Accurate and Efficient Image Forgery Detection Using Lateral Chromatic
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Image Sensors and Image Quality in Mobile Phones
Image Sensors and Image Quality in Mobile Phones Juha Alakarhu Nokia, Technology Platforms, Camera Entity, P.O. Box 1000, FI-33721 Tampere [email protected] (+358 50 4860226) Abstract 2. Performance metric This paper considers image sensors and image quality A reliable sensor performance metric is needed in order in camera phones. A method to estimate the image to have meaningful discussion on different sensor quality and performance of an image sensor using its options, future sensor performance, and effects of key parameters is presented. Subjective image quality different technologies. Comparison of individual and mapping camera technical parameters to its technical parameters does not provide general view to subjective image quality are discussed. The developed the image quality and can be misleading. A more performance metrics are used to optimize sensor comprehensive performance metric based on low level performance for best possible image quality in camera technical parameters is developed as follows. phones. Finally, the future technology and technology First, conversion from photometric units to trends are discussed. The main development trend for radiometric units is needed. Irradiation E [W/m2] is images sensors is gradually changing from pixel size calculated as follows using illuminance Ev [lux], reduction to performance improvement within the same energy spectrum of the illuminant (any unit), and the pixel size. About 30% performance improvement is standard luminosity function V. observed between generations if the pixel size is kept Equation 1: Radiometric unit conversion the same. Image sensor is also the key component to offer new features to the user in the future. s(λ) d λ E = ∫ E lm v 683 s()()λ V λ d λ 1. -
Macro References and Glossary Ofterms.Docx
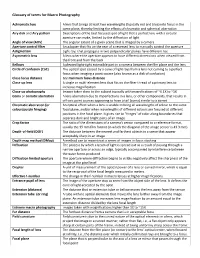
Glossary of terms for Macro Photography Achromatic lens A lens that brings at least two wavelengths (typically red and blue) into focus in the same plane, thereby limiting the effects of chromatic and spherical aberration Airy disk and Airy pattern Descriptions of the best focused spot of light that a perfect lens with a circular aperture can make, limited by the diffraction of light Angle of view (AOV) The angular extent of a given scene that is imaged by a camera Aperture control filter An adapter that fits on the rear of a reversed lens to m anually control the aperture Astigmatism Light rays that propagate in two perpendicular planes have different foci Asymmetric lens A lens where the aperture appears to have different dimensions when viewed from the front and from the back Bellows A pleated light -tight ex ten sible part in a camera between the film plane and the lens Circle of confusion (CoC) The optical spot caused by a cone of light rays from a lens not coming to a perfect focus when imaging a point source (also known as a disk of confusion) Close focus distance See minimum focus distance Close -up lens A single or multi -element lens that fi ts on the filter t hread of a primary lens to increase magnification Close -up photography Images taken close to the subject typically with magnifications of ~0.1X to ~1X Coma or comatic aberration A lens aberration due to imperfections in a lens , or other components, that results in off-axis point sources appearing to have a tail (coma) similar to a comet Chromatic a berration (or An optical effect when a lens is unable to bring all wavelengths of colo ur to the same colour/purple fringing) focal plane, and/or when wavelengths of different colours are focused at different positions in the focal plane. -

Optical Performance:: Characterization of a Pupillometric Camera
RELATED TITLES Documents Science & Tech Tech Digital & Social Media 58 views 0 0 Abb Uploaded by Mabel Ruiz AP-Physical Low Light Manual Twilight Retrato Science Sample Photography for Render 1.4.5 Aberration document explaining the Seidel coefficients Full description Save Embed Share Print S-118.4250 PPOSTGRADUATE SEMINAR ON ILLUMINATION ENGINEERING ,, SSPRING 2008 LLIGHTING UUNIT,, DDEPARTMENT OF EELECTRONICS,, HHELSINKI UUNIVERSITY OF TTECHNOLOGY (TKK) OPTICAL PERFORMANCE:: CHARACTERIZATION OF A PUPILLOMETRIC CAMERA Petteri Teikari,, [email protected] Emmi Rautkylä,, emmi.rautkylä@tkk.fi RELATED TITLES Documents Science & Tech Tech Digital & Social Media 58 views 0 0 Abb Uploaded by Mabel Ruiz AP-Physical Low Light Manual Twilight Retrato Science Sample Photography for Render 1.4.5 Aberration document explaining the Seidel coefficients Full description Save Embed Share Print RELATED TITLES Documents Science & Tech Tech Digital & Social Media 58 views 0 0 Abb Uploaded by Mabel Ruiz AP-Physical Low Light Manual Twilight Retrato Science Sample Photography for Render 1.4.5 Aberration document explaining the Seidel coefficients Full description Save Embed Share Print TABLE OF CONTENTS A A BSTRACT .................................................................................................................................. TT ABLE OF CONTENTS ................................................................................................................2 11 IINTRODUCTION.................................................................................................................3 -

Image Quality Assessment Through FSIM, SSIM, MSE and PSNR—A Comparative Study
Journal of Computer and Communications, 2019, 7, 8-18 http://www.scirp.org/journal/jcc ISSN Online: 2327-5227 ISSN Print: 2327-5219 Image Quality Assessment through FSIM, SSIM, MSE and PSNR—A Comparative Study Umme Sara1, Morium Akter2, Mohammad Shorif Uddin2 1National Institute of Textile Engineering and Research, Dhaka, Bangladesh 2Department of Computer Science and Engineering, Jahangirnagar University, Dhaka, Bangladesh How to cite this paper: Sara, U., Akter, M. Abstract and Uddin, M.S. (2019) Image Quality As- sessment through FSIM, SSIM, MSE and Quality is a very important parameter for all objects and their functionalities. PSNR—A Comparative Study. Journal of In image-based object recognition, image quality is a prime criterion. For au- Computer and Communications, 7, 8-18. thentic image quality evaluation, ground truth is required. But in practice, it https://doi.org/10.4236/jcc.2019.73002 is very difficult to find the ground truth. Usually, image quality is being as- Received: January 30, 2019 sessed by full reference metrics, like MSE (Mean Square Error) and PSNR Accepted: March 1, 2019 (Peak Signal to Noise Ratio). In contrast to MSE and PSNR, recently, two Published: March 4, 2019 more full reference metrics SSIM (Structured Similarity Indexing Method) Copyright © 2019 by author(s) and and FSIM (Feature Similarity Indexing Method) are developed with a view to Scientific Research Publishing Inc. compare the structural and feature similarity measures between restored and This work is licensed under the Creative original objects on the basis of perception. This paper is mainly stressed on Commons Attribution International License (CC BY 4.0). -

Video Quality Assessment: Subjective Testing of Entertainment Scenes Margaret H
1 Video Quality Assessment: Subjective testing of entertainment scenes Margaret H. Pinson, Lucjan Janowski, and Zdzisław Papir This article describes how to perform a video quality subjective test. For companies, these tests can greatly facilitate video product development; for universities, removing perceived barriers to conducting such tests allows expanded research opportunities. This tutorial assumes no prior knowledge and focuses on proven techniques. (Certain commercial equipment, materials, and/or programs are identified in this article to adequately specify the experimental procedure. In no case does such identification imply recommendation or endorsement by the National Telecommunications and Information Administration, nor does it imply that the program or equipment identified is necessarily the best available for this application.) Video is a booming industry: content is embedded on many Web sites, delivered over the Internet, and streamed to mobile devices. Cisco statistics indicate that video exceeded 50% of total mobile traffic for the first time in 2012, and predicts that two-thirds of the world’s mobile data traffic will be video by 2017 [1]. Each company must make a strategic decision on the correct balance between delivery cost and user experience. This decision can be made by the engineers designing the service or, for increased accuracy, by consulting users [2]. Video quality assessment requires a combined approach that includes objective metrics, subjective testing, and live video monitoring. Subjective testing is a critical step to ensuring success in operational management and new product development. Carefully conducted video quality subjective tests are extremely reliable and repeatable, as is shown in Section 8 of [3]. This article provides an approachable tutorial on how to conduct a subjective video quality experiment. -

Revisiting Image Vignetting Correction by Constrained Minimization of Log-Intensity Entropy
Revisiting Image Vignetting Correction by Constrained Minimization of log-Intensity Entropy Laura Lopez-Fuentes, Gabriel Oliver, and Sebastia Massanet Dept. Mathematics and Computer Science, University of the Balearic Islands Crta. Valldemossa km. 7,5, E-07122 Palma de Mallorca, Spain [email protected],[email protected],[email protected] Abstract. The correction of the vignetting effect in digital images is a key pre-processing step in several computer vision applications. In this paper, some corrections and improvements to the image vignetting cor- rection algorithm based on the minimization of the log-intensity entropy of the image are proposed. In particular, the new algorithm is able to deal with images with a vignetting that is not in the center of the image through the search of the optical center of the image. The experimen- tal results show that this new version outperforms notably the original algorithm both from the qualitative and the quantitative point of view. The quantitative measures are obtained using an image database with images to which artificial vignetting has been added. Keywords: Vignetting, entropy, optical center, gain function. 1 Introduction Vignetting is an undesirable effect in digital images which needs to be corrected as a pre-processing step in computer vision applications. This effect is based on the radial fall off of brightness away from the optical center of the image. Specially, those applications which rely on consistent intensity measurements of a scene are highly affected by the existence of vignetting. For example, image mosaicking, stereo matching and image segmentation, among many others, are applications where the results are notably improved if some previous vignetting correction algorithm is applied to the original image. -

Comparison of Color Demosaicing Methods Olivier Losson, Ludovic Macaire, Yanqin Yang
Comparison of color demosaicing methods Olivier Losson, Ludovic Macaire, Yanqin Yang To cite this version: Olivier Losson, Ludovic Macaire, Yanqin Yang. Comparison of color demosaicing methods. Advances in Imaging and Electron Physics, Elsevier, 2010, 162, pp.173-265. 10.1016/S1076-5670(10)62005-8. hal-00683233 HAL Id: hal-00683233 https://hal.archives-ouvertes.fr/hal-00683233 Submitted on 28 Mar 2012 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Comparison of color demosaicing methods a, a a O. Losson ∗, L. Macaire , Y. Yang a Laboratoire LAGIS UMR CNRS 8146 – Bâtiment P2 Université Lille1 – Sciences et Technologies, 59655 Villeneuve d’Ascq Cedex, France Keywords: Demosaicing, Color image, Quality evaluation, Comparison criteria 1. Introduction Today, the majority of color cameras are equipped with a single CCD (Charge- Coupled Device) sensor. The surface of such a sensor is covered by a color filter array (CFA), which consists in a mosaic of spectrally selective filters, so that each CCD ele- ment samples only one of the three color components Red (R), Green (G) or Blue (B). The Bayer CFA is the most widely used one to provide the CFA image where each pixel is characterized by only one single color component. -

A High Image Quality Fully Integrated CMOS Image Sensor
IS&T's 1999 PICS Conference A High Image Quality Fully Integrated CMOS Image Sensor Matt Borg, Ray Mentzer and Kalwant Singh Hewlett-Packard Company, Corvallis, Oregon Abstract ture applications. In this first offering, the primary design em- phasis was on delivering the highest possible image quality We describe the feature set and noise characteristics of a pro- while simultaneously providing a flexible feature set for ease duction quality photodiode-based CMOS active pixel image of use. The first section describes the chip architecture with sensor IC fabricated in Hewlett Packard’s standard 0.5 mi- particular emphasis on the analog signal path. The second cron and 3.3V mixed-signal process. It features an integrated section describes the details of the pixel operation, design timing controller, voltage reference generators, programmable and performance. The third section describes operating modes. gain amplifiers and 10-bit analog-to-digital converters. It of- The fourth section describes parameters important to image fers excellent blooming-resistant image quality and dissipates quality and provides corresponding measurement results. The 125mW (nominal) for a VGA(640X480) resolution image at fifth section describes the integrated feature set. Conclusions 15 frames/sec. Integrated features that simplify overall sys- are presented in the final section. tem design include random access and windowing capabili- ties, subsampling modes, still image capabilities and sepa- Chip Description rate gain control for red, green and blue pixels. HP’s unique CMOS process features a low dark current of 100pA/cm2. We also describe the low fixed-pattern and temporal noise characteristics of the image sensor. -

Orbs in Pictures of the Sun
Orbs in pictures of the sun Continue The backscatter of the camera's flash of motes of dust causes unfocused orb-shaped photographic artifacts. In photography, the backscatter (also called near-camera reflection[1]) is an optical phenomenon that results in typically circular artifacts on an image, due to the camera's flash reflected from unfocused motes of dust, water droplets, or other particles in the air or water. It is especially common with modern compact and ultra-compact digital cameras. [3] [3] A hypothetical underwater instance with two conditions in which circular photographic artifacts are probable (A) and unlikely (B), depending on whether the aspect of particles facing the lens directly reflects the flash, as shown. Elements do not appear to scale. Caused by the backscatter of light of unfocused particles, these artifacts are also sometimes referred to as orbs, citing a common paranormal claim. Some appear with tracks, suggesting movement. [4] Cause circular unfocused visual artifacts caused by raindrops. Additional information: Light scattering of particles and Defocus-aberration Backscatter usually occurs in low light scenes when the camera flash is used. Cases include night time and underwater photography, when a bright light source and reflective unfocused particles are close to the camera. [1] Light appears much brighter much near the source due to the inverse-square law, which says light intensity is inversely proportional to the square of the distance from the source. [5] The artifact may be the result of backscatter or retroreflection of the light from airborne solid particles, such as dust or pollen, or liquid droplets, especially rain or fog. -

Doctoral Thesis High Definition Video Quality Assessment Metric Built
UNIVERSIDAD POLITÉCNICA DE MADRID ESCUELA TÉCNICA SUPERIOR DE INGENIEROS DE TELECOMUNICACIÓN Doctoral Thesis High definition video quality assessment metric built upon full reference ratios DAVID JIMÉNEZ BERMEJO Ingeniero de Telecomunicación 2012 SIGNALS, SYSTEMS AND RADIOCOMMUNICATIONS DEPARTMENT ESCUELA TÉCNICA SUPERIOR DE INGENIEROS DE TELECOMUNICACIÓN DOCTORAL THESIS High definition video quality assessment metric built upon full reference ratios Author: David Jiménez Bermejo Ingeniero de Telecomunicación Director: José Manuel Menéndez García Dr. Ingeniero de Telecomunicación April 2012 DEPARTAMENTO DE SEÑALES, SISTEMAS Y RADIOCOMUNICACIONES ii ESCUELA TÉCNICA SUPERIOR DE INGENIEROS DE TELECOMUNICACIÓN TESIS DOCTORAL High definition video quality assessment metric built upon full reference ratios Autor: David Jiménez Bermejo Ingeniero de Telecomunicación Director: José Manuel Menéndez García Dr. Ingeniero de Telecomunicación Abril 2012 iii UNIVERSIDAD POLITÉCNICA DE MADRID ESCUELA TÉCNICA SUPERIOR DE INGENIEROS DE TELECOMUNICACIÓN DEPARTAMENTO DE SEÑALES, SISTEMAS Y RADIOCOMUNICACIONES “High definition video quality assessment metric built upon full reference ratios” Autor: David Jiménez Bermejo Director: Dr. José Manuel Menéndez García El tribunal nombrado para juzgar la tesis arriba indicada el día de de 2012, compuesto de los siguientes doctores: Presidente: _______________________________________________________ Vocal: ___________________________________________________________ Vocal: ___________________________________________________________ -

The Essential A-Z of Photography Slang Artifact a Loose Term To
The essential A-Z of photography slang Artifact A loose term to describe an element that degrades picture quality. Anything from the blockiness that can occur when pictures are heavily compressed as JPEGs, to the distortion to pictures that occurs with heavy manipulation – even the effect you see with lens flare. ATGNI All The Gear, No Idea. A photographer who has lots of camera equipment but doesn’t know what half of it does. A bit of an Uncle Bob, in fact. BIF A rare acronym that you’ll only see floating around bird photography forums (download our free bird photography cheat sheet). There’s a clue right there: BIF stands for Bird in Flight, and is usually brought up during lengthy technical discussions about autofocus point selection and focus modes. Bigma The Sigma 50-500mm f/4-6.3 lens earned the nickname ‘Bigma’ thanks to its considerable 10x zoom range and considerable proportions. Blown out Bright areas in a photo that are overexposed are said to be blown out. They won’t hold any detail and will be bleached white. Bokeh Pronounced ‘boh-kay’, this term is derived from the Japanese word for ‘blur’ and is used to describe the aesthetic quality of the blur in out- of-focus areas of a picture. The faster the lens, and the more aperture blades it has, the smoother the blur tends to be. Chimping The act of looking at pictures on the back of the camera as soon as you’ve taken them, usually accompanied by lots of ‘ooh-ooh-oohing’, hence the name. -

Assignment 4: Raw Material
Computer Science E-7: Exposing Digital Photography Harvard Extension School Fall 2010 Raw Material Assignment #4. Due 5:30PM on Tuesday, November 23, 2010. Part I. Pick Your Brain! (40 points) Type your answers for the following questions in a word processor; we will accept Word Documents (.doc, .docx), PDF documents (.pdf), or plaintext files (.txt, .rtf). Do not submit your answers for this part to Flickr. Instead, before the due date, attach the file to an email and send it to us at this address: ! [email protected] 1. (2 points) What are two advantages of JPEG over RAW? 2. (2 points) Which color space should you employ for general use? 3. (2 points) Why is white balance measured in degrees Kelvin? 4. (2 points) List two reasons why batteries in digital SLRs tend to last longer than those in compact digital cameras. 5. (2 points) Why is calibrating your monitor important? 6. (3 points) What is a tone curve and why is it necessary? 7. (3 points) Many digital cameras are advertised as having a crop factor. What does this mean? What are some of its advantages and disadvantages? 8. (3 points) Assume you have two sources of light: incandescent light at an approximate color temperature of 3000 K, and the sun with an approximate color temperature of 6000 K. Which source produces warmer tones? If you take two properly-exposed photographs of a white sheet of paper, one photo in each scene, with your camera set at a white balance of 4500 K, in which photo would the paper appear warmer? 1 of 6 Computer Science E-7: Exposing Digital Photography Harvard Extension School Fall 2010 9.