Information Systems Security Assessment Framework (ISSAF) Draft 0.2
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Norton 360™ Version 3.0, Norton Internet Security™ 2009, and Norton Antivirus™ 2009 Feature Comparison Chart
Norton 360™ Version 3.0, Norton Internet Security™ 2009, and Norton AntiVirus™ 2009 Feature Comparison Chart Feature Norton 360 Norton Internet Norton Explanation Version 3.0 Security 2009 AntiVirus 2009 Core Protection Antivirus ✔ ✔ ✔ Detects and removes viruses, Internet worms, and Trojan horses Antispyware ✔ ✔ ✔ Prevents spyware from infecting the PC Email and instant messaging protection ✔ ✔ ✔ Monitors email and instant messaging so users can exchange files without exchanging threats Antispam ✔ ✔ Automatically filters out annoying and fraudulent or phishing email from the user’s email inbox Advanced Protection Botnet detection ✔ ✔ ✔ Detects and prevents others from taking control of the PC, accessing private information, or using the computer to host an attack Rootkit detection ✔ ✔ ✔ Finds and removes threats that are hidden deep in the operating system Norton™ Insight ✔ ✔ ✔ Includes innovative, intelligence-driven technology for faster, fewer, shorter scans Norton™ Pulse Updates ✔ ✔ ✔ Delivers rapid pulse updates every 5 to 15 minutes for protection against new threats Smart, two-way firewall ✔ ✔ Makes intelligent incoming and outgoing security decisions without interrupting users to ask them each time Enhanced browser protection ✔ ✔ ✔ Secures against Web-based attacks that use browser vulnerabilities to infect PCs with malware Real-time behavioral protection ✔ ✔ ✔ Provides enhanced, real-time protection (SONAR™) Wireless network security protection ✔ ✔ Checks the status of wireless network security and provides expert advice on managing -

Norton 360 User Guide on the CD Or the USB Drive in PDF Format
User Guide See back cover for Quick Installation. We protect more people from more online threats than anyone in the world. Care for our Environment, ‘It's the right thing to do’. Symantec has removed the cover from this manual to reduce the Environmental Footprint of our products. Norton 360™ User Guide The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Documentation version 5.0 Copyright © 2010 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, Norton, SONAR, LiveUpdate, Norton AntiSpam, Norton AntiVirus, Norton Internet Security, Norton 360, and Norton SystemWorks are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U.S. and other countries. Windows is a trademark of Microsoft Corporation. Portions of this product Copyright [1996-2008] Glyph & Cog, LLC. Other names may be trademarks of their respective owners. The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of Symantec Corporation and its licensors, if any. THE DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. SYMANTEC CORPORATION SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION. -

Advanced Cyber Security Techniques (PGDCS-08)
Post-Graduate Diploma in Cyber Security Advanced Cyber Security Techniques (PGDCS-08) Title Advanced Cyber Security Techniques Advisors Mr. R. Thyagarajan, Head, Admn. & Finance and Acting Director, CEMCA Dr. Manas Ranjan Panigrahi, Program Officer (Education), CEMCA Prof. Durgesh Pant, Director-SCS&IT, UOU Editor Mr. Manish Koranga, Senior Consultant, Wipro Technologies, Bangalore Authors Block I> Unit I, Unit II, Unit III & Unit Mr. Ashutosh Bahuguna, Scientist- Indian IV Computer Emergency Response Team (CERT-In), Department of Electronics & IT, Ministry of Communication & IT, Government of India Block II> Unit I, Unit II, Unit III & Unit Mr. Sani Abhilash, Scientist- Indian IV Computer Emergency Response Team Block III> Unit I, Unit II, Unit III & Unit (CERT-In), Department of Electronics & IT, IV Ministry of Communication & IT, Government of India ISBN: 978-93-84813-95-6 Acknowledgement The University acknowledges with thanks the expertise and financial support provided by Commonwealth Educational Media Centre for Asia (CEMCA), New Delhi, for the preparation of this study material. Uttarakhand Open University, 2016 © Uttarakhand Open University, 2016. Advanced Cyber Security Techniques is made available under a Creative Commons Attribution Share-Alike 4.0 Licence (international): http://creativecommons.org/licenses/by-sa/4.0/ It is attributed to the sources marked in the References, Article Sources and Contributors section. Published by: Uttarakhand Open University, Haldwani Expert Panel S. No. Name 1 Dr. Jeetendra Pande, School of Computer Science & IT, Uttarakhand Open University, Haldwani 2 Prof. Ashok Panjwani, Professor, MDI, Gurgoan 3 Group Captain Ashok Katariya, Ministry of Defense, New Delhi 4 Mr. Ashutosh Bahuguna, Scientist-CERT-In, Department of Electronics & Information Technology, Government of India 5 Mr. -

Norton-360.Pdf
Norton™ 360 Product Manual Norton™ 360 Product Manual The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Documentation version 22.21.3 Copyright © 2021 NortonLifeLock Inc. All rights reserved. NortonLifeLock, the NortonLifeLock Logo, the Checkmark Logo, Norton, Norton Secured Logo, LifeLock, and the LockMan Logo are trademarks or registered trademarks of NortonLifeLock Inc. or its affiliates in the U. S. and other countries. Other names may be trademarks of their respective owners. The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of NortonLifeLock Inc. and its licensors, if any. THE DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. NORTONLIFELOCK INC. SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE. The Licensed Software and Documentation are deemed to be commercial computer software as defined in FAR 12.212 and subject to restricted rights as defined in FAR Section 52.227-19 "Commercial Computer Software - Restricted Rights" and DFARS 227.7202, et seq. "Commercial Computer Software and Commercial Computer Software Documentation," as applicable, and any successor regulations, whether delivered by NortonLifeLock as on premises or hosted services. -

Norton 360 Användarhandbok
Användarhandbok Mer information om snabbinstallation finns på baksidan. Vi skyddar fler människor från fler hot på Internet än någon annan i världen. Det är det enda rätta är att bry sig om miljön. Symantec har tagit bort omslaget till den här manualen för att minska de ekologiska fotavtrycken från våra produkter. Användarhandbok för Norton 360™ Den programvara som beskrivs här levereras under licensavtal och får endast användas i enlighet med villkoren i avtalet. Dokumentation version 4.0 Copyright © 2009 Symantec Corporation. Med ensamrätt. Symantec, Symantec Logo, Norton, SONAR, LiveUpdate, Norton AntiSpam, Norton AntiVirus, Norton Internet Security, Norton 360 och Norton SystemWorks är varumärken eller registrerade varumärken som ägs av Symantec Corporation eller dess dotterbolag i USA och andra länder. Windows är ett varumärke som tillhör Microsoft Corporation Delar av den här produktens upphovsrätt [1996-2008] Glyph & Cog, LLC. Andra namn kan vara varumärken som tillhör respektive ägare. Den produkt som beskrivs i detta dokument distribueras under licens som begränsar dess användning, kopiering, distribution och dekompilering/omvänd utveckling. Detta dokument eller delar av det får inte reproduceras i någon form för något ändamål utan uttrycklig skriftlig tillåtelse från Symantec Corporation och dess eventuella licensgivare. DOKUMENTATIONEN TILLHANDAHÅLLS I BEFINTLIGT SKICK OCH SYMANTEC FRISKRIVER SIG FRÅN ALLA UTTRYCKLIGA ELLER UNDERFÖRSTÅDDA VILLKOR, UPPGIFTER OCH GARANTIER, INKLUSIVE EVENTUELLA UNDERFÖRSTÅDDA GARANTIER OM KOMMERSIELL GÅNGBARHET, LÄMPLIGHET FÖR ETT VISST ÄNDAMÅL ELLER INTRÅNG I TREDJE PARTS RÄTTIGHETER, UTOM I DEN UTSTRÄCKNING SOM SÅDAN FRISKRIVNING ANSES VARA JURIDISKT OGILTIG. SYMANTEC CORPORATION SKALL INTE HÅLLAS ANSVARIGT FÖR OFÖRUTSEDDA SKADOR ELLER FÖLJDSKADOR I SAMBAND MED UTRUSTNINGENS PRESTANDA ELLER ANVÄNDNINGEN AV DENNA DOKUMENTATION. -

Norton 360 User Guide on the CD Or the USB Drive in PDF Format
User Guide See back cover for Quick Installation. We protect more people from more online threats than anyone in the world. Care for our Environment, ‘It's the right thing to do’. Symantec has removed the cover from this manual to reduce the Environmental Footprint of our products. Norton 360™ User Guide The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Documentation version 4.0 Copyright © 2009 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, Norton, SONAR, LiveUpdate, Norton AntiSpam, Norton AntiVirus, Norton Internet Security, Norton 360, and Norton SystemWorks are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U.S. and other countries. Windows is a trademark of Microsoft Corporation. Portions of this product Copyright [1996-2008] Glyph & Cog, LLC. Other names may be trademarks of their respective owners. The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of Symantec Corporation and its licensors, if any. THE DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. SYMANTEC CORPORATION SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION. -

Norton Internet Security User Guide
User Guide See back cover for Quick Installation. Care for our Environment, ‘It's the right thing to do’. Symantec has removed the cover from this manual to reduce the Environmental Footprint of our products. Norton™ Internet Security User Guide The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Documentation version 19.0 Copyright © 2011 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, Norton, SONAR, LiveUpdate, Norton AntiSpam, Norton AntiVirus, Norton Internet Security, Norton 360, and Norton SystemWorks are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U.S. and other countries. Windows is a trademark of Microsoft Corporation. Portions of this product Copyright [1996-2008] Glyph & Cog, LLC. Other names may be trademarks of their respective owners. The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of Symantec Corporation and its licensors, if any. THE DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. SYMANTEC CORPORATION SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE. -

Penetration Testing and Network Defense
Penetration Testing and Network Defense Andrew Whitaker, Daniel P. Newman Cisco Press 800 East 96th Street Indianapolis, IN 46240 USA ii Penetration Testing and Network Defense Andrew Whitaker and Daniel P. Newman Copyright© 2006 Cisco Systems, Inc. Published by: Cisco Press 800 East 96th Street Indianapolis, IN 46240 USA All rights reserved. No part of this book may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, recording, or by any information storage and retrieval system, without writ- ten permission from the publisher, except for the inclusion of brief quotations in a review. Printed in the United States of America 1 2 3 4 5 6 7 8 9 0 First Printing November 2005 Library of Congress Cataloging-in-Publication Number: 2004108262 ISBN: 1-58705-208-3 Warning and Disclaimer This book is designed to provide information about penetration testing and network defense techniques. Every effort has been made to make this book as complete and as accurate as possible, but no warranty or fitness is implied. The information is provided on an “as is” basis. The authors, Cisco Press, and Cisco Systems, Inc. shall have neither liability nor responsibility to any person or entity with respect to any loss or damages arising from the information contained in this book or from the use of the discs or programs that may accompany it. The opinions expressed in this book belong to the authors and are not necessarily those of Cisco Systems, Inc. Feedback Information At Cisco Press, our goal is to create in-depth technical books of the highest quality and value. -

Norton™ Internet Security
Norton™ Internet Security Product Manual Norton™ Internet Security Product Manual The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Documentation version 22.21.3 Copyright © 2021 NortonLifeLock Inc. All rights reserved. NortonLifeLock, the NortonLifeLock Logo, the Checkmark Logo, Norton, Norton Secured Logo, LifeLock, and the LockMan Logo are trademarks or registered trademarks of NortonLifeLock Inc. or its affiliates in the U. S. and other countries. Other names may be trademarks of their respective owners. The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of NortonLifeLock Inc. and its licensors, if any. THE DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. NORTONLIFELOCK INC. SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE. The Licensed Software and Documentation are deemed to be commercial computer software as defined in FAR 12.212 and subject to restricted rights as defined in FAR Section 52.227-19 "Commercial Computer Software - Restricted Rights" and DFARS 227.7202, et seq. "Commercial Computer Software and Commercial Computer Software Documentation," as applicable, and any successor regulations, whether delivered by NortonLifeLock as on premises or hosted services. -

Norton 360 with Lifelock
Norton™ AntiVirus Plus Norton™ 360 Norton™ 360 with LifeLock™ Norton™ 360 for Gamers User Manual Norton™ 360 with LifeLock™ User Manual The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Copyright © 2021 NortonLifeLock Inc. All rights reserved. The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of NortonLifeLock Inc. and its licensors, if any. THE DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. NORTONLIFELOCK INC. SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE. The Licensed Software and Documentation are deemed to be commercial computer software as defined in FAR 12.212 and subject to restricted rights as defined in FAR Section 52.227-19 "Commercial Computer Software - Restricted Rights" and DFARS 227.7202, et seq. "Commercial Computer Software and Commercial Computer Software Documentation," as applicable, and any successor regulations, whether delivered by NortonLifeLock as on premises or hosted services. Any use, modification, reproduction release, performance, display or disclosure of the Licensed Software and Documentation by the U.S. -
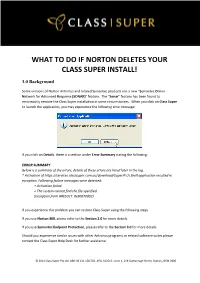
What to Do If Norton Deletes Your Class Super Install!
WHAT TO DO IF NORTON DELETES YOUR CLASS SUPER INSTALL! 1.0 Background Some versions of Norton Antivirus and related Symantec products use a new “ Symantec Online Network for Advanced Response (SONAR) ” feature. The “ Sonar ” feature has been found to erroneously remove the Class Super installation in some circumstances. When you click on Class Super to launch the application, you may experience the following error message: If you click on Details , there is a section under Error Summary stating the following: ERROR SUMMARY Below is a summary of the errors, details of these errors are listed later in the log. * Activation of https://services.classsuper.com.au/download/SuperIP.UI.Shell.application resulted in exception. Following failure messages were detected: + Activation failed. + The system cannot find the file specified. (Exception from HRESULT: 0x80070002) If you experience this problem you can restore Class Super using the following steps. If you use Norton 360 , please refer to the Section 2.0 for more details. If you use Symantec Endpoint Protection , please refer to the Section 3.0 for more details. Should you experience similar issues with other Antivirus programs or related software suites please contact the Class Super Help Desk for further assistance. © 2011 Class Super Pty Ltd. ABN 46 121 158 503. AFSL 313512. Level 1, 219 Castlereagh Street, Sydney, NSW 2000. 2.0 Steps Required for Symantec Norton 360 1. Click on Norton 360 icon, to launch Norton 360 : 2. Click on PC Security icon, to launch PC Security details: © 2011 Class Super Pty Ltd. ABN 46 121 158 503. -
Norton Free Download for Pc Norton Internet Security
norton free download for pc Norton Internet Security. Norton Internet Security is a powerful all-in-one security solution for personal computers. If you want a security solution for your PC that deals with antiviruses as well as a host of other modern threats, then Norton Internet Security is a strong option. This suite of tools features a virus detection engine, a virus removal and quarantine engine, a firewall, an Identity Safe feature, and much more. You can configure Norton Internet Security to perform automatic scans on a schedule or instruct it to perform manual scans on demand. Scans can encompass an entire system or just a portion. The application also provides real-time protection, which safeguards not only against viruses but against all manner of spyware, malware, and even malicious or otherwise unsafe websites. Norton Internet Security also finds a great balance between usability and sophistication. The casual user can configure and use this program without much hassle, but advanced users will also have all the options necessary to have fine control over the firewall, real-time protection, and so forth. Some of those advanced features are a bit buried, but this isn’t a big deal once you know where they are. Something else that has made Norton Internet Security such a success is its use of resources. This is not a resource hog the way many competing software solutions are. It will even run reasonably well on outdated machines, and if you need a solution that can protect your PC in the background while you game, then you won’t find many options better than this one.