Secure Coding Frameworks for the Development of Safe, Secure and Reliable Code
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Vulnerability Assessment and Secure Coding Practices for Middleware Part 1
Vulnerability Assessment and Secure Coding Practices for Middleware Part 1 James A. Kupsch Computer Sciences Department University of Wisconsin © 2007-2008, James A. K1upsch. All rights reserved. Tutorial Objectives • Show how to perform the basics of a vulnerability assessment • Create more people doing vulnerability assessments • Show how different types of vulnerabilities arise in a system • Teach coding techniques that can prevent certain types of vulnerabilities • Make your software more secure 2 Roadmap • Part 1: Vulnerability Assessment Process – Introduction – Evaluation process – Architectural analysis – Computer process – Communication channels – Resource analysis – Privilege analysis – Data Flow Diagrams – Component analysis – Vulnerability Discovery Activities • Part 2: Secure Coding Practices 3 Security Problems Are Real Everyone with a computer knows this. If you’re not seeing vulnerability reports and fixes for a piece of software, it doesn’t mean that it is secure. It probably means the opposite; they aren’t looking or aren’t telling. The grid community has been largely lucky (security through obscurity). 4 Many Avenues of Attack We’re looking for attacks that exploit inherent weakness in your system. Internet Firewall: www server Attack web using www protocols Compromised host Internal bad guy 5 Impact of Vulnerabilities FBI estimates computer security incidents cost U.S. businesses $67 billion in 2005 [CNETnews.com] Number of reported vulnerabilities each year is increasing [CERT stats] 8000 6000 4000 2000 0 1994 1998 -

Understanding Integer Overflow in C/C++
Appeared in Proceedings of the 34th International Conference on Software Engineering (ICSE), Zurich, Switzerland, June 2012. Understanding Integer Overflow in C/C++ Will Dietz,∗ Peng Li,y John Regehr,y and Vikram Adve∗ ∗Department of Computer Science University of Illinois at Urbana-Champaign fwdietz2,[email protected] ySchool of Computing University of Utah fpeterlee,[email protected] Abstract—Integer overflow bugs in C and C++ programs Detecting integer overflows is relatively straightforward are difficult to track down and may lead to fatal errors or by using a modified compiler to insert runtime checks. exploitable vulnerabilities. Although a number of tools for However, reliable detection of overflow errors is surprisingly finding these bugs exist, the situation is complicated because not all overflows are bugs. Better tools need to be constructed— difficult because overflow behaviors are not always bugs. but a thorough understanding of the issues behind these errors The low-level nature of C and C++ means that bit- and does not yet exist. We developed IOC, a dynamic checking tool byte-level manipulation of objects is commonplace; the line for integer overflows, and used it to conduct the first detailed between mathematical and bit-level operations can often be empirical study of the prevalence and patterns of occurrence quite blurry. Wraparound behavior using unsigned integers of integer overflows in C and C++ code. Our results show that intentional uses of wraparound behaviors are more common is legal and well-defined, and there are code idioms that than is widely believed; for example, there are over 200 deliberately use it. -

Rogue Automation: Vulnerable and Malicious Code in Industrial
In partnership with Rogue Automation Vulnerable and Malicious Code in Industrial Programming Federico Maggi Marcello Pogliani Trend Micro Research Politecnico di Milano Rogue Automation Vulnerable and Malicious Code in Industrial Programming Published by TREND MICRO LEGAL DISCLAIMER Trend Micro Research The information provided herein is for general information and educational purposes only. It is not intended and should not be construed to constitute legal advice. The information contained herein may not be applicable to all situations and may not reflect the most Written by current situation. Nothing contained herein should be relied on or acted upon without the benefit of legal advice based on the particular facts and circumstances presented and Federico Maggi nothing herein should be construed otherwise. Trend Micro reserves the right to modify Trend Micro Research the contents of this document at any time without prior notice. Marcello Pogliani Translations of any material into other languages are intended solely as a convenience. Politecnico di Milano Translation accuracy is not guaranteed nor implied. If any questions arise related to the accuracy of a translation, please refer to the original language official version of the document. Any discrepancies or differences created in the translation are not binding and With contributions from have no legal effect for compliance or enforcement purposes. Martino Vittone, Although Trend Micro uses reasonable efforts to include accurate and up-to-date Davide Quarta, information herein, Trend Micro makes no warranties or representations of any kind as to Stefano Zanero its accuracy, currency, or completeness. You agree that access to and use of and reliance Politecnico di Milano on this document and the content thereof is at your own risk. -

Collecting Vulnerable Source Code from Open-Source Repositories for Dataset Generation
applied sciences Article Collecting Vulnerable Source Code from Open-Source Repositories for Dataset Generation Razvan Raducu * , Gonzalo Esteban , Francisco J. Rodríguez Lera and Camino Fernández Grupo de Robótica, Universidad de León. Avenida Jesuitas, s/n, 24007 León, Spain; [email protected] (G.E.); [email protected] (F.J.R.L.); [email protected] (C.F.) * Correspondence: [email protected] Received:29 December 2019; Accepted: 7 February 2020; Published: 13 February 2020 Abstract: Different Machine Learning techniques to detect software vulnerabilities have emerged in scientific and industrial scenarios. Different actors in these scenarios aim to develop algorithms for predicting security threats without requiring human intervention. However, these algorithms require data-driven engines based on the processing of huge amounts of data, known as datasets. This paper introduces the SonarCloud Vulnerable Code Prospector for C (SVCP4C). This tool aims to collect vulnerable source code from open source repositories linked to SonarCloud, an online tool that performs static analysis and tags the potentially vulnerable code. The tool provides a set of tagged files suitable for extracting features and creating training datasets for Machine Learning algorithms. This study presents a descriptive analysis of these files and overviews current status of C vulnerabilities, specifically buffer overflow, in the reviewed public repositories. Keywords: vulnerability; sonarcloud; bot; source code; repository; buffer overflow 1. Introduction In November 1988 the Internet suffered what is publicly known as “the first successful buffer overflow exploitation”. The exploit took advantage of the absence of buffer range-checking in one of the functions implemented in the fingerd daemon [1,2]. Even though it is considered to be the first exploited buffer overflow, different researchers had been working on buffer overflow for years. -

Web Application Vulnerabilities and Insecure Software Root Causes: the OWASP Top 10
Vulnerability Analysis, Secure Development and Risk Management of Web 2.0 Applications Marco Morana OWASP OWASP Cincinnati Chapter, November 2010 Meeting Copyright © 2010 - The OWASP Foundation Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License. The OWASP Foundation http://www.owasp.org What is OWASP? OWASP 2 Agenda For Today’s Presentation 1. The Evolution of Web 2.0 2. Web 2.0 Vulnerability Analysis 3. Building Secure Web 2.0 Applications 4. Web 2.0 Risk Management OWASP 3 The Evolution of the Internet to Web 2.0 OWASP 4 General Web 2.0 Background Can be defined as: “Web applications that facilitate interactive information sharing and collaboration, interoperability, and user-centered design on the World Wide Web” … the main characteristics of web 2.0 are: 1. Encourage user’s participation and collaboration through a virtual community of social networks/sites. Users can and add and update their own content, examples include Twitter and social networks such as Facebook, Myspace, LinkedIn, YouTube 2. Transcend from the technology/frameworks used AJAX, Adobe AIR, Flash, Flex, Dojo, Google Gears and others 3. Combine and aggregate data and functionality from different applications and systems, example include “mashups” as aggregators of client functionality provided by different in-house developed and/or third party services (e.g. web services, SaaS) OWASP 5 Web 2.0 As Evolution of Human Knowledge Source http://digigogy.blogspot.com/2009/02/digital-blooms-visual.html -

From Secure Coding to Secure Software
From Secure Coding to Secure Software Table of Contents From Secure Coding to Secure Software ........................................................................................ 4 Why Software Security? .................................................................................................................. 6 Software and security failures are rampant ................................................................................... 7 Software and security failures are expensive ................................................................................. 8 Polling Question 2 ........................................................................................................................... 9 Engineering and Development ..................................................................................................... 10 Most Vulnerabilities Are Caused by Programming Errors ............................................................ 11 Secure Software Development ..................................................................................................... 12 Sources of Software Insecurity ..................................................................................................... 13 Polling Question 3 ......................................................................................................................... 15 Coding rules – 2016 Edition .......................................................................................................... 17 CWE Guidance .............................................................................................................................. -

RICH: Automatically Protecting Against Integer-Based Vulnerabilities
RICH: Automatically Protecting Against Integer-Based Vulnerabilities David Brumley, Tzi-cker Chiueh, Robert Johnson [email protected], [email protected], [email protected] Huijia Lin, Dawn Song [email protected], [email protected] Abstract against integer-based attacks. Integer bugs appear because programmers do not antici- We present the design and implementation of RICH pate the semantics of C operations. The C99 standard [16] (Run-time Integer CHecking), a tool for efficiently detecting defines about a dozen rules governinghow integer types can integer-based attacks against C programs at run time. C be cast or promoted. The standard allows several common integer bugs, a popular avenue of attack and frequent pro- cases, such as many types of down-casting, to be compiler- gramming error [1–15], occur when a variable value goes implementation specific. In addition, the written rules are out of the range of the machine word used to materialize it, not accompanied by an unambiguous set of formal rules, e.g. when assigning a large 32-bit int to a 16-bit short. making it difficult for a programmer to verify that he un- We show that safe and unsafe integer operations in C can derstands C99 correctly. Integer bugs are not exclusive to be captured by well-known sub-typing theory. The RICH C. Similar languages such as C++, and even type-safe lan- compiler extension compiles C programs to object code that guages such as Java and OCaml, do not raise exceptions on monitors its own execution to detect integer-based attacks. -

Vulnerabilities, Threats, and Secure Coding Practices
Vulnerabilities, Threats, and Secure Coding Practices Barton P. Miller Elisa Heymann Computer Sciences Department Computer Sciences Department University of Wisconsin University of Wisconsin [email protected] & Universitat Autònoma de Barcelona [email protected] NSF CyberSecurity Summit 2015 Arlington, August 17 2015 1 What do we do • Assess Middleware: Make cloud/grid software more secure • Train: We teach tutorials for users, developers, sys admins, and managers • Research: Make in-depth assessments more automated and improve quality of automated code analysis http://www.cs.wisc.edu/mist/papers/VAshort.pdf 2 Our History 2001: “Playing Inside the Black Box” paper, first demonstration of hijacking processes in the Cloud. 2004: First formal funding from US NSF. 2004: First assessment activity, based on Condor, and started development of our methodology (FPVA). 2006: Start of joint effort between UW and UAB. 2006: Taught first tutorial at San Diego Supercomputer Center. 2007: First NATO funding, jointly to UAB, UW, and Ben Gurion University. 2008: First authoritative study of automated code analysis tools. 2009: Published detailed report on our FPVA methodology. 2009: U.S. Dept. of Homeland Security funding support. 2012: DHS Software Assurance Marketplace (SWAMP) research center. 3 Our experience includes Condor, University of Wisconsin Batch queuing workload management system 15 vulnerabilities 600 KLOC of C and C++ Google Chrome, Google Web browser 1 vulnerability 2396 KLOC of C and C++ MyProxy, NCSA Credential Management System 5 vulnerabilities -

Software Analysis for Security
Software Analysis for Security Spiros Mancoridis Department of Computer Science College of Engineering Drexel University Philadelphia, PA 19147, USA E-mail: [email protected] Abstract ware architecture to assure the system’s security. The qual- ity of a security architecture, however, also depends on the This is a survey of the processes, practices, and technolo- security of the applications that constitute the system. In gies that can help software maintenance engineers improve low security operating environments, such as most commer- the security of software systems. A particular emphasis is cial operating systems, it is assumed, albeit optimistically, placed on validating security architectures, verifying that that these applications are trustworthy. Therefore, it is im- the implementation of an architecture’s constituent appli- portant to articulate the practices to support the secure cod- cations adhere to secure coding practices, and protecting ing of applications and the tools for detecting malware. Se- software systems against malicious software. In addition to cure coding involves programming practices and run-time surveying the state-of-the-art, research challenges pertain- mechanisms that can be used to limit the vulnerabilityof ap- ing to software security are posed to the software mainte- plications to dangerous malware that exploit, for example, nance research community. buffer overflows, format string vulnerabilities, and integer vulnerabilities to attack computer systems. One approach to software security is to verify that (a) the security mechanisms used are trustworthy; (b) the security 1. Introduction architecture has been validated against the security policy; and (c) the software applications that constitute the system The goal of computer security is to protect computer as- are trustworthy (e.g., they have been developed using secure sets (e.g., servers, applications, web pages, data) from cor- coding practices, or they are not malware). -

Security Training for Developers
Security Training for Developers Trusted Advisor for All Your Information Security Needs ® ZERODAYLAB Increasing Cyber Resilience by Coding with the Hacker in Mind Our Security Training for Developers has a simple objective, educating software engineers to reinforce security best practice when developing software to reduce the accidental introduction of security vulnerabilities. By training your development team in the latest secure coding practices, you can bring your overall security costs down by: Reducing the number of incidents Conducting fewer penetration tests and re-tests as fewer vulnerabilities are found Changing the way developers think and increasing their ability to identify other risks Following best practice so that code has fewer bugs overall Using tried-and-tested methods to reduce the need for further corrective coding further down the line and resulting in a faster development cycle. Specialists in Face-to-Face Security Training ZeroDayLab delivers security training courses across the world for staff and management at all levels of an organisation, with or without technical knowledge. Drawn from a wealth of experience from the security projects we deliver for clients every day, we specialise in intensive, face-to-face training with specialist content designed to address the issues your organisation faces. ® ZERODAYLAB Security Training for Developers Security Training for Developers is a comprehensive, on-site training programme based around the 2017 OWASP Top 10. This two-day course will assess, educate and re-test to raise your software engineers’ information security knowledge. As a result, they will develop code with fewer vulnerabilities, expand their knowledge of current threats and tactics and learn hacking techniques. -

Integer Overflow
Lecture 05 – Integer overflow Stephen Checkoway University of Illinois at Chicago Unsafe functions in libc • strcpy • strcat • gets • scanf family (fscanf, sscanf, etc.) (rare) • printf family (more about these later) • memcpy (need to control two of the three parameters) • memmove (same as memcpy) Replacements • Not actually safe; doesn’t do what you think • strncpy • strncat • Available on Windows in C11 Annex K (the optional part of C11) • strcpy_s • strcat_s • BSD-derived, moderately widely available, including Linux kernel but not glibc • strlcpy • strlcat Buffer overflow vulnerability-finding strategy 1. Look for the use of unsafe functions 2. Trace attacker-controlled input to these functions Real-world examples from my own research • Voting machine: SeQuoia AVC Advantage • About a dozen uses of strcpy, most checked the length first • One did not. It appeared in infreQuently used code • Configuration file with fixed-width fields containing NUL-terminated strings, one of which was strcpy’d to the stack • Remote compromise of cars • Lots of strcpy of attacker-controlled Bluetooth data, first one examined was vulnerable • memcpy of attacker-controlled data from cellular modem Reminder: Think like an attacker • I skimmed some source code for a client/server protocol • The server code was full of trivial buffer overflows resulting from the attacker not following the protocol • I told the developer about the issue, but he wasn’t concerned because the client software he wrote wouldn’t send too much data • Most people don’t think like attackers. Three flavors of integer overflows 1. Truncation: Assigning larger types to smaller types int i = 0x12345678; short s = i; char c = i; Truncation example struct s { int main(int argc, char *argv[]) { unsigned short len; size_t len = strlen(argv[0]); char buf[]; }; struct s *p = malloc(len + 3); p->len = len; void foo(struct s *p) { strcpy(p->buf, argv[0]); char buffer[100]; if (p->len < sizeof buffer) foo(p); strcpy(buffer, p->buf); return 0; // Use buffer } } Three flavors of integer overflows 2. -
Practical Integer Overflow Prevention
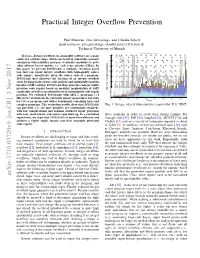
Practical Integer Overflow Prevention Paul Muntean, Jens Grossklags, and Claudia Eckert {paul.muntean, jens.grossklags, claudia.eckert}@in.tum.de Technical University of Munich Memory error vulnerabilities categorized 160 Abstract—Integer overflows in commodity software are a main Other Format source for software bugs, which can result in exploitable memory Pointer 140 Integer Heap corruption vulnerabilities and may eventually contribute to pow- Stack erful software based exploits, i.e., code reuse attacks (CRAs). In 120 this paper, we present INTGUARD, a symbolic execution based tool that can repair integer overflows with high-quality source 100 code repairs. Specifically, given the source code of a program, 80 INTGUARD first discovers the location of an integer overflow error by using static source code analysis and satisfiability modulo 60 theories (SMT) solving. INTGUARD then generates integer multi- precision code repairs based on modular manipulation of SMT 40 Number of VulnerabilitiesNumber of constraints as well as an extensible set of customizable code repair 20 patterns. We evaluated INTGUARD with 2052 C programs (≈1 0 Mil. LOC) available in the currently largest open-source test suite 2000 2002 2004 2006 2008 2010 2012 2014 2016 for C/C++ programs and with a benchmark containing large and Year complex programs. The evaluation results show that INTGUARD Fig. 1: Integer related vulnerabilities reported by U.S. NIST. can precisely (i.e., no false positives are accidentally repaired), with low computational and runtime overhead repair programs with very small binary and source code blow-up. In a controlled flows statically in order to avoid them during runtime. For experiment, we show that INTGUARD is more time-effective and example, Sift [35], TAP [56], SoupInt [63], AIC/CIT [74], and achieves a higher repair success rate than manually generated CIntFix [11] rely on a variety of techniques depicted in detail code repairs.