Security 101
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
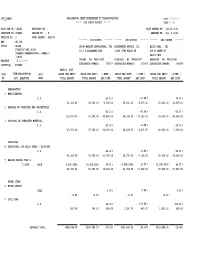
Bid Check Report * * * Time: 14:04
DOT_RGGB01 WASHINGTON STATE DEPARTMENT OF TRANSPORTATION DATE: 05/28/2013 * * * BID CHECK REPORT * * * TIME: 14:04 PS &E JOB NO : 11W101 REVISION NO : BIDS OPENED ON : Jun 26 2013 CONTRACT NO : 008498 REGION NO : 9 AWARDED ON : Jul 1 2013 VERSION NO : 2 WORK ORDER# : XL4078 ------- LOW BIDDER ------- ------- 2ND BIDDER ------- ------- 3RD BIDDER ------- HWY : SR 104 TITLE : SR104 ORION MARINE CONTRACTORS, INC. BLACKWATER MARINE, LLC QUIGG BROS., INC. KINGSTON TML SLIPS 1112 E ALEXANDER AVE 12019 76TH PLACE NE 819 W STATE ST DOLPHIN PRESERVATION - PHASE 4 98520-5934 11W101 PROJECT : NH-2013(079) TACOMA WA 984214102 KIRKLAND WA 980342437 ABERDEEN WA 985200281 COUNTY(S) : KITSAP CONTRACTOR NUMBER : 100767 CONTRACTOR NUMBER : 100874 CONTRACTOR NUMBER : 680000 ENGR'S. EST. ITEM ITEM DESCRIPTION UNIT PRICE PER UNIT/ PRICE PER UNIT/ % DIFF./ PRICE PER UNIT/ % DIFF./ PRICE PER UNIT/ % DIFF./ NO. EST. QUANTITY MEAS TOTAL AMOUNT TOTAL AMOUNT AMT.DIFF. TOTAL AMOUNT AMT.DIFF. TOTAL AMOUNT AMT.DIFF. PREPARATION 1 MOBILIZATION L.S. -25.20 % -25.48 % 40.00 % 25,000.00 18,700.00 -6,300.00 18,630.00 -6,370.00 35,000.00 10,000.00 2 REMOVAL OF STRUCTURE AND OBSTRUCTION L.S. -56.10 % -65.08 % -56.71 % 115,500.00 50,700.00 -64,800.00 40,338.00 -75,162.00 50,000.00 -65,500.00 3 DISPOSAL OF CREOSOTED MATERIAL L.S. -21.05 % -8.99 % -15.79 % 47,500.00 37,500.00 -10,000.00 43,228.35 -4,271.65 40,000.00 -7,500.00 STRUCTURE 4 STRUCTURAL LOW ALLOY STEEL - DOLPHINS L.S. -

Humidity Definitions
ROTRONIC TECHNICAL NOTE Humidity Definitions 1 Relative humidity Table of Contents Relative humidity is the ratio of two pressures: %RH = 100 x p/ps where p is 1 Relative humidity the actual partial pressure of the water vapor present in the ambient and ps 2 Dew point / Frost the saturation pressure of water at the temperature of the ambient. point temperature Relative humidity sensors are usually calibrated at normal room temper - 3 Wet bulb ature (above freezing). Consequently, it generally accepted that this type of sensor indicates relative humidity with respect to water at all temperatures temperature (including below freezing). 4 Vapor concentration Ice produces a lower vapor pressure than liquid water. Therefore, when 5 Specific humidity ice is present, saturation occurs at a relative humidity of less than 100 %. 6 Enthalpy For instance, a humidity reading of 75 %RH at a temperature of -30°C corre - 7 Mixing ratio sponds to saturation above ice. by weight 2 Dew point / Frost point temperature The dew point temperature of moist air at the temperature T, pressure P b and mixing ratio r is the temperature to which air must be cooled in order to be saturated with respect to water (liquid). The frost point temperature of moist air at temperature T, pressure P b and mixing ratio r is the temperature to which air must be cooled in order to be saturated with respect to ice. Magnus Formula for dew point (over water): Td = (243.12 x ln (pw/611.2)) / (17.62 - ln (pw/611.2)) Frost point (over ice): Tf = (272.62 x ln (pi/611.2)) / (22.46 - -

Chapter 19 RECOVERING DIGITAL EVIDENCE from LINUX SYSTEMS
Chapter 19 RECOVERING DIGITAL EVIDENCE FROM LINUX SYSTEMS Philip Craiger Abstract As Linux-kernel-based operating systems proliferate there will be an in evitable increase in Linux systems that law enforcement agents must process in criminal investigations. The skills and expertise required to recover evidence from Microsoft-Windows-based systems do not neces sarily translate to Linux systems. This paper discusses digital forensic procedures for recovering evidence from Linux systems. In particular, it presents methods for identifying and recovering deleted files from disk and volatile memory, identifying notable and Trojan files, finding hidden files, and finding files with renamed extensions. All the procedures are accomplished using Linux command line utilities and require no special or commercial tools. Keywords: Digital evidence, Linux system forensics !• Introduction Linux systems will be increasingly encountered at crime scenes as Linux increases in popularity, particularly as the OS of choice for servers. The skills and expertise required to recover evidence from a Microsoft- Windows-based system, however, do not necessarily translate to the same tasks on a Linux system. For instance, the Microsoft NTFS, FAT, and Linux EXT2/3 file systems work differently enough that under standing one tells httle about how the other functions. In this paper we demonstrate digital forensics procedures for Linux systems using Linux command line utilities. The ability to gather evidence from a running system is particularly important as evidence in RAM may be lost if a forensics first responder does not prioritize the collection of live evidence. The forensic procedures discussed include methods for identifying and recovering deleted files from RAM and magnetic media, identifying no- 234 ADVANCES IN DIGITAL FORENSICS tables files and Trojans, and finding hidden files and renamed files (files with renamed extensions. -

System Planner
System Planner ACE3600 RTU ab 6802979C45-D Draft 2 Copyright © 2009 Motorola All Rights Reserved March 2009 DISCLAIMER NOTE The information within this document has been carefully checked and is believed to be entirely reliable. However, no responsibility is assumed for any inaccuracies. Furthermore Motorola reserves the right to make changes to any product herein to improve reliability, function, or design. Motorola does not assume any liability arising out of the application or use of any product, recommendation, or circuit described herein; neither does it convey any license under its patent or right of others. All information resident in this document is considered copyrighted. COMPUTER SOFTWARE COPYRIGHTS The Motorola products described in this Product Planner include copyrighted Motorola software stored in semiconductor memories and other media. Laws in the United States and foreign countries preserve for Motorola certain exclusive rights for copyrighted computer programs, including the exclusive right to copy or reproduce in any form the copyrighted computer program. Accordingly, any copyrighted Motorola computer programs contained in Motorola products described in this Product Planner may not be copied or reproduced in any manner without written permission from Motorola, Inc. Furthermore, the purchase of Motorola products shall not be deemed to grant either directly or by implication, estoppel, or otherwise, any license under the copyright, patents, or patent applications of Motorola, except for the normal non-exclusive, royalty free license to use that arises by operation in law of the sale of a product. TRADEMARKS MOTOROLA and the Stylized M Logo are registered in the U.S. Patent and Trademark Office. -

PS TEXT EDIT Reference Manual Is Designed to Give You a Complete Is About Overview of TEDIT
Information Management Technology Library PS TEXT EDIT™ Reference Manual Abstract This manual describes PS TEXT EDIT, a multi-screen block mode text editor. It provides a complete overview of the product and instructions for using each command. Part Number 058059 Tandem Computers Incorporated Document History Edition Part Number Product Version OS Version Date First Edition 82550 A00 TEDIT B20 GUARDIAN 90 B20 October 1985 (Preliminary) Second Edition 82550 B00 TEDIT B30 GUARDIAN 90 B30 April 1986 Update 1 82242 TEDIT C00 GUARDIAN 90 C00 November 1987 Third Edition 058059 TEDIT C00 GUARDIAN 90 C00 July 1991 Note The second edition of this manual was reformatted in July 1991; no changes were made to the manual’s content at that time. New editions incorporate any updates issued since the previous edition. Copyright All rights reserved. No part of this document may be reproduced in any form, including photocopying or translation to another language, without the prior written consent of Tandem Computers Incorporated. Copyright 1991 Tandem Computers Incorporated. Contents What This Book Is About xvii Who Should Use This Book xvii How to Use This Book xvii Where to Go for More Information xix What’s New in This Update xx Section 1 Introduction to TEDIT What Is PS TEXT EDIT? 1-1 TEDIT Features 1-1 TEDIT Commands 1-2 Using TEDIT Commands 1-3 Terminals and TEDIT 1-3 Starting TEDIT 1-4 Section 2 TEDIT Topics Overview 2-1 Understanding Syntax 2-2 Note About the Examples in This Book 2-3 BALANCED-EXPRESSION 2-5 CHARACTER 2-9 058059 Tandem Computers -

Unix / Linux Processes Management
UUNNIIXX // LLIINNUUXX -- PPRROOCCEESSSSEESS MMAANNAAGGEEMMEENNTT http://www.tutorialspoint.com/unix/unix-processes.htm Copyright © tutorialspoint.com Advertisements In this chapter, we will discuss in detail about process management in Unix. When you execute a program on your Unix system, the system creates a special environment for that program. This environment contains everything needed for the system to run the program as if no other program were running on the system. Whenever you issue a command in Unix, it creates, or starts, a new process. When you tried out the ls command to list the directory contents, you started a process. A process, in simple terms, is an instance of a running program. The operating system tracks processes through a five-digit ID number known as the pid or the process ID. Each process in the system has a unique pid. Pids eventually repeat because all the possible numbers are used up and the next pid rolls or starts over. At any point of time, no two processes with the same pid exist in the system because it is the pid that Unix uses to track each process. Starting a Process When you start a process (run a command), there are two ways you can run it − Foreground Processes Background Processes Foreground Processes By default, every process that you start runs in the foreground. It gets its input from the keyboard and sends its output to the screen. You can see this happen with the ls command. If you wish to list all the files in your current directory, you can use the following command − $ls ch*.doc This would display all the files, the names of which start with ch and end with .doc − ch01-1.doc ch010.doc ch02.doc ch03-2.doc ch04-1.doc ch040.doc ch05.doc ch06-2.doc ch01-2.doc ch02-1.doc The process runs in the foreground, the output is directed to my screen, and if the ls command wants any input (which it does not), it waits for it from the keyboard. -

Conditioning Flyer
Winter Sports Condi�oning: Girls’ and Boys‘ Basketball, Wrestling, and Sideline Cheer can start condi�oning on October 19th. Exact dates and �mes will be sent out later. The first two weeks will be outdoors with no equipment. Fall Sports Condi�oning: Football, Golf, Cross Country, Volleyball, and Compe��on Cheer can start condi�oning on November 16th. Exact dates and �mes will be sent out later. The first two weeks will be outdoors with no equipment. Must Complete Before Condi�oning: • Must have a physical and the VHSL physical form completed on or a�er May 1st 2020 • Must have complete the Acknowledgement of the Concussion materials • Must have completed the Acknowledgement of Par�cipa�on in the Covid-19 parent mi�ga�on form h�ps://whs.iwcs.k12.va.us/ - this is the link to the WHS web page where the forms can be found. Winter Parent Mee�ng Dates and Zoom Links: • Sideline Cheer - October 12th at 6pm h�ps://us02web.zoom.us/j/89574054101?pwd=djJyMFZSeU9QeFpjdGd6VFB4NkZoQT09 • Wrestling - October 13th at 6pm h�ps://us02web.zoom.us/j/87806116997?pwd=c0RKa1I1NFU1T2ZZbWNUVVZqaG9rdz09 • Girls’ and Boys’ Basketball - October 14th at 6pm h�ps://us02web.zoom.us/j/86956809676?pwd=UWkycEJ2K0pBbW0zNk5tWmE0bkpuUT09 Fall Parent Mee�ng Dates and Zoom Links: • Football - November 9th at 6:00pm h�ps://us02web.zoom.us/j/81813330973?pwd=b0I3REJ0WUZtTUs4Z0o3RDNtNzd3dz09 • Cross Country and Golf - November 10th at 6:00pm h�ps://us02web.zoom.us/j/86072144126?pwd=U0FUb0M2a3dBaENIaDVRYmVBNW1KUT09 • Volleyball - November 12th at 6:00pm h�ps://us02web.zoom.us/j/82413556218?pwd=ZjdZdzZhODNVMHlVSk5kSk5CcjBwQT09 • Compe��on Cheer - November 12th at 7:30pm h�ps://us02web.zoom.us/j/81803664890?pwd=dWVDaHNZS0JTdXdWNlNrZkJoVi92UT09 The parent and student athlete must attend the zoom meeting or watch the recorded zoom session prior to attending conditioning. -

Respiratory Therapy Pocket Reference
Pulmonary Physiology Volume Control Pressure Control Pressure Support Respiratory Therapy “AC” Assist Control; AC-VC, ~CMV (controlled mandatory Measure of static lung compliance. If in AC-VC, perform a.k.a. a.k.a. AC-PC; Assist Control Pressure Control; ~CMV-PC a.k.a PS (~BiPAP). Spontaneous: Pressure-present inspiratory pause (when there is no flow, there is no effect ventilation = all modes with RR and fixed Ti) PPlateau of Resistance; Pplat@Palv); or set Pause Time ~0.5s; RR, Pinsp, PEEP, FiO2, Flow Trigger, rise time, I:E (set Pocket Reference RR, Vt, PEEP, FiO2, Flow Trigger, Flow pattern, I:E (either Settings Pinsp, PEEP, FiO2, Flow Trigger, Rise time Target: < 30, Optimal: ~ 25 Settings directly or by inspiratory time Ti) Settings directly or via peak flow, Ti settings) Decreasing Ramp (potentially more physiologic) PIP: Total inspiratory work by vent; Reflects resistance & - Decreasing Ramp (potentially more physiologic) Card design by Respiratory care providers from: Square wave/constant vs Decreasing Ramp (potentially Flow Determined by: 1) PS level, 2) R, Rise Time ( rise time ® PPeak inspiratory compliance; Normal ~20 cmH20 (@8cc/kg and adult ETT); - Peak Flow determined by 1) Pinsp level, 2) R, 3)Ti (shorter Flow more physiologic) ¯ peak flow and 3.) pt effort Resp failure 30-40 (low VT use); Concern if >40. Flow = more flow), 4) pressure rise time (¯ Rise Time ® Peak v 0.9 Flow), 5) pt effort ( effort ® peak flow) Pplat-PEEP: tidal stress (lung injury & mortality risk). Target Determined by set RR, Vt, & Flow Pattern (i.e. for any set I:E Determined by patient effort & flow termination (“Esens” – PDriving peak flow, Square (¯ Ti) & Ramp ( Ti); Normal Ti: 1-1.5s; see below “Breath Termination”) < 15 cmH2O. -

Green Creative 97837 LED T8 Tube Ballast Compatibility
Titanium Series T8 13W 4FT. DIR, 10.5W 4FT. DIR, 8W 3FT. DIR, 8W 2FT. DIR For models: 13T8/4F/xxx/DIR, 10.5T8/4F/xxx/DIR, 8T8/3F/xxx/DIR, 8T8/2F/xxx/DIR Where xxx means 824-965 which indicates CRI and color temperature Electronic Ballast Compatibility Compatibility (Ballasts are compatible with 120V & 277V Series Model Type unless otherwise noted) 1 2 3 4 lamp lamps lamps lamps Philips - Advance ICN-1P32-N IS OK - Philips - Advance ICN-2P32-N IS OK - Philips - Advance ICN-3P32-N IS OK - Philips - Advance ICN-4P32-N IS OK Philips - Advance IOPA-1P32-N IS OK - Philips - Advance IOP-2P32-LW-N IS OK - Philips - Advance IOP-3P32-N IS OK - Philips - Advance IOPA-4P32-N IS OK Philips - Advance IOPA-1P32-LW-N IS OK - Philips - Advance IOPA-2P32-LW-N IS OK - Philips - Advance IOP-4P32-LW-N IS OK Philips - Advance IOPA-4P32-SC IS 277V only Philips - Advance IOP-3P32-HL-N IS OK - Philips - Advance ICN-4P32-SC IS OK Philips - Advance ICN-132-MC IS OK - Philips - Advance VEZ-132-SC PS OK - Philips - Advance IZT-132-SC PS OK - Philips - Advance IZT-2PSP32-SC PS OK - Philips - Advance REZ-132-SC PS OK - Philips - Advance VEZ-2S32-SC PS - OK - Philips - Advance REZ-2P32-SC PS - OK - Philips - Advance REL-2P32-SC IS X Philips - Advance REL-2P32-RH-TP IS X GE - Ultramax GE132MAXP-N/ULTRA IS OK - GE - Ultramax GE232MAX-L/ULTRA IS OK - GE - Ultramax GE232MAX-N/ULTRA IS OK - GE - Ultramax GE232MAX-H/ULTRA IS OK - GE - Ultramax GE232MAXP-H/ULTRA IS OK - GE - Ultramax GE232MAXP-N/ULTRA IS OK - GE - Ultramax GE332MAX-N/ULTRA IS OK - GE - Ultramax GE332MAX-H/ULTRA -

NI PS-15 Power Supply User Manual And
Power Supply NI PS-15 Power Supply User Manual NI PS-15 Power Supply User Manual June 2011 372911B-01 Worldwide Technical Support and Product Information ni.com Worldwide Offices Visit ni.com/niglobal to access the branch office Web sites, which provide up-to-date contact information, support phone numbers, email addresses, and current events. National Instruments Corporate Headquarters 11500 North Mopac Expressway Austin, Texas 78759-3504 USA Tel: 512 683 0100 For further support information, refer to the Technical Support and Professional Services appendix. To comment on National Instruments documentation, refer to the National Instruments Web site at ni.com/info and enter the Info Code feedback. © 2009–2011 National Instruments Corporation. All rights reserved. Important Information Warranty The NI PS-15 is warranted against defects in materials and workmanship for a period of one year from the date of shipment, as evidenced by receipts or other documentation. National Instruments will, at its option, repair or replace equipment that proves to be defective during the warranty period. This warranty includes parts and labor. The media on which you receive National Instruments software are warranted not to fail to execute programming instructions, due to defects in materials and workmanship, for a period of 90 days from date of shipment, as evidenced by receipts or other documentation. National Instruments will, at its option, repair or replace software media that do not execute programming instructions if National Instruments receives notice of such defects during the warranty period. National Instruments does not warrant that the operation of the software shall be uninterrupted or error free. -

A Brief Introduction to Unix-2019-AMS
A Brief Introduction to Linux/Unix – AMS 2019 Pete Pokrandt UW-Madison AOS Systems Administrator [email protected] Twitter @PTH1 Brief Intro to Linux/Unix o Brief History of Unix o Basics of a Unix session o The Unix File System o Working with Files and Directories o Your Environment o Common Commands Brief Intro to Unix (contd) o Compilers, Email, Text processing o Image Processing o The vi editor History of Unix o Created in 1969 by Kenneth Thompson and Dennis Ritchie at AT&T o Revised in-house until first public release 1977 o 1977 – UC-Berkeley – Berkeley Software Distribution (BSD) o 1983 – Sun Workstations produced a Unix Workstation o AT&T unix -> System V History of Unix o Today – two main variants, but blended o System V (Sun Solaris, SGI, Dec OSF1, AIX, linux) o BSD (Old SunOS, linux, Mac OSX/MacOS) History of Unix o It’s been around for a long time o It was written by computer programmers for computer programmers o Case sensitive, mostly lowercase abbreviations Basics of a Unix Login Session o The Shell – the command line interface, where you enter commands, etc n Some common shells Bourne Shell (sh) C Shell (csh) TC Shell (tcsh) Korn Shell (ksh) Bourne Again Shell (bash) [OSX terminal] Basics of a Unix Login Session o Features provided by the shell n Create an environment that meets your needs n Write shell scripts (batch files) n Define command aliases n Manipulate command history n Automatically complete the command line (tab) n Edit the command line (arrow keys in tcsh) Basics of a Unix Login Session o Logging in to a unix -

System Analysis and Tuning Guide System Analysis and Tuning Guide SUSE Linux Enterprise Server 15 SP1
SUSE Linux Enterprise Server 15 SP1 System Analysis and Tuning Guide System Analysis and Tuning Guide SUSE Linux Enterprise Server 15 SP1 An administrator's guide for problem detection, resolution and optimization. Find how to inspect and optimize your system by means of monitoring tools and how to eciently manage resources. Also contains an overview of common problems and solutions and of additional help and documentation resources. Publication Date: September 24, 2021 SUSE LLC 1800 South Novell Place Provo, UT 84606 USA https://documentation.suse.com Copyright © 2006– 2021 SUSE LLC and contributors. All rights reserved. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or (at your option) version 1.3; with the Invariant Section being this copyright notice and license. A copy of the license version 1.2 is included in the section entitled “GNU Free Documentation License”. For SUSE trademarks, see https://www.suse.com/company/legal/ . All other third-party trademarks are the property of their respective owners. Trademark symbols (®, ™ etc.) denote trademarks of SUSE and its aliates. Asterisks (*) denote third-party trademarks. All information found in this book has been compiled with utmost attention to detail. However, this does not guarantee complete accuracy. Neither SUSE LLC, its aliates, the authors nor the translators shall be held liable for possible errors or the consequences thereof. Contents About This Guide xii 1 Available Documentation xiii