UNIX Tutorial Two
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

AEDIT Text Editor Iii Notational Conventions This Manual Uses the Following Conventions: • Computer Input and Output Appear in This Font
Quick Contents Chapter 1. Introduction and Tutorial Chapter 2. The Editor Basics Chapter 3. Editing Commands Chapter 4. AEDIT Invocation Chapter 5. Macro Commands Chapter 6. AEDIT Variables Chapter 7. Calc Command Chapter 8. Advanced AEDIT Usage Chapter 9. Configuration Commands Appendix A. AEDIT Command Summary Appendix B. AEDIT Error Messages Appendix C. Summary of AEDIT Variables Appendix D. Configuring AEDIT for Other Terminals Appendix E. ASCII Codes Index AEDIT Text Editor iii Notational Conventions This manual uses the following conventions: • Computer input and output appear in this font. • Command names appear in this font. ✏ Note Notes indicate important information. iv Contents 1 Introduction and Tutorial AEDIT Tutorial ............................................................................................... 2 Activating the Editor ................................................................................ 2 Entering, Changing, and Deleting Text .................................................... 3 Copying Text............................................................................................ 5 Using the Other Command....................................................................... 5 Exiting the Editor ..................................................................................... 6 2 The Editor Basics Keyboard ......................................................................................................... 8 AEDIT Display Format .................................................................................. -

COMMAND LINE CHEAT SHEET Presented by TOWER — the Most Powerful Git Client for Mac
COMMAND LINE CHEAT SHEET presented by TOWER — the most powerful Git client for Mac DIRECTORIES FILES SEARCH $ pwd $ rm <file> $ find <dir> -name "<file>" Display path of current working directory Delete <file> Find all files named <file> inside <dir> (use wildcards [*] to search for parts of $ cd <directory> $ rm -r <directory> filenames, e.g. "file.*") Change directory to <directory> Delete <directory> $ grep "<text>" <file> $ cd .. $ rm -f <file> Output all occurrences of <text> inside <file> (add -i for case-insensitivity) Navigate to parent directory Force-delete <file> (add -r to force- delete a directory) $ grep -rl "<text>" <dir> $ ls Search for all files containing <text> List directory contents $ mv <file-old> <file-new> inside <dir> Rename <file-old> to <file-new> $ ls -la List detailed directory contents, including $ mv <file> <directory> NETWORK hidden files Move <file> to <directory> (possibly overwriting an existing file) $ ping <host> $ mkdir <directory> Ping <host> and display status Create new directory named <directory> $ cp <file> <directory> Copy <file> to <directory> (possibly $ whois <domain> overwriting an existing file) OUTPUT Output whois information for <domain> $ cp -r <directory1> <directory2> $ curl -O <url/to/file> $ cat <file> Download (via HTTP[S] or FTP) Copy <directory1> and its contents to <file> Output the contents of <file> <directory2> (possibly overwriting files in an existing directory) $ ssh <username>@<host> $ less <file> Establish an SSH connection to <host> Output the contents of <file> using -

UNIX Version 7 Volume 1
UNIXTM TIME-SHARING SYSTEM: UNIX PROGRAMMER'S MANUAL Seventh Edition, Volume 1 January, 1979 Bell Telephone Laboratories, Incorporated Murray Hill, New Jersey PREFACE Although this Seventh Edition no longer bears their byline, Ken Thompson and Dennis Ritchie remain the fathers and preceptors of the UNIX² time-sharing system. Many of the improvements here described bear their mark. Among many, many other people who have contributed to the further ¯owering of UNIX, we wish especially to acknowledge the contributions of A. V. Aho, S. R. Bourne, L. L. Cherry, G. L. Chesson, S. I. Feldman, C. B. Haley, R. C. Haight, S. C. Johnson, M. E. Lesk, T. L. Lyon, L. E. McMahon, R. Morris, R. Muha, D. A. Nowitz, L. Wehr, and P. J. Weinberger. We appreciate also the effective advice and criticism of T. A. Dolotta, A. G. Fraser, J. F. Maranzano, and J. R. Mashey; and we remember the important work of the late Joseph F. Ossanna. B. W. Kernighan M. D. McIlroy __________________ ²UNIX is a Trademark of Bell Laboratories. INTRODUCTION TO VOLUME 1 This volume gives descriptions of the publicly available features of the UNIX² system. It does not attempt to provide perspective or tutorial information upon the UNIX operating system, its facilities, or its implementation. Various documents on those topics are contained in Volume 2. In particular, for an overview see `The UNIX Time-Sharing System' by Ritchie and Thompson; for a tutorial see `UNIX for Beginners' by Kernighan. Within the area it surveys, this volume attempts to be timely, complete and concise. Where the latter two objectives con¯ict, the obvious is often left unsaid in favor of brevity. -

AT Command User Guide 80591ST10886A Rev
LN940 SERIES AT Command User Guide 80591ST10886A Rev. 1.4 – 2018-04-05 ] 7 .201 Mod. 0806 2017-01 Rev.6 01 [ SPECIFICATIONS ARE SUBJECT TO CHANGE WITHOUT NOTICE NOTICES LIST While reasonable efforts have been made to assure the accuracy of this document, Telit assumes no liability resulting from any inaccuracies or omissions in this document, or from use of the information obtained herein. The information in this document has been carefully checked and is believed to be reliable. However, no responsibility is assumed for inaccuracies or omissions. Telit reserves the right to make changes to any products described herein and reserves the right to revise this document and to make changes from time to time in content hereof with no obligation to notify any person of revisions or changes. Telit does not assume any liability arising out of the application or use of any product, software, or circuit described herein; neither does it convey license under its patent rights or the rights of others. It is possible that this publication may contain references to, or information about Telit products (machines and programs), programming, or services that are not announced in your country. Such references or information must not be construed to mean that Telit intends to announce such Telit products, programming, or services in your country. COPYRIGHTS This instruction manual and the Telit products described in this instruction manual may be, include or describe copyrighted Telit material, such as computer programs stored in semiconductor memories or other media. Laws in the Italy and other countries preserve for Telit and its licensors certain exclusive rights for copyrighted material, including the exclusive right to copy, reproduce in any form, distribute and make derivative works of the copyrighted material. -

Clostridium Difficile (C. Diff)
Living with C. diff Learning how to control the spread of Clostridium difficile (C. diff) This can be serious, I need to do something about this now! IMPORTANT C. diff can be a serious condition. If you or someone in your family has been diagnosed with C. diff, there are steps you can take now to avoid spreading it to your family and friends. This booklet was developed to help you understand and manage C. diff. Follow the recommendations and practice good hygiene to take care of yourself. C. diff may cause physical pain and emotional stress, but keep in mind that it can be treated. For more information on your C.diff infection, please contact your healthcare provider. i CONTENTS Learning about C. diff What is Clostridium difficile (C. diff)? ........................................................ 1 There are two types of C.diff conditions .................................................... 2 What causes a C. diff infection? ............................................................... 2 Who is most at risk to get C. diff? ............................................................ 3 How do I know if I have C. diff infection? .................................................. 3 How does C. diff spread from one person to another? ............................... 4 What if I have C. diff while I am in a healthcare facility? ............................. 5 If I get C. diff, will I always have it? ........................................................... 6 Treatment How is C. diff treated? ............................................................................. 7 Prevention How can the spread of C. diff be prevented in healthcare facilities? ............ 8 How can I prevent spreading C. diff (and other germs) to others at home? .. 9 What is good hand hygiene? .................................................................... 9 What is the proper way to wash my hands? ............................................ 10 What is the proper way to clean? ......................................................... -

Lab - Observing DNS Resolution (Instructor Version) Instructor Note: Red Font Color Or Gray Highlights Indicate Text That Appears in the Instructor Copy Only
Lab - Observing DNS Resolution (Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Objectives Part 1: Observe the DNS Conversion of a URL to an IP Address Part 2: Observe DNS Lookup Using the Nslookup Command on a Web Site Part 3: Observe DNS Lookup Using the Nslookup Command on Mail Servers Background / Scenario The Domain Name System (DNS) is invoked when you type a Uniform Resource Locator (URL), such as http://www.cisco.com, into a web browser. The first part of the URL describes which protocol is used. Common protocols are Hypertext Transfer Protocol (HTTP), Hypertext Transfer Protocol over Secure Socket Layer (HTTPS), and File Transfer Protocol (FTP). DNS uses the second part of the URL, which in this example is www.cisco.com. DNS translates the domain name (www.cisco.com) to an IP address to allow the source host to reach the destination host. In this lab, you will observe DNS in action and use the nslookup (name server lookup) command to obtain additional DNS information. Work with a partner to complete this lab. Required Resources 1 PC (Windows 7, Vista, or XP with Internet and command prompt access) Part 1: Observe the DNS Conversion of a URL to an IP Address a. Click the Windows Start button, type cmd into the search field, and press Enter. The command prompt window appears. b. At the command prompt, ping the URL for the Internet Corporation for Assigned Names and Numbers (ICANN) at www.icann.org. ICANN coordinates the DNS, IP addresses, top-level domain name system management, and root server system management functions. -

Your Performance Task Summary Explanation
Lab Report: 11.2.5 Manage Files Your Performance Your Score: 0 of 3 (0%) Pass Status: Not Passed Elapsed Time: 6 seconds Required Score: 100% Task Summary Actions you were required to perform: In Compress the D:\Graphics folderHide Details Set the Compressed attribute Apply the changes to all folders and files In Hide the D:\Finances folder In Set Read-only on filesHide Details Set read-only on 2017report.xlsx Set read-only on 2018report.xlsx Do not set read-only for the 2019report.xlsx file Explanation In this lab, your task is to complete the following: Compress the D:\Graphics folder and all of its contents. Hide the D:\Finances folder. Make the following files Read-only: D:\Finances\2017report.xlsx D:\Finances\2018report.xlsx Complete this lab as follows: 1. Compress a folder as follows: a. From the taskbar, open File Explorer. b. Maximize the window for easier viewing. c. In the left pane, expand This PC. d. Select Data (D:). e. Right-click Graphics and select Properties. f. On the General tab, select Advanced. g. Select Compress contents to save disk space. h. Click OK. i. Click OK. j. Make sure Apply changes to this folder, subfolders and files is selected. k. Click OK. 2. Hide a folder as follows: a. Right-click Finances and select Properties. b. Select Hidden. c. Click OK. 3. Set files to Read-only as follows: a. Double-click Finances to view its contents. b. Right-click 2017report.xlsx and select Properties. c. Select Read-only. d. Click OK. e. -

Rve P.Vp:Corelventura
® M-8400RVe Thermal Transfer Printer Operator and Technical Reference Manual PN 9001075A SATO America, Inc. 10350-A Nations Ford Rd. Charlotte, NC 28273 Main Phone: (704) 644-1650 Fax: (704) 644-1661 Technical Support Hotline: (704) 644-1660 E-Mail:[email protected] © Copyright 2000 SATO America, Inc. Warning: This equipment complies with the requirements in Part 15 of FCC rules for a Class A computing device. Operation of this equipment in a residential area may cause unacceptable interference to radio and TV reception requiring the operator to take whatever steps are necessary to correct the interference. All rights reserved. No part of this document may be reproduced or issued to third parties in any form whatsoever without the express permission of SATO America, Inc. The materials in this document is provided for general information and is subject to change without notice. SATO America, Inc. assumes no responibilities for any errors that may appear. SATOM8400RVe PREFACE M-8400RVe PRINTER OPERATOR’S MANUAL The M-8400RVe Printer Operator’s Manual contains basic information about the printer such as setup, installation, cleaning and maintenance. It also contains complete instructions on how to use the operator panel to configure the printer. The following is a brief description of each section in this manual. SECTION 1. PRINTER OVERVIEW This section contains a discussion of the printer specifications and optional features. SECTION 2. INSTALLATION This section contains instructions on how to unpack and set up the printer, load the labels and ribbon. SECTION 3. CONFIGURATION This section contains instructions on how to configure the printer using the DIP switches and the LCD/Menu/Control panel. -

Powerview Command Reference
PowerView Command Reference TRACE32 Online Help TRACE32 Directory TRACE32 Index TRACE32 Documents ...................................................................................................................... PowerView User Interface ............................................................................................................ PowerView Command Reference .............................................................................................1 History ...................................................................................................................................... 12 ABORT ...................................................................................................................................... 13 ABORT Abort driver program 13 AREA ........................................................................................................................................ 14 AREA Message windows 14 AREA.CLEAR Clear area 15 AREA.CLOSE Close output file 15 AREA.Create Create or modify message area 16 AREA.Delete Delete message area 17 AREA.List Display a detailed list off all message areas 18 AREA.OPEN Open output file 20 AREA.PIPE Redirect area to stdout 21 AREA.RESet Reset areas 21 AREA.SAVE Save AREA window contents to file 21 AREA.Select Select area 22 AREA.STDERR Redirect area to stderr 23 AREA.STDOUT Redirect area to stdout 23 AREA.view Display message area in AREA window 24 AutoSTOre .............................................................................................................................. -
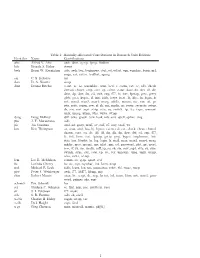
Manually-Allocated Contributions in Research Unix Editions Identifier Name Contributions Aho Alfred V
Table 1: Manually-Allocated Contributions in Research Unix Editions Identifier Name Contributions aho Alfred V. Aho awk, dbm, egrep, fgrep, libdbm bsb Brenda S. Baker struct bwk Brian W. Kernighan adv, awk, beg, beginners, ctut, ed, edtut, eqn, eqnchar, learn, m4, neqn, rat, ratfor, trofftut, uprog csr C. S. Roberts tss dan D. A. Nowitz uucp dmr Dennis Ritchie a.out, ar, as, assembler, atan, bcd, c, cacm, cat, cc, cdb, check, chmod, chown, cmp, core, cp, ctime, ctour, date, db, dev, df, dir, dmr, dp, dsw, du, ed, exit, exp, f77, fc, fort, fptrap, getc, getty, glob, goto, hypot, if, init, iolib, iosys, istat, ld, libc, ln, login, ls, m4, man2, man3, man4, mesg, mkdir, mount, mv, nm, od, pr, ptx, putc, regen, rew, rf, rk, rm, rmdir, rp, secur, security, setup, sh, sin, sort, sqrt, strip, stty, su, switch, tp, tty, type, umount, unix, uprog, utmp, who, write, wtmp doug Doug McIlroy diff, echo, graph, join, look, m6, sort, spell, spline, tmg jfm J. F. Maranzano adb jfo Joe Ossanna azel, ed, getty, nroff, ov, roff, s7, stty, troff, wc ken Ken Thompson ar, atan, atof, bas, bj, bproc, cacm, cal, cat, check, chess, chmod, chown, core, cp, dc, dd, df, dir, dli, dp, dsw, dtf, ed, exp, f77, fc, fed, form, fort, fptrap, getty, grep, hypot, implement, init, itoa, ken, libplot, ln, log, login, ls, mail, man, man2, man4, mesg, mkdir, moo, mount, mv, nlist, nm, od, password, plot, pr, qsort, rew, rf, rk, rm, rmdir, roff, rp, sa, sh, sin, sort, sqrt, stty, su, sum, switch, sync, sys, tabs, tp, ttt, tty, umount, uniq, unix, utmp, who, write, wtmp lem Lee E. -

NETSTAT Command
NETSTAT Command | NETSTAT Command | Use the NETSTAT command to display network status of the local host. | | ┌┐────────────── | 55──NETSTAT─────6─┤ Option ├─┴──┬────────────────────────────────── ┬ ─ ─ ─ ────────────────────────────────────────5% | │┌┐───────────────────── │ | └─(──SELect───6─┤ Select_String ├─┴ ─ ┘ | Option: | ┌┐─COnn────── (1, 2) ──────────────── | ├──┼─────────────────────────── ┼ ─ ──────────────────────────────────────────────────────────────────────────────┤ | ├─ALL───(2)──────────────────── ┤ | ├─ALLConn─────(1, 2) ────────────── ┤ | ├─ARp ipaddress───────────── ┤ | ├─CLients─────────────────── ┤ | ├─DEvlinks────────────────── ┤ | ├─Gate───(3)─────────────────── ┤ | ├─┬─Help─ ┬─ ───────────────── ┤ | │└┘─?──── │ | ├─HOme────────────────────── ┤ | │┌┐─2ð────── │ | ├─Interval─────(1, 2) ─┼───────── ┼─ ┤ | │└┘─seconds─ │ | ├─LEVel───────────────────── ┤ | ├─POOLsize────────────────── ┤ | ├─SOCKets─────────────────── ┤ | ├─TCp serverid───(1) ─────────── ┤ | ├─TELnet───(4)───────────────── ┤ | ├─Up──────────────────────── ┤ | └┘─┤ Command ├───(5)──────────── | Command: | ├──┬─CP cp_command───(6) ─ ┬ ────────────────────────────────────────────────────────────────────────────────────────┤ | ├─DELarp ipaddress─ ┤ | ├─DRop conn_num──── ┤ | └─RESETPool──────── ┘ | Select_String: | ├─ ─┬─ipaddress────(3) ┬ ─ ───────────────────────────────────────────────────────────────────────────────────────────┤ | ├─ldev_num─────(4) ┤ | └─userid────(2) ─── ┘ | Notes: | 1 Only ALLCON, CONN and TCP are valid with INTERVAL. | 2 The userid -

HP BIOS Configuration Utility FAQ
Technical white paper HP BIOS Configuration Utility FAQ Table of contents Feature updates ............................................................................................................................................................................ 2 Common questions ....................................................................................................................................................................... 2 For more information ................................................................................................................................................................. 12 Feature updates Version Features 4.0.2.1 Changes config file keyword to BIOSConfig. Changes commands from /cspwdfile and /nspwdfile to /cpwdfile and /npwdfile to match HP SSM. Adds /Unicode command to query if a system supports a Unicode password. Removes BIOS user commands. Maintains backwards compatibility. 3.0.13.1 Allows only one /cspwdfile command. Adds /WarningAsErr command to include warnings in the final BCU return code. 3.0.3.1 Changes commands from /cspwd and /nspwd command to /cspwdfile and /nspwdfile to read passwords from encrypted files created by HPQPswd.exe 2.60.13.1 Adds additional return codes when encountering WMI errors. 2.60.3 Add /SetDefaults command to reset BIOS to factory default. Supports configuration file comments. Common questions Q: The BIOS Configuration Utility (BCU) is an HP utility, so why it does not work on some HP platforms? A: BCU is a command-line utility for controlling various BIOS settings on a supported HP notebook, desktop, or workstation system. It requires a BIOS that supports HP WMI Namespace within the BIOS. HP began integrating CMI/WMI support directly into the BIOS during approximately 2006–2008 for managed business systems, which did not include consumer-based systems or entry-level units. If the system BIOS does not have the required WMI support, BCU does not work. This is not a failure of BCU. It is a limitation of the system BIOS that does include WMI support in the BIOS code.