IDOL Keyview Filter SDK 12.7 .NET Programming Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
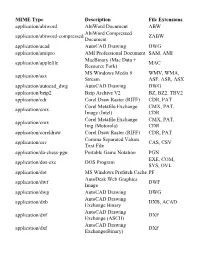
MIME Type Description File Extensions Application/Abiword
MIME Type Description File Extensions application/abiword AbiWord Document ABW AbiWord Compressed application/abiword-compressed ZABW Document application/acad AutoCAD Drawing DWG application/amipro AMI Professional Document SAM, AMI MacBinary (Mac Data + application/applefile MAC Resource Fork) MS Windows Media 9 WMV, WMA, application/asx Stream ASF, ASR, ASX application/autocad_dwg AutoCAD Drawing DWG application/bzip2 Bzip Archive V2 BZ, BZ2, TBV2 application/cdr Corel Draw Raster (RIFF) CDR, PAT Corel Metafile Exchange CMX, PAT, application/cmx Image (Intel) CDR Corel Metafile Exchange CMX, PAT, application/cmx Img (Motorola) CDR application/coreldraw Corel Draw Raster (RIFF) CDR, PAT Comma Separated Values application/csv CAS, CSV Text File application/da-chess-pgn Portable Game Notation PGN EXE, COM, application/dos-exe DOS Program SYS, OVL application/dot MS Windows Prefetch Cache PF AutoDesk Web Graphics application/dwf DWF Image application/dwg AutoCAD Drawing DWG AutoCAD Drawing application/dxb DXB, ACAD Exchange Binary AutoCAD Drawing application/dxf DXF Exchange (ASCII) AutoCAD Drawing application/dxf DXF Exchange(Binary) EMF, TMP, EMF, TMP, application/emf Windows Enhanced Metafile WMF application/envoy Envoy Document EVY, ENV Comma Separated Values application/excel CAS, CSV Text File MS Excel XLS, XLA, application/excel Worksheet/Add-In/Template XLT, XLB EXE, COM, application/exe DOS Program SYS, OVL EXE, VXD, application/exe MS Windows Driver (16 bit) SYS, DRV, 386 MS Windows Program (16 application/exe EXE, MOD, BIN bit) -

Compress/Decompress Encrypt/Decrypt
Windows Compress/Decompress WinZip Standard WinZip Pro Compressed Folders Zip and unzip files instantly with 64-bit, best-in-class software ENHANCED! Compress MP3 files by 15 - 20 % on average Open and extract Zipx, RAR, 7Z, LHA, BZ2, IMG, ISO and all other major compression file formats Open more files types as a Zip, including DOCX, XLSX, PPTX, XPS, ODT, ODS, ODP, ODG,WMZ, WSZ, YFS, XPI, XAP, CRX, EPUB, and C4Z Use the super picker to unzip locally or to the cloud Open CAB, Zip and Zip 2.0 Methods Convert other major compressed file formats to Zip format Apply 'Best Compression' method to maximize efficiency automatically based on file type Reduce JPEG image files by 20 - 25% with no loss of photo quality or data integrity Compress using BZip2, LZMA, PPMD and Enhanced Deflate methods Compress using Zip 2.0 compatible methods 'Auto Open' a zipped Microsoft Office file by simply double-clicking the Zip file icon Employ advanced 'Unzip and Try' functionality to review interrelated components contained within a Zip file (such as an HTML page and its associated graphics). Windows Encrypt/Decrypt WinZip Standard WinZip Pro Compressed Folders Apply encryption and conversion options, including PDF conversion, watermarking and photo resizing, before, during or after creating your zip Apply separate conversion options to individual files in your zip Take advantage of hardware support in certain Intel-based computers for even faster AES encryption Administrative lockdown of encryption methods and password policies Check 'Encrypt' to password protect your files using banking-level encryption and keep them completely secure Secure sensitive data with strong, FIPS-197 certified AES encryption (128- and 256- bit) Auto-wipe ('shred') temporarily extracted copies of encrypted files using the U.S. -

Portable Paper
Volume 2, Number 2 The HP Portable/Portable Plus Users Newsletter March / April, 1987 PortableTHE Paper Special Feature: Database Software Management Publisher's Message ...................... I Special Feature: Database Management Letters Software Charge Portable Off Car Lighter .............. 2 Introduction ............................ 16 Portable To Macintosh ..................... 4 Database Management Product Summary ...... 16 110% Lotus As A Database Manager . 18 New HP Portable? ......................... '; Executive Card Manager ................... 18 Updates on Personalized Software Products ..... 5 dBASE II ............................... 22 Buying Disks ............................ 6 Turbo Pascal Toolbox ..................... 2-} X-rays And The Portable .................... 6 PC File III .............................. 24 More Info On Backlighting ................. 33 T/Master ............................... 25 HP-IL Link Program ........ .............. 33 Condor Junior .......................... 25 Foundations Conclusion ............................. 25 Built-in Self-Test .......................... 8 PLUS Notes Six Ways To Restart Your Portable ............. 8 Lotus 2.01 and HAL ...................... 25 Getting Program To Run . ..... 8 B Drive RAM Cards With Greater Capacity ........... 26 EPROM Update .......................... 26 DOS AID Software Drawer & SPC ................ 27 Bypassing PAM ............................ 11 1erminal Through The Looking Glass ............ 27 CompuServe Autologon, Uploading Revisited .... -

Interactive SVG with Jsxgraph
Interactive SVG with JSXGraph Bianca Valentin and Michael Gerhäuser August 30, 2009 Contents 1 Introduction2 2 Mathematics3 2.1 JSXGraph as a web viewer for dynamic geometry software . .3 2.2 Currently supported file formats . .4 2.3 Constructing from scratch . .4 2.4 Calculus . .6 3 Turtle graphics8 3.1 Turtle graphics in mathematical modelling . .8 3.2 Drawing with turtle graphics . .8 4 Charts 10 5 JSXGraph as a front end to server side applications 12 5.1 Just AJAX . 12 5.2 JXG.Server . 14 6 Plugins for integration in other web applications 14 7 Implementation details 15 7.1 Cross-browser development . 15 7.2 SVG vs. VML . 15 7.3 HTML elements . 17 7.4 Speed improvements . 17 7.4.1 Avoid DOM accesses with getElementById() . 17 7.4.2 Suspend the update of SVG nodes . 17 7.4.3 Use memoizers . 18 7.4.4 Distinguish mouse move and mouse up events . 18 7.4.5 Reduce the download and initialization time . 18 7.4.6 Use closures . 18 7.4.7 An Internet Explorer trick . 19 1 8 References 20 8.1 References . 20 8.2 Websites . 20 List of Figures 1 The Euler Line . .6 2 Sine with it’s derivative and riemann sum. .7 3 SVG written by a turtle. Result of . .9 4 The Koch curve with recursion level 7 . 10 5 A pie chart on the left hand side and an interactive bar chart together with a static line chart on the right hand side. 11 6 Scheme showing the renderer split in JSXGraph . -

Metadefender Core V4.12.2
MetaDefender Core v4.12.2 © 2018 OPSWAT, Inc. All rights reserved. OPSWAT®, MetadefenderTM and the OPSWAT logo are trademarks of OPSWAT, Inc. All other trademarks, trade names, service marks, service names, and images mentioned and/or used herein belong to their respective owners. Table of Contents About This Guide 13 Key Features of Metadefender Core 14 1. Quick Start with Metadefender Core 15 1.1. Installation 15 Operating system invariant initial steps 15 Basic setup 16 1.1.1. Configuration wizard 16 1.2. License Activation 21 1.3. Scan Files with Metadefender Core 21 2. Installing or Upgrading Metadefender Core 22 2.1. Recommended System Requirements 22 System Requirements For Server 22 Browser Requirements for the Metadefender Core Management Console 24 2.2. Installing Metadefender 25 Installation 25 Installation notes 25 2.2.1. Installing Metadefender Core using command line 26 2.2.2. Installing Metadefender Core using the Install Wizard 27 2.3. Upgrading MetaDefender Core 27 Upgrading from MetaDefender Core 3.x 27 Upgrading from MetaDefender Core 4.x 28 2.4. Metadefender Core Licensing 28 2.4.1. Activating Metadefender Licenses 28 2.4.2. Checking Your Metadefender Core License 35 2.5. Performance and Load Estimation 36 What to know before reading the results: Some factors that affect performance 36 How test results are calculated 37 Test Reports 37 Performance Report - Multi-Scanning On Linux 37 Performance Report - Multi-Scanning On Windows 41 2.6. Special installation options 46 Use RAMDISK for the tempdirectory 46 3. Configuring Metadefender Core 50 3.1. Management Console 50 3.2. -

Windows NT® 4 for Dummies® File:///P|/VSCAN/TOSCAN/MT/NT4DUM/NT4.HTM
Table of contents Windows NT® 4 For Dummies® file:///P|/VSCAN/TOSCAN/MT/NT4DUM/NT4.HTM Table of Contents Windows NT® 4 For Dummies® Introduction About This Book How to Use This Book And What about You? How This Book Is Organized Part I: Introducing Windows NT (Bare-Bones Stuff) Part II: Making Windows NT Do Something Part III: Using Windows NT Applications Part IV: Been There, Done That: Quick References for Moving to Windows NT Part V: Getting Help Part VI: The Part of Tens Icons Used in This Book Where to Go from Here Part I: Intro to Windows NT (Bare Bones Stuff) Chapter 1: What Is Windows NT? What Is This "Windows" Stuff, Anyway? What Does Windows NT 4 Do? Why Should I Bother Using Windows NT? Will I Like Windows NT 4 Better than Windows NT 3.51? What's the Difference between Windows NT Workstation and Windows NT Server? Bracing Yourself for Windows NT 4 Chapter 2: Boring Information, Bothersome Computer Parts The Computer Microprocessor Floppy Disks, Compact Discs (CDs), and Disk Drives Floppy disk flipping What disk drives does Windows NT like? What does "write-protected" mean? Driving with compact discs The Mouse and That Double-Click Stuff Cards and Monitors Keyboards Groups of keys More key principles Print Screen: the one fun, weird code key Modems Printers Networks Sound Cards (Disgusting Bioactive Noises) Parts Required by Windows NT Chapter 3: Windows NT Stuff Everybody Thinks You Already Know Backing Up Your Work Clicking 1 of 9 07/14/99 08:29:14 Table of contents Windows NT® 4 For Dummies® file:///P|/VSCAN/TOSCAN/MT/NT4DUM/NT4.HTM -

OS 386 Multiuser/Multitasking Operating System
OS 386 Multiuser/Multitasking Operating System REFERENCE GUIDE [Q] DIGITAL RESEARCH@ os REFERENCE GUIDE [jill DIGITAL RESEARCH~ COPYRIGHT Copyright © 1987 Digital Research Inc. All rights reserved. No part of this publication may be reproduced, transcribed, stored in a retrieval system, or translated into any language or computer language, in any form or by any means, electronic, mechanical, magnetic, optical, chemical, manual or otherwise without the prior written permission of Digital Research Inc, 60 Garden Court, Box DRI, Monterey, California 93942 DISCLAIMER DIGITAL RESEARCH MAKES NO REPRESENTATIONS OR WARRANTIES WITH RESPECT TO THE CONTENTS HEREOF AND SPECIFICALLY DISCLAIMS ANY IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR ANY PARTICULAR PURPOSE. Further Digital Research Inc. reserves the right to revise this publication and to make changes from time to time in the content hereof without obligation of Digital Research Inc to notify any person of such revision or changes. NOTICE TO USER This manual should not be construed as any representation or warranty with respect to the software named herein. Occasionally changes or variations exist in the software that are not reflected in the manual. Generally, if such changes or variations are known to exist and to affect the product significantly, a release note or READ.ME file accompanies the manual and the distribution disks. In that event, be sure to read the release note or READ.ME file before using the product. ii TRADEMARKS Digital Research and its logo, CP/M, and CP/M-86 are registered trademarks of Digital Research Inc. Cardfile, Concurrent, Concurrent DOS 386, Concurrent DOS XM, DR EDIX, DOS Plus and MP/M-86 are trademarks of Digital Research Inc. -

Vcube User Manual
Table of Contents Table of Contents Welcome 1 What's New in VCube 2? 2 VCube Overview 5 How to Update 6 VCube User Interface 7 Tool and Transport Bars 11 Tool Bar 12 Transport Bar 16 Quick Settings for SD and HD Video Formats 19 Quick Settings for SD 21 Quick Settings for HD 23 Control Pages 25 Files 26 VCube Compositions 29 OMF Compositions 32 AAF and Apple XML Compositions 34 Media Files 36 Import Composition and Export Changes 38 Import Layer 39 Convert Still Images 40 Locators 42 View 44 Clips Information 45 Shortcuts 49 Workspace 50 ii Table of Contents Edit 52 Main 53 Clips 54 Layers 56 Tracks 58 Settings 59 Presets 60 Formats & Synchro 62 Video I/O 67 Xena LS Plug-in 68 Xena LH Plug-in 70 Xena 2 Plug-in 72 Overlay 74 Preview 76 Composition 78 Disk & Network Cache Buffers 81 User Interface 82 Isis 83 Encryption 84 Media Settings 90 Timeline 91 Video Engine 92 Output View 93 Script View 95 Recording and Editing 96 Recording 97 Editing 103 Timeline 104 Editing Functions 106 Layer Controls 110 iii Table of Contents Motion Rectangles (PiP) 111 Selections and Groups 114 Watermark and Text 115 Watermark 116 Text Clip 117 Utility Clips 119 Countdown Clip 120 Wipe Clip 122 Video Test Patern Clip 123 Audio Tone Clip 124 Conforming and Reconforming 125 Conversions 134 Export 135 Convert Media Files 136 Render 140 Import Images Sequence 144 Media Wrapper 146 Frame Rate Management 147 Using the QuickTime File Format 148 Using the MXF File Format 150 Using the MPEG Codec 151 Basic Settings 153 Video Settings 154 Advanced Video Settings 157 Audio Settings 164 Multiplexer Settings 167 Synchronization 171 Connections for synchronization 174 iv Table of Contents The USB Sync Board Oprtion 175 USB Sync Board Installation 176 Specific Control Panels 177 Virtual Transport 180 Network 183 VCube Chasing Pyramix through Virtual Transport. -

Developing High-Order Mathematical Thinking Competency on High School Students’ Through Geogebra-Assisted Blended Learning
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by International Institute for Science, Technology and Education (IISTE): E-Journals Mathematical Theory and Modeling www.iiste.org ISSN 2224-5804 (Paper) ISSN 2225-0522 (Online) Vol.4, No.6, 2014 Developing High-Order Mathematical Thinking Competency on High School Students’ Through GeoGebra-Assisted Blended Learning Nanang Supriadi1* Yaya S. Kusumah2 Jozua Sabandar2 Jarnawi D. Afgani2 1. Raden Intan State Institute for Islamic Studies, Jl. Letkol. H. Endro Suratmin, Sukarame, Bandar Lampung, Lampung 35131, Indonesia 2. Indonesia University of Education, Jl. Dr Setiabudi No. 229, Bandung, West Java,40154, Indonesia *E-mail of the corresponding author: [email protected] ABSTRACT Blended Learning has received considerable attention in the field of mathematics education in recent years. This study combines online learning and face-to-face based learning. Blended Learning is based on some of the weaknesses found in online learning. In Blended Learning, Online learning is not just the learning that collects teaching materials, assignments, exercises, tests, and results of students’ works. It also has to be an interesting and attractive learning so that students’ will have better understanding on learning objectives. One of the tools for developing interesting and attractive online learning process is an open source software called GeoGebra. Blended Learning has very good quality when applied in developing students’ High-Order Mathematical Thinking Competency (HOMTC) as it is evident from previous researches. This study was an experiment based on pretest-posttest control group aiming to examine the influence of Blended Learning and students’ initial mathematical ability on students’ achievement and enhancement of HOMTC consisting of some aspects such as mathematical problem solving, mathematical communication, mathematical reasoning, and mathematical connections. -

Symantec Web Security Service Policy Guide
Web Security Service Policy Guide Revision: NOV.07.2020 Symantec Web Security Service/Page 2 Policy Guide/Page 3 Copyrights Broadcom, the pulse logo, Connecting everything, and Symantec are among the trademarks of Broadcom. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries. Copyright © 2020 Broadcom. All Rights Reserved. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries. For more information, please visit www.broadcom.com. Broadcom reserves the right to make changes without further notice to any products or data herein to improve reliability, function, or design. Information furnished by Broadcom is believed to be accurate and reliable. However, Broadcom does not assume any liability arising out of the application or use of this information, nor the application or use of any product or circuit described herein, neither does it convey any license under its patent rights nor the rights of others. Policy Guide/Page 4 Symantec WSS Policy Guide The Symantec Web Security Service solutions provide real-time protection against web-borne threats. As a cloud-based product, the Web Security Service leverages Symantec's proven security technology, including the WebPulse™ cloud community. With extensive web application controls and detailed reporting features, IT administrators can use the Web Security Service to create and enforce granular policies that are applied to all covered users, including fixed locations and roaming users. If the WSS is the body, then the policy engine is the brain. While the WSS by default provides malware protection (blocks four categories: Phishing, Proxy Avoidance, Spyware Effects/Privacy Concerns, and Spyware/Malware Sources), the additional policy rules and options you create dictate exactly what content your employees can and cannot access—from global allows/denials to individual users at specific times from specific locations. -
![Archive and Compressed [Edit]](https://docslib.b-cdn.net/cover/8796/archive-and-compressed-edit-1288796.webp)
Archive and Compressed [Edit]
Archive and compressed [edit] Main article: List of archive formats • .?Q? – files compressed by the SQ program • 7z – 7-Zip compressed file • AAC – Advanced Audio Coding • ace – ACE compressed file • ALZ – ALZip compressed file • APK – Applications installable on Android • AT3 – Sony's UMD Data compression • .bke – BackupEarth.com Data compression • ARC • ARJ – ARJ compressed file • BA – Scifer Archive (.ba), Scifer External Archive Type • big – Special file compression format used by Electronic Arts for compressing the data for many of EA's games • BIK (.bik) – Bink Video file. A video compression system developed by RAD Game Tools • BKF (.bkf) – Microsoft backup created by NTBACKUP.EXE • bzip2 – (.bz2) • bld - Skyscraper Simulator Building • c4 – JEDMICS image files, a DOD system • cab – Microsoft Cabinet • cals – JEDMICS image files, a DOD system • cpt/sea – Compact Pro (Macintosh) • DAA – Closed-format, Windows-only compressed disk image • deb – Debian Linux install package • DMG – an Apple compressed/encrypted format • DDZ – a file which can only be used by the "daydreamer engine" created by "fever-dreamer", a program similar to RAGS, it's mainly used to make somewhat short games. • DPE – Package of AVE documents made with Aquafadas digital publishing tools. • EEA – An encrypted CAB, ostensibly for protecting email attachments • .egg – Alzip Egg Edition compressed file • EGT (.egt) – EGT Universal Document also used to create compressed cabinet files replaces .ecab • ECAB (.ECAB, .ezip) – EGT Compressed Folder used in advanced systems to compress entire system folders, replaced by EGT Universal Document • ESS (.ess) – EGT SmartSense File, detects files compressed using the EGT compression system. • GHO (.gho, .ghs) – Norton Ghost • gzip (.gz) – Compressed file • IPG (.ipg) – Format in which Apple Inc. -

Forcepoint DLP Supported File Formats and Size Limits
Forcepoint DLP Supported File Formats and Size Limits Supported File Formats and Size Limits | Forcepoint DLP | v8.8.1 This article provides a list of the file formats that can be analyzed by Forcepoint DLP, file formats from which content and meta data can be extracted, and the file size limits for network, endpoint, and discovery functions. See: ● Supported File Formats ● File Size Limits © 2021 Forcepoint LLC Supported File Formats Supported File Formats and Size Limits | Forcepoint DLP | v8.8.1 The following tables lists the file formats supported by Forcepoint DLP. File formats are in alphabetical order by format group. ● Archive For mats, page 3 ● Backup Formats, page 7 ● Business Intelligence (BI) and Analysis Formats, page 8 ● Computer-Aided Design Formats, page 9 ● Cryptography Formats, page 12 ● Database Formats, page 14 ● Desktop publishing formats, page 16 ● eBook/Audio book formats, page 17 ● Executable formats, page 18 ● Font formats, page 20 ● Graphics formats - general, page 21 ● Graphics formats - vector graphics, page 26 ● Library formats, page 29 ● Log formats, page 30 ● Mail formats, page 31 ● Multimedia formats, page 32 ● Object formats, page 37 ● Presentation formats, page 38 ● Project management formats, page 40 ● Spreadsheet formats, page 41 ● Text and markup formats, page 43 ● Word processing formats, page 45 ● Miscellaneous formats, page 53 Supported file formats are added and updated frequently. Key to support tables Symbol Description Y The format is supported N The format is not supported P Partial metadata