Unobtrusive, Pervasive, and Cost-Effective Communications with Mobile Devices
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

DISTRICTS Peter Calamari Asst
DISTRICTS Peter Calamari Asst. Vice President Facilities Operations and Development 614.292.3377 Facilities Operations Functional Org Chart Administration Remi Timmons June 22, 2021 Office Admin. Associate 614.247.4094 Zone 1 Buildings 18th Avenue Library, 209 W. 18th, Baker Systems, Bricker Hall, Caldwell Laboratory, Central Service Building, Cockins Hall, Denney Hall, Derby Zone 1 Hall, Dreese Laboratories, Dulles Hall, Enarson Classroom, French Field House, Hayes Hall, Hopkins Hall, Ice Rink, Independence Hall, Jesse Karen Crabbe Owens North, Journalism Building, Maintenance Building, Math Building, Math Tower, McCorkle Aquatic Pavilion, McCracken Power Plant, Zone Leader Northwood-High Building, Ohio Stadium, Physical Activity & Education Services, Recreation & Physical Activity Center, St. John Arena, Stillman 614.688.8264 Hall, University Hall, Wilce Student Health Center, Women’s Field House Academic District 3,513,341 Sq Ft (Services All Campus) Zone 2 Buildings Kenny King 140 W. 19th, Arps Hall, Bolz Hall, Celeste Laboratory, Chemical & Biomolecular Engineering, Chemical Engineering Storage, Converse Hall, Evans Zone 2 Laboratory, Fisher Hall, Fontana Laboratories, Gerlach Hall, Hitchcock Hall, Hughes Hall, Knowlton Hall, Koffolt Laboratories, MacQuigg Laboratory, Leader Jim Wright Mason Hall, McPherson Chemical Laboratory, Mershon Auditorium, Newman & Wolfrom Laboratory, Page Hall, Pfahl Hall, Physics Research 614.688.8632 Zone Leader (Interim) Building, Ramseyer Hall, Smith Laboratory, Schoenbaum Hall, Scott Laboratory, Student Academic Service Building, Sullivant Hall, Tuttle Park 614.292.9844 Place Garage Retail Space, Watts Hall, Weigel Hall, Wexner Center for the Arts 3,694,839 Sq Ft Administration Zone 3 Buildings Kathy Snoke Atwell Hall, BRT, Comprehensive Cancer Center, Davis Heart & Lung Research Institute, Evans Hall, Graves Hall, Hamilton Hall, Meiling Hall, Office Admin. -

THE OHIO STATE UNIVERSITY BULLETIN College of Law
1967-68 Announcements / Book 10 THE OHIO STATE UNIVERSITY BULLETIN THE OHIO STATE UNIVERSITY BULLETIN College of Law 1967-68 Announcem ents / Book 10 THE OHIO STATE UNIVERSITY BULLETIN Volum e LXXI No. 16 A pril 25, 1967 Published by The Ohio State University at Columbus, Ohio. Issued 20 times during the year: twice in July, once in October, three times in November, and 14 times in April. Second-class postage paid at Columbus, Ohio. Board of Trustees of the University Jacob E. Davis, Chairman, Cincinnati Stanley C. Allyn, Vice Chairman, Dayton John W. Bricker, Colum bus Bertram D. Thomas, Columbus John G. Ketterer, Canton Frederick E. Jones, Columbus Mervin B. France, Cleveland Jam es W. Shocknessy, Colum bus Donald M. Hilliker, Bellefontaine John T. Mount, Secretary, Columbus Administrative Officers of the University Novice G. Fawcett President John E. Corbally, Jr. V/ce President for Academic Affairs and Provost of the University Gordon B. Carson Vice President for Business and Finance Alfred B. Garrett Vice President for Research John T. M ount Vice President for Educational Services John T. Bonner, Jr. Executive Dean for Student Relations Ronald B. Thompson Executive Dean for Admissions and Registrations John H. Herrick Executive Director for Campus Planning Frederick Stecker Executive Director for University Relations G. Robert Holsinger Executive Assistant to the President Table of Contents Officers and Faculty 5 Objectives and Organization 6 O bjectives H istory Total Responsibility Facilities Library Research Facilities The Ohio -

USDOT Region V Regional University Transportation Center Final Report
MN WI MI OH IL IN USDOT Region V Regional University Transportation Center Final Report NEXTRANS Projects No. 141OSUY2.1 and No. 172OSUY2.2 RESEARCH, EDUCATION AND OUTREACH FROM CAMPUS TRANSIT LABORATORY And CAMPUS TRANSIT LABORATORY: INFRASTRUCTURE FOR RESEARCH, EDUCATION, AND OUTREACH By Mark R. McCord, Principal Investigator Professor of Civil, Environmental, and Geodetic Engineering The Ohio State University [email protected] and Rabi G. Mishalani, Principal Investigator Professor of Civil, Environmental, and Geodetic Engineering The Ohio State University [email protected] Report Submission Date: March 13, 2018 ACKNOWLEDGMENTS AND DISCLAIMER Partial funding for this research was provided by the NEXTRANS Center, Purdue University under Grant No. DTRT12-G-UTC05 of the U.S. Department of Transportation, Office of the Assistant Secretary for Research and Technology (OST-R), University Transportation Centers Program. Additional funding was provided by The Ohio State University (OSU) including the College of Engineering and Transportation and Traffic Management. The authors are grateful to OSU’s Transportation and Traffic Management for its support of the OSU Campus Transit Lab (CTL) and Elizabeth Kelley-Snoke, Tom Holman, Timothy Smith, and Sean Roberts for their efforts in supporting the development and continued maintenance of the CTL, which resulted in the availability of the data used in this project. The contents of this report reflect the views of the authors, who are responsible for the facts and the accuracy of the information presented herein. This document is disseminated under the sponsorship of the Department of Transportation, University Transportation Centers Program, in the interest of information exchange. The U.S. -

We're All Over Campus Like Scarlet and Gray™ on Game Day
We’re all over campus like SCARLET AND GRAY™ ON GAME DAY. Huntington is proud to be the Official Consumer Bank of The Ohio State University,® with more campus-area access, including 19 ATMs and 2 full-service branches. Visit huntington.com/OSU Member FDIC. ® and Huntington® are federally registered service marks of Huntington Bancshares Incorporated. Huntington® Welcome.™ is a service mark of Huntington Bancshares Incorporated. © 2012 Huntington Bancshares Incorporated. 122302 0412 21838-3 OSU VisitorsGuideBanner_R5 CR.indd 1 5/9/12 2:54 PM CAMPUS VISIT INFORMATION: osu.edu/visitors ERSITY V UNI STATE OHIO THE OF ANK B ONSUMER C IAL C OFFI THE , TON G HUNTIN Y B D SPONSORE COLUMBUS CAMPus MAP INDEX Welcome to The Ohio State University, a world-class public research and teaching FO 191 4-H Center ............................................................................ F-5 891 Lane Avenue Residence Hall .............................................. I-5 institution. We hope you enjoy your visit and experience some of the tradition and AK 243 600–640, 670, 680 Ackerman Road ................................... F-0 898 1480 W. Lane Avenue .........................................................A-6 241 650 Ackerman Road ........................................................... F-0 LZ 041 Lazenby Hall ........................................................................ J-8 excitement that Ohio State has to offer. AP M US P M A C COLUMBUS 2012–2013 242 660 Ackerman Road ........................................................... F-0 -

THE OHIO STATE UNIVERSITY BULLETIN the Graduate School
THE OHIO STATE UNIVERSITY BULLETIN THE OHIO STATE UNIVERSITY BULLETIN The Graduate School 1968-69 Catalog / Book 9 THE OHIO STATE UNIVERSITY BULLETIN V o lum e LX X II No. 15 A p ril 11, 1968 Published by The Ohio State University at Columbus, Ohio. Issued 25 times during the year: once in July, twice in October, once in November, once in January, and 20 times in April. Second class postage paid at Columbus, Ohio. I Board of Trustees of the University Stanley C. Allyn, Chairman, Dayton John W. Bricker, Vice Chairman, Columbus Bertram D. Thomas, Columbus John G. Ketterer, Canton Frederick E. Jones, Columbus Mervin B. France, Cleveland James W. Shocknessy, Columbus Donald M. Hilliker, Bellefontaine William C. Safford, Cincinnati John T. Mount, Secretary, Columbus Administrative Officers of the University Novice G. Fawcett President John E. Corbally, Jr. Vice President for Academic Affairs and Provost Gordon B. Carson Vice President for Business and Finance Alfred B. G arrett Vice President for Research John T. Mount Vice President for Educational Services John T. Bonner, Jr. Executive Dean for Student Relations Ronald B. Thompson Executive Dean for Admissions and Registrations Frederick Stecker Executive Director for University Relations G. Robert Holsinger Executive Assistant to the President Table of Contents The Graduate School 5 General Information Organization Degrees Conferred Through the Graduate School Preparation for College Teaching Off-Campus Graduate Centers Agreements with Other Institutions Other Cooperative Programs The University -
2011 EVENT SCHEDULE and INFORMATION Students, Siblings, Parents and Friends
2011 EVENT SCHEDULE AND INFORMATION Students, Siblings, Parents and Friends, We are pleased to welcome you to campus for Sibs & Kids Weekend 2011. Sibs & Kids Weekend is an opportunity for Ohio State students, faculty, and staff to invite brothers, sisters, nieces, nephews, cousins, children, or friends of the family to campus to experience the excitement of Ohio State. We hope all of you will get a taste of Buckeye life as you explore many fun and interesting activities throughout the weekend. Events such as Sibs & Kids Weekend allow our students to share elements of their collegiate experience with important people in their lives, and aid in maintaining the connections with family and friends that are so important to the success of our students and our university. We hope the programs and events offered over the next few days will offer you a window into the lives of our students and further nurture the already strong relationships that exist within your family. Ohio State prides itself on the vast network of faculty, staff, alumni, and friends who work to support the growth and maturity of our students. Only through partnerships between the university and you and your family can we address the complete development and success of your student. Please enjoy your time at Ohio State. And come back often! Sincerely, Javaune Adams-Gaston, Ph.D. Vice-President for Student Life 1 TABLE OF CONTENTS Campus Map 2 Ohio Union Map 4 Sibs & Kids Events 8 Columbus Happenings 18 Discounts 20 1 Building Index FO 191 4-H Center...................................................J-3 FL 151 Fontana Laboratories .......................... -
CONCERNS at BCHS Tions Has Been Set by the William Hall Rodgers Tentative Christmas Basket Fund
T U E S D A Y 162nd YEAR • No. 182 NOVEMBER 29, 2016 CLEVELAND, TN 16 PAGES • 50¢ Local firefighters dispatched to Sevier County Cleveland, Bradley crews CU crews restore fighting Gatlinburg blazes electricity to 1,944 By ALLEN MINCEY Banner Staff Writer By LARRY BOWERS Cleveland and Bradley County “We are in the process Banner Staff Writer today of sending a “We were able to firefighters are helping the Cleveland Utilities sent crews restore power very efforts to fight fires in the different engine that into the windstorms Monday quickly in each of the Gatlinburg and Pigeon Forge way, and we will have evening and early this morning, areas today, and will continue to two of the four up there disruptions.” with scattered damage and power — Jamie Creekmore do so as long as they are need- returning with it.” outages reported across the utili- ed. — Shawn Fairbanks ty’s service area. According to Chief Shawn Two waves of storms swept outages. Fairbanks of Bradley County through the Cleveland communi- “The total of customers out of Fire-Rescue, one engine and AP/Photo Courtesy of Brianna Paciorka/Knoxville News Sentinel “We are in the process today ty, one in the evening and anoth- power overnight was 1,944,” said four firefighters were sent to THICK SMOKE from area forest fires looms in Gatlinburg on er after midnight. Creekmore, adding that the max- that area around 8:30 p.m. of sending a different engine Monday. According to reports, as many as 30 structures there were that way, and we will have two Jamie Creekmore, CU imum number without power at Monday. -

Graduate School
THE OHIO STATE UNIVERSITY CATALOG 1969-70 I Book 9 Graduate School THE OHIO STATE UNIVERSITY CATALOG V o lu m e I N o . 9 A p ril 11, 1969 Published by The Ohio State University at Columbus, Ohio. Issued 18 times during April. Application to mail under second class postage privileges is pending at Columbus, Ohio. Board of Trustees of the University John W. Bricker, Chairman, Columbus Bertram D. Thomas, Vice Chairman, Santa Barbara John G. Ketterer, Canton Frederick E. Jones, Columbus Mervin B. France, Cleveland James W. Shocknessy, Columbus Donald M. Hilliker, Bellefontaine William C. Safford, Cincinnati John H. Dunlap, Williamsport Edward Q. Moulton, Secretary, Columbus Administrative Officers of the University Novice G. Fawcett President John E. Corbally, Jr. Vice President for Academic Affairs and Provost Gordon B. Carson Vice President for Business and Finance Alfred B. Garrett Vice President for Research John T. Mount Vice President for Student Affairs John T. Bonner, Jr. Vice President for Educational Services Robert G. Smith Vice President for University Development Ronald B. Thompson Executive Dean for Student Statistical Services Edward Q. Moulton Executive Assistant to the President Table of Contents The Graduate School 5 General Information Organization Degrees Conferred Through the Graduate School Preparation for College Teaching Off-Campus Graduate Centers Agreements with Other Institutions Other Cooperative Programs The University Libraries Research 11 Admission and Registration 15 Admission Procedures and Requirements Test -
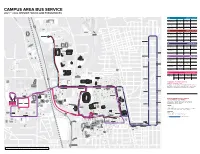
Campus Area Bus Service 2021 – 2022 Service Hours and Frequencies
CAMPUS AREA BUS SERVICE 2021 – 2022 SERVICE HOURS AND FREQUENCIES The Ohio State University Airport The Ohio State University Golf Course Outpatient Care Center of Upper Arlington Sandefur Wetland Pavilion Olentangy St. CLN CAMPUS LOOP NORTH 600 N. High St. Wilma H. Schiermeier Olentangy River Ackerman Rd. FREQUENCY 680 610 Wetland Research Park 7am – 6Pm 6Pm – 10Pm 10Pm – MIDNIGHT Ackerman Rd., 700 630 REGULAR WEEKDAY Monday - Friday service. No weekend service. 8 mIN 15 mIN — Cliside Dr. 670 640 Hener Wetland Research and Education Olentangy Greenway Trail 7am – 7Pm 7Pm – 10Pm 10Pm – MIDNIGHT 650 St. Calumet 660 SUMMER SERVICE Weekday service only. No weekend service. 15 mIN — — Arcadia Ave. Ackerman Rd. Arcadia Ave. 7am – 7Pm 7Pm – 10Pm 10Pm – MIDNIGHT Kenny Rd. BREAK SERVICE W. North St. Ave. East Weekday service only. No weekend service. 15 mIN — — Jameson Crane Pl. Pomeroy Sports Medicine Institute B A Adams Ave. Adams Findley Ave. Findley Medary Ave. Medary Dayton Ave. Dayton Defiance Dr. Fred Taylor Dr. Cuyahoga Ct. Glenmawr Ave. E E. Dodridge St. C CLS CAMPUS LOOP SOUTH D J W. Dodridge St. F FREQUENCY 7am – 6Pm 6Pm – 10Pm 10Pm – MIDNIGHT Central Mahoning Ct. Ackerman Rd. Neil Ave. Sterile Stark Ct. K Supply G L REGULAR WEEKDAY Monday - Friday service. No weekend service. 8 mIN 15 mIN — H ChildCenter Care W. Dodridge St. Indianola Ave. M Glen Echo Dr. E. Duncan St. E. Hudson St. N E. Hudson St. Buckeye Montgomery Ct. 7am – 7Pm 7Pm – 10Pm 10Pm – MIDNIGHT BUCKEYE LOT LOOP W. Duncan St. Village R P Administration SUMMER SERVICE Weekday service only. -

BIM Initiative and Implementation 2015 9.23.15
The Buckeye BIM Initiative Facilities Information & Technology Services BIM for Design and Construction Developing BIM standards and execution plans for the design and construction process. The BIM Project Delivery Standard and BIM Implementation Plan have been approved by senior leadership. The BIM Project Delivery Standard has been published to the FOD website for use by AEC firms. Phase 1 of the Implementation Plan which include, training, updates to the BDS, support for several pilot projects, and finalization of the process to rapidly push data into AiM from the models has begun. BIM for Existing Buildings Moving from Autocad based oorplans to Revit based building models. 0 12.5 25 37.5 50 62.5 75 87.5 100 8.3% 45.8% In Progress The Ohio State University Academic Campus Goal: 5,000,000sqft Base Model Development Base Model May 2015 - May 2016 Year Complete Base Model Exterior (detail) | Walls/Cubicles | Doors | Windows | Roof (basic) | 48.6% Plumbing Fixtures (basic) | Columns | Column Grids | Floors | Ceilings (basic) | Stairs (basic) | Expected 62% Conference and Classroom Furniture 141 Buildings Complete May 2016 16,676,957 Sqft. Completed Total Buckeye BIM Implementation Total Goal: 34,350,000sqft Base Model Development Visit http://bit.ly/OSU_Fits_Gallery to view more project renderings Sept. 22nd, 2015 Tzagournis Medical Research (0163) University Hospital East - Main Building (0398) University Hospital East - Talbot Hall (0399) University Hospital East - Tower (0397) BIM Building List Key Expected Academic Year 2015 In Progress -

The College of Engineering in the First Hundred Years of the Ohio State
__j The College of Engineering in the First Hundred Years of The Ohio State University by J. Merrill Weed September, 1969 I I Subject: TEE COLLEGE OF ENGDJEERI.tm n: THE FI'tST 100 YEARS OF ThE OHIO STATE UNIVERSITY Length: Approximately -!0,008 words Completion date: May 1969 Outli:1e: I. The First Quarter Century--Before the College of Engineering was established, 1870-1895 A. The place of ":Mechanics" in The Ohio Agricultural and Mechanical College a. Breadth in Education ••• Training "Engineers" rather than 11Eechanics 11 or technicians b. Engineering subjects in the curriculum: (1) Physics and mechanics (2) Mathewatics, astronomy, surveying, and civil engineering (3) Geology and }~ining (4) Applied chemistry B. Engineering in the early Ohio state University, 1878-1895 a. Eneineerinz in the School of the Exact Sciences b. The School of Enzineering C. Activities and service of graduates and faculty II. The Second Quarter Century -- 1895-1920 A. The College of Engineerinc, 1895-1920 a. Ad.irinistration (1) Dean N. w. Lord, 1895-1901 (2) Dean C. N. Brown, 1901-1902 (3) Dean Edward Orton, Jr., 1902-1906 (4) Dean F. A. P.ay, 1906-1908 (5) Acting Dean F. C. Caldi:-r.-:,ll, 1908-1909 (6) Acting Dean J.E. Boyd, 19:>9-1910 (7) Dean Edward Orton, Jr., 1910-1915 (8) Act in? Dean E. F. Coddinzton, 1915-1920 b. Curricula and Activities (1) :mrollment, courses, and graduates, including Arts-Enzineering (2) Proble,ns chrin? and following the first world war (3) Develo·;:)lnent of student activities, including Ohio Sta~~-_I~ngineer (L~) .::L·ects upon indu~;trial activity of the State -:,f Ohio and the Profession of Engineering B. -

A Map of the OSU Campus
A B C D E F G H I J K L M N Building Index AA 003 Agricultural Administration Bldg..........I-3 385 Child Care Center...............................M-3 FF 086 French Field House................................I-4 AE 298 Agricultural Engineering Bldg..............I-3 CH 063 Cockins Hall.........................................F-5 FR 059 Fry Hall ..................................................B-5 AO Airport, The Ohio State University 363 Comprehensive Cancer Center 282 Galbreath Equine Center.....................G-3 974 (See web site for location (above Wiseman Hall)....................C-4 GB 132 General Biology Annex........................D-5 094 www.osuairport.org) CV 056 Converse Hall .......................................I-5 GE 250 Gerlach Graduate Programs Bldg........I-6 009 1 174 Animal House........................................F-1 300 Cramblett Hall (Hospitals Clinic).......B-4 GL 180 Goss Laboratory...................................F-3 137 1 AS 156 Animal Science Building .....................H-3 CZ 293 Cunz Hall of Languages .....................E-5 GR 277 Graves Hall............................................B-5 158 261 Archer House .........................................I-6 317 Dairy Science Center, Waterman HH 037 Hagerty Hall ..........................................D-7 951 264 017 Architecture Building...........................H-5 Farm Complex.................................J-1 HL 259 Hale Hall ................................................C-6 174 131 Aronoff Laboratory...............................C-5