C24/2007 SOFTWARE-KOLLEKTION 7
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Directory Opus 6 Kurzanleitung
Directory Opus 6 für Windows Anleitung Copyright © 2007 HAAGE & PARTNER Computer GmbH, Deutschland Seite 1 von 58 Directory Opus 6 für Windows Anleitung Inhalt 1. Willkommen....................................................................................................................3 2. Die Installation ...............................................................................................................5 2.1. Voraussetzungen ......................................................................................................5 2.2. Installieren von Directory Opus 6 ..............................................................................5 2.3. Online-Registrierung .................................................................................................6 2.4. Der erste Start...........................................................................................................7 3. Einführung und Übersicht...........................................................................................10 3.1. Die Komponenten von Directory Opus....................................................................10 3.2. Grundlegende Konzepte: Wie Opus arbeitet...........................................................12 4. Erste Schritte ...............................................................................................................16 5. Einstellungen ...............................................................................................................19 5.1. Einstellungen...........................................................................................................19 -

The Apple Ecosystem
APPENDIX A The Apple Ecosystem There are a lot of applications used to manage Apple devices in one way or another. Additionally, here’s a list of tools, sorted alphabetically per category in order to remain vendor agnostic. Antivirus Solutions for scanning Macs for viruses and other malware. • AVG: Basic antivirus and spyware detection and remediation. • Avast: Centralized antivirus with a cloud console for tracking incidents and device status. • Avira: Antivirus and a browser extension. Avira Connect allows you to view device status online. • BitDefender: Antivirus and malware managed from a central console. • CarbonBlack: Antivirus and Application Control. • Cylance: Ransomware, advanced threats, fileless malware, and malicious documents in addition to standard antivirus. • Kaspersky: Antivirus with a centralized cloud dashboard to track device status. © Charles Edge and Rich Trouton 2020 707 C. Edge and R. Trouton, Apple Device Management, https://doi.org/10.1007/978-1-4842-5388-5 APPENDIX A THe AppLe ECOSYSteM • Malware Bytes: Antivirus and malware managed from a central console. • McAfee Endpoint Security: Antivirus and advanced threat management with a centralized server to track devices. • Sophos: Antivirus and malware managed from a central console. • Symantec Mobile Device Management: Antivirus and malware managed from a central console. • Trend Micro Endpoint Security: Application whitelisting, antivirus, and ransomware protection in a centralized console. • Wandera: Malicious hot-spot monitoring, jailbreak detection, web gateway for mobile threat detection that integrates with common MDM solutions. Automation Tools Scripty tools used to automate management on the Mac • AutoCasperNBI: Automates the creation of NetBoot Images (read: NBI’s) for use with Casper Imaging. • AutoDMG: Takes a macOS installer (10.10 or newer) and builds a system image suitable for deployment with Imagr, DeployStudio, LANrev, Jamf Pro, and other asr or Apple Systems Restore-based imaging tools. -
PDF File .Pdf
Software Learn what software is available and the installation processes. General Software Software Availability (link) Service Level Agreements How to Register for & Purchase Software from the Spartan Store Setting Up Slack Desktop Notifications Flickr FAQ Import and export Firefox bookmarks Installing Web Browser Extensions: Google Chrome, Safari, FireFox Recommended Software (link) Remote Software & Computer Access Procedure General Software Information Reference Page (Link) Operating Systems Recommended Operating Systems: MacOS & Windows Computer Backup Computer Storage Management Computer Performance Change your macOS Login Password Change your Windows 10 Login Password Backing Up with Windows File History Change the Default Application Associated with a File Type How do I install device drivers? Help for New Mac Users Start your Windows Computer in Safe Mode macOS Startup Key Commands Use VirtualBox to Create a Windows Virtual Machine Create a Disk Image Backup with Macrium Reflect Microsoft Office Request Microsoft Office for State-Owned Computers Microsoft Office Installation for Students Microsoft Office 365 Info and Tutorials Configure Office to Save in Compatibility Mode OneDrive Image Management FAQ Using PowerPoint's Presenter View Saving a Portable PowerPoint Presentation How do I Uninstall Office? Word, Excel, or PowerPoint Crashes or Freezes (macOS) Converting your PowerPoint Presentation to Widescreen (16:9) Convert Columns to Rows, or Rows to Columns using Excel Adobe Adobe Creative Cloud Information & Installation Save -

W32.Ramnit Analysis
W32.Ramnit analysis SECURITY RESPONSE W32.Ramnit analysis Symantec Security Response Version 1.0 – February 24, 2015, 12:00 GMT It is estimated that the Ramnit botnet may consist of up to 350,000 compromised computers worldwide. CONTENTS SUMMARY ..................................................................... 3 Overview ....................................................................... 4 Operations ..................................................................... 6 Victims .......................................................................... 8 Technical analysis of W32.Ramnit.B ........................... 10 Overview ................................................................ 10 Exploit usage ......................................................... 11 Anti-analysis .......................................................... 11 Installer ................................................................. 11 Device driver .......................................................... 14 Embedded DLL_1 .................................................. 14 DLL_2 .................................................................... 16 Communications ................................................... 18 Master boot record infection routine .................... 19 Ramnit modules .................................................... 24 Detection guidance ..................................................... 30 Network traffic ...................................................... 30 Yara signature ...................................................... -

DLCC Software Catalog
Daniel's Legacy Computer Collections Software Catalog Category Platform Software Category Title Author Year Media Commercial Apple II Integrated Suite Claris AppleWorks 2.0 Claris Corporation and Apple Computer, Inc. 1987 800K Commercial Apple II Operating System Apple IIGS System 1.0.2 --> 1.1.1 Update Apple Computer, Inc. 1984 400K Commercial Apple II Operating System Apple IIGS System 1.1 Apple Computer, Inc. 1986 800K Commercial Apple II Operating System Apple IIGS System 2.0 Apple Computer, Inc. 1987 800K Commercial Apple II Operating System Apple IIGS System 3.1 Apple Computer, Inc. 1987 800K Commercial Apple II Operating System Apple IIGS System 3.2 Apple Computer, Inc. 1988 800K Commercial Apple II Operating System Apple IIGS System 4.0 Apple Computer, Inc. 1988 800K Commercial Apple II Operating System Apple IIGS System 5.0 Apple Computer, Inc. 1989 800K Commercial Apple II Operating System Apple IIGS System 5.0.2 Apple Computer, Inc. 1989 800K Commercial Apple II Reference: Programming ProDOS Basic Programming Examples Apple Computer, Inc. 1983 800K Commercial Apple II Utility: Printer ImageWriter Toolkit 1.5 Apple Computer, Inc. 1984 400K Commercial Apple II Utility: User ProDOS User's Disk Apple Computer, Inc. 1983 800K Total Apple II Titles: 12 Commercial Apple Lisa Emulator MacWorks 1.00 Apple Computer, Inc. 1984 400K Commercial Apple Lisa Office Suite Lisa 7/7 3.0 Apple Computer, Inc. 1984 400K Total Apple Lisa Titles: 2 Commercial Apple Mac OS 0-9 Audio Audioshop 1.03 Opcode Systems, Inc. 1992 800K Commercial Apple Mac OS 0-9 Audio Audioshop 2.0 Opcode Systems, Inc. -

Paul Collins Status Name/Startup Item Command Comments X System32
SYSINFO.ORG STARTUP LIST : 11th June 2006 (c) Paul Collins Status Name/Startup Item Command Comments X system32.exe Added by the AGOBOT-KU WORM! Note - has a blank entry under the Startup Item/Name field X pathex.exe Added by the MKMOOSE-A WORM! X svchost.exe Added by the DELF-UX TROJAN! Note - this is not the legitimate svchost.exe process which is always located in the System (9x/Me) or System32 (NT/2K/XP) folder and should not normally figure in Msconfig/Startup! This file is located in the Winnt or Windows folder X SystemBoot services.exe Added by the SOBER-Q TROJAN! Note - this is not the legitimate services.exe process which is always located in the System (9x/Me) or System32 (NT/2K/XP) folder and should not normally figure in Msconfig/Startup! This file is located in a HelpHelp subfolder of the Windows or Winnt folder X WinCheck services.exe Added by the SOBER-S WORM! Note - this is not the legitimate services.exe process which is always located in the System (9x/Me) or System32 (NT/2K/XP) folder and should not normally figure in Msconfig/Startup! This file is located in a "ConnectionStatusMicrosoft" subfolder of the Windows or Winnt folder X Windows services.exe Added by the SOBER.X WORM! Note - this is not the legitimate services.exe process which is always located in the System (9x/Me) or System32 (NT/2K/XP) folder and should not normally figure in Msconfig/Startup! This file is located in a "WinSecurity" subfolder of the Windows or Winnt folder X WinStart services.exe Added by the SOBER.O WORM! Note - this is not the legitimate -

What Is the Contribution of Personal Information Management Systems (PIMS) to the Working Model and Personal Work System of Knowledge Workers?
Open Research Online The Open University’s repository of research publications and other research outputs What is the contribution of personal information management systems (PIMS) to the Working Model and personal work system of knowledge workers? Thesis How to cite: Gregory, Mark Roger (2017). What is the contribution of personal information management systems (PIMS) to the Working Model and personal work system of knowledge workers? PhD thesis The Open University. For guidance on citations see FAQs. c 2016 The Author Version: Version of Record Copyright and Moral Rights for the articles on this site are retained by the individual authors and/or other copyright owners. For more information on Open Research Online’s data policy on reuse of materials please consult the policies page. oro.open.ac.uk What is the contribution of personal information management systems (PIMS) to the Working Model and personal work system of knowledge workers? Mark Gregory, B.Sc. (Hons), M.Sc. Thesis submitted in partial fulfilment of the requirements for the degree of Ph.D. in Information Systems December 2016 The Open University Rennes School of Business Affiliated Research Centre ARC Supervisors: Prof. David Weir (Visiting Professor at York St John University) Dr. Renaud Macgilchrist (Rennes School of Business) Examiners: Prof. Trevor Wood-Harper (Manchester Business School) Dr. Tom Mcnamara (Rennes School of Business) 1 / 343 Abstract The thesis reports research into a phenomenon which it calls the personal working model of an individual knowledge worker. The principal conjecture addressed in this thesis is that each of us has a personal working model which is supported by a personal work system enabled by a personal information management system. -

Directory Opus 9
Reference Manual Directory Opus 9 (c) GPSoftware, Brisbane, 2008 Reference Manual Directory Opus 9 Contents · i Contents Copyright Notice ..................................................................................................................1 Program License...................................................................................................................2 Acknowledgments ................................................................................................................4 Introduction and Overview 6 System Requirements............................................................................................................7 Installing and Registering Directory Opus 9 ..........................................................................8 Launching Opus for the First Time......................................................................................10 Welcome to Directory Opus................................................................................................11 Summary ..............................................................................................................11 Directory Opus 9 Components 13 Overview............................................................................................................................14 New Features for Version 9 17 New Vista related ...............................................................................................................17 New Explorer Replacement Changes...................................................................................18 -

CIT381 COURSE TITLE: File Processing and Management
NATIONAL OPEN UNIVERSITY OF NIGERIA SCHOOL OF SCIENCE AND TECHNOLOGY COURSE CODE: CIT381 COURSE TITLE: File Processing and Management CIT381 COURSE GUIDE COURSE GUIDE CIT381 FILE PROCESSING AND MANAGEMENT Course Team Ismaila O. Mudasiru (Developer/Writer) - OAU NATIONAL OPEN UNIVERSITY OF NIGERIA ii CIT381 COURSE GUIDE National Open University of Nigeria Headquarters 14/16 Ahmadu Bello Way Victoria Island Lagos Abuja Office No. 5 Dar es Salaam Street Off Aminu Kano Crescent Wuse II, Abuja Nigeria e-mail: [email protected] URL: www.nou.edu.ng Published By: National Open University of Nigeria First Printed 2011 ISBN: 978-058-525-7 All Rights Reserved CONTENTS PAGE iii CIT381 COURSE GUIDE Introduction …………………..…………………………………… 1 What You Will Learn in this Course………………………………. 1 Course Aims ………………………………………………………. 2 Course Objectives …………………………………………………. 2 Working through this Course………………………….…………… 3 The Course Materials………………………………………………. 3 Study Units…………………………………………………………. 3 Presentation Schedule……………….……………………………… 4 Assessment…………………………………………………………. 5 Tutor-Marked Assignment…………………………………………. 5 Final Examination and Grading……………………………………. 6 Course Marking Scheme…………………………………………… 6 Facilitators/Tutors and Tutorials…………………………………… 6 Summary…………………………………………………………… 7 iv CIT381 FILE PROCESSING AND MANAGEMENT Introduction File Processing and Management is a second semester course. It is a 2- credit course that is available to students offering Bachelor of Science, B. Sc., Computer Science, Information Systems and Allied degrees. Computers can store information on several different types of physical media. Magnetic tape, magnetic disk and optical disk are the most common media. Each of these media has its own characteristics and physical organisation. For convenience use of the computer system, the operating system provides a uniform logical view of information storage. The operating system abstracts from the physical properties of its storage devices to define a logical storage unit, the file. -

ВНУТРИ UBUNTU О Космических Полетах И Open- Source С.62 KOFFICE 1.4 KDE Наносит Ответный Удар! ЧИТАЮТ ВСЕ ПОЛЬЗОВАТЕЛИ LINUX С
• KOFFICE 1.4 • НАСТОЛЬНЫЙ LINUX • ФАЙЛОВЫЕ МЕНЕДЖЕРЫ • CAIRO • SUPER SUDOKU • ВНУТРИ UBUNTU О космических полетах и open- source с.62 KOFFICE 1.4 KDE наносит ответный удар! ЧИТАЮТ ВСЕ ПОЛЬЗОВАТЕЛИ LINUX с. 18 №2(71) октябрь 2005 БЛОКИРУЕМ все необходимое для защиты вашего ХАКЕРОВ! компьютера • SSH • Bastille Linux • Брандмауэры • PGP • SELinux • Антивирусы ФАЙЛОВЫЕ УЧЕБНИКИ НА ЛЮБОЙ ВКУС МЕНЕДЖЕРЫ ПРИГОТОВЬТЕ ПЕРО И БУМАГУ Отделяем зерна от плевел с.30 Сжатие файлов с.74 Гель для GIMP с.80 ДНЕВНИКИ LINUX Знакомство с Gnuplot с.78 Вихри времени доносят дурные Программируем на Gambas с.86 вести – это и есть судьба Linux? с.56 PHP – и никаких коз с.90 «Кто-то дал мне упаковку с шестью банками пива и стопку дискет со Slackware. Так все и началось» Марк Шаттлворт с.62 добро поЖАЛовАтЬ Мой дом – К вАшим усЛуГАм... безопасность – главное слово этого выпуска. Мы моя крепость отправили сотрудникам редакции шифрованное сообщение, в котором спрашивалось: «Что может безопасность – это необходимое зло. Поскольку за миром IT заставить вас выдать свой пароль постороннему никто не присматривает, кто-нибудь обязательно захочет просто человеку? прийти и взять – ну или хотя бы попробовать. безопасность – зло, поскольку необходимые меры всегда очень назойливы. Лет 10 назад у меня был один PIN-код и пара паролей, а сейчас у меня – 12 пол Хадсон Грэхэм моррисон учетных записей, дюжина невесть откуда взявшихся девичьих фамилий «Согласен написать на «Угроза теста Войта- шоколадке. конечно, это не кампффа и различные матери и секретные вопросы, не поддающиеся запоминанию. будет мой настоящий пароль вопросы о черепахах, – он займет две лежащих на спине где-то в шоколадки» пустыне.» различные требования и реализации защитных систем в Интернете еще больше сбивают с толку простого пользователя и мешают ему запомнить информацию о себе. -
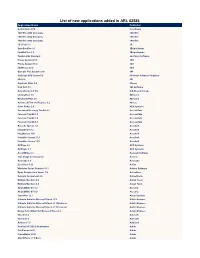
List of New Applications Added in ARL #2586
List of new applications added in ARL #2586 Application Name Publisher NetCmdlets 2016 /n software 1099 Pro 2009 Corporate 1099 Pro 1099 Pro 2020 Enterprise 1099 Pro 1099 Pro 2008 Corporate 1099 Pro 1E Client 5.1 1E SyncBackPro 9.1 2BrightSparks FindOnClick 2.5 2BrightSparks TaxAct 2002 Standard 2nd Story Software Phone System 15.5 3CX Phone System 16.0 3CX 3CXPhone 16.3 3CX Grouper Plus System 2021 3M CoDeSys OPC Server 3.1 3S-Smart Software Solutions 4D 15.0 4D Duplicate Killer 3.4 4Team Disk Drill 4.1 508 Software NotesHolder 2.3 Pro A!K Research Labs LibraryView 1.0 AB Sciex MetabolitePilot 2.0 AB Sciex Advanced Find and Replace 5.2 Abacre Color Picker 2.0 ACA Systems Password Recovery Toolkit 8.2 AccessData Forensic Toolkit 6.0 AccessData Forensic Toolkit 7.0 AccessData Forensic Toolkit 6.3 AccessData Barcode Xpress 7.0 AccuSoft ImageGear 17.2 AccuSoft ImagXpress 13.6 AccuSoft PrizmDoc Server 13.1 AccuSoft PrizmDoc Server 12.3 AccuSoft ACDSee 2.2 ACD Systems ACDSync 1.1 ACD Systems Ace Utilities 6.3 Acelogix Software True Image for Crucial 23. Acronis Acrosync 1.6 Acrosync Zen Client 5.10 Actian Windows Forms Controls 16.1 Actipro Software Opus Composition Server 7.0 ActiveDocs Network Component 4.6 ActiveXperts Multiple Monitors 8.3 Actual Tools Multiple Monitors 8.8 Actual Tools ACUCOBOL-GT 5.2 Acucorp ACUCOBOL-GT 8.0 Acucorp TransMac 12.1 Acute Systems Ultimate Suite for Microsoft Excel 13.2 Add-in Express Ultimate Suite for Microsoft Excel 21.1 Business Add-in Express Ultimate Suite for Microsoft Excel 21.1 Personal Add-in Express -

Win32/Kelihos
Win32/Kelihos http://www.securityhome.eu/malware/malware.php?mal_id=2141573224e82ba04891fc9.31999277 Win32/Kelihos Article URL malware.php?mal_id=2141573224e82ba04891fc9.31999277 Author SecurityHome.eu Published: 28 September 2011 Aliases : There are no other names known for Win32/Kelihos . Explanation : Win32/Kelihos is a trojan family that distributes spam email messages. The spam messages could contain hyperlinks to installers of Win32/Kelihos malware. The malware may communicate with remote servers to exchange information that is used to execute various tasks, including sending spam email, capturing sensitive information or downloading and executing arbitrary files. Top Win32/Kelihos is a trojan family that distributes spam email messages. The spam messages could contain hyperlinks to installers of Win32/Kelihos malware. The malware may communicate with remote servers to exchange information that is used to execute various tasks, including sending spam email, capturing sensitive information or downloading and executing arbitrary files. Installation When run, Win32/Kelihos creates a shared memory object, or "section object", named "GoogleImpl" to ensure only one instance of the trojan executes at a time. The registry is modified to run Win32/Kelihos at each Windows start: In subkey: HKLMSOFTWAREMicrosoftWindowsCurrentVersionRun Sets value: "SmartIndex" Page 1/7 Win32/Kelihos http://www.securityhome.eu/malware/malware.php?mal_id=2141573224e82ba04891fc9.31999277 With data: "<path and file name of Win32/Kelihos trojan>" Some variants may also install WinPcap, a legitimate and commonly used Windows packet capture library, as the following files: * <system folder>packet.dll * <system folder>wpcap.dll * <system folder>driversnpf.sys These files are not malicious themselves, but Kelihos uses them to spy on the affected computer€™s network activities.