LINUX: Rute User's Tutorial and Exposition
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Opengear User Manual 4.4.Pdf
User Manual ACM5000 Remote Site Managers ACM5500 Management Gateways ACM7000 Resilience Gateways IM7200 & IM4200 Infrastructure Managers CM7100 Console Servers Revision 4.32 2019-4-10 Table of Contents Safety Please take care to follow the safety precautions below when installing and operating the console server: - Do not remove the metal covers. There are no operator serviceable components inside. Opening or removing the cover may expose you to dangerous voltage which may cause fire or electric shock. Refer all service to Opengear qualified personnel. - To avoid electric shock the power cord protective grounding conductor must be connected through to ground. - Always pull on the plug, not the cable, when disconnecting the power cord from the socket. Do not connect or disconnect the console server during an electrical storm. Also it is recommended you use a surge suppressor or UPS to protect the equipment from transients. FCC Warning Statement This device complies with Part 15 of the FCC rules. Operation of this device is subject to the following conditions: (1) This device may not cause harmful interference, and (2) this device must accept any interference that may cause undesired operation. Proper back-up systems and necessary safety devices should be utilized to protect against injury, death or property damage due to system failure. Such protection is the responsibility of the user. This console server device is not approved for use as a life-support or medical system. Any changes or modifications made to this console server device without the explicit approval or consent of Opengear will void Opengear of any liability or responsibility of injury or loss caused by any malfunction. -

Ubuntu Kung Fu
Prepared exclusively for Alison Tyler Download at Boykma.Com What readers are saying about Ubuntu Kung Fu Ubuntu Kung Fu is excellent. The tips are fun and the hope of discov- ering hidden gems makes it a worthwhile task. John Southern Former editor of Linux Magazine I enjoyed Ubuntu Kung Fu and learned some new things. I would rec- ommend this book—nice tips and a lot of fun to be had. Carthik Sharma Creator of the Ubuntu Blog (http://ubuntu.wordpress.com) Wow! There are some great tips here! I have used Ubuntu since April 2005, starting with version 5.04. I found much in this book to inspire me and to teach me, and it answered lingering questions I didn’t know I had. The book is a good resource that I will gladly recommend to both newcomers and veteran users. Matthew Helmke Administrator, Ubuntu Forums Ubuntu Kung Fu is a fantastic compendium of useful, uncommon Ubuntu knowledge. Eric Hewitt Consultant, LiveLogic, LLC Prepared exclusively for Alison Tyler Download at Boykma.Com Ubuntu Kung Fu Tips, Tricks, Hints, and Hacks Keir Thomas The Pragmatic Bookshelf Raleigh, North Carolina Dallas, Texas Prepared exclusively for Alison Tyler Download at Boykma.Com Many of the designations used by manufacturers and sellers to distinguish their prod- ucts are claimed as trademarks. Where those designations appear in this book, and The Pragmatic Programmers, LLC was aware of a trademark claim, the designations have been printed in initial capital letters or in all capitals. The Pragmatic Starter Kit, The Pragmatic Programmer, Pragmatic Programming, Pragmatic Bookshelf and the linking g device are trademarks of The Pragmatic Programmers, LLC. -
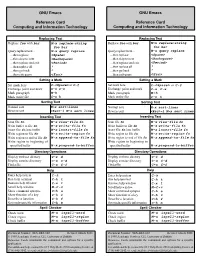
GNU Emacs GNU Emacs
GNU Emacs GNU Emacs Reference Card Reference Card Computing and Information Technology Computing and Information Technology Replacing Text Replacing Text Replace foo with bar M-x replace-string Replace foo with bar M-x replace-string foo bar foo bar Query replacement M-x query replace Query replacement M-x query replace then replace <Space> then replace <Space> then skip to next <Backspace> then skip to next <Backspace> then replace and exit <Period> then replace and exit <Period> then replace all ! then replace all ! then go back ^ then go back ^ then exit query <Esc> then exit query <Esc> Setting a Mark Setting a Mark Set mark here C-<Space> or C-@ Set mark here C-<Space> or C-@ Exchange point and mark C-x C-x Exchange point and mark C-x C-x Mark paragraph M-h Mark paragraph M-h Mark entire file C-x h Mark entire file C-x h Sorting Text Sorting Text Normal sort M-x sort-lines Normal sort M-x sort-lines Reverse sort <Esc>-1 M-x sort lines Reverse sort <Esc>-1 M-x sort lines Inserting Text Inserting Text Scan file fn M-x view-file fn Scan file fn M-x view-file fn Write buffer to file fn M-x write-file fn Write buffer to file fn M-x write-file fn Insert file fn into buffer M-x insert-file fn Insert file fn into buffer M-x insert-file fn Write region to file fn M-x write-region fn Write region to file fn M-x write-region fn Write region to end of file fn M-x append-to-file fn Write region to end of file fn M-x append-to-file fn Write region to beginning of Write region to beginning to specified buffer M-x prepend-to-buffer specified buffer -

Prebrane Zo Stranky
Manuál pre začiatočníkov a používateľov Microsoft Windows Galadriel 1.7.4 Manuál je primárne tvorený pre Ubuntu 7.04 Feisty Fawn. Dá sa však použiť aj pre Kubuntu, Xubuntu, Edubuntu, Ubuntu Studio a neoficiálne distribúcie založené na Ubuntu. Pokryté verzie: 7.10, 7.04, 6.10, 6.06 a 5.10 (čiastočne) Vypracoval Stanislav Hoferek (ICQ# 258126362) s komunitou ľudí na stránkach: linuxos.sk kubuntu.sk ubuntu.wz.cz debian.nfo.sk root.cz 1 Začíname! 5 Pracovné prostredie 9 Live CD 1.1 Postup pre začiatočníkov 5.1 Programové vybavenie 9.1 Vysvetlenie 1.2 Zoznámenie s manuálom 5.1.1 Prvé kroky v Ubuntu 9.2 Prístup k internetu 1.3 Zoznámenie s Ubuntu 5.1.2 Základné programy 9.3 Pripojenie pevných diskov 1.3.1 Ubuntu, teší ma! 5.1.3 Prídavné programy 9.4 Výhody a nevýhody Live CD 1.3.2 Čo tu nájdem? 5.2 Nastavenie jazyka 9.5 Live CD v prostredí Windows 1.3.3 Root 5.3 Multimédia 9.6 Ad-Aware pod Live CD 1.4. Užitočné informácie 5.3.1 Audio a Video Strana 48 1.4.1 Odkazy 5.3.2 Úprava fotografii 1.4.2 Slovníček 5.4 Kancelária 10 FAQ 1.4.3 Ako Linux funguje? 5.4.1 OpenOffice.org 10 FAQ 1.4.4 Spúšťanie programov 5.4.2 PDF z obrázku Strana 50 1.5 Licencia 5.4.3 Ostatné Strana 2 5.5 Hry 11 Tipy a triky 5.6 Estetika 11.1 Všeobecné rady 2 Linux a Windows 5.7 Zavádzanie systému 11.2 Pokročilé prispôsobenie systému 2.1 Porovnanie OS 5.7.1 Zavádzač 11.3 Spustenie pri štarte 2.2 Náhrada Windows Programov 5.7.2 Prihlasovacie okno 11.4 ALT+F2 2.3 Formáty 5.7.3 Automatické prihlásenie 11.5 Windows XP plocha 2.4 Rozdiely v ovládaní 5.8 Napaľovanie v Linuxe Strana 55 2.5 Spustenie programov pre Windows 5.9 Klávesové skratky 2.6 Disky 5.10 Gconf-editor 12 Konfigurácia 2.7 Klávesnica Strana 27 12.1 Nástroje na úpravu konfigurákov Strana 12 12.2 Najdôležitejšie konf. -

Muuglines the Manitoba UNIX User Group Newsletter
MUUGLines The Manitoba UNIX User Group Newsletter Volume 28 No. 10, June 2016 Editor: Bradford C. Vokey Next Meeting: June 14th, 2016, )here to Find the Meeting 7:30 pm University of Winnipeg Room 1M28 Manitoba Hall Main Topic: Gentoo Eric Raine will be presenting on the Gentoo Linux Dist. Differ- ences in installation from Ubuntu will be covered. Also covered is how to configure installation of packages and update. entoo is a free operating s!stem based on either Linux or Free#$D that can be automaticall! optimi%ed and customized for just about any applic- ation or need. RTFM: Termina Control Commands Due to a recent influx of new and novice members 'revor Cordes will be doing an R'") instead of a daemon dash this month. The topic is something ever! *+,- user should master. terminal control commands (i.e.0 ^2 and ^L3 and rudimentar! job control. These little dual ke! presses will streamline !our terminal sessions and make you more efficient. 4ou5ll wonder how you ever got b! without them6 Door %rize'#( )eetings are held in the University of Winnipeg's 'his month we will be giving )anitoba Hall (marked “M” on the map30 along awa! the O8Reill! book #almoral Street south of Ellice Avenue. We can be "Using csh & tcsh"0 found in room 1)@A0 but may occasionall! get b! Paul Du#ois. relocated to nearb! rooms. If there is a change0 it should be conve!ed via a sign on the door to 1)@A. Type Less, Accomplish More. Doors are usuall! open b! 7.CC pm with the meeting starting at 7.DC pm. -

Emacspeak — the Complete Audio Desktop User Manual
Emacspeak | The Complete Audio Desktop User Manual T. V. Raman Last Updated: 19 November 2016 Copyright c 1994{2016 T. V. Raman. All Rights Reserved. Permission is granted to make and distribute verbatim copies of this manual without charge provided the copyright notice and this permission notice are preserved on all copies. Short Contents Emacspeak :::::::::::::::::::::::::::::::::::::::::::::: 1 1 Copyright ::::::::::::::::::::::::::::::::::::::::::: 2 2 Announcing Emacspeak Manual 2nd Edition As An Open Source Project ::::::::::::::::::::::::::::::::::::::::::::: 3 3 Background :::::::::::::::::::::::::::::::::::::::::: 4 4 Introduction ::::::::::::::::::::::::::::::::::::::::: 6 5 Installation Instructions :::::::::::::::::::::::::::::::: 7 6 Basic Usage. ::::::::::::::::::::::::::::::::::::::::: 9 7 The Emacspeak Audio Desktop. :::::::::::::::::::::::: 19 8 Voice Lock :::::::::::::::::::::::::::::::::::::::::: 22 9 Using Online Help With Emacspeak. :::::::::::::::::::: 24 10 Emacs Packages. ::::::::::::::::::::::::::::::::::::: 26 11 Running Terminal Based Applications. ::::::::::::::::::: 45 12 Emacspeak Commands And Options::::::::::::::::::::: 49 13 Emacspeak Keyboard Commands. :::::::::::::::::::::: 361 14 TTS Servers ::::::::::::::::::::::::::::::::::::::: 362 15 Acknowledgments.::::::::::::::::::::::::::::::::::: 366 16 Concept Index :::::::::::::::::::::::::::::::::::::: 367 17 Key Index ::::::::::::::::::::::::::::::::::::::::: 368 Table of Contents Emacspeak :::::::::::::::::::::::::::::::::::::::::: 1 1 Copyright ::::::::::::::::::::::::::::::::::::::: -

Unix/Linux Command Reference
Unix/Linux Command Reference .com File Commands System Info ls – directory listing date – show the current date and time ls -al – formatted listing with hidden files cal – show this month's calendar cd dir - change directory to dir uptime – show current uptime cd – change to home w – display who is online pwd – show current directory whoami – who you are logged in as mkdir dir – create a directory dir finger user – display information about user rm file – delete file uname -a – show kernel information rm -r dir – delete directory dir cat /proc/cpuinfo – cpu information rm -f file – force remove file cat /proc/meminfo – memory information rm -rf dir – force remove directory dir * man command – show the manual for command cp file1 file2 – copy file1 to file2 df – show disk usage cp -r dir1 dir2 – copy dir1 to dir2; create dir2 if it du – show directory space usage doesn't exist free – show memory and swap usage mv file1 file2 – rename or move file1 to file2 whereis app – show possible locations of app if file2 is an existing directory, moves file1 into which app – show which app will be run by default directory file2 ln -s file link – create symbolic link link to file Compression touch file – create or update file tar cf file.tar files – create a tar named cat > file – places standard input into file file.tar containing files more file – output the contents of file tar xf file.tar – extract the files from file.tar head file – output the first 10 lines of file tar czf file.tar.gz files – create a tar with tail file – output the last 10 lines -

Dig, a DNS Query Tool for Windows and Replacement for Nslookup 2008-04-15 15:29
dig, a DNS query tool for Windows and replacement for nslookup 2008-04-15 15:29 Disclaimer dig (dig for Windows ) (dig is a powerful tool to investigate [digging into] the DNS system) Source of the binary is from ftp.isc.org Manual Page of dig, in the cryptic Unix style, for reference only. (1) Download: Windows 2000 or Windows XP or Windows Vista ( dig version 9.3.2) Create a folder c:\dig Download this dig-files.zip and save it to c:\dig Use winzip or equivalent to extract the files in dig-files.zip to c:\dig Note: If msvcr70.dll already exists in %systemroot%\system32\ , then you can delete c:\dig\msvcr70.dll Note: Included in dig-files.zip is a command line whois, version 4.7.11: The canonical site of the whois source code is http://ftp.debian.org/debian/pool/main/w/whois/ The whois.exe file inside dig-files.zip is compiled using cygwin c++ compiler. (2) Do a file integrity check (why ? Because some virus checkers destroy dll files) Click Start.. Run ... type CMD (a black screen pops up) cd c:\dig sha1 * You should see some SHA1 hashes (in here, SHA1 hash is used as an integrity check, similar to checksums). Compare your hashes with the following table. SHA1 v1.0 [GPLed] by Stephan T. Lavavej, http://stl.caltech.edu 6CA70A2B 11026203 EABD7D65 4ADEFE3D 6C933EDA cygwin1.dll 57487BAE AA0EB284 8557B7CA 54ED9183 EAFC73FA dig.exe 97DBD755 D67A5829 C138A470 8BE7A4F2 6ED0894C host.exe D22E4B89 56E1831F F0F9D076 20EC19BF 171F0C29 libbind9.dll 81588F0B E7D3C6B3 20EDC314 532D9F2D 0A105594 libdns.dll E0BD7187 BBC01003 ABFE7472 E64B68CD 1BDB6BAB libeay32.dll F445362E 728A9027 96EC6871 A79C6307 054974E4 libisc.dll B3255C0E 4808A703 F95C217A 91FFCD69 40E680C9 libisccfg.dll DFBDE4F9 E25FD49A 0846E97F D813D687 6DC94067 liblwres.dll 61B8F573 DB448AE6 351AE347 5C2E7C48 2D81533C msvcr70.dll BDA14B28 7987E168 F359F0C9 DD96866D 04AB189B resolv.conf 1112343A 319C3EEE E44BF261 AE196C96 289C70E2 sha1.exe 21D20035 2A5B64E2 69FEA407 4D78053F 3C7A2738 whois.exe If your hashes are the same as the above table, then your files pass the integrity check. -

Streamlining Integrated Infrastructure Implementation “Dig Once” Strategy Development Workshop June 9, 2016
Streamlining Integrated Infrastructure Implementation “Dig Once” Strategy Development Workshop June 9, 2016 Workshop Report February 2017 Sponsored By: Alliance for the Chesapeake Bay Local Government Advisory Committee (LGAC) Funding: National Fish & Wildlife Foundation (NFWF) Prepared By: Alliance for the Chesapeake Bay Hirschman Water & Environment, LLC 1. Workshop Overview and Focus The focus of this workshop was to explore better ways to integrate green infrastructure (GI) into other infrastructure projects, such as roads, school and park improvements, and other capital projects. The workshop was hosted by the Alliance for the Chesapeake Bay (ACB) in conjunction with the Local Government Advisory Committee to the Chesapeake Executive Council (LGAC), with funding from the National Fish & Wildlife Foundation (NFWF). Mary Gattis, Director of Local Government Programs for ACB, was the lead facilitator for the workshop. The workshop was held on June 9, 2016 at the Eisenhower Hotel in Gettysburg, Pennsylvania. The organizers targeted certain sector representatives for attendance in order to achieve the necessary cross-section of experiences and points of view. Figure 1 shows the breakdown of attendees by type of organization. A total of 58 individuals attended the 1-day workshop, 52 participants and six staff representatives. See Appendix A for a list of workshop participants. Prior to the workshop, the following problem statement and workshop goal Figure 1. Representation of 52 Workshop Attendees were sent to attendees as part of the agenda. This was done in order to maintain a clear focus for the workshop, as the topic of green infrastructure has many facets, each of which could fill the entire agenda for a one-day event. -

Emacspeak User's Guide
Emacspeak User's Guide Jennifer Jobst Revision History Revision 1.3 July 24,2002 Revised by: SDS Updated the maintainer of this document to Sharon Snider, corrected links, and converted to HTML Revision 1.2 December 3, 2001 Revised by: JEJ Changed license to GFDL Revision 1.1 November 12, 2001 Revised by: JEJ Revision 1.0 DRAFT October 19, 2001 Revised by: JEJ This document helps Emacspeak users become familiar with Emacs as an audio desktop and provides tutorials on many common tasks and the Emacs applications available to perform those tasks. Emacspeak User's Guide Table of Contents 1. Legal Notice.....................................................................................................................................................1 2. Introduction.....................................................................................................................................................2 2.1. What is Emacspeak?.........................................................................................................................2 2.2. About this tutorial.............................................................................................................................2 3. Before you begin..............................................................................................................................................3 3.1. Getting started with Emacs and Emacspeak.....................................................................................3 3.2. Emacs Command Conventions.........................................................................................................3 -

Spelling Correction: from Two-Level Morphology to Open Source
Spelling Correction: from two-level morphology to open source Iñaki Alegria, Klara Ceberio, Nerea Ezeiza, Aitor Soroa, Gregorio Hernandez Ixa group. University of the Basque Country / Eleka S.L. 649 P.K. 20080 Donostia. Basque Country. [email protected] Abstract Basque is a highly inflected and agglutinative language (Alegria et al., 1996). Two-level morphology has been applied successfully to this kind of languages and there are two-level based descriptions for very different languages. After doing the morphological description for a language, it is easy to develop a spelling checker/corrector for this language. However, what happens if we want to use the speller in the "free world" (OpenOffice, Mozilla, emacs, LaTeX, ...)? Ispell and similar tools (aspell, hunspell, myspell) are the usual mechanisms for these purposes, but they do not fit the two-level model. In the absence of two-level morphology based mechanisms, an automatic conversion from two-level description to hunspell is described in this paper. previous work and reuse the morphological information. 1. Introduction Two-level morphology (Koskenniemi, 1983; Beesley & Karttunen, 2003) has been applied successfully to the 2. Free software for spelling correction morphological description of highly inflected languages. Unfortunately there are not open source tools for spelling There are two-level based descriptions for very different correction with these features: languages (English, German, Swedish, French, Spanish, • It is standardized in the most of the applications Danish, Norwegian, Finnish, Basque, Russian, Turkish, (OpenOffice, Mozilla, emacs, LaTeX, ...). Arab, Aymara, Swahili, etc.). • It is based on the two-level morphology. After doing the morphological description, it is easy to The spell family of spell checkers (ispell, aspell, myspell) develop a spelling checker/corrector for the language fits the first condition but not the second. -

Brewer Mkiv Spectrophotometer
BREWER MKII Spectrophotometer Operator's Manual BREWER MKIV SPECTROPHOTOMETER OPERATOR'S MANUAL OM-BA-C231 REV B, August 15, 1999 SCI-TEC Instruments Inc. 1503 Fletcher Road Saskatoon, Sask. , Canada S7M 5S5 Phone 306-934-0101 Fax 306-978-2339 Email: [email protected] Web site: www.sci-tec.com BREWER MKII Spectrophotometer Operator's Manual This Page is Intentionally left Blank TABLE OF CONTENTS 1 SYSTEM OVERVIEW..................................................................................................................................1 2 SYSTEM DESCRIPTION .............................................................................................................................3 2.1 SPECTROPHOTOMETER ......................................................................................................................4 2.2 SOLAR TRACKING..............................................................................................................................16 2.3 COMPUTER EQUIPMENT ...................................................................................................................17 3 BREWER SYSTEM SETUP........................................................................................................................19 3.1 SPECTROPHOTOMETER UNPACKING AND SETUP........................................................................21 3.2 TRIPOD UNPACKING AND SETUP ....................................................................................................21 3.3 AZIMUTH TRACKER UNPACKING AND SETUP..............................................................................21