The Windows Registry
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Exploring the X64
Exploring the x64 Junichi Murakami Executive Officer, Director of Research Fourteenforty Research Institute, Inc. Who am I? • Junichi Murakami – @Fourteenforty Research Institute, Inc. – Both Windows and Linux kernel development – Reversing malware and P2P software, etc. – Speaker at: • Black Hat 2008 US and Japan, AVAR 2009, RSA Conference(2009-) – Instructor at Security & Programming Camp(2006-) 2 Environment • Windows 7 x64 Edition • Visual Studio 2008 • Windbg • IDA Pro Advanced – STD doesn’t support x64, an offering is needed! 4 Agenda • Windows x64 • ABI(Application Binary Interface) • API Hooking • Code Injection 5 Windows x64 • Native x64 and WoW64 • Virtual Address Space – 2^64 = 16 Exa Byte ( Exa: 10^18) – but, limited to 16TB by Microsoft • File/Registry reflection • New 64-bit APIs – IsWow64Process, GetNativeSystemInfo, etc. 6 ABI • Binary Format • Register • Calling Convention • Exception Handling • Systemcall(x64, WoW64) 11 Binary Format(Cont.) • Some fields were extended to 64-bits – IMAGE_NT_HEADERS.IMAGE_OPTIONAL_HEADER • ImageBase • SizeOfStackReserve • SizeOfStackCommit • SizeOfHeapReserve • SizeOfHeapCommit 13 Calling Convention • first 4 parameters are passed by RCX, RDX, R8, R9 – 5th and later are passed on the stack • caller allocates register home space on the stack • RAX is used for return values • leaf / non-leaf function – leaf function: never use stack – PE32+ contains non-leaf function’s information in its EXCEPTION DIRECTORY • Register’s volatility – volatile: RAX, RCX, RDX, R8-R11 15 Exception Handling • -

Through the Looking Glass: Webcam Interception and Protection in Kernel
VIRUS BULLETIN www.virusbulletin.com Covering the global threat landscape THROUGH THE LOOKING GLASS: and WIA (Windows Image Acquisition), which provides a WEBCAM INTERCEPTION AND still image acquisition API. PROTECTION IN KERNEL MODE ATTACK VECTORS Ronen Slavin & Michael Maltsev Reason Software, USA Let’s pretend for a moment that we’re the bad guys. We have gained control of a victim’s computer and we can run any code on it. We would like to use his camera to get a photo or a video to use for our nefarious purposes. What are our INTRODUCTION options? When we talk about digital privacy, the computer’s webcam The simplest option is just to use one of the user-mode APIs is one of the most relevant components. We all have a tiny mentioned previously. By default, Windows allows every fear that someone might be looking through our computer’s app to access the computer’s camera, with the exception of camera, spying on us and watching our every move [1]. And Store apps on Windows 10. The downside for the attackers is while some of us think this scenario is restricted to the realm that camera access will turn on the indicator LED, giving the of movies, the reality is that malware authors and threat victim an indication that somebody is watching him. actors don’t shy away from incorporating such capabilities A sneakier method is to spy on the victim when he turns on into their malware arsenals [2]. the camera himself. Patrick Wardle described a technique Camera manufacturers protect their customers by incorporating like this for Mac [8], but there’s no reason the principle into their devices an indicator LED that illuminates when can’t be applied to Windows, albeit with a slightly different the camera is in use. -

Minimum Hardware and Operating System
Hardware and OS Specifications File Stream Document Management Software – System Requirements for v4.5 NB: please read through carefully, as it contains 4 separate specifications for a Workstation PC, a Web PC, a Server and a Web Server. Further notes are at the foot of this document. If you are in any doubt as to which specification is applicable, please contact our Document Management Technical Support team – we will be pleased to help. www.filestreamsystems.co.uk T Support +44 (0) 118 989 3771 E Support [email protected] For an in-depth list of all our features and specifications, please visit: http://www.filestreamsystems.co.uk/document-management-specification.htm Workstation PC Processor (CPU) ⁴ Supported AMD/Intel x86 (32bit) or x64 (64bit) Compatible Minimum Intel Pentium IV single core 1.0 GHz Recommended Intel Core 2 Duo E8400 3.0 GHz or better Operating System ⁴ Supported Windows 8, Windows 8 Pro, Windows 8 Enterprise (32bit, 64bit) Windows 10 (32bit, 64bit) Memory (RAM) ⁵ Minimum 2.0 GB Recommended 4.0 GB Storage Space (Disk) Minimum 50 GB Recommended 100 GB Disk Format NTFS Format Recommended Graphics Card Minimum 128 MB DirectX 9 Compatible Recommended 128 MB DirectX 9 Compatible Display Minimum 1024 x 768 16bit colour Recommended 1280 x 1024 32bit colour Widescreen Format Yes (minimum vertical resolution 800) Dual Monitor Yes Font Settings Only 96 DPI font settings are supported Explorer Internet Minimum Microsoft Internet Explorer 11 Network (LAN) Minimum 100 MB Ethernet (not required on standalone PC) Recommended -

Powershell Delete Registry Key Remote Computer
Powershell delete registry key remote computer In Use PowerShell to Edit the Registry on Remote Computers, I talked cmdlet to find and delete the registry key on all remote servers that are. There is a pre powershell registry tool called reg. It will perform registry operations on remote computers. REG DELETE /? REG DELETE. I am trying to create a PowerShell script that deletes two keys on a remote computer. (One key in the code below) I have successfully created a. The Remove-RegistryKey cmdlet is used to delete registry keys and values on the local or a remote computer. I'm working on remotely modifying an autologin key value on batches of {Remove-ItemProperty -Path "HKLM:\Software\Microsoft\Windows Solution: $Computers = Get-Content "C:\"$Path me with a powershell script that can modify registry key on a list of remote computers Basically, I need to modify a product name in add/remove programs list. Then I need to find out whether I got the admin permission on the remote machines. Lastly, remove the specified reg keys. #Read the machine. Deleting Specific Remote Registry Entry - Powershell playing about with trying to write a script to delete a specific software GPO deployed to a remote computer. $Items = $Keys | Foreach-Object {Get-ItemProperty $_. $RegistryKeyValue = $ue($RegistryKeyName) Write-output "Attempting to delete $RegistryKeyName on $Computer `r ". Powershell: Delete Registry Key On Remote Server To run a script on one or many remote computers, use the FilePath parameter of the. I am having trouble changing registry keys. I know the trouble is Set-ItemProperty does not support connections to remote computers. -

Programming Model Intel Itanium 64
11/11/2003 64-bit computing AMD Opteron 64 Application of Win32 Executable File Legacy 64 bit platforms Inbuilt 128-bit bus DDR memory controller with memory bandwidth speed up to 5.3GB/s. Infectors on Intel Itanium and AMD Benefits of 64-bit processors Opteron Based Win64 Systems Use of hyper transport protocol, “glueless” architecture. Oleg Petrovsky and Shali Hsieh Increased integer dynamic range Computer Associates International Inc. Available in up to 8 way configuration with the clock speeds 1 Computer Associates Plaza, Islandia, NY 11749, Much larger addressable memory space of 1.4 GHz, 1.6 GHz and 1.8 GHz . USA Benefits to database, scientific and cryptography Reuses already familiar 32-bit x86 instruction set and applications extends it to support 64-bit operands, registers and memory pointers. AMD64 Programming Model AMD64: Programming model Intel Itanium 64 X86 32-64 64 bit Itanium line of processors is being developed by Intel XMM8 X86 80-Bit Extends general use registers to 64-bit, adds additional eight 64-Bit X87 general purpose 64-bit registers. Itanium - 800 MHz, no on die L3 cache, Itanium 2 - 1GHz, RAX EAX AX 3MB L3 on die, Itanium 2003 (Madison) - 1.5 GHz, 6MB L3 on die cache, 410M transistors, largest integration on a RBX Reuses x86 instruction set. single silicon crystal today. XMM15 RCX Runs 32-bit code without emulation or translation to a native Itanium line of processors utilizes more efficient and robust XMM0 than legacy x86 instruction set architecture F instruction set. R8 L A Itanium has to use x86-to-IA-64 decoder a specifically Minimizes learning curve. -
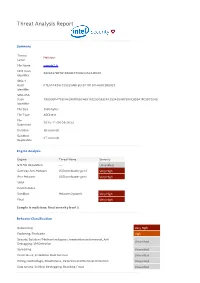
Sample2.Js Malware Summary
Threat Analysis Report Summary Threat Malicious Level File Name sample2.js MD5 Hash 580E637B97B16698CC750B445223D5C0 Identifier SHA-1 Hash 07E507426F72522DABFECF91181D7F64DC3B8D23 Identifier SHA-256 Hash 790999F47B2FA4396FF6B0A6916E295D832A12B3495A87590C859A1FE9D73245 Identifier File Size 3586 bytes File Type ASCII text File 2015-11-06 09:26:23 Submitted Duration 38 seconds Sandbox 27 seconds Replication Engine Analysis Engine Threat Name Severity GTI File Reputation --- Unverified Gateway Anti-Malware JS/Downloader.gen.f Very High Anti-Malware JS/Downloader.gen.f Very High YARA Custom Rules Sandbox Malware.Dynamic Very High Final Very High Sample is malicious: f inal severit y level 5 Behavior Classif icat ion Networking Very High Exploiting, Shellcode High Security Solution / Mechanism bypass, termination and removal, Anti Unverified Debugging, VM Detection Spreading Unverified Persistence, Installation Boot Survival Unverified Hiding, Camouflage, Stealthiness, Detection and Removal Protection Unverified Data spying, Sniffing, Keylogging, Ebanking Fraud Unverified Dynamic Analysis Action Severity Malware behavior: networking activities from non-executable file Very High ATTENTION: connection made to a malicious website (see Web/URL Very High reputation for details) Detected suspicious Java Script content High Downloaded data from a webserver Low Modified INTERNET_OPTION_CONNECT_RETRIES: number of times that Low WinInet attempts to resolve and connect to a host Connected to a specific service provider Low Cracks a URL into its component -

Tracking Computer Use with the Windows® Registry Dataset Doug
Tracking Computer Use with the Windows® Registry Dataset Doug White Disclaimer Trade names and company products are mentioned in the text or identified. In no case does such identification imply recommendation or endorsement by the National Institute of Standards and Technology, nor does it imply that the products are necessarily the best available for the purpose. Statement of Disclosure This research was funded by the National Institute of Standards and Technology Office of Law Enforcement Standards, the Department of Justice National Institute of Justice, the Federal Bureau of Investigation and the National Archives and Records Administration. National Software Reference Library & Reference Data Set The NSRL is conceptually three objects: • A physical collection of software • A database of meta-information • A subset of the database, the Reference Data Set The NSRL is designed to collect software from various sources and incorporate file profiles computed from this software into a Reference Data Set of information. Windows® Registry Data Set It is possible to compile a historical list of applications based on RDS metadata and residue files. Many methods can be used to remove application files, but these may not purge the Registry. Examining the Registry for residue can augment a historical list of applications or provide additional context about system use. Windows® Registry Data Set (WiReD) The WiReD contains changes to the Registry caused by application installation, de-installation, execution or other modifying operations. The applications are chosen from the NSRL collection, to be of interest to computer forensic examiners. WiReD is currently an experimental prototype. NIST is soliciting feedback from the computer forensics community to improve and extend its usefulness. -

Operational and Administrative Guidance
Operational and Administrative Guidance Microsoft Windows Server, Microsoft Windows 10 version 1909 (November 2019 Update), Microsoft Windows Server 2019 version 1809 Hyper-V Common Criteria Evaluation under the Protection Profile for Virtualization, including the Extended Package for Server Virtualization Revision date: January 15, 2021 © 2021 Microsoft. All rights reserved. Microsoft Windows Server and Windows 10 Hyper-V Administrative Guidance Copyright and disclaimer The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial VLicense (which allows redistribution of the work). To view a copy of this license, visithttp://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious. -

Oracle Database Platform Guide for Windows
Oracle® Database Platform Guide 10g Release 1 (10.1) for Windows Part No. B10113-01 December 2003 Oracle Database Platform Guide, 10g Release 1 (10.1) for Windows Part No. B10113-01 Copyright © 1996, 2003 Oracle Corporation. All rights reserved. Primary Author: Craig B. Foch Contributing Author: Mark Kennedy and Helen Slattery Contributor: David Collelo The Programs (which include both the software and documentation) contain proprietary information of Oracle Corporation; they are provided under a license agreement containing restrictions on use and disclosure and are also protected by copyright, patent and other intellectual and industrial property laws. Reverse engineering, disassembly or decompilation of the Programs, except to the extent required to obtain interoperability with other independently created software or as specified by law, is prohibited. The information contained in this document is subject to change without notice. If you find any problems in the documentation, please report them to us in writing. This document is not warranted to be error-free. Except as may be expressly permitted in your license agreement for these Programs, no part of these Programs may be reproduced or transmitted in any form or by any means, electronic or mechanical, for any purpose. If the Programs are delivered to the U.S. Government or anyone licensing or using the programs on behalf of the U.S. Government, the following notice is applicable: Restricted Rights Notice Programs delivered subject to the DOD FAR Supplement are "commercial computer software" and use, duplication, and disclosure of the Programs, including documentation, shall be subject to the licensing restrictions set forth in the applicable Oracle license agreement. -

Compressed Modes User's Guide
Drivers for Windows Compressed Modes User’s Guide Version 2.0 NVIDIA Corporation August 27, 2002 NVIDIA Drivers Compressed Modes User’s Guide Version 2.0 Published by NVIDIA Corporation 2701 San Tomas Expressway Santa Clara, CA 95050 Copyright © 2002 NVIDIA Corporation. All rights reserved. This software may not, in whole or in part, be copied through any means, mechanical, electromechanical, or otherwise, without the express permission of NVIDIA Corporation. Information furnished is believed to be accurate and reliable. However, NVIDIA assumes no responsibility for the consequences of use of such information nor for any infringement of patents or other rights of third parties, which may result from its use. No License is granted by implication or otherwise under any patent or patent rights of NVIDIA Corporation. Specifications mentioned in the software are subject to change without notice. NVIDIA Corporation products are not authorized for use as critical components in life support devices or systems without express written approval of NVIDIA Corporation. NVIDIA, the NVIDIA logo, GeForce, GeForce2 Ultra, GeForce2 MX, GeForce2 GTS, GeForce 256, GeForce3, Quadro2, NVIDIA Quadro2, Quadro2 Pro, Quadro2 MXR, Quadro, NVIDIA Quadro, Vanta, NVIDIA Vanta, TNT2, NVIDIA TNT2, TNT, NVIDIA TNT, RIVA, NVIDIA RIVA, NVIDIA RIVA 128ZX, and NVIDIA RIVA 128 are registered trademarks or trademarks of NVIDIA Corporation in the United States and/or other countries. Intel and Pentium are registered trademarks of Intel. Microsoft, Windows, Windows NT, Direct3D, DirectDraw, and DirectX are registered trademarks of Microsoft Corporation. CDRS is a trademark and Pro/ENGINEER is a registered trademark of Parametric Technology Corporation. OpenGL is a registered trademark of Silicon Graphics Inc. -

Product Name User Guide
Smart-X Software Solutions Core Configurator User guide _______________________________________________________________ SmartX Software Solutions Core Configurator User Guide Table of content: WELCOME 4 FEATURES AND CAPABILITIES 5 MORE SYSTEM MANAGEMENT TOOLS 6 REQUIREMENTS 8 LICENSING AND INSTALLATION 8 EVALUATION VERSION LIMITATION 8 INSTALLATION 8 INSTALLING CORECONFIG ON WINDOWS 7 / 2008 R2 BETA VERSIONS 9 LICENSING 10 WORKING WITH CORE CONFIGURATOR 11 שגיאה! הסימניה אינה מוגדרת. CORE CONFIGURATOR MAIN SCREEN – 32 BIT HOW IT WORKS 11 CORE CONFIGURATOR MAIN SCREEN – 64 BIT 12 ACTIVATION SCREEN 13 HOW IT WORKS: 13 DISPLAY SETTINGS 14 HOW IT WORKS 14 TIME ZONE 15 HOW IT WORKS 15 REMOTE DESKTOP 16 HOW IT WORKS 16 ACCOUNT MANAGEMENT 17 HOW IT WORKS 17 FIREWALL 18 HOW IT WORKS 18 WINRM 19 HOW IT WORKS 19 NETWORKING 20 HOW IT WORKS 21 COMPUTER NAME 22 HOW IT WORKS 22 FEATURES 23 HOW IT WORKS 23 BACKUP PERFORMANCE 24 DCPROMO 25 HOW IT WORKS 26 AUTOMATIC UPDATES 27 HOW IT WORKS 29 REGIONAL LANGUAGES 30 HOW IT WORKS 30 REGISTRY EDITOR 31 2 SmartX Software Solutions Core Configurator User Guide HOW IT WORKS 31 TASK MANAGER 32 HOW IT WORKS 32 SERVICE 33 HOW IT WORKS 33 SYSTEM INFO 34 SHOW COMMANDS 35 3 SmartX Software Solutions Core Configurator User Guide Chapter 1 Welcome Welcome to Smart-X. Thank you for choosing Core Configurator™, one of the top tools developed by Smart-X Software Solutions expert team in an effort to optimize your everyday work. Core Configurator helps you manage your system efficiently, effortlessly and productively. This chapter describes the features and capabilities of Core Configurator, and lists additional tools in the same field that can help optimize your work environment. -

The Evolution of TDL: Conquering X64
The Evolution of TDL: Conquering x64 Revision 1.1 Eugene Rodionov, Malware Researcher Aleksandr Matrosov, Senior Malware Researcher 2 2 CONTENTS 3 INTRODUCTION ..................................................................................................................................................... 4 1 INVESTIGATION ............................................................................................................................................. 5 1.1 GANGSTABUCKS ............................................................................................................................................... 6 2 INSTALLATION ............................................................................................................................................. 11 2.1 INFECTING X86 SYSTEMS .................................................................................................................................. 11 2.2 INFECTING X64 SYSTEMS .................................................................................................................................. 13 2.3 THE DROPPER’S PAYLOAD ................................................................................................................................ 14 2.4 COMPARISON WITH TDL3/TDL3+..................................................................................................................... 15 3 THE BOT .....................................................................................................................................................