Analysis of Browser-Specific Characte
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Cache Files Detect and Eliminate Privacy Threats
Award-Winning Privacy Software for OS X Every time you surf the web or use your computer, bits of Recover Disk Space data containing sensitive information are left behind that Over time, the files generated by web browsers can start could compromise your privacy. PrivacyScan provides to take up a large amount of space on your hard drive, protection by scanning for these threats and offers negatively impacting your computer’s performance. multiple removal options to securely erase them from PrivacyScan can locate and removes these space hogs, your system. freeing up valuable disk space and giving your system a speed boost in the process. PrivacyScan can seek and destroy internet files used for tracking your online whereabouts, including browsing history, cache files, cookies, search history, and more. Secure File Shredding Additionally, PrivacyScan can eliminate Flash Cookies, PrivacyScan utilizes advanced secure delete algorithms which are normally hidden away on your system. that meet and exceed US Department of Defense recommendations to ensure complete removal of Privacy Threat: Cookies sensitive data. Cookies can be used to track your usage of websites, determining which pages you visited and the length Intuitive Interface of time you spent on each page. Advertisers can use PrivacyScan’s award-winning design makes it easy to cookies to track you across multiple sites, building up track down privacy threats that exist on your system and a “profile” of who you are based on your web browsing quickly eliminate them. An integrated setup assistant and habits. tip system provide help every step of the way to make file cleaning a breeze. -
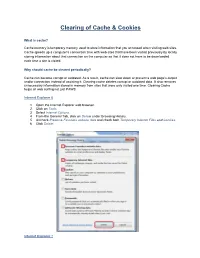
Clearing of Cache & Cookies
Clearing of Cache & Cookies What is cache? Cache memory is temporary memory used to store information that you accessed when visiting web sites. Cache speeds up a computer’s connection time with web sites that have been visited previously by locally storing information about that connection on the computer so that it does not have to be downloaded each time a site is visited. Why should cache be cleared periodically? Cache can become corrupt or outdated. As a result, cache can slow down or prevent a web page’s output and/or connection instead of assisting it. Clearing cache deletes corrupt or outdated data. It also removes unnecessary information stored in memory from sites that were only visited one time. Clearing Cache helps all web surfing not just PAWS. Internet Explorer 8 1. Open the Internet Explorer web browser. 2. Click on Tools. 3. Select Internet Options. 4. From the General Tab, click on Delete under Browsing History. 5. Uncheck Preserve Favorites website data and check both Temporary Internet Files and Cookies. 6. Click Delete. Internet Explorer 7 1. Open the Internet Explorer web browser. 2. Click on Tools. 3. Click on Internet Options. 4. Click on Delete under Browsing History. 5. Click Delete cookies. 6. When prompted, click Yes. 7. Click on Delete Internet Files. 8. When prompted, click Yes. 9. Click Close. 10. Click OK. 11. Close and reopen the browser for the changes to go into effect. Internet Explorer 6 1. Open the Internet Explorer web browser. 2. Click on Tools. 3. Click on Internet Options. 4. -

Infrastructural Requirements for a Privacy Preserving Internet
Infrastructural Requirements for a Privacy Preserving Internet Brad Rosen Fall 2003 Professor Feigenbaum Sensitive Information in the Wired World Abstract With much gusto, firms routinely sell “privacy enhancing technology” to enrich the web experience of typical consumers. Standards bodies have thrown in their hats, and even large organizations such as AT&T and IBM have gotten involved. Still, it seems no one has asked the question, “Are we trying to save a sinking ship?” “Are our ultimate goals actually achievable given the current framework?” This paper tries to examine the necessary infrastructure to support the goals of privacy enhancing technologies and the reasoning behind them. Contents 1 Introduction 2 2 Definition of Terms 3 2.1 User-Centric Terms . 3 2.2 Technical Terms . 4 2.3 Hypothetical Terms . 5 3 Privacy and Annoyances 5 3.1 Outflows – Encroachment . 6 3.2 Inflows – Annoyances . 6 3.3 Relevance . 7 4 Privacy Preserving vs. Privacy Enhancing 7 1 5 Current Infrastructure 8 5.1 Overview . 8 5.2 DNS Request . 8 5.3 Routing . 9 5.4 Website Navigation . 9 5.5 Sensitive Data-Handling . 9 5.6 Infrastructural Details . 10 5.6.1 IPv4 . 10 5.6.2 Java/ECMA Script . 10 5.6.3 Applets/ActiveX . 10 5.6.4 (E)SMTP . 10 6 Next-Generation Infrastructure 11 6.1 Overview . 11 6.2 DNS Request . 11 6.3 Routing . 12 6.4 Website Navigation . 12 6.5 Sensitive Data-Handling . 12 6.6 Infrastructural Details . 13 6.6.1 IPv6 . 13 6.6.2 Java/ECMA Script . 13 6.6.3 Applets/ActiveX . -

HTTP Cookie - Wikipedia, the Free Encyclopedia 14/05/2014
HTTP cookie - Wikipedia, the free encyclopedia 14/05/2014 Create account Log in Article Talk Read Edit View history Search HTTP cookie From Wikipedia, the free encyclopedia Navigation A cookie, also known as an HTTP cookie, web cookie, or browser HTTP Main page cookie, is a small piece of data sent from a website and stored in a Persistence · Compression · HTTPS · Contents user's web browser while the user is browsing that website. Every time Request methods Featured content the user loads the website, the browser sends the cookie back to the OPTIONS · GET · HEAD · POST · PUT · Current events server to notify the website of the user's previous activity.[1] Cookies DELETE · TRACE · CONNECT · PATCH · Random article Donate to Wikipedia were designed to be a reliable mechanism for websites to remember Header fields Wikimedia Shop stateful information (such as items in a shopping cart) or to record the Cookie · ETag · Location · HTTP referer · DNT user's browsing activity (including clicking particular buttons, logging in, · X-Forwarded-For · Interaction or recording which pages were visited by the user as far back as months Status codes or years ago). 301 Moved Permanently · 302 Found · Help 303 See Other · 403 Forbidden · About Wikipedia Although cookies cannot carry viruses, and cannot install malware on 404 Not Found · [2] Community portal the host computer, tracking cookies and especially third-party v · t · e · Recent changes tracking cookies are commonly used as ways to compile long-term Contact page records of individuals' browsing histories—a potential privacy concern that prompted European[3] and U.S. -

Marcia Knous: My Name Is Marcia Knous
Olivia Ryan: Can you just state your name? Marcia Knous: My name is Marcia Knous. OR: Just give us your general background. How did you come to work at Mozilla and what do you do for Mozilla now? MK: Basically, I started with Mozilla back in the Netscape days. I started working with Mozilla.org shortly after AOL acquired Netscape which I believe was in like the ’99- 2000 timeframe. I started working at Netscape and then in one capacity in HR shortly after I moved working with Mitchell as part of my shared responsibility, I worked for Mozilla.org and sustaining engineering to sustain the communicator legacy code so I supported them administratively. That’s basically what I did for Mozilla. I did a lot of I guess what you kind of call of blue activities where we have a process whereby people get access to our CVS repository so I was the gatekeeper for all the CVS forms and handle all the bugs that were related to CVS requests, that kind of thing. Right now at Mozilla, I do quality assurance and I run both our domestic online store as well as our international store where we sell all of our Mozilla gear. Tom Scheinfeldt: Are you working generally alone in small groups? In large groups? How do you relate to other people working on the project? MK: Well, it’s a rather interesting project. My capacity as a QA person, we basically relate with the community quite a bit because we have a very small internal QA organization. -

THE POWER of CLOUD COMPUTING COMES to SMARTPHONES Neeraj B
THE POWER OF CLOUD COMPUTING COMES TO SMARTPHONES Neeraj B. Bharwani B.E. Student (Information Science and Engineering) SJB Institute of Technology, Bangalore 60 Table of Contents Introduction ............................................................................................................................................3 Need for Clone Cloud ............................................................................................................................4 Augmented Execution ............................................................................................................................5 Primary functionality outsourcing ........................................................................................................5 Background augmentation..................................................................................................................5 Mainline augmentation .......................................................................................................................5 Hardware augmentation .....................................................................................................................6 Augmentation through multiplicity .......................................................................................................6 Architecture ...........................................................................................................................................7 Snow Flock: Rapid Virtual Machine Cloning for Cloud Computing ........................................................ -
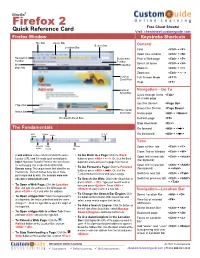
Firefox 2 Free Cheat Sheets! Quick Reference Card Visit: Cheatsheet.Customguide.Com Firefox Window Keystroke Shortcuts
® Mozilla Firefox 2 Free Cheat Sheets! Quick Reference Card Visit: cheatsheet.customguide.com Firefox Window Keystroke Shortcuts Title Bar Menu Bar Search bar General Location Bar Find <Ctrl> + <F> Open new window <Ctrl> + <N> Navigation Bookmarks Print a Web page <Ctrl> + <P> Toolbar Toolbar Select all items <Ctrl> + <A> Web Tabs Bar page tab Zoom in <Ctrl> + <+> Zoom out <Ctrl> + < - > Vertical Full Screen Mode <F11> Scroll Box Help <F1> Vertical Navigation—Go To Scroll Bar Cycle through items <Tab> on a web page Up One Screen <Page Up> Hyperlink Down One Screen <Page Down> Horizontal Status Bar Scroll Bar Home page <Alt> + <Home> Horizontal Scroll Box Refresh page <F5> Stop download <Esc> The Fundamentals Go forward <Alt> + < → > Back Search Reload Home Go backward <Alt> + < ← > button Bar Tabs Forward Stop Location Open a New Tab <Ctrl> + <T> button button Bar Close Tab or Window <Ctrl> + <W> • A web address is also called a Uniform Resource • To Go Back to a Page: Click the Back Open link in new tab <Ctrl> + <click> Locator (URL) and it is made up of several parts: button or press <Alt> + <←>. Or, click the Back (background) http:// Hypertext Transfer Protocol, the set of rules button list arrow and select a page from the list. for exchanging files on the World Wide Web. Open link in new tab <Ctrl> + <Shift> To Go Forward a Page: Click the Forward Domain name: The unique name that identifies an • (foreground) + <click> button or press <Alt> + <→>. Or, click the Internet site. Domain names have two or more Switch to next tab <Ctrl> + <Tab> parts separated by dots. -

Bienvenue Sur L'aide En Ligne Du Simulateur Affranchigo
AIDE EN LIGNE DU SIMULATEUR Bienvenue sur l’aide en ligne du simulateur AFFRANCHIGO A. Aide à la navigation Le développement de ce site s'efforce de respecter au mieux les critères d'accessibilité de façon à faciliter la consultation du site pour tous. Si malgré nos efforts, vous rencontrez des difficultés à consulter certaines informations, n'hésitez pas à nous en faire part. 1. Logo du haut de page Le logo La Poste du haut de page permet d’accéder à l’espace «Solutions Business» pour affranchir votre courrier entreprise sur le portail www.laposte.fr. 2. Présentation du contenu-Téléchargement La plus grande partie du contenu est disponible en format HTML. Vous trouverez des documents téléchargeables au format RTF. Ce format est lisible par tous les sites bureautiques. Vous trouverez également des documents téléchargeables au format PDF. Si vous n'avez pas Acrobat Reader, vous pouvez le télécharger sur le site d'Adobe : télécharger Acrobat Reader. Ou alors, vous pouvez transformer les PDF en format HTML classique en utilisant le moteur de conversion en ligne d'Adobe. Pour cela, copier l'adresse du lien vers le fichier en PDF et collez-la dans le champ prévu à cet effet sur l'outil de conversion en ligne d'Adobe. 3. Raccourcis claviers Par ailleurs, des raccourcis claviers ont été programmés sur la totalité du site : − «s» vous amène sur le bouton «suivant» − «p» vous amène sur le bouton «précédent» Les combinaisons de touches pour valider ces raccourcis diffèrent selon les navigateurs, c'est pourquoi nous listons ci-dessous les procédures -

Discontinued Browsers List
Discontinued Browsers List Look back into history at the fallen windows of yesteryear. Welcome to the dead pool. We include both officially discontinued, as well as those that have not updated. If you are interested in browsers that still work, try our big browser list. All links open in new windows. 1. Abaco (discontinued) http://lab-fgb.com/abaco 2. Acoo (last updated 2009) http://www.acoobrowser.com 3. Amaya (discontinued 2013) https://www.w3.org/Amaya 4. AOL Explorer (discontinued 2006) https://www.aol.com 5. AMosaic (discontinued in 2006) No website 6. Arachne (last updated 2013) http://www.glennmcc.org 7. Arena (discontinued in 1998) https://www.w3.org/Arena 8. Ariadna (discontinued in 1998) http://www.ariadna.ru 9. Arora (discontinued in 2011) https://github.com/Arora/arora 10. AWeb (last updated 2001) http://www.amitrix.com/aweb.html 11. Baidu (discontinued 2019) https://liulanqi.baidu.com 12. Beamrise (last updated 2014) http://www.sien.com 13. Beonex Communicator (discontinued in 2004) https://www.beonex.com 14. BlackHawk (last updated 2015) http://www.netgate.sk/blackhawk 15. Bolt (discontinued 2011) No website 16. Browse3d (last updated 2005) http://www.browse3d.com 17. Browzar (last updated 2013) http://www.browzar.com 18. Camino (discontinued in 2013) http://caminobrowser.org 19. Classilla (last updated 2014) https://www.floodgap.com/software/classilla 20. CometBird (discontinued 2015) http://www.cometbird.com 21. Conkeror (last updated 2016) http://conkeror.org 22. Crazy Browser (last updated 2013) No website 23. Deepnet Explorer (discontinued in 2006) http://www.deepnetexplorer.com 24. Enigma (last updated 2012) No website 25. -

Web Browsing and Communication Notes
digital literacy movement e - learning building modern society ITdesk.info – project of computer e-education with open access human rights to e - inclusion education and information open access Web Browsing and Communication Notes Main title: ITdesk.info – project of computer e-education with open access Subtitle: Web Browsing and Communication, notes Expert reviwer: Supreet Kaur Translator: Gorana Celebic Proofreading: Ana Dzaja Cover: Silvija Bunic Publisher: Open Society for Idea Exchange (ODRAZI), Zagreb ISBN: 978-953-7908-18-8 Place and year of publication: Zagreb, 2011. Copyright: Feel free to copy, print, and further distribute this publication entirely or partly, including to the purpose of organized education, whether in public or private educational organizations, but exclusively for noncommercial purposes (i.e. free of charge to end users using this publication) and with attribution of the source (source: www.ITdesk.info - project of computer e-education with open access). Derivative works without prior approval of the copyright holder (NGO Open Society for Idea Exchange) are not permitted. Permission may be granted through the following email address: [email protected] ITdesk.info – project of computer e-education with open access Preface Today’s society is shaped by sudden growth and development of the information technology (IT) resulting with its great dependency on the knowledge and competence of individuals from the IT area. Although this dependency is growing day by day, the human right to education and information is not extended to the IT area. Problems that are affecting society as a whole are emerging, creating gaps and distancing people from the main reason and motivation for advancement-opportunity. -

Minnesota River Weekly Update April 15, 2009
Minnesota River Weekly Update April 15, 2009 Not Your Typical Online Auction NICOLLET — Some may think farming and the Internet are two opposite ends of the technological spectrum, but Joe and Liza Domeier are proving they work well together. And profitably at that. They run Pehling Bay Farm near Nicollet. Joe’s mother grew up on the 30-acre property established by her grandfather. Liza was raised on a hog farm near St. Clair. The couple sells pasture-fed livestock and poultry, as well as fiber from their sheep flock. They are building a healthy business utilizing the Internet and direct marketing to draw buyers who are willing to pay premium prices for local grown products. The small acreage would pay like a part-time job if they attempted traditional row crop farming. So a different approach was chosen: raising pasture fed animals to sell to very select markets. Their sheep, hogs, chickens and beef are all pasture-fed, which may mean slower growth. However, Joe said it makes for healthier and more flavorful meats. They don’t sell meat or fiber retail or wholesale, only directly to customers. Direct marketing allows more money to be generated from the land. Their web site, www.pehlingbayfarm.com, advertises their meat and is a place where they can take product orders. In fact, most of their sales come via online sources. ―Direct marketing without the Internet is like not having a phone,‖ Joe said, ―And you reach a much larger audience.‖ Joe says he is able to get about twice the market price for lambs as he would at a sale barn. -

Home Java Plugin Detector Java (Using <Applet> And/Or <Object> Tag
22/05/12 Java plugin detection with PluginDetect Home Java Plugin Detector Java (using <applet> and/or <object> tag) installed & enabled: true Highest Installed Java Version: 1,6,0,31 Java 1,6,0,10 or higher (using <applet> and/or <object> tag) is installed & enabled. Java detection: completed ON THE FLY (OTF) Deployment Toolkit browser plugin installed & enabled: false Next-Generation Java Plugin2 installed & enabled: true Java vendor: Sun Microsystems Inc. Java plugin name: Java(TM) Platform SE 6 U31 Java plugin description: Next Generation Java Plug-in 1.6.0_31 for Mozilla browsers navigator.javaEnabled(): true [This detector is capable of OTF & NOTF Java detection. Detection occurs before window.onload event has fired.] [window.onload event has fired successfully.] [ The plugin detector(s) in this web page use the following: PluginDetect_Java.js, detectJava_OTF_NOTF.js, getJavaInfo.jar ] Download PluginDetect and the jarfile here... In order to do Java detection, you will need 2 things: 1) download the getJavaInfo.jar applet along with a few Java detection examples. The jarfile (Java ARchive file) is used by PluginDetect in order to accomplish Java detection. 2) download the PluginDetect script itself. The PluginDetect script generator will allow you to customize the PluginDetect script to include whatever features you desire. That being said, I would still recommend that you read thru most of this page before creating your own Java detection code. A brief introduction to Java detection PluginDetect uses a number of different methods when trying to detect Java in your browser. These Java detection methods can be divided into 2 groups: a) the non-applet methods and b) the applet methods.