Customer Security Promises
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

MASTERCLASS GNUPG MASTERCLASS You Wouldn’T Want Other People Opening Your Letters and BEN EVERARD Your Data Is No Different
MASTERCLASS GNUPG MASTERCLASS You wouldn’t want other people opening your letters and BEN EVERARD your data is no different. Encrypt it today! SECURE EMAIL WITH GNUPG AND ENIGMAIL Send encrypted emails from your favourite email client. our typical email is about as secure as a The first thing that you need to do is create a key to JOHN LANE postcard, which is good news if you’re a represent your identity in the OpenPGP world. You’d Ygovernment agency. But you wouldn’t use a typically create one key per identity that you have. postcard for most things sent in the post; you’d use a Most people would have one identity, being sealed envelope. Email is no different; you just need themselves as a person. However, some may find an envelope – and it’s called “Encryption”. having separate personal and professional identities Since the early 1990s, the main way to encrypt useful. It’s a personal choice, but starting with a single email has been PGP, which stands for “Pretty Good key will help while you’re learning. Privacy”. It’s a protocol for the secure encryption of Launch Seahorse and click on the large plus-sign email that has since evolved into an open standard icon that’s just below the menu. Select ‘PGP Key’ and called OpenPGP. work your way through the screens that follow to supply your name and email address and then My lovely horse generate the key. The GNU Privacy Guard (GnuPG), is a free, GPL-licensed You can, optionally, use the Advanced Key Options implementation of the OpenPGP standard (there are to add a comment that can help others identify your other implementations, both free and commercial – key and to select the cipher, its strength and set when the PGP name now refers to a commercial product the key should expire. -

Cisco SCA BB Protocol Reference Guide
Cisco Service Control Application for Broadband Protocol Reference Guide Protocol Pack #60 August 02, 2018 Cisco Systems, Inc. www.cisco.com Cisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco website at www.cisco.com/go/offices. THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS. THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY. The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California. NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS” WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. -

Wiretapping End-To-End Encrypted Voip Calls Real-World Attacks on ZRTP
Institute of Operating Systems and Computer Networks Wiretapping End-to-End Encrypted VoIP Calls Real-World Attacks on ZRTP Dominik Schürmann, Fabian Kabus, Gregor Hildermeier, Lars Wolf, 2017-07-18 wiretapping difficulty End-to-End Encryption SIP + DTLS-SRTP (SIP + Datagram Transport Layer Security-SRTP) End-to-End Encryption & Authentication SIP + SRTP + ZRTP Introduction Man-in-the-Middle ZRTP Attacks Conclusion End-to-End Security for Voice Calls Institute of Operating Systems and Computer Networks No End-to-End Security PSTN (Public Switched Telephone Network) SIP + (S)RTP (Session Initiation Protocol + Secure Real-Time Transport Protocol) 2017-07-18 Dominik Schürmann Wiretapping End-to-End Encrypted VoIP Calls Page 2 of 13 wiretapping difficulty End-to-End Encryption & Authentication SIP + SRTP + ZRTP Introduction Man-in-the-Middle ZRTP Attacks Conclusion End-to-End Security for Voice Calls Institute of Operating Systems and Computer Networks No End-to-End Security PSTN (Public Switched Telephone Network) SIP + (S)RTP (Session Initiation Protocol + Secure Real-Time Transport Protocol) End-to-End Encryption SIP + DTLS-SRTP (SIP + Datagram Transport Layer Security-SRTP) 2017-07-18 Dominik Schürmann Wiretapping End-to-End Encrypted VoIP Calls Page 2 of 13 wiretapping difficulty Introduction Man-in-the-Middle ZRTP Attacks Conclusion End-to-End Security for Voice Calls Institute of Operating Systems and Computer Networks No End-to-End Security PSTN (Public Switched Telephone Network) SIP + (S)RTP (Session Initiation Protocol + Secure Real-Time -

CS 255: Intro to Cryptography 1 Introduction 2 End-To-End
Programming Assignment 2 Winter 2021 CS 255: Intro to Cryptography Prof. Dan Boneh Due Monday, March 1st, 11:59pm 1 Introduction In this assignment, you are tasked with implementing a secure and efficient end-to-end encrypted chat client using the Double Ratchet Algorithm, a popular session setup protocol that powers real- world chat systems such as Signal and WhatsApp. As an additional challenge, assume you live in a country with government surveillance. Thereby, all messages sent are required to include the session key encrypted with a fixed public key issued by the government. In your implementation, you will make use of various cryptographic primitives we have discussed in class—notably, key exchange, public key encryption, digital signatures, and authenticated encryption. Because it is ill-advised to implement your own primitives in cryptography, you should use an established library: in this case, the Stanford Javascript Crypto Library (SJCL). We will provide starter code that contains a basic template, which you will be able to fill in to satisfy the functionality and security properties described below. 2 End-to-end Encrypted Chat Client 2.1 Implementation Details Your chat client will use the Double Ratchet Algorithm to provide end-to-end encrypted commu- nications with other clients. To evaluate your messaging client, we will check that two or more instances of your implementation it can communicate with each other properly. We feel that it is best to understand the Double Ratchet Algorithm straight from the source, so we ask that you read Sections 1, 2, and 3 of Signal’s published specification here: https://signal. -

Security System for Mobile Messaging Applications Pejman Dashtinejad
Security System for Mobile Messaging Applications Pejman Dashtinejad Master of Science Thesis Stockholm, Sweden TRITA–ICT–EX-2015:2 Introduction | 1 Security System for Mobile Messaging Applications Pejman Dashtinejad 8 January 2015 Master of Science Thesis Examiner Professor Sead Muftic Department of ICT KTH University SE-100 44 Stockholm, Sweden TRITA–ICT–EX-2015:2 Abstract | iii Abstract Instant messaging (IM) applications are one of the most popular applications for smartphones. The IMs have the capability of sending messages or initiating voice calls via Internet which makes it almost cost free for the users to communicate with each other. Unfortunately, like any other type of applications, majority of these applications are vulnerable to malicious attacks and have privacy issues. The motivation for this thesis is the need to identifying security services of an IM application and to design a secure system for any mobile messaging application. This research proposes an E2EE (End-to-End Encryption) approach which provides a secure IM application design which protects its users with better integrity, confidentiality and privacy. To achieve this goal a research is conducted to investigate current security features of popular messaging applications in the mobile market. A list of requirements for good security is generated and based on those requirements an architecture is designed. A demo is also implemented and evaluated. Keywords: Mobile, Application, messaging, Chat, Encryption, Security Acknowledgments | v Acknowledgments First and foremost, thank you God to give me another chance to complete my higher education and to learn enormous skills and knowledge through all these years of study at the university. -

Parental Control – Whatsapp
Parental controls guide WhatsApp privacy guide Parental Controls information Type of guide Social media privacy guides Features and Benefits WhatsApp privacy settings allow you to restrict who can see your child’s messages and location. There are also ways to block delete or report users on the platform. Please note, WhatsApp new privacy policy has come into effect starting May 15. What specific content can I restrict? Chatting Downloading file sharing Location sharing Privacy Privacy and identity theft What do I need? A WhatsApp account WhatsApp privacy guide Step by step guide 1 Control who sees your information You can set your last seen, profile photo and/or status to the following options: Everyone, My Contacts and Nobody: 1. Open WhatsApp and go to your Settings, tap Account, then tap Privacy. 2. Next, tap your selected option, then choose from either option: ‘Everyone’, ‘My Contacts’ or ‘Nobody’. 3. The changes will be applied automatically. 1 WhatsApp privacy guide 2 3 WhatsApp privacy guide Step by step guide 2 How to block contacts You can stop receiving messages, calls and status updates from certain contacts by blocking them. Open WhatsApp, choose the person you want to block either by searching or scrolling through your chat list. 2. Tap on their name, then scroll down and tap Block Contact. 1 2 WhatsApp privacy guide WhatsApp privacy guide Step by step guide 3 How to report contacts 1. Open WhatsApp, choose the person you want to report either by searching or scrolling through your chat list. 2. Tap on their name, then scroll down and tap Report or Report and Block Contact. -

Enterprise Edition
Secure Communication. Simplified. SAFECHATS Problem Most companies use popular insecure email and ⛔ messaging services to communicate confidential information P The information flow within the Company is ⛔ disorganized Metadata is exposed and available to third-party ⛔ services SAFECHATS Introducing SAFECHATS Ultra-secure communication solution P Designed with security in mind SAFECHATS Why SAFECHATS? ✔ Information is always end-to-end encrypted by default P ✔ All-in-one communication suite: • Text messaging (one-on-one and group chats) • Voice calls • File transfers (no size and file type limits) SAFECHATS How does SAFECHATS solve the problem? ✔ Customizable white label solution ✔ Integrates with existing softwareP infrastructure ✔ Enterprise-wide account and contact list management, supervised audited chats for compliance SAFECHATS What makes SAFECHATS different? ✔ Your own isolated cloud environment or on-premise deployment P ✔ Customizable solution allows to be compliant with internal corporate security policies ✔ No access to your phone number and contact list SAFECHATS Screenshot Protection ✔ Notifications on iOS P ✔ DRM protection on Android SAFECHATS Identity Verification ✔ Protection from man-in-the-middle attacksP ✔ SMP Protocol SAFECHATS Privacy Features ✔ Show / hide messages and files P ✔ Recall messages and files ✔ Self-destructing messages and files SAFECHATS Additional Protection ✔ History retention control P ✔ Application lock: • PIN-code • Pattern-lock on Android devices • Touch ID on iOS devices SAFECHATS How does SAFECHATS -

FALL 2020 E-NEWSLETTER at Digital Mountain We Assist Our Clients with Their Computer Forensics, E-Discovery, Cybersecurity and Data Analytics Needs
FALL 2020 E-NEWSLETTER At Digital Mountain we assist our clients with their computer forensics, e-discovery, cybersecurity and data analytics needs. For this E-Newsletter, we focus on ephemeral communications and the affect of disappearing messages on discovery cases. Ephemeral Applications: Digital Trick or Treat The trick in trick or treating is one that has evolved from the neighbor who dons a monster mask when opening the door to the disappearance of peanut butter cups when Dad does the safety check of the night’s candy haul. Our digital communications have gone through an analogous transformation as we first marveled at how much data our devices could hold. Just as we upgraded from a small plastic pumpkin to a pillowcase for larger candy collections - we saved a growing plethora of emails, text messages, digital images, voice messages, and all manner of documents on mobile devices. Now, with the rise of discovery, we want our vulnerable data to disappear as if it were our least favorite candy. Ephemeral applications may be just the trick for that unwanted data. Call It What You Will There is no consensus about what constitutes an ephemeral application beyond the understanding that there is an element of impermanence. In 2016, three Georgia Tech College of Computing researchers proposed the creation of “ephemeral apps” that would allow users to engage with apps on a trial basis that would “pop-up instantaneously” on devices and then disappear after a certain period (https://www.cc.gatech.edu/~kbhardwa/papers/eapps.pdf). At the opposite end of the spectrum, in 2017 fan favorite Snapchat modified its app to allow recipients to determine when photographs and video would disappear rather than the burn after reading settings that propelled Snapchat’s rapid rise (https://www.vox.com/2017/5/9/15595040/snapchat-product-update-limitless-q1-earnings). -

Pgpfone Pretty Good Privacy Phone Owner’S Manual Version 1.0 Beta 7 -- 8 July 1996
Phil’s Pretty Good Software Presents... PGPfone Pretty Good Privacy Phone Owner’s Manual Version 1.0 beta 7 -- 8 July 1996 Philip R. Zimmermann PGPfone Owner’s Manual PGPfone Owner’s Manual is written by Philip R. Zimmermann, and is (c) Copyright 1995-1996 Pretty Good Privacy Inc. All rights reserved. Pretty Good Privacy™, PGP®, Pretty Good Privacy Phone™, and PGPfone™ are all trademarks of Pretty Good Privacy Inc. Export of this software may be restricted by the U.S. government. PGPfone software is (c) Copyright 1995-1996 Pretty Good Privacy Inc. All rights reserved. Phil’s Pretty Good engineering team: PGPfone for the Apple Macintosh and Windows written mainly by Will Price. Phil Zimmermann: Overall application design, cryptographic and key management protocols, call setup negotiation, and, of course, the manual. Will Price: Overall application design. He persuaded the rest of the team to abandon the original DOS command-line approach and designed a multithreaded event-driven GUI architecture. Also greatly improved call setup protocols. Chris Hall: Did early work on call setup protocols and cryptographic and key management protocols, and did the first port to Windows. Colin Plumb: Cryptographic and key management protocols, call setup negotiation, and the fast multiprecision integer math package. Jeff Sorensen: Speech compression. Will Kinney: Optimization of GSM speech compression code. Kelly MacInnis: Early debugging of the Win95 version. Patrick Juola: Computational linguistic research for biometric word list. -2- PGPfone Owner’s -

Internet Telephony with Linphone WELLWELL CONNECTEDCONNECTED
Linphone COVER STORY Internet telephony with Linphone WELLWELL CONNECTEDCONNECTED When you want to call your friends in distant countries, don’t pick up municate with the VoIP provider, so you will need to install the library first. To do the phone; just put on your headset and fire up Linphone. so, open a terminal window, then be- come root by typing su and supplying BY SIMONE SCHÄFER the root password. Unpack the archive by typing tar xzf libosip2-2.2.0.tar.gz, ne of the most popular methods wants to take incoming calls via Purtel. and then change to the new directory (cd for accessing Voice over IP tech- The procedures are similar for other pro- libosip2-2.2.0). The following commands Onology is through a so-called viders. will build and install the library: softphone. A softphone is simply a com- puter program running on your desktop Installation ./configure --prefix=/usr that handles call establishment and com- The source code for the 1.1.0 release, make munication. Linphone [1] is one of the and the libraries, are available on the most popular softphone applications for DVD with this issue below LinuxUser/ Phone Numbers and SIP Ids Linux. Linphone is optimized for the linphone/. In the simplest of all cases, the phone Gnome desktop, although that doesn’t Mandriva Linux 2006 has the current number will be a simple telephone num- mean you can’t run it on KDE. This arti- 1.1.0 version. Gentoo Linux users can ber followed by the SIP domain, such as cles describes how to install, configure, install Linphone 1.1.0 simply by running [email protected]. -

PGP Command Line User Guide
PGP Command Line User Guide Last updated: July 2020 Copyright statement Broadcom, the pulse logo, Connecting everything, and Symantec are among the trademarks of Broadcom. Copyright © 2020 Broadcom. All Rights Reserved. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries. For more information, please visit www.broadcom.com. Broadcom reserves the right to make changes without further notice to any products or data herein to improve reliability, function, or design. Information furnished by Broadcom is believed to be accurate and reliable. However, Broadcom does not assume any liability arising out of the application or use of this information, nor the application or use of any product or circuit described herein, neither does it convey any license under its patent rights nor the rights of others. Contents About PGP Command Line 1 Important Concepts 1 Technical Support 2 Installing 5 Install Location 5 Installing on AIX 6 Installing on AIX 6 Changing the Home Directory on AIX 7 Uninstalling on AIX 7 Installing on HP-UX 8 Installing on HP-UX 8 Changing the Home Directory on HP-UX 9 Installing to a Non-Default Directory on HP-UX 9 Uninstalling on HP-UX 9 Installing on macOS 10 Installing on macOS 10 Changing the Home Directory on macOS 10 Uninstalling on macOS 11 Installing on Red Hat Enterprise Linux, SLES, or Fedora Core 11 Installing on Red Hat Enterprise Linux or Fedora Core 11 Changing the Home Directory on Linux or Fedora Core 12 Uninstalling on Linux or Fedora Core 12 Installing on Oracle Solaris 13 Installing on Oracle -
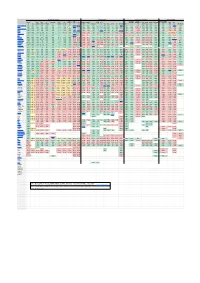
Digital Communications Protocols
Security & Privacy Compatibility Features & Usability Sustainability E2E E2E Offline Local Decentralized Active Open Open On Anonymous E2E E2E Default Audit FIDO1 Desktop Mobile Apple AOSP Messages messaging File Audio Video Phoneless or Federated Open IETF [1] TLS Client Server Premise [2] Private Group [3] [4] / U2F Web Web Android iOS [5] Win macOS Linux *BSD Terminal MDM [6] [7] [8] Share Call Call [9] [10] Spec [11] Introduced Element/Matrix TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE PARTIAL TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE FALSE 2014 XMPP TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE PARTIAL [12]TRUE FALSE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE FALSE [13] TRUE TRUE TRUE TRUE TRUE TRUE TRUE 1999 NextCloud Talk TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE FALSE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE FALSE TRUE TRUE FALSE TRUE TRUE TRUE TRUE TRUE FALSE FALSE 2018 Wire TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE FALSE TRUE FALSE TRUE TRUE FALSE TRUE TRUE TRUE TRUE PARTIAL TRUE TRUE FALSE TRUE TRUE TRUE TRUE FALSE FALSE FALSE 2014 Jami TRUE TRUE TRUE N/A [14] N/A TRUE TRUE FALSE [15] TRUE FALSE N/A [16] FALSE FALSE TRUE TRUE TRUE TRUE TRUE TRUE TRUE FALSE TRUE FALSE FALSE TRUE TRUE TRUE TRUE TRUE PARTIAL PARTIAL[17] [18] 2016 Briar [19] TRUE TRUE TRUE N/A [20] N/A TRUE TRUE TRUE TRUE TRUE N/A [21] FALSE FALSE TRUE FALSE TRUE FALSE FALSE FALSE FALSE FALSE FALSE TRUE TRUE FALSE FALSE FALSE FALSE TRUE FALSE FALSE 2016 Tox TRUE TRUE TRUE