IDC Marketscape: Worldwide Mobile Threat Management Security Software 2017 Vendor Assessment
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

CIO - Dec15/Jan1, 1996 - Think Tank
CIO - Dec15/Jan1, 1996 - Think Tank http://www.cio.com/archive/010196/davenpor.html L ead ersh i p E n t erp ri se KM / S t o rag e S ecu ri t y I n d u st ri es S o u rci n g T ech n o l o g y CareerCRM E-Business ERP SCM CIO.com Archives Research Viewpoints Blogs CIO Store Newsletters Search Dec 15, 1995 /Jan. 1, 1996 Issue of CIO Magazine The Future of Knowledge Management When we think of how knowledge will be managed in 10 years, all sorts of futuristic images come to mind. There will be Superfast Ethernet jacks on every knowledge worker's neck allowing knowledge downloads. Our heads will have swelled in "Brainiac" fashion to contain the increased knowledge of the new millennium. Intelligent agents (why are there never stupid agents?) will cruise the InterInterNet, seeking out juicy bits of knowledge wherever they hide. The most common Pocket-sized "knowledge appliances" will pull relevant mistake made by knowledge from wireless networks and display it on our futurists is to overstate glasses. technology progress. Technology changes will be incremental, and Even if you're a Harry Houdini, however, don't hold your we've already heard breath until this vision becomes a reality. The most common about most of the mistake made by futurists is to overstate technology progress. technologies that will be Technology changes will be incremental, and we've already widespread in 2005. heard about most of the technologies that will be widespread in 2005. -

Computerworld Storage Networking World
Background SNW SNW Spring 2010 will bring together top information technology executives, leading product and service providers and key industry influencers for the world’s largest conference on storage, infrastructure and the data center. Produced by Computerworld and co-owned by Computerworld and SNIA (The Storage Networking Industry Association), SNW is the largest event for IT professionals, vendors, channel partners, media and analysts involved in storage, data centers, infrastructure and business continuity. SNW also offers the world's largest Expo devoted to storage and related technologies. SNW Spring 2010 will feature more than 150 educational sessions and presentations by dozens of top IT management experts covering today’s most compelling IT topics, including cloud computing, green storage, virtualization and business continuity. SNW attendees will also have the opportunity to participate in tutorials, hands-on labs and SNIA certification workshops, as well as countless networking opportunities. The conference program features an opening keynote by Lawrence Lessig, director of the Edmond J. Safra Foundation Center for Ethics, and professor of law at Harvard Law School. Other featured presenters include Anthony Abbattista, vice president, technology solutions, Allstate Insurance Company, who will share how Allstate is reinventing protection and retirement for consumers by using the latest green technology and reducing the direct impact of its operations on the environment and Martin Gomberg, chief information officer and senior vice president, A&E Television Network, and History Channel, who will discuss the changing face of business continuity and the importance of strategic planning. About Computerworld Computerworld is the leading source of technology news and information for IT influencers worldwide. -

Matchinggiftlistjune02 Revised
Price Brothers Co. RW Beck and Associates SPS Technologies, Inc. Toys 'R Us Price Waterhouse Coopers LLP Ryco Division, Reilly-Whiteman, SPX Corp. Tracor Inc., a Westmark Co. W The Procter & Gamble Co. Inc. Square D. Co. Trady Co. Wachovia Corp. Promark International, Inc. Ryder System, Inc. The Squibb Corp. Transamerica Systems Matching Gifts Walden Books Co. The Promus Cos. Stanadyne Inc. Transco Energy Co. Wallace & Wallace Ltd. Promutual Stanley Works Foundation Transtar, Inc. S The Wallingford Steel Co. Make Your Contributions Go Further! Prospect Hill Foundation Sta-Rite Industries, Inc. The Travelers Companies Wal-Mart Foundation Protection Mutual Insurance Saber Enterprises A.E. Staley Manufacturing Co. Travelers Express Co., Inc. Warnaco Protector Group Safeco Corp. Staley Robeson Ryan St. Treadway Cos., Inc. 1. Check with your company’s personnel department to see Warner-Lambert Co. Provident Life and Accident Saint-Gobain Corp. Foundation Lawrence, Inc. Tremco, Inc. if they have a matching gifts program. Warren Pump, Inc. Insurance Co. The St. Paul Cos. Standard Insurance Co. Tribune Co. Washington Mutual Provident Mutual Life Insurance Sallie Mae The Standard Products Co. TRINOVA Corp. 2. Ask for matching gifts forms for all the members of Washington National Insurance Provident National Bank Salomon, Inc. Stanhome, Inc. Triskelion Ltd. The Washington Post Co. your team. Providian Corp. Sam's Club Foundation Star Enterprise TRW, Inc. Waste Management, Inc. Prudential Insurance Co. Sanders Associates State Farm Insurance Cos. Tufts Healthplan Waters Corp. 3. Review the requirements of your matching gifts program carefully – Purolator Products, Inc. Sandoz Pharmaceuticals Corp. State Mutual Life Assurance Co. Tudor Investment Corporation Watkins-Johnson Co. -

Macworld.Com September 2014
THE OBSESSIVE-COMPULSIVEʼS FAQ: OS X GUIDE TO iTUNES YOSEMITE www.macworld.com September 2014 iOS 8: GAME CHANGER How Appleʼs New Mobile OS Will Transform the iPhone, iPad PLUS APPLE AND BEATS: WHATʼS THE DEAL? Introducing the Haiku® ceiling fan with SenseME™ Technology Forget the Switch Forget the Pull Chain Forget Discomfort SenseME knows when you SenseME monitors the room’s SenseME learns your comfort enter or leave a room, turning temperature and humidity, preferences, tailoring those Haiku on and off automatically. adjusting Haiku’s speed when speed adjustments to what you conditions change. fi nd comfortable. Now the world’s quietest and most energy-efficient ceiling fan is also the smartest. Call 877-835-9115 or visit bigassfans.com/smartass and enter promo code MW914 to learn more about SenseME technology and receive a Haiku info kit. SeptemberINCORPORATING MACUSER 2014 46 COVER STORY OPINION 46 What You Need to 5 From the 20 Mac Reviews Know: iOS 8 and Editor’s Desk Software and hardware for Macs. Is Apple tossing the Jobs playbook? OS X Yosemite iOS CENTRAL Apple’s upgrades to its operating iOS 8 and Education systems will change the way you MACUSER 30 One educator’s wish list for iOS gets use your iPad, iPhone, and Mac. Nine Technologies 10 the magic wand treatment. Apple Disrupted FEATURE 32 iOS Matures With Extensions Apple raised the stakes with a host 33 Continuity Is the Future of Apple 64 Organize Your of innovations in iOS and OS X. 34 Bringing Order to the App Store iTunes Library 12 Developers Take the Stage Tags hold the key to creating an 13 Security in iOS 8 and Yosemite über-organized iTunes library. -

Android (Operating System) 1 Android (Operating System)
android text PDF generated using the open source mwlib toolkit. See http://code.pediapress.com/ for more information. PDF generated at: Sun, 11 Sep 2011 07:56:19 UTC Android (operating system) 1 Android (operating system) Android Home screen displayed by Samsung Nexus S with Google, running Android 2.3 "Gingerbread" Company / developer Google Inc, Open Handset Alliance [1] Programmed in C (core), Java (UI), C++ Working state Current [2] [3] Source model Mixed (free and open source software and proprietary software) Initial release 21 October 2008 [4] [4] Latest stable release Tablets: 3.2 (Honeycomb) Phones: 2.3.6 (Gingerbread) / 2 September 2011 Package manager APK [5] [6] Supported platforms ARM, MIPS, x86 Kernel type Linux kernel (monolithic) Android (operating system) 2 Default user interface Graphical [7] License Apache License 2.0 before 3.0, closed source for 3.0, 3.1 and 3.2: Linux kernel patches under GNU GPL v2 [8] Official website android.com Android is an operating system for mobile devices such as smartphones and tablet computers. It is developed by the Open Handset Alliance led by Google.[9] [10] Google purchased the initial developer of the software, Android Inc., in 2005.[11] The unveiling of the Android distribution on 5 November 2007 was announced with the founding of the Open Handset Alliance, a consortium of 84 hardware, software, and telecommunication companies devoted to advancing open standards for mobile devices.[12] [13] [14] [15] Google released most of the Android code under the Apache License, a free software license.[16] The Android Open Source Project (AOSP) is tasked with the maintenance and further development of Android.[17] Android consists of a kernel based on the Linux kernel, with middleware, libraries and APIs written in C and application software running on an application framework which includes Java-compatible libraries based on Apache Harmony. -

Companies with Matching Gift Programs
Companies with Matching Gift Programs Many companies encourage charitable giving by matching gifts made by their employees. As a 501(c)(3) non-profit organization, CHCA is eligible for matching gifts. Below is a list of companies that have matching gift programs. Even if a company is not listed, they may still have a matching gift program. In addition, not all companies match PK-12 schools. To find out if your company matches gifts made to CHCA, please contact your HR representative. If you need additional assistance, please e-mail Paige Tomlin at [email protected]. A AK Steel 3Com Corporation Albemarle Corp. 3M Company Alco Standard AlliedSignal Inc. Alexander and Baldwin Inc. Allstate Alexander Hamilton Life Abacus Capital Investments Alexander Haas Martin and Partners Abbott Laboratories Al Neyer Altera Corp. Contributions Allegro Microsystems Inc. Accenture Alliance Bernstein Access Fund Alliance Capital Management L.P. ACE INA Foundation Alliance Coal LLC Adams Harkness and Hill Inc. Alliant Techsystems Altria Group Allegiance Corp. and Baxter International Adaptec Foundation Allendale Insurance Foundation AMBAC Indemnity American Natl Bank & Trust ADC Telecommunications American Intl Group, Inc. AMD Corporate Giving American Standard Found Adobe Systems Inc. Amgen Inc. ADP Foundation AMN Healthcare Services American Express Co. AmSouth BanCorp. A & E Television Networks American Stock Exchange AEGON TRANSAMERICA Ameriprise Financial AEP Ameritech Corp. AES Corporation AMETEK / Sealtron A.E. Staley Manufacturing Co. AMSTED Industries Inc. American Fidelity Corp. Amylin Pharmaceuticals Aetna Foundation, Inc. Anadarko Petroleum Corp. American General Corp. Analytics Operations Engineering AG Communications Systems Analog Devices Inc. American Honda Motor Co. Avon Products Foundation, Inc. -
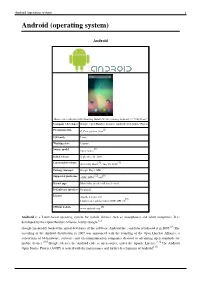
Android (Operating System) 1 Android (Operating System)
Android (operating system) 1 Android (operating system) Android Home screen displayed by Samsung Galaxy Nexus, running Android 4.1 "Jelly Bean" Company / developer Google, Open Handset Alliance, Android Open Source Project [1] Programmed in C, C++, python, Java OS family Linux Working state Current [2] Source model Open source Initial release September 20, 2008 [3] [4] Latest stable release 4.1.1 Jelly Bean / July 10, 2012 Package manager Google Play / APK [5] [6] Supported platforms ARM, MIPS, x86 Kernel type Monolithic (modified Linux kernel) Default user interface Graphical License Apache License 2.0 [7] Linux kernel patches under GNU GPL v2 [8] Official website www.android.com Android is a Linux-based operating system for mobile devices such as smartphones and tablet computers. It is developed by the Open Handset Alliance, led by Google.[2] Google financially backed the initial developer of the software, Android Inc., and later purchased it in 2005.[9] The unveiling of the Android distribution in 2007 was announced with the founding of the Open Handset Alliance, a consortium of 86 hardware, software, and telecommunication companies devoted to advancing open standards for mobile devices.[10] Google releases the Android code as open-source, under the Apache License.[11] The Android Open Source Project (AOSP) is tasked with the maintenance and further development of Android.[12] Android (operating system) 2 Android has a large community of developers writing applications ("apps") that extend the functionality of the devices. Developers write primarily in a customized version of Java.[13] Apps can be downloaded from third-party sites or through online stores such as Google Play (formerly Android Market), the app store run by Google. -

E N Terp Rise D Ata & a N Alytics
FEBRUARY 2017 Enterprise Data & Analytics Data & Analytics MARKET UPDATE M&AMARLIN & ASSOCIATES INVESTMENT BANKING AND STRATEGIC ADVISORY TO THE TECHNOLOGY, INFORMATION AND HEALTHCARE INDUSTRIES New York San Francisco Washington, D.C. Toronto www.MarlinLLC.com © Marlin & Associates Holdings LLC, All Right Reserved Enterprise DEAR CLIENTS AND FRIENDS, Big Data, Analytics, and Politics. Our February 2017 Enterprise Data & Analytics Update Please see our latest update on m&a trends for the four segments of the Enterprise Data and Analytics sector that we follow, and sometimes lead, below. In December we wrote a blog post on why Data & Analytics failed the pundits predicting the outcome of the Brexit referendum and our recent Presidential Election. A few weeks ago, in our Fintech Market Update, we noted that, in spite of the fears raised by many of these same pundits, following both events, interest rates did not skyrocket – they fell; and securities markets did not crater; they rose. The sky has not fallen...yet… There are many drivers of this continued growth. Among them, we note three: The first is simply optimism. We meet with buyers, sellers, and investors every day and it is clear that in the aggregate, most are willing to bet that our institutions and sanity will prevail regardless of the breathless pronouncements of politicians and pundits. I hope they are correct. If that optimism should fail – watch out for falling objects from the sky. The second driver of growth is the abundance of cash. There is over $1 trillion of committed, unspent capital available for m&a transactions out there - and a lot of people whose job is to spend it as long as the values are rising…. -

Company Matching
Company Matching 4850 Clarewood Drive, Oakland, CA 94618 | 510.547.3146 | www.sttheresaschool.org BAY AREA COMPANIES WITH MATCHING GIFT PROGRAMS Adaptec, Inc. eBay Morrison & Foerster Adobe Systems Electronic Arts, Inc. Motorolla Advanced Fibre Communications Evelyn and Walter Haas, Jr. Fund National Semiconductor Corp. Aetna Foundation ExxonMobil Nokia Air Products & Chemicals, Inc. First Data Corporation NORCAL Mutual Insurance Alain Pinel Realtors First Solar Northern Trust Company ALZA Corporation FleetBoston Financial Novartis US AMD - Advanced Micro Devices Flora Family Foundation Novellus System American Express Corporation Franklin Templeton Oracle Corporation American International Group, Inc. Fremont Group. PBG - PepsiCo Amgen Gap Inc. Peninsula Community Foundation Apple Gartner, Inc. Pfizer Applied Materials Genentech, Inc. PG&E Applied Signal Tech General Mills Providian Financial Aspect Global Giving Program General Re Corporation Prudential AT&T GlaxoSmithKline Quaker Oats Autodesk, Inc. Google Qualcomm Inc. Automatic Data Processing, Inc. Grainger, Inc. Rockefeller Foundation Avaya Communication GreenPoint Foundation Rosendin Electric, Inc. BAE Systrems Guidant, Inc. Salesforce Bank of America Hancock Financial Services, Inc. SAP Barclays Global Investors Harcourt Education SBC Baxter International Hewlett Packard Schwab Corporation Birkenstock Footprint Sandals, Inc. Higashi Sephora Blue Shield of California Home Depot Sony Electronics Inc. Boeing Household International SPX Corporation BP Foundation IBM Corporation Starbucks -

MACWORLD 1 Working Mac 64 Unleash Google Drive Use Google’S Web Productivity Suite Effectively, with These Tips
You like the way it looks. You’ll love the way it feels. The award-winning design, quality craftsmanship and unprecedented performance of a Big Ass Fan® are always in style. Hidden behind a seamless fit and finish, Haiku’s revolutionary motor features Whoosh®, a proprietary algorithm that simulates a natural breeze to keep you feeling up to 40% cooler*. This Big Ass Fan is recognized by Popular Science as the world’s quietest ceiling fan and rated by ENERGY STAR® as the world’s most energy efficient. With 16 unique brightness settings and a digital dimmer, Haiku’s patent-pending LED module delivers 80% greater efficiency than traditional bulbs over a lifespan of 50,000 hours. Visit haikufan.com/OFFER and use promo code MW314 to receive a free Haiku® info kit. HAIKUFAN.COM/OFFER 877-835-9115 *Human thermal sensation to air movement frequency, Yizai Xia, Rongyi Zhao and Weiquan Xu (2000) Incorporating MacUser MARCH 2014 Features 42 What Everyone Should 12 Know About OS X Mavericks Get up to speed with the most useful new features of Apple’s latest operating system. 57 Mac Buying Guide We compare the features of Apple’s six current computers, to help you pick the right one. Opinion 5 From the Editor’s Desk The real enemy is complacency. 10 Feedback Readers respond. MacUser 12 New Mac Pro Really Is for Pros Apple’s new desktop computer is surprisingly small—and powerful. 18 Why Apple Put Maps in Mavericks 20 Consumer Faith in Apple Shaken 22 Orientation-Neutral USB Cables 24 Apple Buys Topsy, PrimeSense 25 Apple Wins $290 Million Suit PLUS: Hot Stuff 26 28 Mac Gems Apps for desktop Pandora, background sounds, and more. -

Macworld.Com
SEPTEMBER 2015 MACWORLD.COM OS X EL CAPITAN FIRST LOOK Jason Snell turns over every rock in the OS X 10.11 beta PLUS: PARKING AND VALET APPS, PUT TO THE TEST Book smart contactless scanner Floating optical array Curvature correction Page turn detection http://ez.com/macwor © 2015 Fujitsu Computer Products of America, Inc. All rights reserved. Fujitsu and the Fujitsu logo are registered trademarks of Fujitsu Ltd. All other trademarks are the property of their respective owners. INCORPORATING MACUSER September 2015 CONTENTS MacUser The 5 biggest takeaways of Apple’s Q3 2015 quarterly earnings 6 Saying goodbye to a beloved 2008 MacBook Pro 12 MacUser Reviews 18 Hot Stuff 34 iOS Central In its second year, Apple Pay is ready to cash in 38 Use parking apps to find lots, garages, valet, and meters 44 iOS Central Reviews 52 What’s new at the App Store 64 iOS Accessories 65 Working Mac How to configure a cheap, secure RAID backup system 88 Why a strong password doesn’t help as much as a unique one 94 Playlist In praise of the iPod shuffle 98 Ask the iTunes Guy 101 Staff Picks: Our very favorite podcasts 106 Help Desk Mac 911: When iWork doesn’t 110 First look at OS X El Capitan public beta 68 3 MASTHEAD CCO & SVP, U.S. MEDIA AT IDG John Gallant EDITOR IN CHIEF, CONSUMER BRANDS Jon Phillips EXECUTIVE EDITOR Susie Ochs DESIGN DIRECTOR Rob Schultz Editorial SENIOR EDITOR Roman Loyola ASSOCIATE MANAGING EDITOR Leah Yamshon STAFF WRITERS Caitlin McGarry, Oscar Raymundo SENIOR CONTRIBUTORS Adam C. -
How Not to Get "Offshored" | Computerworld Blogs Page 1 of 2
In searching the publicly accessible web, we found a webpage of interest and provide a snapshot of it below. Please be advised that this page, and any images or links in it, may have changed since we created this snapshot. For your convenience, we provide a hyperlink to the current webpage as part of our service. How not to get "offshored" | Computerworld Blogs Page 1 of 2 IDG Network: Login Register Computerworld Blogs > blogs > Robert L. Mitchell Featured Blogs About Robert L. IT Blogwatch How not to get "offshored" Featured Bloggers Mitchell Blog Topics By Robert L. Mitchell Robert Mitchell is a National Mar 31 2006 - 12:12pm BI/Data Management Correspondent for Careers Here's my three-step Development Computerworld weekend reading program Government/Regulations View full user profile Hardware for IT folks who are IT Management concerned about offshoring Recent blog posts Mobile/Wireless and IT careers. Networking Shark Tank: Because that Security FIRST STOP: THE ACM would be too easy Software REPORT Enterprise Applications The changing face of Operating Systems IT professionals interested performance statistics Linux in keeping ahead of the Macintosh BI with Microsoft Office offshoring wave will want to Windows Why I don’t allow any P2P Storage read through the recently sharing released Globalization and Knowledge Centers Offshoring of Software, Hey, Microsoft! Virtualize Select one... (and no need to whistle) written by the Association Partner Zones for Computing Machinery's Content Aware Storage – (ACM) Job Migration Task Vendor Lock-in is Re-born Blade-Ready Data Center Data Explosion Zone Force. The executive Got hacked? 11 things to Enterprise Infrastructure Zone summary is a must read for next Enterprise Server Zone employers and IT The sophistication of toda Making Storage Simple professionals alike.