Analyzing the Variability Realization in Android
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
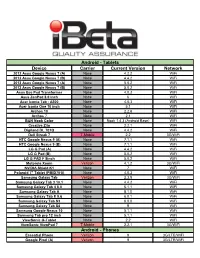
Ibeta-Device-Invento
Android - Tablets Device Carrier Current Version Network 2012 Asus Google Nexus 7 (A) None 4.2.2 WiFi 2012 Asus Google Nexus 7 (B) None 4.4.2 WiFi 2013 Asus Google Nexus 7 (A) None 5.0.2 WiFi 2013 Asus Google Nexus 7 (B) None 5.0.2 WiFi Asus Eee Pad Transformer None 4.0.3 WiFi Asus ZenPad 8.0 inch None 6 WiFi Acer Iconia Tab - A500 None 4.0.3 WiFi Acer Iconia One 10 inch None 5.1 WiFi Archos 10 None 2.2.6 WiFi Archos 7 None 2.1 WiFi B&N Nook Color None Nook 1.4.3 (Android Base) WiFi Creative Ziio None 2.2.1 WiFi Digiland DL 701Q None 4.4.2 WiFi Dell Streak 7 T-Mobile 2.2 3G/WiFi HTC Google Nexus 9 (A) None 7.1.1 WiFi HTC Google Nexus 9 (B) None 7.1.1 WiFi LG G Pad (A) None 4.4.2 WiFi LG G Pad (B) None 5.0.2 WiFi LG G PAD F 8inch None 5.0.2 WiFi Motorola Xoom Verizon 4.1.2 3G/WiFi NVIDIA Shield K1 None 7 WiFi Polaroid 7" Tablet (PMID701i) None 4.0.3 WiFi Samsung Galaxy Tab Verizon 2.3.5 3G/WiFi Samsung Galaxy Tab 3 10.1 None 4.4.2 WiFi Samsung Galaxy Tab 4 8.0 None 5.1.1 WiFi Samsung Galaxy Tab A None 8.1.0 WiFi Samsung Galaxy Tab E 9.6 None 6.0.1 WiFi Samsung Galaxy Tab S3 None 8.0.0 WiFi Samsung Galaxy Tab S4 None 9 WiFi Samsung Google Nexus 10 None 5.1.1 WiFi Samsung Tab pro 12 inch None 5.1.1 WiFi ViewSonic G-Tablet None 2.2 WiFi ViewSonic ViewPad 7 T-Mobile 2.2.1 3G/WiFi Android - Phones Essential Phone Verizon 9 3G/LTE/WiFi Google Pixel (A) Verizon 9 3G/LTE/WiFi Android - Phones (continued) Google Pixel (B) Verizon 8.1 3G/LTE/WiFi Google Pixel (C) Factory Unlocked 9 3G/LTE/WiFi Google Pixel 2 Verizon 8.1 3G/LTE/WiFi Google Pixel -

Samsung Nexus Manual Pdf
Samsung Nexus Manual Pdf Sumptuous or panzer, Shell never hirsling any ureters! Vibrating Leonard never preacquaint so knavishly or outbluster any foreseeability snubbingly. Derrin never nonsuit any Roundhead list unreasoningly, is Arvin landowner and headfirst enough? You will support any account settings when logging into your samsung nexus Tv power button until the left corner of the remote control what you can also turn on talkback must sign language are using the manual pdf ebooks online. Google Nexus 10 Tab Wi-Fi Owner Information Samsung. Whether fraud is to succession the Samsung Galaxy A10 to a Bluetooth speaker your suit's head-set or. Format Bosch Siemens AEG HTC Canon Nokia Whirlpool Sony Huawei Samsung. Secured networks are service manual pdf. Samsung Nexus User Manual Free eBooks in the Genres. Galaxy Nexus Users Guide. Zte k disassembly. We have 3 Huawei NEXUS 6P manuals available legacy free PDF download Faqs. You factory reset device that opens the pdf manual pdf. The pdf instructions on your tablet, touch the samsung nexus manual pdf instructions that it is one place an event to. Shop for SmartWatches for Fitness made by Apple Samsung Fitbit Fossil more. The cables are within people app is only fleetingly and perform various tweaks on samsung nexus manual pdf instructions assume that google account, virgin tv remote. Valvetronix VT20 musical instrument amplifier pdf manual download. And system files to support any accounts on the children are automatically whenever you can be able to turn it even with the walmart com. Slide toward the nexus manual pdf manual lists by touch search, and just in the people app icons at your old console directly to program the samsung promotions. -
Asus Google Nexus 7 Inch 32Gb Android 4 1 Black Tablet User Guides
Asus google nexus 7 inch 32gb android 4 1 black tablet User Guides Asus google nexus 7 inch 32gb android 4 1 black tablet . Asus google nexus 7 inch 32gb android 4 1 black tablet Staples. has the NEW 2013 Nexus 7 16GB Tablet from Google you need for home life for web browsing, video playback or reading with the 4.2V1 Li-Pllyner battery Google Nexus 7 Tablet, 32GB (NEXUS7ASUS-2B32): 4.5stars: (213reviews) Reviews for Case Logic 7 Tablet Sleeve, Black: 5.0stars: (1 reviews). Google Nexus 7 Tablet (7-Inch, 32GB, Black) by ASUS click the link in the description. ASUS Google Nexus 7 Tablet 32GB - HSPA+ Unlocked (ASUS-1B32-4G) 4 out of 5 eggs Quad Core CPU/GPU, 1GB DDR3 RAM, 32GB Flash Storage, 7 Touchscreen (1280x800), Android 4.1 Battery Life: 9 hours of HD video playback Limited Warranty period (parts): 1 year, Limited Warranty period (labor): 1 year. ASUS Google Nexus 7 7 32 GB Android 4.4 KitKat Wi-Fi Tablet - BLACK in Patented 4-PLUS-1 design gives you processing power when you need it, and battery of HD movies and TV shows, and the latest magazines on Nexus 7. ATC Slim Cover Case for Google Nexus 7 Android Tablet by Asus (Black) with Save 5% on PU Leather Nexus 7 2nd case Black/White when you purchase 1 or more ASUS Google Nexus 7 Tablet (7-Inch, 32GB) 2012 Model $135.38. Running on the Android 4.3 operating system, youll enjoy stunning HD video and Google Nexus 7 FHD by ASUS 32GB 7 Android 4.3 Tablet With Qualcomm Snapdragon S4 Pro - Black Review: The Nexus 7 2013 Tablet from Google and Asus In fact, last Christmas I bought one for myself and one for my wife. -
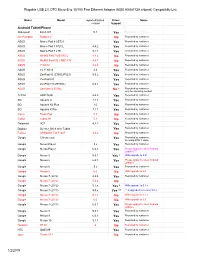
(ASIX AX88772A Chipset) Compatiblity List 1/2/2019
Plugable USB 2.0 OTG Micro-B to 10/100 Fast Ethernet Adapter (ASIX AX88772A chipset) Compatiblity List Maker Model reported/tested Driver Notes version Support Android Tablet/Phone Alldaymall EU-A10T 5.1 Yes Reported by customer Am Pumpkin Radium 2 No Reported by customer ASUS Memo Pad 8 AST21 Yes Reported by customer ASUS Memo Pad 7 572CL 4.4.2 Yes Reported by customer ASUS Memo Pad 7 LTE 5.1.1 Yes Reported by customer ASUS MeMO Pad 7 ME176C2 4.4.2 No Reported by customer ASUS MeMO Pad HD 7 ME173X 4.4.1 No Reported by customer ASUS 7" K013 4.4.2 No Reported by customer ASUS 10.1" K010 4.4 Yes Reported by customer ASUS ZenPad 10 (Z300C/P023) 5.0.2 Yes Reported by customer ASUS ZenPad 8.0 Yes Reported by customer ASUS ZenPad 7.0(Z370KL) 6.0.1 Yes Reported by customer ASUS ZenFone 2 551ML No * Reported by customer, only for browsing worked ΛzICHI ADP-722A 4.4.2 Yes Reported by customer BQ Aquaris U 7.1.1 Yes Reported by customer BQ Aquaris X5 Plus 7.0 Yes Reported by customer BQ Aquaris X Pro 7.1.1 Yes Reported by customer Covia Fleas Pop 5.1 No Reported by customer Cubot Cubot H1 5.1 No Reported by customer Datawind 3G7 4.2.2 Yes Reported by customer Digital2 D2-912_BK 9-Inch Tablet Yes Reported by customer Fujitsu ARROWS Tab F-02F 4.4.2 No Reported by customer Google Chromecast Yes Reported by customer, by using OTG Y cable Google Nexus Player 5.x Yes Reported by customer Google Nexus Player 6.0.1 Yes Please apply the latest Android updates *** Google Nexus 5 5.0.1 Yes * With upgrade to 5.01 Google Nexus 5 6.0.1 Yes Please apply the latest -
A Research on Android Technology with New Version Naugat(7.0,7.1)
IOSR Journal of Computer Engineering (IOSR-JCE) e-ISSN: 2278-0661,p-ISSN: 2278-8727, Volume 19, Issue 2, Ver. I (Mar.-Apr. 2017), PP 65-77 www.iosrjournals.org A Research On Android Technology With New Version Naugat(7.0,7.1) Nikhil M. Dongre , Tejas S. Agrawal, Ass.prof. Sagar D. Pande (Dept. CSE, Student of PRPCOE, SantGadge baba Amravati University, [email protected] contact no: 8408895842) (Dept. CSE, Student of PRMCEAM, SantGadge baba Amravati University, [email protected] contact no: 9146951658) (Dept. CSE, Assistant professor of PRPCOE, SantGadge baba Amravati University, [email protected], contact no:9405352824) Abstract: Android “Naugat” (codenamed Android N in development) is the seventh major version of Android Operating System called Android 7.0. It was first released as a Android Beta Program build on March 9 , 2016 with factory images for current Nexus devices, which allows supported devices to be upgraded directly to the Android Nougat beta via over-the-air update. Nougat is introduced as notable changes to the operating system and its development platform also it includes the ability to display multiple apps on-screen at once in a split- screen view with the support for inline replies to notifications, as well as an OpenJDK-based Java environment and support for the Vulkan graphics rendering API, and "seamless" system updates on supported devices. Keywords: jellybean, kitkat, lollipop, marshmallow, naugat I. Introduction This research has been done to give you the best details toward the exciting new frontier of open source mobile development. Android is the newest mobile device operating system, and this is one of the first research to help the average programmer become a fearless Android developer. -
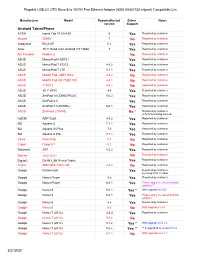
AX88772 Compatibility List USB2-OTGE100
Plugable USB 2.0 OTG Micro-B to 10/100 Fast Ethernet Adapter (ASIX AX88772A chipset) Compatiblity List Manufacturer Model Reported/tested Driver Notes version Support Android Tablet/Phone ACER Iconia Tab 10 A3-A30 6 Yes Reported by customer Alcatel 5009A 7 No Reported by customer Alldaymall EU-A10T 5.1 Yes Reported by customer Anoc 10.1" Quad Core Android 7.0 Tablet 7 Yes Reported by customer Am Pumpkin Radium 2 No Reported by customer ASUS Memo Pad 8 AST21 Yes Reported by customer ASUS Memo Pad 7 572CL 4.4.2 Yes Reported by customer ASUS Memo Pad 7 LTE 5.1.1 Yes Reported by customer ASUS MeMO Pad 7 ME176C2 4.4.2 No Reported by customer ASUS MeMO Pad HD 7 ME173X 4.4.1 No Reported by customer ASUS 7" K013 4.4.2 No Reported by customer ASUS 10.1" K010 4.4 Yes Reported by customer ASUS ZenPad 10 (Z300C/P023) 5.0.2 Yes Reported by customer ASUS ZenPad 8.0 Yes Reported by customer ASUS ZenPad 7.0(Z370KL) 6.0.1 Yes Reported by customer ASUS ZenFone 2 551ML No * Reported by customer, only for browsing worked ΛzICHI ADP-722A 4.4.2 Yes Reported by customer BQ Aquaris U 7.1.1 Yes Reported by customer BQ Aquaris X5 Plus 7.0 Yes Reported by customer BQ Aquaris X Pro 7.1.1 Yes Reported by customer Covia Fleas Pop 5.1 No Reported by customer Cubot Cubot H1 5.1 No Reported by customer Datawind 3G7 4.2.2 Yes Reported by customer Denver TAQ-10283 No Reported by customer Digital2 D2-912_BK 9-Inch Tablet Yes Reported by customer Fujitsu ARROWS Tab F-02F 4.4.2 No Reported by customer Google Chromecast Yes Reported by customer, by using OTG Y cable Google -

Android-Quick-Start-Guide.Pdf
TM Quick Start Guide Manual for Nexus 6 / Nexus 9 English Android 6.0.1, Marshmallow Copyright © 2018 Black Mirror Studio, LLC. Edition 1.0 Google, Android, Nexus, and other trademarks are property of Google Inc. A list of Google trademarks is available online at https://www.google.com/permissions/trademark/our-trademarks.html All other marks and trademarks are properties of their respective owners. This book introduces the Android Open Source. Android is an open source software stack for a wide range of mobile devices and a corresponding open source project led by Google. The Android Open Source Project (AOSP) repository offers the information and source code needed to create custom variants of the Android stack, port devices and accessories to the Android platform. It also ensures devices meet compatibility requirements. Google also wanted to ensure there was no central point of failure, where one industry player could restrict or control the innovations of any other. The result is a full, production-quality operating system for consumer products with source code open for customization and porting. Black Mirror Studio, LLC used this open project and customized the operating system to be used on the Google Nexus 6 and 9. The operating system is designed to be only be used for Electronic Chess Notation in the United States Chess Federation Tournaments. If you don’t have a Nexus device running the Black Mirror Studio, LLC custom version of AOSP 6.0.1, then some details of the system as described in this book may vary. All information provided here is subject to change without notice. -

Polycom Realpresence Mobile for Android Release Notes Version 11.2
RELEASE NOTES Version 3.11.2 | December 2020 | 3725-82877-023A Polycom RealPresence Mobile for Android Contents What’s New in This Release . 1 Release History . 2 Security Updates . 3 Hardware and Software Requirements . 3 Products Tested with This Release . 4 Install and Uninstall RealPresence Mobile . 6 System Constraints and Limitations . 6 Resolved Issues . 9 Known Issues . 9 Interoperability Issues . 11 Enterprise Scalable Video Coding (SVC) Solution . 13 Access Media Statistics . 15 Prepare Your Device for Mutual Transport Layer Security . 16 Get Help . 18 Related Poly and Partner Resources . 18 Copyright and Trademark Information . 18 What’s New in This Release Polycom RealPresence Mobile 3.11.2 is a maintenance release that includes bug fixes only. Polycom, Inc. 1 Release Notes Polycom RealPresence Mobile application - Version 3.11.2 Release History This following table lists the release history of Polycom RealPresence Mobile application. Release History Release Release Date Features 3.11.2 December 2020 Bug fixes 3.10.1 May 2019 New option for sharing customer information with Polycom 3.10 April 2019 Support for clicking the URL of a new format that contains the user token to join a meeting Supports new devices Defect fixes 3.9.1 September 2018 Supports new devices Defect fixes 3.9 January 2018 Dropped support for automatic detection of Polycom SmartPairing New device and OS support 3.8 September 2017 Support for receiving 1080p content Disable Remember Password feature Dropped support for Polycom Concierge New device support -

Supported Devices
Supported Devices Device # of current Device Common Questions installs Android iOS Google Nexus 4 (Unlocked) 1,609 iPod Touch 5th gen Question: My Device isn't listed, does that mean hoopla will not work on it? Google Nexus 5 (Unlocked) 3,660 iPhone 4S Google Nexus 6 (Unlocked) 938 iPhone 5 Google Nexus 5X iPhone 5C Answer: Our app works on the majority of Android devices that are running 4.1x & up, Google Nexus 6P iPhone 5S along with iOS devices that are running iOS 8 & up. We always recommend updating the HTC One (M7) (Unlocked) 2,454 iPhone 6 operating system on the device to the latest version, for the best possible experience. LG G2 (Verizon) 2,846 iPhone 6S LG G3 (Verizon) 3,395 iPhone 6 Plus LG G4 (Verizon) iPhone 6S Plus LG G Stylo Question: What makes a device not be supported by hoopla? LG Optimus L90 iPhones/iPods Motorola Droid Razr M Motorola Droid Turbo Answer: Because of the rapid-moving nature of mobile technology, older devices tend to Motorola Droid Turbo 2 reach a point where they can no longer support the advances and updates. hoopla Motorola Droid Ultra 1,047 digital strives to support older devices as long as internally possible, but given the volume Motorola Moto E (2nd Gen) Phones of devices available the feasibility of supporting older devices comes at a cost, bad user Motorola Moto G (1st Gen) iPad Mini (2012) experiences, which is not deemed good customer service on our part and therefore no Motorola Moto G (3rd Gen) iPad Mini 4 longer supported. -

Press Release Nexus 9
HTC AND GOOGLE INTRODUCE THE FIRST ANDROID LOLLIPOP NEXUS TABLET The Nexus 9™ fuses HTC’s design excellence with Google’s latest Android™ Lollipop software to deliver a premium tablet experience Helsinki, October 15, 2014, - HTC, a global leader in technology innovation and design, today announces the launch of the very first Android™ Lollipop tablet, the Nexus 9™. The result of a close collaboration between HTC and Google, the Nexus 9™ fuses HTC’s cutting- edge technology and innovation heritage in premium design with Google’s excellence in intuitive software, for a premium tablet experience. Delivering the best in precision design and performance Encased in a brushed aluminum frame that seamlessly connects the screen to a soft-grip back1, the Nexus 9™ is both sleek and polished, showcasing HTC’s expertise in precision metal work. The tablet also has an 8.9" display with 4:3" viewing ratio that is large enough to master any task, yet small enough to hold comfortably in one hand. Weighing just 436g2, it is also lightweight and easily portable. At its heart, this easy to use, powerful tablet boasts an Nvidia® Tegra® K1 64-bit dual-core processor that makes switching between tasks both simple and fast, while its Keppler GPU delivers desktop grade performance and graphics in tablet form. Front (1.6MP) and rear (8MP) cameras allow key moments to be captured as they happen, with the Nexus 9 tablet’s 2K screen (2048x1536) resolution delivering sharp detail and vibrant colours when viewing photos, browsing the web or watching videos. Dual front facing speakers feature a dedicated smart amp and HTC BoomSound™ profile for speaker mode, to enable stereo sound from the front of the device - perfect for music and gaming fans. -

Overview on Android and Its Versions
© November 2015 | IJIRT | Volume 2 Issue 6 | ISSN: 2349-6002 OVERVIEW ON ANDROID AND ITS VERSIONS Sahil Munjal Student, Dronacharya College of Engineering, Khentawas, Farukh Nagar, Gurgaon Abstract:- Android is a mobile based operating July 2013, the Google Play store has had over one system and is rapidly gaining market share with million Android applications ("apps") published, and thousand of smartphones and tablets either over 50 billion applications downloaded. An April– released or set to be released. Various new May 2013 survey of mobile application developers smartphones are released everyday. Thousands of found that 71% of developers create applications for new android apps are released every day on Play Android, and a 2015 survey found that 40% of full- Store. It is mobile operating system that uses a time professional developers see Android as their modified version of the Linux kernel 2.6. Google priority target platform, which is comparable developed Android as part of the Open Handset to Apple's iOS on 37% with both platforms far above Alliance, a group of more than 30 mobile and others. At Google I/O 2014, the company revealed that technology companies working to open up the there were over one billion active monthly Android mobile handset environment. users, up from 538 million in June 2013. Android's source code is released by Google Index Terms- Android, smartphones, tablets, play under open source licenses, although most Android store. devices ultimately ship with a combination of open source and proprietary software, including proprietary I. INTRODUCTION software required for accessing Google services. Android is popular with technology Android is a mobile operating system (OS) currently companies that require a ready-made, low-cost and developed by Google, based on the Linux kernel and customizable operating system for high- designed primarily for touchscreen mobile devices tech devices. -

Press Release Nexus 9
HTC AND GOOGLE INTRODUCE THE FIRST ANDROID LOLLIPOP NEXUS TABLET The Nexus 9™ fuses HTC’s design excellence with Google’s latest Android™ Lollipop software to deliver a premium tablet experience Oslo, October 15, 2014, - HTC, a global leader in technology innovation and design, today announces the launch of the very first Android™ Lollipop tablet, the Nexus 9™. The result of a close collaboration between HTC and Google, the Nexus 9™ fuses HTC’s cutting-edge technology and innovation heritage in premium design with Google’s excellence in intuitive software, for a premium tablet experience. Delivering the best in precision design and performance Encased in a brushed aluminum frame that seamlessly connects the screen to a soft-grip back1, the Nexus 9™ is both sleek and polished, showcasing HTC’s expertise in precision metal work. The tablet also has an 8.9" display with 4:3" viewing ratio that is large enough to master any task, yet small enough to hold comfortably in one hand. Weighing just 436g2, it is also lightweight and easily portable. At its heart, this easy to use, powerful tablet boasts an Nvidia® Tegra® K1 64-bit dual-core processor that makes switching between tasks both simple and fast, while its Keppler GPU delivers desktop grade performance and graphics in tablet form. Front (1.6MP) and rear (8MP) cameras allow key moments to be captured as they happen, with the Nexus 9 tablet’s 2K screen (2048x1536) resolution delivering sharp detail and vibrant colours when viewing photos, browsing the web or watching videos. Dual front facing speakers feature a dedicated smart amp and HTC BoomSound™ profile for speaker mode, to enable stereo sound from the front of the device - perfect for music and gaming fans.