Home Java Plugin Detector Java (Using <Applet> And/Or <Object> Tag
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
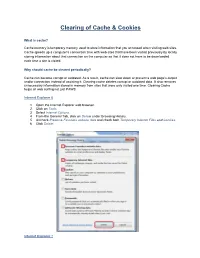
Clearing of Cache & Cookies
Clearing of Cache & Cookies What is cache? Cache memory is temporary memory used to store information that you accessed when visiting web sites. Cache speeds up a computer’s connection time with web sites that have been visited previously by locally storing information about that connection on the computer so that it does not have to be downloaded each time a site is visited. Why should cache be cleared periodically? Cache can become corrupt or outdated. As a result, cache can slow down or prevent a web page’s output and/or connection instead of assisting it. Clearing cache deletes corrupt or outdated data. It also removes unnecessary information stored in memory from sites that were only visited one time. Clearing Cache helps all web surfing not just PAWS. Internet Explorer 8 1. Open the Internet Explorer web browser. 2. Click on Tools. 3. Select Internet Options. 4. From the General Tab, click on Delete under Browsing History. 5. Uncheck Preserve Favorites website data and check both Temporary Internet Files and Cookies. 6. Click Delete. Internet Explorer 7 1. Open the Internet Explorer web browser. 2. Click on Tools. 3. Click on Internet Options. 4. Click on Delete under Browsing History. 5. Click Delete cookies. 6. When prompted, click Yes. 7. Click on Delete Internet Files. 8. When prompted, click Yes. 9. Click Close. 10. Click OK. 11. Close and reopen the browser for the changes to go into effect. Internet Explorer 6 1. Open the Internet Explorer web browser. 2. Click on Tools. 3. Click on Internet Options. 4. -

Workforce Management Web
Workforce Management Web 8.5.214.14 9/23/2021 8.5.214.14 8.5.214.14 Workforce Management Web Release Notes Release Date Release Type Restrictions AIX Linux Solaris Windows 05/08/19 General X X Contents • 1 8.5.214.14 • 1.1 Helpful Links • 1.2 What's New • 1.3 Resolved Issues • 1.4 Upgrade Notes • 1.5 Supported Languages Workforce Management Web 2 8.5.214.14 What's New Helpful Links This release includes the following new features and enhancements: Releases Info • WFM Web for Supervisors includes a redesigned Forecast module, • List of 8.5.x Releases enabling access to existing forecasting functionality and features, but with many user-friendly enhancements, wizards, and tools. Web for • 8.5.x Known Issues Supervisors (Classic) Forecast module is still supported and available. Note: The Forecast module is currently available only in English. (WFM-28004) Product Documentation • AI-powered Forecasting is introduced in the redesigned Forecast module, providing a sophisticated, automated build method that uses the best of best forecasting algorithms provided through Genesys Workforce Management hosted cloud infrastructure. For information about how to use this build method, see Building Volumes in the Workforce Management Genesys Products Supervisor Help.(WFM-28004) List of Release Notes • The Workforce Management Supervisor Help is a context-sensitive Help that describes the new Forecast interface, including topics that describe the Forecast Scenario and Master Forecast views, and procedures that describe forecasting tasks. The Workforce Management Supervisors (Classic) Help is still available. (WFM-29230) • The Overlays view in the new WFM Web Forecast interface is enhanced, enabling supervisors to adjust Spread over distribution to 15 or 30 minutes (in addition to 60). -

Making Speech Recognition Work on the Web Christopher J. Varenhorst
Making Speech Recognition Work on the Web by Christopher J. Varenhorst Submitted to the Department of Electrical Engineering and Computer Science in partial fulfillment of the requirements for the degree of Masters of Engineering in Computer Science and Engineering at the MASSACHUSETTS INSTITUTE OF TECHNOLOGY May 2011 c Massachusetts Institute of Technology 2011. All rights reserved. Author.................................................................... Department of Electrical Engineering and Computer Science May 20, 2011 Certified by . James R. Glass Principal Research Scientist Thesis Supervisor Certified by . Scott Cyphers Research Scientist Thesis Supervisor Accepted by . Christopher J. Terman Chairman, Department Committee on Graduate Students Making Speech Recognition Work on the Web by Christopher J. Varenhorst Submitted to the Department of Electrical Engineering and Computer Science on May 20, 2011, in partial fulfillment of the requirements for the degree of Masters of Engineering in Computer Science and Engineering Abstract We present an improved Audio Controller for Web-Accessible Multimodal Interface toolkit { a system that provides a simple way for developers to add speech recognition to web pages. Our improved system offers increased usability and performance for users and greater flexibility for developers. Tests performed showed a %36 increase in recognition response time in the best possible networking conditions. Preliminary tests shows a markedly improved users experience. The new Wowza platform also provides a means of upgrading other Audio Controllers easily. Thesis Supervisor: James R. Glass Title: Principal Research Scientist Thesis Supervisor: Scott Cyphers Title: Research Scientist 2 Contents 1 Introduction and Background 7 1.1 WAMI - Web Accessible Multimodal Toolkit . 8 1.1.1 Existing Java applet . 11 1.2 SALT . -

Cross-Platform System of Medical Documents Protection Through Digital Signatures
CROSS-PLATFORM SYSTEM OF MEDICAL DOCUMENTS PROTECTION THROUGH DIGITAL SIGNATURES Fernando Guilherme Ferreira Sousa Project/Dissertation developed under supervising of José Magalhães Cruz (PhD) in Glintt - Healthcare Solutions, S.A. 1. Motivation documents, which are then sent to the server and, consequently, validated and stored in the database. Due to the extreme information sensibility in the Subsequent to this process, each time a document is health area, it is really necessary to be absolutely sure opened to be viewed, for example, a check is made of about who performs certain medical transactions. It a possible change to the same document, in order to must have permission and authority to do so, i.e. be ensure that recurrently its integrity. Through really the right person to do this transaction. In areas cryptography-based security methods of public keys, involving health treatments, marking of exams or it is verified if someone tampered the document or even surgeries and new prescriptions, there must be made it invalid in some way. an extremely effective control to verify effectively that all transactions must be properly carried out, Each platform that the doctor use should read his without any type of deception or illegality. digital certificate, which is contained in a Smart Card and is installed on the machine, once inserted in a One of the biggest motivations is that the patient, in suitable card reader. Then, the digital signature is the future, might be aware that there is a control in performed with the certificate’s associated private the preparation of their medical documents. All key, which certificates the medical document. -

Marcia Knous: My Name Is Marcia Knous
Olivia Ryan: Can you just state your name? Marcia Knous: My name is Marcia Knous. OR: Just give us your general background. How did you come to work at Mozilla and what do you do for Mozilla now? MK: Basically, I started with Mozilla back in the Netscape days. I started working with Mozilla.org shortly after AOL acquired Netscape which I believe was in like the ’99- 2000 timeframe. I started working at Netscape and then in one capacity in HR shortly after I moved working with Mitchell as part of my shared responsibility, I worked for Mozilla.org and sustaining engineering to sustain the communicator legacy code so I supported them administratively. That’s basically what I did for Mozilla. I did a lot of I guess what you kind of call of blue activities where we have a process whereby people get access to our CVS repository so I was the gatekeeper for all the CVS forms and handle all the bugs that were related to CVS requests, that kind of thing. Right now at Mozilla, I do quality assurance and I run both our domestic online store as well as our international store where we sell all of our Mozilla gear. Tom Scheinfeldt: Are you working generally alone in small groups? In large groups? How do you relate to other people working on the project? MK: Well, it’s a rather interesting project. My capacity as a QA person, we basically relate with the community quite a bit because we have a very small internal QA organization. -
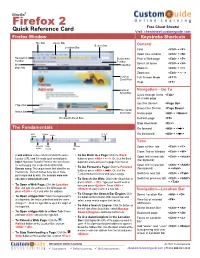
Firefox 2 Free Cheat Sheets! Quick Reference Card Visit: Cheatsheet.Customguide.Com Firefox Window Keystroke Shortcuts
® Mozilla Firefox 2 Free Cheat Sheets! Quick Reference Card Visit: cheatsheet.customguide.com Firefox Window Keystroke Shortcuts Title Bar Menu Bar Search bar General Location Bar Find <Ctrl> + <F> Open new window <Ctrl> + <N> Navigation Bookmarks Print a Web page <Ctrl> + <P> Toolbar Toolbar Select all items <Ctrl> + <A> Web Tabs Bar page tab Zoom in <Ctrl> + <+> Zoom out <Ctrl> + < - > Vertical Full Screen Mode <F11> Scroll Box Help <F1> Vertical Navigation—Go To Scroll Bar Cycle through items <Tab> on a web page Up One Screen <Page Up> Hyperlink Down One Screen <Page Down> Horizontal Status Bar Scroll Bar Home page <Alt> + <Home> Horizontal Scroll Box Refresh page <F5> Stop download <Esc> The Fundamentals Go forward <Alt> + < → > Back Search Reload Home Go backward <Alt> + < ← > button Bar Tabs Forward Stop Location Open a New Tab <Ctrl> + <T> button button Bar Close Tab or Window <Ctrl> + <W> • A web address is also called a Uniform Resource • To Go Back to a Page: Click the Back Open link in new tab <Ctrl> + <click> Locator (URL) and it is made up of several parts: button or press <Alt> + <←>. Or, click the Back (background) http:// Hypertext Transfer Protocol, the set of rules button list arrow and select a page from the list. for exchanging files on the World Wide Web. Open link in new tab <Ctrl> + <Shift> To Go Forward a Page: Click the Forward Domain name: The unique name that identifies an • (foreground) + <click> button or press <Alt> + <→>. Or, click the Internet site. Domain names have two or more Switch to next tab <Ctrl> + <Tab> parts separated by dots. -

Exploiting SAS Software Using Java Technology
Exploiting SAS® Software Using Java™ Technology Barbara Walters, SAS Institute Inc., Cary, NC Java programs are often delivered via the Internet. In order to protect the local machine from malicious programs, the Java language and the JVM Abstract provide a secure environment for application execution. The secure This paper describes how to use Java™ technology with SAS software. environment ensures that the client machine (the machine where the SAS Institute currently offers several Java development tools that allow browser is running) is not corrupted by the downloaded program and that applications to access SAS data and take advantage of SAS no information is stolen from the client machine. computational capabilities. This paper describes how to use these class libraries and address client/server configuration and performance Java security is based upon the “sandbox” model. The sandbox is the issues. set of resources (threads, socket connections, local files, etc.) that the downloaded Java code is allowed to access. The code is restricted from accessing resources outside of its sandbox. In executing Java applets, Introduction each Web browser defines the limits of the sandbox. Since its introduction in mid-1995, Java have become an integral part of The Security Manager enforces the limits of the sandbox. For applets, the World Wide Web. Java is a rich programming language that enables the Web browser controls the Security Manager. Each browser may put Web programmers to create sophisticated and responsive client/server different restrictions on applet behavior. The default limits imposed by applications. Because Java is portable and secure, users of Web the Security Manager are: applications can be confident that those applications will execute • Classes cannot access the local file system properly and not corrupt their computers. -

Applets, Servlets and JSP
Java Programming : applets, servlets and JSP. SR03 Dritan Nace A summary of Java Java is a language developed by Sun, which is designed to be object oriented and Simple, robust and secure, independent of hardware architectures and Multitasking. Object oriented and simple : Simpler than C++, transparent memory managment… Robust et secure : Data typing is extremely strict. For applets, it is in principle impossible to access the resources of the host machine. Independant of hardware architectures : The compiler generates a universal code : the « byte-code ». An interpreter which is specific to the host machine, « virtual machine », executes the programs. Multitasking : Java seemingly allows execution of several processes. In reality, a time slot is given to each process on the processor (Multithreaded). J2SE versus J2EE J2SE (standard edition) contains the basic usable components from both the client and server side, – GUI, AWT/Swing for applications (client) or applets. Currently J2SE v1.6 (ou V6) J2EE (enterprise edition), is in a certain sense an extension of SE, designed for server side programming – Servlets, JSP, EJB, etc. • Currently J2EE v1.4 Java and object oriented programming • Classes, and objects – The objects include data and processing for the data. Communication is done via messages (methods). – A class corresponds to an abstract model for object construction. A class is made up of: • attributes (static part) • Methods (dynamic part), which define the behaviour. – Inheritance : the « is a » relationship : a car is a vehicule, – Polymorphism : the same message can be recognised by several objects and entail different behaviour. Portability: JVM The compiler compiles the java source in byte code : javac car.java => car.class Then, java is the name of the program which will interpret the generated byte code. -

Abstract Window Toolkit Overview
In this chapter: • Components • Peers 1 • Layouts • Containers • And the Rest • Summary Abstract Window Toolkit Overview For years, programmers have had to go through the hassles of porting software from BSD-based UNIX to System V Release 4–based UNIX, from OpenWindows to Motif, from PC to UNIX to Macintosh (or some combination thereof), and between various other alternatives, too numerous to mention. Getting an applica- tion to work was only part of the problem; you also had to port it to all the plat- forms you supported, which often took more time than the development effort itself. In the UNIX world, standards like POSIX and X made it easier to move appli- cations between different UNIX platforms. But they only solved part of the prob- lem and didn’t provide any help with the PC world. Portability became even more important as the Internet grew. The goal was clear: wouldn’t it be great if you could just move applications between different operating environments without worr yingabout the software breaking because of a different operating system, win- dowing environment, or internal data representation? In the spring of 1995, Sun Microsystems announced Java, which claimed to solve this dilemma. What started out as a dancing penguin (or Star Trek communicator) named Duke on remote controls for interactive television has become a new paradigm for programming on the Internet. With Java, you can create a program on one platform and deliver the compilation output (byte-codes/class files) to ever yother supported environment without recompiling or worrying about the local windowing environment, word size, or byte order. -

Apache Harmony Project Tim Ellison Geir Magnusson Jr
The Apache Harmony Project Tim Ellison Geir Magnusson Jr. Apache Harmony Project http://harmony.apache.org TS-7820 2007 JavaOneSM Conference | Session TS-7820 | Goal of This Talk In the next 45 minutes you will... Learn about the motivations, current status, and future plans of the Apache Harmony project 2007 JavaOneSM Conference | Session TS-7820 | 2 Agenda Project History Development Model Modularity VM Interface How Are We Doing? Relevance in the Age of OpenJDK Summary 2007 JavaOneSM Conference | Session TS-7820 | 3 Agenda Project History Development Model Modularity VM Interface How Are We Doing? Relevance in the Age of OpenJDK Summary 2007 JavaOneSM Conference | Session TS-7820 | 4 Apache Harmony In the Beginning May 2005—founded in the Apache Incubator Primary Goals 1. Compatible, independent implementation of Java™ Platform, Standard Edition (Java SE platform) under the Apache License 2. Community-developed, modular architecture allowing sharing and independent innovation 3. Protect IP rights of ecosystem 2007 JavaOneSM Conference | Session TS-7820 | 5 Apache Harmony Early history: 2005 Broad community discussion • Technical issues • Legal and IP issues • Project governance issues Goal: Consolidation and Consensus 2007 JavaOneSM Conference | Session TS-7820 | 6 Early History Early history: 2005/2006 Initial Code Contributions • Three Virtual machines ● JCHEVM, BootVM, DRLVM • Class Libraries ● Core classes, VM interface, test cases ● Security, beans, regex, Swing, AWT ● RMI and math 2007 JavaOneSM Conference | Session TS-7820 | -

Migrating from Java Applets to Plugin-Free Java Technologies
Migrating from Java Applets to plugin-free Java technologies An Oracle White Paper January, 2016 Migrating from Java Applets to plugin-free Java technologies Migrating from Java Applets to plugin-free Java technologies Disclaimer The following is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated into any contract. It is not a commitment to deliver any material, code, or functionality, and should not be relied upon in making purchasing decisions. The development, release, and timing of any features or functionality described for Oracle’s products remains at the sole discretion of Oracle. Migrating from Java Applets to plugin-free Java technologies Executive Overview ........................................................................... 4 Browser Plugin Perspectives ............................................................. 4 Java Web Start .................................................................................. 5 Alternatives ....................................................................................... 6 Native Windows/OS X/Linux Installers ........................................... 6 Inverted Browser Control ............................................................... 7 Detecting Applets .............................................................................. 7 Migrating from Java Applets to plugin-free Java technologies Executive Overview With modern browser vendors working to restrict or reduce the support of plugins like -

Installing Open Java Development Kit – Ojdkbuild for Windows
Installing Open Java Development Kit – ojdkbuild for Windows © IZUM, 2019 IZUM, COBISS, COMARC, COBIB, COLIB, CONOR, SICRIS, E-CRIS are registered trademarks owned by IZUM. CONTENTS 1 Introduction ......................................................................................................... 1 2 OpenJDK distribution .......................................................................................... 1 3 Removing Oracle Java ......................................................................................... 2 4 Installing OJDK – 32bit or 64bit, IcedTea Java .................................................. 3 5 Installing the COBISS3 interface ........................................................................ 7 6 Launching the COBISS3 interface .................................................................... 11 7 COBISS3 interface as a trusted source in IcedTea ojdkbuild ........................... 11 © IZUM, 16. 7. 2019, VOS-NA-EN-380, V1.0 i VOS Installing Open Java Development Kit – ojdkbuild for Windows 1 Introduction At the end of 2018 Oracle announced a new business policy for Java SE which entered into force in April 2019. That is why when you install Java a notification and warning window appears. All versions of Java from 8 u201 onwards not intended for personal use are payable. For this reason, we suggest you do not update Java 8 to a newer version for work purposes. If you want a newer version of Java 8, install OpenJDK 8 and IcedTea. Also, do not install Java 8 on new computers (clients), but install OpenJDK 8 with IcedTea support. 2 OpenJDK distribution OpenJDK 1.8. build for Windows and Linux is available at the link https://github.com/ojdkbuild/ojdkbuild. There you will find versions for the installation. The newest version is always at the top, example from 7 May 2019: © IZUM, 16. 7. 2019, VOS-NA-EN-380, V1.0 1/11 Installing Open Java Development Kit – ojdkbuild for Windows VOS 3 Removing Oracle Java First remove the Oracle Java 1.8 software in Control Panel, Programs and Features.