Technical Blueprint for Vertical Use Cases and Validation Framework
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Windows 7 Operating Guide
Welcome to Windows 7 1 1 You told us what you wanted. We listened. This Windows® 7 Product Guide highlights the new and improved features that will help deliver the one thing you said you wanted the most: Your PC, simplified. 3 3 Contents INTRODUCTION TO WINDOWS 7 6 DESIGNING WINDOWS 7 8 Market Trends that Inspired Windows 7 9 WINDOWS 7 EDITIONS 10 Windows 7 Starter 11 Windows 7 Home Basic 11 Windows 7 Home Premium 12 Windows 7 Professional 12 Windows 7 Enterprise / Windows 7 Ultimate 13 Windows Anytime Upgrade 14 Microsoft Desktop Optimization Pack 14 Windows 7 Editions Comparison 15 GETTING STARTED WITH WINDOWS 7 16 Upgrading a PC to Windows 7 16 WHAT’S NEW IN WINDOWS 7 20 Top Features for You 20 Top Features for IT Professionals 22 Application and Device Compatibility 23 WINDOWS 7 FOR YOU 24 WINDOWS 7 FOR YOU: SIMPLIFIES EVERYDAY TASKS 28 Simple to Navigate 28 Easier to Find Things 35 Easy to Browse the Web 38 Easy to Connect PCs and Manage Devices 41 Easy to Communicate and Share 47 WINDOWS 7 FOR YOU: WORKS THE WAY YOU WANT 50 Speed, Reliability, and Responsiveness 50 More Secure 55 Compatible with You 62 Better Troubleshooting and Problem Solving 66 WINDOWS 7 FOR YOU: MAKES NEW THINGS POSSIBLE 70 Media the Way You Want It 70 Work Anywhere 81 New Ways to Engage 84 INTRODUCTION TO WINDOWS 7 6 WINDOWS 7 FOR IT PROFESSIONALS 88 DESIGNING WINDOWS 7 8 WINDOWS 7 FOR IT PROFESSIONALS: Market Trends that Inspired Windows 7 9 MAKE PEOPLE PRODUCTIVE ANYWHERE 92 WINDOWS 7 EDITIONS 10 Remove Barriers to Information 92 Windows 7 Starter 11 Access -

Windows 7 – Hands-On Training Table of Contents PINNING PROGRAMS and USING JUMP LISTS
Windows 7 – Hands-on Training Table of Contents PINNING PROGRAMS AND USING JUMP LISTS ..................................................................................... 3 THE START MENU .............................................................................................................................................. 3 Pin a program icon to the Start menu ............................................................................................................. 3 View the Jump List for a program .................................................................................................................. 4 Open an item from the Jump List ................................................................................................................... 4 Pin an item to a Jump List .............................................................................................................................. 4 Unpin an item ................................................................................................................................................. 4 THE TASKBAR .................................................................................................................................................... 5 Pin a program icon to the taskbar ................................................................................................................... 5 View the Jump List for a program ................................................................................................................. -

Cloud Computing Bible Is a Wide-Ranging and Complete Reference
A thorough, down-to-earth look Barrie Sosinsky Cloud Computing Barrie Sosinsky is a veteran computer book writer at cloud computing specializing in network systems, databases, design, development, The chance to lower IT costs makes cloud computing a and testing. Among his 35 technical books have been Wiley’s Networking hot topic, and it’s getting hotter all the time. If you want Bible and many others on operating a terra firma take on everything you should know about systems, Web topics, storage, and the cloud, this book is it. Starting with a clear definition of application software. He has written nearly 500 articles for computer what cloud computing is, why it is, and its pros and cons, magazines and Web sites. Cloud Cloud Computing Bible is a wide-ranging and complete reference. You’ll get thoroughly up to speed on cloud platforms, infrastructure, services and applications, security, and much more. Computing • Learn what cloud computing is and what it is not • Assess the value of cloud computing, including licensing models, ROI, and more • Understand abstraction, partitioning, virtualization, capacity planning, and various programming solutions • See how to use Google®, Amazon®, and Microsoft® Web services effectively ® ™ • Explore cloud communication methods — IM, Twitter , Google Buzz , Explore the cloud with Facebook®, and others • Discover how cloud services are changing mobile phones — and vice versa this complete guide Understand all platforms and technologies www.wiley.com/compbooks Shelving Category: Use Google, Amazon, or -

SILK Using the Remote Desktop Scheduler Logging Into SILK Using Mozilla Firefox Browser - SILK Quick Reference Guide
SILK Using the Remote Desktop Scheduler Logging into SILK Using Mozilla Firefox Browser - SILK Quick Reference Guide Overview As of October 21, 2015, there are two methods of logging into the SILK Scheduler: LBLESD Citrix Login Interface or the new LBL Remote Desktop User Logon Interface. Citrix Login Interface is used to provide a secured entry into SILK applications. Citrix requires a license for each person logging into using SILK. The Remote Desktop Login Interface (for SILK - RD SILK Scheduler) is another type of secure login method for accessing SILK. LBL has purchased a single license for this product that allows an unlimited number of client users. LBL Information Systems and LBL Network are promoting the use of the Remote Desktop Login Interface for SILK because of: • Security control • Quicker logon response • No idle time limits • No limit to the number of users logged into SILK • Uses the same security – Domain, User ID and Password • SILK works as it always has • And works with web browsers: IE (10 and up), Mozilla Firefox, and Google Chrome Logging into SILK using RD SILK Scheduler To log into SILK using the RD SILK Scheduler you will need to know the Domain, your User ID, and password. For most SILK users the domain is SIS. The user id and password is the same that you currently use for SILK. During your first time using this URL address, you may encounter several Firefox browser security windows before you are allowed to log into your SILK district. Using Mozillia Firefox, enter the following URL to access the RD SILK Scheduler: https://scheduler.lblesd.k12.or.us Linn Benton Lincoln ESD Help Desk: 541.812.2800 or 866.914.2800 firefox browser-remote desktop silk scheduler.docx www.lblesd.k12.or.us https://swhelpdesk.lblesd.k12.or.us version date: 2015.12.04 SILK Using the Remote Desktop Scheduler Logging into SILK Using Mozilla Firefox Browser - SILK Quick Reference Guide Once the User Login page is displayed, enter your SILK security information. -

ARCHIVE 2711.Pdf
ComputorEdge 3/13/09 ComputorEdge™ Online — 03/13/09 This issue: Flash Drives: Computing in Your Pocket The little memory chips have become more than just a way to save and move files. Now you can carry all your computing with you to work with any computer. Table of Contents: Digital Dave by Digital Dave Digital Dave answers your tech questions. A reader wants to run antivirus software from a flash drive; a reader's new external SATA drive isn't much faster than his old ATA drive; why would a reader's computer be shutting down at random intervals? Flash Drive Security by Michael J. Ross They're handy, portable and easy to lose. The diminutive size and light weight of flash drives makes them ideal for portable data storage, but it also makes them easily lost or stolen. Flash drive manufacturers and security software developers are creating a variety of solutions. Linux on a Flash Drive by Michael J. Ross Shrinking OS meets growing-capacity drives. (Click Banner) Linux is an operating system shrinking in size, while USB flash drives are growing in capacity. It was inevitable that a point would be reached at which Linux could be running on a simple flash drive. Windows Vista Tips and Tricks by Jack Dunning Save Time by Using Favorite Links in Windows Explorer Many people ignore the existence of the Favorite Links feature. However, if you take the time to play with it, you will most likely fall in love with this extra feature of Windows Vista. Wally Wang's Apple Farm by Wally Wang New Macintosh Models After a seeming eternity of waiting, Apple released updates to the Mac Pro, (Click Banner) iMac and Mac mini. -

Security Analysis of Browser Extension Concepts
Saarland University Faculty of Natural Sciences and Technology I Department of Computer Science Bachelor's thesis Security Analysis of Browser Extension Concepts A comparison of Internet Explorer 9, Safari 5, Firefox 8, and Chrome 14 submitted by Karsten Knuth submitted January 14, 2012 Supervisor Prof. Dr. Michael Backes Advisors Raphael Reischuk Sebastian Gerling Reviewers Prof. Dr. Michael Backes Dr. Matteo Maffei Statement in Lieu of an Oath I hereby confirm that I have written this thesis on my own and that I have not used any other media or materials than the ones referred to in this thesis. Saarbr¨ucken, January 14, 2012 Karsten Knuth Declaration of Consent I agree to make both versions of my thesis (with a passing grade) accessible to the public by having them added to the library of the Computer Science Department. Saarbr¨ucken, January 14, 2012 Karsten Knuth Acknowledgments First of all, I thank Professor Dr. Michael Backes for giving me the chance to write my bachelor's thesis at the Information Security & Cryptography chair. During the making of this thesis I have gotten a deeper look in a topic which I hope to be given the chance to follow up in my upcoming academic career. Furthermore, I thank my advisors Raphael Reischuk, Sebastian Gerling, and Philipp von Styp-Rekowsky for supporting me with words and deeds during the making of this thesis. In particular, I thank the first two for bearing with me since the release of my topic. My thanks also go to Lara Schneider and Michael Zeidler for offering me helpful advice. -

Optimizing Windows 10, Build 2004, for a Virtual Desktop Role
Optimizing Windows 10, Build 2004, for a Virtual Desktop role Written by Robert M. Smith, Program Manager, Azure Global Customer Engineering Date Created: May 12, 2020 Date Updated: July 08, 2020 Date Published: tbd Contributors: Tim Muessig, Senior Premier Field Engineer; Narklis Engler, Principal Program Manager Version 1.2 Document Change History Version Changes 1.0 Adding verbiage for Windows Virtual Desktop, and Windows 10 build 2004 specifically 1.1 Additional updates for 2004 1.2 Final pass, updated group policy, services, tasks, and added info about Storage Sense for disk cleanup. Introduction This article is intended to provide suggestions for configurations for Windows 10, build 2004, for optimal performance in Virtualized Desktop environments, including Virtual Desktop Infrastructure (VDI) and Windows Virtual Desktop (WVD). All settings in this guide are suggested optimization settings only and are in no way requirements. The information in this guide is pertinent to Windows 10, version 2004, operating system (OS) build 19041. The guiding principles to optimize performance of Windows 10 in a virtual desktop environment are to minimize graphic redraws and “effects”, background activities that have no major benefit to the virtual desktop environment, and generally reduce running processes to the bare minimum. A secondary goal is to reduce disk space usage in the base image to the bare minimum. With virtual desktop implementations, the smallest possible base, or “gold” image size, can slightly reduce memory utilization on the host system, as well as a small reduction in overall network operations required to deliver the desktop environment to the consumer. No optimizations should reduce the user experience. -

ASP.NET Developer Guidance Map
ASP.NET Developer Guidance Map J.D. Meier, Principal PM, Microsoft http://blogs.msdn.com/jmeier Contents at a Glance • Introduction • Sources of ASP.NET Developer Guidance • Topics and Features Map (a “Lens” for Finding ASP.NET Content) • Summary Table of Topics • How The Map is Organized (Organizing the “Content Collections”) • Getting Started • Architecture and Design • Code Samples • How Tos • Videos • Training Introduction Welcome to the Microsoft ASP.NET Developer Guidance Map! This map is a consolidated index of ASP.NET content collections for developers. The primary content collections included in this map are: Code Samples, How Tos, Videos, and Training. Within the content collections, the resources are organized by ASP.NET features, common tasks, and common categories for ASP.NET. Usage Scenarios • Use the map to discover the various sources of developer content at Microsoft • Use the map to find some of the most useful content for helping you solve your problems with ASP.NET • Use the map as an example to help you create your own map of content resources Mental Model ASP.NET Developer Guidance Map (Mental Model) Sources Lens Content Collections Code How Tos Videos Training q Documentation Samples q Dev Centers Topics q MDSN Library q Channel9 Tasks q Code Gallery q Forums Features q … etc. Types Sources of ASP.NET Developer Guidance You can think of this as a “topology map” of some of the main sources of ASP.NET developer guidance from Microsoft. Simply by knowing what types of resources are available (code, forums, documentation, training, etc.), and by knowing where to look, you improve your success at finding the resources you need to get your job done, whether that’s figuring out how to code for a particular scenario, ramping up on the technology, or finding the latest news. -

Eventtracker V7.1 Enterprise User Guide
EventTracker Enterprise User Guide Version 7.3 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com Copyright All intellectual property rights in this work belong to Prism Microsystems, Inc. The information contained in this work must not be reproduced or distributed to others in any form or by any means, electronic or mechanical, for any purpose, without the prior permission of Prism Microsystems, Inc., or used except as expressly authorized in writing by Prism Microsystems, Inc. Copyright © 1999 - 2012 Prism Microsystems, Inc. All Rights Reserved. Trademarks All company, brand and product names are referenced for identification purposes only and may be trademarks or registered trademarks that are the sole property of their respective owners. Disclaimer Prism Microsystems, Inc. reserves the right to make changes to this manual and the equipment described herein without notice. Prism Microsystems, Inc. has made all reasonable efforts to ensure that the information in this manual is accurate and complete. However, Prism Microsystems, Inc. shall not be liable for any technical or editorial errors or omissions made herein or for incidental, special, or consequential damage of whatsoever nature resulting from the furnishing of this manual, or operation and performance of equipment in connection with this manual. EventTracker Ver.7.3 Enterprise User Guide Contents Contents About this Guide ................................................................................................................................... -

코딩 예제) Window.External.Isserviceinstalled( „Map');
웹 서비스의 한계를 넘어 - IE8 for Developer 한국마이크로소프트 개발자 및 플랫폼 사업 본부 차세대 웹 플랫폼 팀 김대우 http://www.uxkorea.net IE8 for Developer!!! 웹 개발자를 위한 IE8 디버깅 Accelerator Web Slice Visual Search 웹 개발자를 위한 IE8 디버깅 시작은 F12 한눈에 보이는 HTML DOM CSS 벗기기 Script 디버깅 프로파일러 브라우져 호홖성 체크 … Accelerator 현재 보고 있는 사이트에서 기존의 서비스로 직접 연결가능 Web Slice 웹의 다양한 컨텐츠를 빠르게 조회 사용자의 직접적인 구독 UI 모듈을 최소화한 개발 가능 Visual Search 다양한 검색 제공자로부터 빠른 검색을 수행 시각적인 검색 제공 UI모듈 개발 필요 없음 Guest - Auction Accelerator Accelerator – Developer Web 페이지의 컨텐츠와 다양한 온라인 서비스를 갂단한 동작으로 제휴 기능 추가적인 클라이언트 UI 개발 필요 없음 – 개발 모듈 최소화 표준 XML기반 OpenService 포맷 XML 문서 기반 Accelerator 등록 제공 Accelerator – Developer <?xml version="1.0" encoding="utf-8" ?> <openServiceDescription xmlns="http://www.microsoft.com/schemas/openservicedescription/1.0"> <homepageUrl>http://maps.live.com</homepageUrl> <display> <name>Live Maps 지도 서비스</name> <icon>http://maps.live.com/favicon.ico</icon> </display> <activity category="Map"> <activityAction context="selection"> <execute method="get“ action="http://maps.live.com/default.aspx?where1={selection}" /> <preview method="get" action="http://maps.live.com/geotager.aspx"> <parameter name="b" value="{selection}" /> <parameter name="clean" value="true" /> <parameter name="w" value="320" /> <parameter name="h" value="240" /> <parameter name="format" value="full" /> </preview> </activityAction> </activity> </openServiceDescription> Accelerator – OpenService 포맷 Accelerator의 XML 네임 스페이스 <openServiceDescription xmlns="http://www.microsoft.com/schemas/openservicedescription/1.0"> homepageUrl:Accelerator에 의해 액세스하는 Web 서비스의 URL <homepageUrl>http://maps.live.com</homepageUrl> diaplay:Accelerator의 메뉴에 표시되는 항목 <display> <name>Live Maps의 지도</name> <icon>http://maps.live.com/favicon.ico</icon> </display> activity:Accelerator의 동작 설정 - category :Accelerator가 제공하는 기능별로 그룹화 Map: Windows Live Map, Google Maps Blog: Windows Live Spaces, Blogger Define: Encarta, Wikipedia Add: Del.icio.us ··· <activity category="Map“> Accelerator – OpenService 포맷 context : Accelerator가 동작할 때 데이터 형식 설정 - 디폴트 「selection」 - 「selection」. -
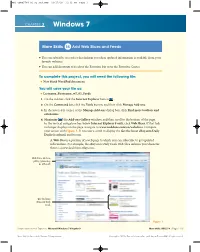
More Skills 14 Add Web Slices and Feeds
M03_TOWN5764_01_SE_SM3.QXD 11/17/10 11:13 AM Page 1 CHAPTER 3 Windows 7 More Skills 14 Add Web Slices and Feeds ᭤ You can subscribe to services that inform you when updated information is available from your favorite websites. ᭤ You can add shortcuts to feeds to the Favorites bar or to the Favorites Center. To complete this project, you will need the following file: New blank WordPad document You will save your file as: Lastname_Firstname_w7_03_Feeds 1. On the taskbar, click the Internet Explorer button . 2. On the Command bar, click the Tools button, and then click Manage Add-ons. 3. In the lower-left corner of the Manage Add-ons dialog box, click Find more toolbars and extensions. 4. Maximize the Add-ons Gallery window, and then scroll to the bottom of the page. In the vertical navigation bar, below Internet Explorer 8 only, click Web Slices. If that link no longer displays on the page, navigate to www.ieaddons.com/en/webslices. Compare your screen with Figure 1. If necessary, scroll to display the Get the latest eBay.com Daily Deals thumbnail and button. A Web Slice is a portion of a web page to which you can subscribe to get updated information. For example, the eBay.com Daily Deals Web Slice informs you whenever there is a new deal from eBay.com. Web Slices add-ons gallery (yours may be different) Get the latest eBay.com Daily Deals Figure 1 Browse with Internet Explorer | Microsoft Windows 7 Chapter 3 More Skills: SKILL 14 | Page 1 of 5 From Skills for Success with Windows 7 Comprehensive Copyright © 2011 by Pearson Education Inc. -

Basic Christian 2008 G Christian Information, Links, Resources and Free Downloads
Friday, November 7, 2008 19:44 GMT Basic Christian 2008 G Christian Information, Links, Resources and Free Downloads Copyright © 2004-2008 David Anson Brown http://www.basicchristian.org/ Updated: Final 2008 Version *** Updated 11-04-2008 - The BasicChristian.org Website Articles Version 2008 (PDF) - Now Available (1051 Pages) Basic Christian Full Content PDF Version 2008. The BasicChristian.org most complete resource. http://www.basicchristian.us/downloads/BasicChristian.pdf Updated: Final 2008 Version FREE Download - Basic Christian Complete - eBook Version (.CHM) Possibly the best Basic Christian resource! Download it and give it a try!Includes the Red Letter Edition Holy Bible KJV 1611 Version. To download Right-Click then Select Save Target _As... http://www.basicchristian.us/downloads/BasicChristian.CHM --New Article-- The 7 Church Letters of Revelation from Jesus Christ - The Christian Church is divided into Seven Church groups - Which Church group are You in? Like the seven miracles that we went through in the Gospel of John that John himself personally witnessed, Jesus personally spoke to the disciple John and had John write an evaluation of the Christian Church in the book of Revelation - Likewise to critique the entire Christian Church (people) Jesus divided it up into seven churches. Each Church existed in the day that Jesus spoke to John about it and each Church type is still practiced throughout today. Note the book of Revelation and in particular the part about the seven churches is unique because Jesus is asking John to write it for Him. The entire Bible is written by God through man but Revelation makes that point even more evident.