Proceedings of Bsdcon ’03
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ebook - Informations About Operating Systems Version: August 15, 2006 | Download
eBook - Informations about Operating Systems Version: August 15, 2006 | Download: www.operating-system.org AIX Internet: AIX AmigaOS Internet: AmigaOS AtheOS Internet: AtheOS BeIA Internet: BeIA BeOS Internet: BeOS BSDi Internet: BSDi CP/M Internet: CP/M Darwin Internet: Darwin EPOC Internet: EPOC FreeBSD Internet: FreeBSD HP-UX Internet: HP-UX Hurd Internet: Hurd Inferno Internet: Inferno IRIX Internet: IRIX JavaOS Internet: JavaOS LFS Internet: LFS Linspire Internet: Linspire Linux Internet: Linux MacOS Internet: MacOS Minix Internet: Minix MorphOS Internet: MorphOS MS-DOS Internet: MS-DOS MVS Internet: MVS NetBSD Internet: NetBSD NetWare Internet: NetWare Newdeal Internet: Newdeal NEXTSTEP Internet: NEXTSTEP OpenBSD Internet: OpenBSD OS/2 Internet: OS/2 Further operating systems Internet: Further operating systems PalmOS Internet: PalmOS Plan9 Internet: Plan9 QNX Internet: QNX RiscOS Internet: RiscOS Solaris Internet: Solaris SuSE Linux Internet: SuSE Linux Unicos Internet: Unicos Unix Internet: Unix Unixware Internet: Unixware Windows 2000 Internet: Windows 2000 Windows 3.11 Internet: Windows 3.11 Windows 95 Internet: Windows 95 Windows 98 Internet: Windows 98 Windows CE Internet: Windows CE Windows Family Internet: Windows Family Windows ME Internet: Windows ME Seite 1 von 138 eBook - Informations about Operating Systems Version: August 15, 2006 | Download: www.operating-system.org Windows NT 3.1 Internet: Windows NT 3.1 Windows NT 4.0 Internet: Windows NT 4.0 Windows Server 2003 Internet: Windows Server 2003 Windows Vista Internet: Windows Vista Windows XP Internet: Windows XP Apple - Company Internet: Apple - Company AT&T - Company Internet: AT&T - Company Be Inc. - Company Internet: Be Inc. - Company BSD Family Internet: BSD Family Cray Inc. -

OM-Cube Project
OM-Cube project V. Hiribarren, N. Marchand, N. Talfer [email protected] - [email protected] - [email protected] Abstract. The OM-Cube project is composed of several components like a minimal operating system, a multi- media player, a LCD display and an infra-red controller. They should be chosen to fit the hardware of an em- bedded system. Several other similar projects can provide information on the software that can be chosen. This paper aims to examine the different available tools to build the OM-Multimedia machine. The main purpose is to explore different ways to build an embedded system that fits the hardware and fulfills the project. 1 A Minimal Operating System The operating system is the core of the embedded system, and therefore should be chosen with care. Because of its popu- larity, a Linux based system seems the best choice, but other open systems exist and should be considered. After having elected a system, all unnecessary components may be removed to get a minimal operating system. 1.1 A Linux Operating System Using a Linux kernel has several advantages. As it’s a popular kernel, many drivers and documentation are available. Linux is an open source kernel; therefore it enables anyone to modify its sources and to recompile it. Using Linux in an embedded system requires adapting the kernel to the hardware and to the system needs. A simple method for building a Linux embed- ded system is to create a partition on a development host and to mount it on a temporary mount point. This partition is filled as one goes along and then, the final distribution is put on the target host [Fich02] [LFS]. -

Freebsd and Netbsd on Small X86 Based Systems
FreeBSD and NetBSD on Small x86 Based Systems Dr. Adrian Steinmann <[email protected]> Asia BSD Conference in Tokyo, Japan March 17th, 2011 1 Introduction Who am I? • Ph.D. in Mathematical Physics (long time ago) • Webgroup Consulting AG (now) • IT Consulting Open Source, Security, Perl • FreeBSD since version 1.0 (1993) • NetBSD since version 3.0 (2005) • Traveling, Sculpting, Go AsiaBSDCon Tutorial March 17, 2011 in Tokyo, Japan “Installing and Running FreeBSD and NetBSD on Small x86 Based Systems” Dr. Adrian Steinmann <[email protected]> 2 Focus on Installing and Running FreeBSD and NetBSD on Compact Flash Systems (1) Overview of suitable SW for small x86 based systems with compact flash (CF) (2) Live CD / USB dists to try out and bootstrap onto a CF (3) Overview of HW for small x86 systems (4) Installation strategies: what needs special attention when doing installations to CF (5) Building your own custom Install/Maintenance RAMdisk AsiaBSDCon Tutorial March 17, 2011 in Tokyo, Japan “Installing and Running FreeBSD and NetBSD on Small x86 Based Systems” Dr. Adrian Steinmann <[email protected]> 3 FreeBSD for Small HW Many choices! – Too many? • PicoBSD / TinyBSD • miniBSD & m0n0wall • pfSense • FreeBSD livefs, memstick • NanoBSD • STYX. Others: druidbsd, Beastiebox, Cauldron Project, ... AsiaBSDCon Tutorial March 17, 2011 in Tokyo, Japan “Installing and Running FreeBSD and NetBSD on Small x86 Based Systems” Dr. Adrian Steinmann <[email protected]> 4 PicoBSD & miniBSD • PicoBSD (1998): Initial import into src/release/picobsd/ by Andrzej Bialecki <[email protected] -

The Complete Freebsd
The Complete FreeBSD® If you find errors in this book, please report them to Greg Lehey <grog@Free- BSD.org> for inclusion in the errata list. The Complete FreeBSD® Fourth Edition Tenth anniversary version, 24 February 2006 Greg Lehey The Complete FreeBSD® by Greg Lehey <[email protected]> Copyright © 1996, 1997, 1999, 2002, 2003, 2006 by Greg Lehey. This book is licensed under the Creative Commons “Attribution-NonCommercial-ShareAlike 2.5” license. The full text is located at http://creativecommons.org/licenses/by-nc-sa/2.5/legalcode. You are free: • to copy, distribute, display, and perform the work • to make derivative works under the following conditions: • Attribution. You must attribute the work in the manner specified by the author or licensor. • Noncommercial. You may not use this work for commercial purposes. This clause is modified from the original by the provision: You may use this book for commercial purposes if you pay me the sum of USD 20 per copy printed (whether sold or not). You must also agree to allow inspection of printing records and other material necessary to confirm the royalty sums. The purpose of this clause is to make it attractive to negotiate sensible royalties before printing. • Share Alike. If you alter, transform, or build upon this work, you may distribute the resulting work only under a license identical to this one. • For any reuse or distribution, you must make clear to others the license terms of this work. • Any of these conditions can be waived if you get permission from the copyright holder. Your fair use and other rights are in no way affected by the above. -
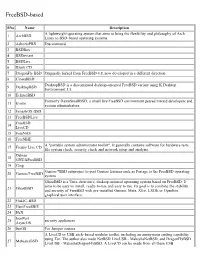
List of BSD Operating Systems
FreeBSD-based SNo Name Description A lightweight operating system that aims to bring the flexibility and philosophy of Arch 1 ArchBSD Linux to BSD-based operating systems. 2 AskoziaPBX Discontinued 3 BSDBox 4 BSDeviant 5 BSDLive 6 Bzerk CD 7 DragonFly BSD Originally forked from FreeBSD 4.8, now developed in a different direction 8 ClosedBSD DesktopBSD is a discontinued desktop-oriented FreeBSD variant using K Desktop 9 DesktopBSD Environment 3.5. 10 EclipseBSD Formerly DamnSmallBSD; a small live FreeBSD environment geared toward developers and 11 Evoke system administrators. 12 FenestrOS BSD 13 FreeBSDLive FreeBSD 14 LiveCD 15 FreeNAS 16 FreeSBIE A "portable system administrator toolkit". It generally contains software for hardware tests, 17 Frenzy Live CD file system check, security check and network setup and analysis. Debian 18 GNU/kFreeBSD 19 Ging Gentoo/*BSD subproject to port Gentoo features such as Portage to the FreeBSD operating 20 Gentoo/FreeBSD system GhostBSD is a Unix-derivative, desktop-oriented operating system based on FreeBSD. It aims to be easy to install, ready-to-use and easy to use. Its goal is to combine the stability 21 GhostBSD and security of FreeBSD with pre-installed Gnome, Mate, Xfce, LXDE or Openbox graphical user interface. 22 GuLIC-BSD 23 HamFreeSBIE 24 HeX IronPort 25 security appliances AsyncOS 26 JunOS For Juniper routers A LiveCD or USB stick-based modular toolkit, including an anonymous surfing capability using Tor. The author also made NetBSD LiveUSB - MaheshaNetBSD, and DragonFlyBSD 27 MaheshaBSD LiveUSB - MaheshaDragonFlyBSD. A LiveCD can be made from all these USB distributions by running the /makeiso script in the root directory. -

BSD Based Systems
Pregled BSD sistema I projekata Glavne BSD grane FreeBSD Homepage: http://www.freebsd.org/ FreeBSD je Unix-like slobodni operativni sistem koji vodi poreklo iz AT&T UNIX-a preko Berkeley Software Distribution (BSD) grane kroz 386BSD i 4.4BSD. Radi na procesorima kompatibilnim sa Intel x86 familijom procesora, kao I na DEC Alpha, UltraSPARC procesorima od Sun Microsystems, Itanium (IA-64), AMD64 i PowerPC procesorima. Radi I na PC-98 arhitekturi. Podrska za ARM i MIPS arhitekture je trenutno u razvoju. Početkom 1993. godine Jordan K. Hubbard, Rod Grimes i Nate Williams su pokrenuli projekat čiji je cilj bio rešavanje problema koji su postojali u principima razvoja Jolitzovog 386BSD-a. Posle konsultovanja sa tadašnjim korisnicima sistema, uspostavljeni su principi i smišljeno je ime - FreeBSD. Pre nego što je konkretan razvoj i počeo, Jordan Hubbard je predložio je firmi Walnut Creek CDROM (danas BSDi) da pripreme distribuiranje FreeBSD-a na CD-ROM-ovima. Walnut Creek CDROM su prihvatili ideju, ali i obezbedili (tada potpuno nepoznatom) projektu mašinu na kojoj će biti razvijan i brzu Internet konekciju. Bez ove pomoći teško da bi FreeBSD bio razvijen u ovolikoj meri i ovolikom brzinom kao što jeste. Prva distribucija FreeBSD-a na CD-ROM-ovima (i naravno na netu) bila je FreeBSD 1.0, objavljena u decembru 1993. godine. Bila je zasnovana na Berkeley-evoj 4.3BSD-Lite ("Net/2") traci, a naravno sadržala je i komponente 386BSD-a i mnoge programe Free Software Foundation (fondacija besplatnog- slobodnog softvera). Nakon što je Novell otkupio UNIX od AT&T-a, Berkeley je morao da prizna da Net/2 traka sadrži velike delove UNIX koda. -

Freebsd System Programming Freebsd System Programming
FreeBSD system programming FreeBSD system programming Authors: Nathan Boeger (nboeger at khmere.com) Mana Tominaga (manna at dumaexplorer.com ) Copyright (C) 2001,2002,2003,2004 Nathan Boeger and Mana Tominaga Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.1 or any later version published by the Free Software Foundation; with no Invariant Sections, one Front-Cover Texts, and one Back-Cover Text: "Nathan Boeger and Mana Tominaga wrote this book and asks for your support through donation. Contact the authors for more information" A copy of the license is included in the section entitled GNU Free Documentation License" Welcome to the FreeBSD System Programming book. Please note that this is a work in progress and feedback is appreciated! please note a few things first: • We have written the book in a new format. I have read many programming books that have covered many different areas. Personally, I found it hard to follow code with no comments or switching back and forth between text explaining code and the code. So in this book, after chapter 1, I have split the code and text into separate pieces. The source code for each chapter is online and fully downloaded able. That way if you only want to check out the source code examples you can view them only. And if you want to understand the concepts you can read the text or even have them side by side. Please let us know your thoughts on this • The book was ordinally intended to be published in hard copy form. -

Installing Openbsd: a Beginner's Guide (Mac PPC) Freebsd 5.X And
Daemon News: December 2004 http://ezine.daemonnews.org/200412/ Mirrors Primary (US) Issues December 2004 December 2004 Get BSD Contact Us Search BSD FAQ New to BSD? DN Print Magazine BSD News BSD Mall BSD Support Join Us T H I S M O N T H ' S F E A T U R E S From the Editor Installing OpenBSD: A Beginner's Guide (Mac PPC) by Brian Schonhorst Digium releases g.729 codec for FreeBSD The OpenBSD website is contains an extermely thorough FAQ and by Chris Coleman manual that should be any OpenBSD user's primary resource. Below Digium makes the g.729 speech I will go through a basic installation of OpenBSD 3.5 to clarify some vocoder codec available for points that might be confusing to a new OpenBSD user. FreeBSD after bsdnews.com readers lobby for a FreeBSD There are many ways you can get OpenBSD up and running on your port machine. I will assume you are using the official OpenBSD CD set because if you aren't, you should be. The official CD's are one of the few ways to support the OpenBSD community financially. Get BSD Stuff A few things you should consider before beginning: Read More FreeBSD 5.x and the Future by Scott Long The release of FreeBSD 5.3 signals the true kick-off of the 5-STABLE and 6-CURRENT series. We are very excited about this, both because 5.3 is a good release, and because 6.0 will give us a chance to, erm, redeem ourselves and our development process. -

Cours D.Introduction Tcp-Ip.Pdf
Cours d’introduction `aTCP/IP Fran¸coisLaissus Version du 25 f´evrier2009 ii Copyright°c 1999 - 2009 — $Rev: 131 $ — Fran¸coisLaissus Avant propos Les sources de ce document sont d´evelopp´ees,g´er´eeset conserv´eesgrˆace aux services de FreeBSD1, remarquable syst`emed’exploitation OpenSource ! Les divers fichiers qui composent le source sont ´edit´es`al’aide de l’´editeur de texte vi ; l’historique des modifications est confi´eaux bons soins de l’outil subversion (gestionnaire de versions). L’ensemble du processus de fabrica- tion est pilot´epar une poign´eede fichiers Makefile (commande make). La mise en forme s’effectue grˆaceau logiciel LATEX. Les figures sont des- sin´eessous “ X Window Systems ”(X11) `al’aide du logiciel xfig et int´egr´ees directement dans le document final sous forme de PostScript encapsul´e.Les listings des exemples de code C ont ´et´efabriqu´es`al’aide du logiciel a2ps et inclus dans le document final ´egalement en PostScript encapsul´e. La sortie papier a ´et´eimprim´eeen PostScript sur une imprimante de type laser, avec dvips. La version pdf est une transformation du format PostScript `al’aide du logiciel dvipdfm, enfin la version HTML est traduite directement en HTML `apartir du format LATEX `al’aide du logiciel latex2html. Tous les outils ou formats utilis´essont en acc`esou usage libre, c’est `adire sans versement de droit `aleurs auteurs respectifs. Qu’ils en soient remerci´es pour leurs contributions inestimables au monde informatique libre et ouvert ! Je remercie ´egalement Jean-Jacques Dh´enin et les nombreux lecteurs que je ne connais qu’au travers de leur e-mails, d’avoir bien voulu prendre le temps de relire l’int´egralit´ede ce cours et de me faire part des innombrables erreurs et coquilles typographiques qu’il comporte, merci encore ! Ce support de cours est en consultation libre `acette url : HTML http://www.laissus.fr/cours/cours.html Ou `at´el´echarger au format PDF : HTTP http://www.laissus.fr/cours/cours.pdf FTP ftp://ftp.laissus.fr/pub/cours/cours.pdf D’autres formats (.ps,.dvi,. -

Inne Systemy Operacyjne Olsztyn 2008-2010
Wojciech Sobieski Oprogramowanie Alternatywne Inne Systemy Operacyjne Olsztyn 2008-2010 Systemy Operacyjne Firmy komercyjne: Społeczność RWO: ● tworzenie „zamkniętych” ● tworzenie „wolnych” systemów komercyjnych zamienników systemów komercyjnych ● realizacja własnych idei ● realizacja własnych idei Rodzaje systemów operacyjnych Amiga: ● AmigaOS ● Amiga Research Operating System (AROS) ● MorphOS Apple: ● Apple DOS, ProDOS ● Darwin ● GS/OS ● iPhoneOS ● Mac OS ● Mac OS X, Mac OS X Server ● A/UX ● Lisa OS wg: http://pl.wikipedia.org/wiki/System_operacyjny Rodzaje systemów operacyjnych Systemy firmy Be i pochodne: ● BeOS ● BeIA ● NewOS/Haiku ● yellowTAB Zeta Systemy firmy Digital (DEC)/Compaq: ● AIS ● OS-8 ● RSTS/E ● RSX ● RT-11 ● TOPS: TOPS-10, TOPS-20 ● VMS (później przemianowany na OpenVMS) Rodzaje systemów operacyjnych Systemy firmy IBM: ● OS/2 ● MFT ● AIX ● MVT ● OS/400 ● PC-DOS ● OS/390 ● SVS ● VM/CMS ● MVS ● DOS/VSE ● TPF ● DOS/360 ● ALCS ● OS/360 ● z/OS Rodzaje systemów operacyjnych Systemy firmy Microsoft i pochodne: ● MS-DOS ̶ PC-DOS, DR-DOS, FreeDOS, NDOS (DOS), QDOS ● Microsoft Windows 1.0, 2.0, 3.x, ● Microsoft Windows 95/98/98 SE/Me, ● Microsoft Windows CE, NT/2000/XP/2003/Vista ̶ PetrOS, ReactOS Rodzaje systemów operacyjnych Systemy firmy Novell: ● NetWare ● SuSE Linux Systemy NeXT: ● NeXTStep Rodzaje systemów operacyjnych Systemy UNIX i jego pochodne: ● AIX ● BSD, FreeBSD, NetBSD, OpenBSD, DragonFly, DesktopBSD, PC-BSD ● Darwin ● Digital UNIX ● Ultrix ● HP-UX ● Xenix ● IRIX ● GNU/Linux (z jądrem Linux) ● Mac OS X ● GNU/Hurd -

Installing and Running Freebsd and Netbsd on Small X86-Based Systems
Installing and Running FreeBSD and NetBSD on Small x86-based Systems Dr. Adrian Steinmann <[email protected]> Asia BSD Conference in Tokyo, Japan Thursday, March 12th, 2009 10:00-12:30, 14:00-16:30 1 Installing and Running FreeBSD and NetBSD on Small x86-based Systems Dr. Adrian Steinmann <[email protected]> Asia BSD Conference in Tokyo, Japan Thursday, March 12th, 2009 10:00-12:30, 14:00-16:30 2 Introduction Who am I? • Ph.D. in Mathematical Physics (long time ago) • Webgroup Consulting AG (now) • IT Consulting Open Source, Security, Perl • FreeBSD since version 1.0 (1993) • NetBSD since version 3.0 (2005) • Traveling, Sculpting, Go AsiaBSDCon Tutorial March 12, 2009, Tokyo, Japan “Installing and Running FreeBSD and NetBSD on Small x86-based Systems” Dr. Adrian Steinmann <[email protected]> 3 Introductions Who are you? • Name and where you come from • Your (favorite) work and play • Why you’re here today • Do you have small x86 system experience? • If so, which one and what OS did you use? AsiaBSDCon Tutorial March 12, 2009, Tokyo, Japan “Installing and Running FreeBSD and NetBSD on Small x86-based Systems” Dr. Adrian Steinmann <[email protected]> 4 Schedule for the day 1. Overview SW and HW for small systems 2. Secrets about Compact Flash (CF) Installations 3. The Maintenance RAMdisk in Action (Demos) 4. You install and use a Maintenance RAMdisk on your own systems AsiaBSDCon Tutorial March 12, 2009, Tokyo, Japan “Installing and Running FreeBSD and NetBSD on Small x86-based Systems” Dr. Adrian Steinmann <[email protected]> 5 FreeBSD for Small HW Many choices! – Too many? • PicoBSD • miniBSD • m0n0wall • pfSense • Freesbie Live CD • NanoBSD • STYX. -

Embedded Freebsd Cookbook.Pdf
Embedded FreeBSD Cookbook A Volume in the Embedded Technology™ Series Embedded FreeBSD Cookbook by Paul Cevoli An imprint of Elsevier Science Amsterdam Boston London New York Oxford Paris San Diego San Francisco Singapore Sydney Tokyo iv Newnes is an imprint of Elsevier Science. Copyright © 2002, Elsevier Science (USA). All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior written permission of the publisher. Recognizing the importance of preserving what has been written, Elsevier Science prints its books on acid-free paper whenever possible. Library of Congress Cataloging-in-Publication Data ISBN: 1-5899-5004-6 British Library Cataloguing-in-Publication Data A catalogue record for this book is available from the British Library. The publisher offers special discounts on bulk orders for this book. For information, please contact: Manager of Special Sales Elsevier Science 200 Wheeler Road Burlington, MA 01803 For information on all Newnes publications available, contact our World Wide Web home page at http://www.newnespress.com 10 9 8 7 6 5 4 3 2 1 Printed in the United States of America Preface .................................................................................. vii Prerequisites and Other Resources .................................................... vii 1 Getting Started .................................................................. 1 Overview ............................................................................................