Defending Spacecraft in the Cyber Domain
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Vulnerability Assessment and Secure Coding Practices for Middleware Part 1
Vulnerability Assessment and Secure Coding Practices for Middleware Part 1 James A. Kupsch Computer Sciences Department University of Wisconsin © 2007-2008, James A. K1upsch. All rights reserved. Tutorial Objectives • Show how to perform the basics of a vulnerability assessment • Create more people doing vulnerability assessments • Show how different types of vulnerabilities arise in a system • Teach coding techniques that can prevent certain types of vulnerabilities • Make your software more secure 2 Roadmap • Part 1: Vulnerability Assessment Process – Introduction – Evaluation process – Architectural analysis – Computer process – Communication channels – Resource analysis – Privilege analysis – Data Flow Diagrams – Component analysis – Vulnerability Discovery Activities • Part 2: Secure Coding Practices 3 Security Problems Are Real Everyone with a computer knows this. If you’re not seeing vulnerability reports and fixes for a piece of software, it doesn’t mean that it is secure. It probably means the opposite; they aren’t looking or aren’t telling. The grid community has been largely lucky (security through obscurity). 4 Many Avenues of Attack We’re looking for attacks that exploit inherent weakness in your system. Internet Firewall: www server Attack web using www protocols Compromised host Internal bad guy 5 Impact of Vulnerabilities FBI estimates computer security incidents cost U.S. businesses $67 billion in 2005 [CNETnews.com] Number of reported vulnerabilities each year is increasing [CERT stats] 8000 6000 4000 2000 0 1994 1998 -
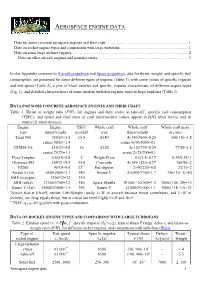
Aerospace Engine Data
AEROSPACE ENGINE DATA Data for some concrete aerospace engines and their craft ................................................................................. 1 Data on rocket-engine types and comparison with large turbofans ................................................................... 1 Data on some large airliner engines ................................................................................................................... 2 Data on other aircraft engines and manufacturers .......................................................................................... 3 In this Appendix common to Aircraft propulsion and Space propulsion, data for thrust, weight, and specific fuel consumption, are presented for some different types of engines (Table 1), with some values of specific impulse and exit speed (Table 2), a plot of Mach number and specific impulse characteristic of different engine types (Fig. 1), and detailed characteristics of some modern turbofan engines, used in large airplanes (Table 3). DATA FOR SOME CONCRETE AEROSPACE ENGINES AND THEIR CRAFT Table 1. Thrust to weight ratio (F/W), for engines and their crafts, at take-off*, specific fuel consumption (TSFC), and initial and final mass of craft (intermediate values appear in [kN] when forces, and in tonnes [t] when masses). Engine Engine TSFC Whole craft Whole craft Whole craft mass, type thrust/weight (g/s)/kN type thrust/weight mini/mfin Trent 900 350/63=5.5 15.5 A380 4×350/5600=0.25 560/330=1.8 cruise 90/63=1.4 cruise 4×90/5000=0.1 CFM56-5A 110/23=4.8 16 -

Rogue Automation: Vulnerable and Malicious Code in Industrial
In partnership with Rogue Automation Vulnerable and Malicious Code in Industrial Programming Federico Maggi Marcello Pogliani Trend Micro Research Politecnico di Milano Rogue Automation Vulnerable and Malicious Code in Industrial Programming Published by TREND MICRO LEGAL DISCLAIMER Trend Micro Research The information provided herein is for general information and educational purposes only. It is not intended and should not be construed to constitute legal advice. The information contained herein may not be applicable to all situations and may not reflect the most Written by current situation. Nothing contained herein should be relied on or acted upon without the benefit of legal advice based on the particular facts and circumstances presented and Federico Maggi nothing herein should be construed otherwise. Trend Micro reserves the right to modify Trend Micro Research the contents of this document at any time without prior notice. Marcello Pogliani Translations of any material into other languages are intended solely as a convenience. Politecnico di Milano Translation accuracy is not guaranteed nor implied. If any questions arise related to the accuracy of a translation, please refer to the original language official version of the document. Any discrepancies or differences created in the translation are not binding and With contributions from have no legal effect for compliance or enforcement purposes. Martino Vittone, Although Trend Micro uses reasonable efforts to include accurate and up-to-date Davide Quarta, information herein, Trend Micro makes no warranties or representations of any kind as to Stefano Zanero its accuracy, currency, or completeness. You agree that access to and use of and reliance Politecnico di Milano on this document and the content thereof is at your own risk. -

Spacecraft American Aerospace Controls
Spacecraft For More Than 50 Years, Our Experience Is Your Assurance™ AAC Manufactures high-reliability voltage and current sensors for: Satellites UAVs Commercial Aircraft Missiles Underwater Vehicles Military Aircraft Launch Systems Armored Vehicles Ships Helicopters Industrial Equipment Rail AAC is a Woman-Owned Business and all parts are manufactured at AAC’s Farmingdale, NY location. American Aerospace Controls 570 Smith Street, Farmingdale NY 11735 Phone: +1 (631) 694-5100 – Fax: +1 (631) 694-6739 http://a-a-c.com ©American Aerospace Controls 10-2016 Aircraft-UAVs Rail AAC Quality and Engineering Industrial Defense For More Than 50 Years, Our Experience is Your Assurance™ AAC Engineering and Quality Depart- Since 1965, American Aerospace Controls has been manufacturing high reliability ments are here to work with you on the AC & DC current, voltage and frequency sensors, transducers and detectors. With design and qualification of your parts. an emphasis on engineering solutions and customer support, AAC has developed Our vast experience in space flight app- long-term relationships with some of the largest aerospace, defense, transit and industrial companies around the globe. lications allows us to offer insight into the design and requirements of each unique Space Application. AAC main- AAC in Space tains the highest standards in Quality and Production. AAC sensors have been used on numerous manned and unmanned spacecraft, satellite, rocket and Unmanned Aerial Vehicle (UAV) programs. AAC has been involved with space flight applications since the mid-1960s. AAC’s extensive From the Mercury Program in the 1960’s to today’s international commercial and knowledge and decades of experience in designing and manufacturing defense satellite systems, AAC engineers have helped design current and voltage transducers and detectors capable of providing high reliability in harsh remote detectors and transducers that are the best available. -

Web Application Vulnerabilities and Insecure Software Root Causes: the OWASP Top 10
Vulnerability Analysis, Secure Development and Risk Management of Web 2.0 Applications Marco Morana OWASP OWASP Cincinnati Chapter, November 2010 Meeting Copyright © 2010 - The OWASP Foundation Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License. The OWASP Foundation http://www.owasp.org What is OWASP? OWASP 2 Agenda For Today’s Presentation 1. The Evolution of Web 2.0 2. Web 2.0 Vulnerability Analysis 3. Building Secure Web 2.0 Applications 4. Web 2.0 Risk Management OWASP 3 The Evolution of the Internet to Web 2.0 OWASP 4 General Web 2.0 Background Can be defined as: “Web applications that facilitate interactive information sharing and collaboration, interoperability, and user-centered design on the World Wide Web” … the main characteristics of web 2.0 are: 1. Encourage user’s participation and collaboration through a virtual community of social networks/sites. Users can and add and update their own content, examples include Twitter and social networks such as Facebook, Myspace, LinkedIn, YouTube 2. Transcend from the technology/frameworks used AJAX, Adobe AIR, Flash, Flex, Dojo, Google Gears and others 3. Combine and aggregate data and functionality from different applications and systems, example include “mashups” as aggregators of client functionality provided by different in-house developed and/or third party services (e.g. web services, SaaS) OWASP 5 Web 2.0 As Evolution of Human Knowledge Source http://digigogy.blogspot.com/2009/02/digital-blooms-visual.html -

From Secure Coding to Secure Software
From Secure Coding to Secure Software Table of Contents From Secure Coding to Secure Software ........................................................................................ 4 Why Software Security? .................................................................................................................. 6 Software and security failures are rampant ................................................................................... 7 Software and security failures are expensive ................................................................................. 8 Polling Question 2 ........................................................................................................................... 9 Engineering and Development ..................................................................................................... 10 Most Vulnerabilities Are Caused by Programming Errors ............................................................ 11 Secure Software Development ..................................................................................................... 12 Sources of Software Insecurity ..................................................................................................... 13 Polling Question 3 ......................................................................................................................... 15 Coding rules – 2016 Edition .......................................................................................................... 17 CWE Guidance .............................................................................................................................. -

Aerospace Manufacturing a Growth Leader in Georgia
Aerospace Manufacturing A Growth Leader in Georgia In this study: 9. Research Universities 10. GTRI and GTMI 1. Industry Snapshot 11. High-Tech Talent 3. A Top Growth Leader 12. Centers of Innovation 4. Industry Mix 13. World-Class Training Programs 6. Industry Wages and Occupational 15. Strong Partnerships and Ready Workforce Employment 16. Transportation Infrastructure 7. Pro-Business State 17. Powering Your Manufacturing Facility Community and Economic Development 8. Unionization 18. Aerospace Companies Aerospace Manufacturing A Growth Leader in Georgia Aerospace is defined as Aerospace Products and Parts Manufacturing as well as Other Support Activities for Air Transportation. Aerospace Georgia is the ideal home for aerospace include Pratt & Whitney’s expansion in companies with ¨¦§75 ¨¦§575 25+ employees companies. With the world’s most traveled Columbus in both 2016 and 2017, Meggitt «¬400 ¨¦§85 ¨¦§985 airport, eight regional airports, prominent Polymers & Composites’ expansion in military bases and accessibility to the Rockmart and MSB Group’s location in ¨¦§20 ¨¦§20 country’s fastest-growing major port, Savannah. For a complete list of new major ¨¦§85 Georgia’s aerospace industry serves a locations and expansions, see page 2. ¨¦§185 global marketplace. Georgia is also home to a highly-skilled workforce and world- ¨¦§16 Why Georgia for Aerospace? class technical expertise geared toward promoting the success of the aerospace • Highly skilled workers ¨¦§75 ¨¦§95 industry. Georgia’s business climate is • World-class technical expertise consistently ranked as one of the best • Renowned workforce training program in the country, with a business-friendly tax code and incentives that encourage • Increasing number of defense manufacturing growth for existing and personnel newly arriving companies. -

Vulnerabilities, Threats, and Secure Coding Practices
Vulnerabilities, Threats, and Secure Coding Practices Barton P. Miller Elisa Heymann Computer Sciences Department Computer Sciences Department University of Wisconsin University of Wisconsin [email protected] & Universitat Autònoma de Barcelona [email protected] NSF CyberSecurity Summit 2015 Arlington, August 17 2015 1 What do we do • Assess Middleware: Make cloud/grid software more secure • Train: We teach tutorials for users, developers, sys admins, and managers • Research: Make in-depth assessments more automated and improve quality of automated code analysis http://www.cs.wisc.edu/mist/papers/VAshort.pdf 2 Our History 2001: “Playing Inside the Black Box” paper, first demonstration of hijacking processes in the Cloud. 2004: First formal funding from US NSF. 2004: First assessment activity, based on Condor, and started development of our methodology (FPVA). 2006: Start of joint effort between UW and UAB. 2006: Taught first tutorial at San Diego Supercomputer Center. 2007: First NATO funding, jointly to UAB, UW, and Ben Gurion University. 2008: First authoritative study of automated code analysis tools. 2009: Published detailed report on our FPVA methodology. 2009: U.S. Dept. of Homeland Security funding support. 2012: DHS Software Assurance Marketplace (SWAMP) research center. 3 Our experience includes Condor, University of Wisconsin Batch queuing workload management system 15 vulnerabilities 600 KLOC of C and C++ Google Chrome, Google Web browser 1 vulnerability 2396 KLOC of C and C++ MyProxy, NCSA Credential Management System 5 vulnerabilities -

Micro-Jet Test Facility for Aerospace Propulsión Engineering Education*
Micro-Jet Test Facility for Aerospace Propulsión Engineering Education* G. L. JUSTE, J. L. MONTAÑÉS and A. VELAZQUEZ Universidad Politécnica de Madrid, School of Aeronautics, Aerospace Propulsión and Fluid Mechanics Department, Plaza del Cardenal Cisneros 3, 28040 Madrid, Spain. E-mail: [email protected] This paper describes the methodology that has been developed and implemented at the School of Aeronautics (ETSIA) of the Universidad Politécnica de Madrid (UPM) to familiarize aerospace engineering students with the operation ofreal complexjet engine systems. This methodology has a two-pronged approach: students carry out preparatory work by using, first, a gas turbine performance prediction numerical code; then they valídate their assumptions and results on an experimental test rig. When looking at the educational aspects, we have taken care that, apartfrom being sufficiently robust and flexible, the experimental set-up is similar to real jet engine rigs, so the students are not constrained to exploring a much too limited parametric space. Also, because a facility like this is usually subject to extensive and somewhat rugged use, we have focused on a low cosí design. Keywords: micro-jet engine test facility; aerospace propulsión INTRODUCTION should be considered: (1) a comprehensive under standing of these systems is based on acquiring AEROSPACE ENGINEERING EDUCATION theoretical, computational and experimental test in Europe is undergoing a significant change for knowledge, and (2) the cost of a jet engine experi two reasons: (1) the aerospace industry, which mental facility is too high for many public univer- used to be a mostly national concern, is now sities, not to mention the environmental aspects consolidating at the continental level, and (2) a associated with the fact that some of these institu- common frame of engineering education is devel- tions, like ours, are located in downtown áreas. -

Software Analysis for Security
Software Analysis for Security Spiros Mancoridis Department of Computer Science College of Engineering Drexel University Philadelphia, PA 19147, USA E-mail: [email protected] Abstract ware architecture to assure the system’s security. The qual- ity of a security architecture, however, also depends on the This is a survey of the processes, practices, and technolo- security of the applications that constitute the system. In gies that can help software maintenance engineers improve low security operating environments, such as most commer- the security of software systems. A particular emphasis is cial operating systems, it is assumed, albeit optimistically, placed on validating security architectures, verifying that that these applications are trustworthy. Therefore, it is im- the implementation of an architecture’s constituent appli- portant to articulate the practices to support the secure cod- cations adhere to secure coding practices, and protecting ing of applications and the tools for detecting malware. Se- software systems against malicious software. In addition to cure coding involves programming practices and run-time surveying the state-of-the-art, research challenges pertain- mechanisms that can be used to limit the vulnerabilityof ap- ing to software security are posed to the software mainte- plications to dangerous malware that exploit, for example, nance research community. buffer overflows, format string vulnerabilities, and integer vulnerabilities to attack computer systems. One approach to software security is to verify that (a) the security mechanisms used are trustworthy; (b) the security 1. Introduction architecture has been validated against the security policy; and (c) the software applications that constitute the system The goal of computer security is to protect computer as- are trustworthy (e.g., they have been developed using secure sets (e.g., servers, applications, web pages, data) from cor- coding practices, or they are not malware). -

Security Training for Developers
Security Training for Developers Trusted Advisor for All Your Information Security Needs ® ZERODAYLAB Increasing Cyber Resilience by Coding with the Hacker in Mind Our Security Training for Developers has a simple objective, educating software engineers to reinforce security best practice when developing software to reduce the accidental introduction of security vulnerabilities. By training your development team in the latest secure coding practices, you can bring your overall security costs down by: Reducing the number of incidents Conducting fewer penetration tests and re-tests as fewer vulnerabilities are found Changing the way developers think and increasing their ability to identify other risks Following best practice so that code has fewer bugs overall Using tried-and-tested methods to reduce the need for further corrective coding further down the line and resulting in a faster development cycle. Specialists in Face-to-Face Security Training ZeroDayLab delivers security training courses across the world for staff and management at all levels of an organisation, with or without technical knowledge. Drawn from a wealth of experience from the security projects we deliver for clients every day, we specialise in intensive, face-to-face training with specialist content designed to address the issues your organisation faces. ® ZERODAYLAB Security Training for Developers Security Training for Developers is a comprehensive, on-site training programme based around the 2017 OWASP Top 10. This two-day course will assess, educate and re-test to raise your software engineers’ information security knowledge. As a result, they will develop code with fewer vulnerabilities, expand their knowledge of current threats and tactics and learn hacking techniques. -

A Case Study of Evolvability and Excess on the B-52 Stratofortress and F/A-18 Hornet
ASME 2017 International Design Engineering Technical Conferences and Computers and Information in Engineering Conference IDETC 2017 August 6-9, 2017, Cleveland, Ohio IDETC2017-67886 A CASE STUDY OF EVOLVABILITY AND EXCESS ON THE B-52 STRATOFORTRESS AND F/A-18 HORNET Daniel Long Dr. Scott Ferguson1 Graduate Research Assistant Associate Professor North Carolina State University North Carolina State University Raleigh, NC, USA Raleigh, NC, USA [email protected] [email protected] ABSTRACT operate for 60 years, yet there is speculation that they The moment a system is put into service it begins to lose value ultimately could operate for eighty to one hundred years [2]. as technological and societal changes accrue while the system The total cost of building a replacement unit in 2009 was is frozen in the state it was constructed. System decision estimated at $7 billion per unit excluding transmission [3], makers are faced with the choice of accepting a decline in which was a nontrivial fraction of the then $53.5 billion market performance, updating the design, or retiring the system. Each cap for Duke Energy, the largest utility in the US [4]. time a decision maker faces these alternatives, the value of the A variety of methods for increasing CES lifecycle value available options must be evaluated to determine the preferred have been explored in literature. Design for: adaptability [5], course of action. A design that can adapt to changes with flexibility [6,7], changeability [8,9], and reconfigurability [10] minimal cost should provide more value over a longer period all provide system designers with heuristics and tools to design than a system that is initially less costly, but less adaptable.