle) 1À2, corona 1À2 11À12 streamers 48, 63, 105, 254 Advanced Composition Explorer see ACE temperature 42 Alfve´n waves 116, 140, 266 coronal hole 30, 42, 104, 254, 265 AMPTE (Active Magnetospheric Particle PCH (polar coronal hole) 104, 126, 128 Tracer Explorer) mission 43, 197, coronal mass ejections see CME 259 corotating interaction regions see CIR anisotropy telescopes (AT) 158 corotating rarefaction region see CRR Cosmic Ray and Solar Particle Bastille Day see flares Investigation (COSPIN) 152 bow shock 10 cosmic ray nuclear composition (CRNC) butterfly diagram 24À25 172 cosmic rays 2, 16, 22, 29, 34, 37, 195, 259 Cassini mission 181 anomalous 195 CELIAS see SOHO charge state 217 CH see coronal hole composition 196, 217 CHEM 43 convection–diffusion model 213 282 Index cosmic rays (cont.) Energetic Particle Composition Experiment drift 101, 225 (EPAC) 152 force-free approximation 213 energetic particle 268 galactic 195 anisotropy 156, -

Arxiv:1408.5899V3
January 11, 2016 1:30 World Scientific Review Volume - 9.75in x6.5in kaaret-xpol page1 Chapter 1 X-Ray Polarimetry Philip Kaaret Department of Physics and Astronomy, University of Iowa Van Allen Hall, Iowa City, IA 52242, USA [email protected] We review the basic principles of X-ray polarimetry and current detector tech- nologies based on the photoelectric effect, Bragg reflection, and Compton scat- tering. Recent technological advances in high-spatial-resolution gas-filled X-ray detectors have enabled efficient polarimeters exploiting the photoelectric effect that hold great scientific promise for X-ray polarimetry in the 2–10 keV band. Advances in the fabrication of multilayer optics have made feasible the construc- tion of broad-band soft X-ray polarimeters based on Bragg reflection. Develop- ments in scintillator and solid-state hard X-ray detectors facilitate construction of both modular, large area Compton scattering polarimeters and compact devices suitable for use with focusing X-ray telescopes. 1. Polarization The polarization of photons reflects their fundamental nature as electromagnetic waves. A photon is a discrete packet of electric and magnetic fields oriented trans- verse to the direction of motion. The fields evolve in time and position according to Maxwell’s equations. The polarization describes the configuration of the fields. Since the electric and magnetic fields are interrelated by Maxwell’s equations, the configuration of both fields is set by specification of the electric field alone. An electromagnetic plane wave propagating along the z-axis with angular fre- quency ω can be described as a sinusoidally varying electric field of the form arXiv:1408.5899v3 [astro-ph.IM] 8 Jan 2016 E~ =xE ˆ X +ˆyEY =xE ˆ 0X cos(kz ωt)+ˆyE0Y cos(kz ωt + ξ). -

United States Space Program Firsts
KSC Historical Report 18 KHR-18 Rev. December 2003 UNITED STATES SPACE PROGRAM FIRSTS Robotic & Human Mission Firsts Kennedy Space Center Library Archives Kennedy Space Center, Florida Foreword This summary of the United States space program firsts was compiled from various reference publications available in the Kennedy Space Center Library Archives. The list is divided into four sections. Robotic mission firsts, Human mission firsts, Space Shuttle mission firsts and Space Station mission firsts. Researched and prepared by: Barbara E. Green Kennedy Space Center Library Archives Kennedy Space Center, Florida 32899 phone: [321] 867-2407 i Contents Robotic Mission Firsts ……………………..........................……………...........……………1-4 Satellites, missiles and rockets 1950 - 1986 Early Human Spaceflight Firsts …………………………............................……........…..……5-8 Projects Mercury, Gemini, Apollo, Skylab and Apollo Soyuz Test Project 1961 - 1975 Space Shuttle Firsts …………………………….........................…………........……………..9-12 Space Transportation System 1977 - 2003 Space Station Firsts …………………………….........................…………........………………..13 International Space Station 1998-2___ Bibliography …………………………………..............................…………........…………….....…14 ii KHR-18 Rev. December 2003 DATE ROBOTIC EVENTS MISSION 07/24/1950 First missile launched at Cape Canaveral. Bumper V-2 08/20/1953 First Redstone missile was fired. Redstone 1 12/17/1957 First long range weapon launched. Atlas ICBM 01/31/1958 First satellite launched by U.S. Explorer 1 10/11/1958 First observations of Earth’s and interplanetary magnetic field. Pioneer 1 12/13/1958 First capsule containing living cargo, squirrel monkey, Gordo. Although not Bioflight 1 a NASA mission, data was utilized in Project Mercury planning. 12/18/1958 First communications satellite placed in space. Once in place, Brigadier Project Score General Goodpaster passed a message to President Eisenhower 02/17/1959 First fully instrumented Vanguard payload. -

Titan Explorer: the Next Step in the Exploration of a Mysterious World
Titan Explorer: The Next Step in the Exploration of a Mysterious World Principal Investigator: Dr. Joel S. Levine, NASA Langley Research Center Study Manager: Mr. Henry S. Wright, NASA Langley Research Center Cover Image: Image Credit: NASA/JPL/Space Science Institute Image Caption: This natural color image shows Titan's upper atmosphere -- an active place where methane molecules are being broken apart by solar ultraviolet light and the byproducts combine to form compounds like ethane and acetylene. The haze preferentially scatters blue and ultraviolet wavelengths of light, making its complex layered structure more easily visible at the shorter wavelengths used in this image. Inset Image 1: Image Credit: NASA/JPL/University of Arizona Image Caption: The visual and infrared mapping spectrometer instrument onboard Cassini has found an unusual bright, red spot on Titan. This dramatic color (but not true color) image was taken during the April 16, 2005, encounter with Titan. North is to the right. In the center it shows the dark lanes of the "H"-shaped feature discovered from Earth and first seen by Cassini July 2004 shortly after it arrived in the Saturn system Inset Image 2: Image Credit: NASA/JPL/ESA/University of Arizona Image Caption: This image was returned yesterday, January 14, 2005, by the European Space Agency's Huygens probe during its successful descent to land on Titan. This is the colored view, following processing to add reflection spectra data, and gives a better indication of the actual color of the surface. TITAN EXPLORER Titan Explorer: The Next Step in the Exploration of a Mysterious World Final Report for NASA Vision Mission Study per NRA-03-OSS-01 Submitted by: Principal Investigator: Dr. -

Offshore Supply and Support Vessels – History Book
0 Offshore Supply and Support Vessels – History Book JUNE 2020 A Westcoasting Product Compiled by Ko Rusman and Herbert Westerwal [email protected] Compiled by Ko Rusman / Herbert Westerwal June 2020 1 WESTCOASTING 1966 (96-98) Claes Compaen ===> IOSL Discovery ex NVG 5 ‘67 ex Dammtor ‘84 1969 (96-09) Soliman Reys ===> Unicorn ex Deichtor ‘84 INTERNATIONAL OFFSHORE SERVICES 1964 (64-75) Lady Diana ===> Diana Tide ‘86 ===> Golden 1 ‘86 ===> broken up 1965 (65-74) Lady Alison ===> Aberdeen Blazer ‘76 ===> Suffolk Blazer ‘87 ===> Dawn Blazer ‘94 ===> Putford Blazer ‘95 ===> Sea King ‘10 ===> My Lady Norma I (65-70) Lady Anita ===> Volans ’17 ===> broken up (72-74) Lady Christine ===> sank ex Hamme (71-75) Lady Isabelle ===> Nan Hai 501 ===> Continued Existence in doubt ex Wumme (65-74) Lady Laura ===> Decca Mariner ‘80 ===> Bon Venture ‘90 ===> Suffolk Venturer ‘91 ===> Britannia Venturer ‘04 ===> Britannia (65-68) Lady Nathalia ===> sank (72-75) Lady Rana ===> Rana ===> Existence in doubt ex Master Marc (65-84) Master Bruno ===> Mariette S ‘84 ===> Deira ‘87 ===> broken up 1966 (66-75) Lady Astri ===> Astri Tide ‘82 ===> Ocean Pearl ‘14 ===> broken up (66-74) Lady Brigid ===> Lowland Blazer ‘76 ===> Suffolk Enterprise ‘84 ===> Lady Brigid ‘90 ===> Northern Lady ‘95 ===> Lady Brigid ‘99 ===> Ocean Mythology (66-72) Lady Carolina ===> Shai ‘80 ===> Palex Supplier ===> Existence in doubt (66-75) Lady Cecilie ===> Cecilie Tide ‘85 ===> Lady Celica ‘88 ===> Lady Katherine ‘92 ===> Wonder ‘95 ===> Alice ‘01 ===> Cecilia ‘08 ===> Sicilia Queen -

RSA Envision Event Explorer 4.0.3 Installation Guide
RSA enVision Event Explorer 4.1 Installation Guide Revision 1 Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com Trademarks RSA, the RSA Logo, RSA enVision Event Explorer, and EMC are either registered trademarks or trademarks of EMC Corporation in the United States and/or other countries. All other trademarks used herein are the property of their respective owners. For a list of EMC trademarks, go to www.rsa.com/legal/trademarks_list.pdf. License agreement This software and the associated documentation are proprietary and confidential to EMC, are furnished under license, and may be used and copied only in accordance with the terms of such license and with the inclusion of the copyright notice below. This software and the documentation, and any copies thereof, may not be provided or otherwise made available to any other person. No title to or ownership of the software or documentation or any intellectual property rights thereto is hereby transferred. Any unauthorized use or reproduction of this software and the documentation may be subject to civil and/or criminal liability. This software is subject to change without notice and should not be construed as a commitment by EMC. Third-party licenses This product may include software developed by parties other than RSA. The text of the license agreements applicable to third-party software in this product may be viewed in the thirdpartylicenses.pdf file. Note on encryption technologies This product may contain encryption technology. Many countries prohibit or restrict the use, import, or export of encryption technologies, and current use, import, and export regulations should be followed when using, importing or exporting this product. -

Silk Truelog Explorer 20.0
Silk TrueLog Explorer 20.0 Help for Silk Test Micro Focus The Lawn 22-30 Old Bath Road Newbury, Berkshire RG14 1QN UK http://www.microfocus.com © Copyright 1992-2019 Micro Focus or one of its affiliates. MICRO FOCUS, the Micro Focus logo and Silk Test are trademarks or registered trademarks of Micro Focus or one of its affiliates. All other marks are the property of their respective owners. 2019-04-30 ii Contents Getting Started ................................................................................................... 4 TrueLog Explorer Overview .................................................................................................4 Tour of the TrueLog Explorer UI .......................................................................................... 4 Viewer Perspective ................................................................................................... 4 Menu Tree ................................................................................................................ 5 Source Pane .............................................................................................................6 Info Pane .................................................................................................................. 6 Supported Applications ....................................................................................................... 6 Working with TrueLog Explorer ....................................................................... 8 Enabling TrueLog and Setting TrueLog Options in -

5. Spacecraft Environment MAE 342 2016
2/12/20 Spacecraft Environment Space System Design, MAE 342, Princeton University Robert Stengel • Atmospheric characteristics • Loads on spacecraft • Near-earth and space environment • Spacecraft charging • Orbits and orbital decay Copyright 2016 by Robert Stengel. All rights reserved. For educational use only. http://www.princeton.edu/~stengel/MAE342.html 1 1 Launch Phases and Loading Issues-1 § Liftoff § Reverberation from the ground § Random vibrations § Thrust transients § Winds and Transonic Aerodynamics § High-altitude jet stream § Buffeting § Staging § High sustained acceleration § Thrust transients 2 2 1 2/12/20 Launch Phases and Loading Issues-2 § Heat shield separation § Mechanical and pyrotechnic transients § Spin stabilization § Tangential and centripetal acceleration § Steady-state rotation § Separation § Pyrotechnic transients 3 3 Typical Acoustic and Shock Environment (Delta II) Sound Pressure (dB) Peak Acceleration (g) Decibel (dB) ⎛ Measured Power ⎞ ⎛ Measured Amplitude⎞ 10log or 20log 10 ⎝⎜ Reference Power ⎠⎟ 10 ⎝⎜ Reference Amplitude⎠⎟ http://dangerousdecibels.org/education/information-center/decibel-exposure-time-guidelines/ 4 4 2 2/12/20 Transient Loads at Thrusting Cutoff 5 Fortescue, et al, 2003 5 Properties of the Lower Atmosphere • Air density and pressure decay exponentially with altitude • Air temperature and speed of sound are linear functions of altitude US Standard Atmosphere, 1976 6 6 3 2/12/20 Earth’s High-Altitude Explorer-9 Atmosphere Temperature of the Density of the Atmosphere Atmosphere Atmosphere