What Is the Contribution of Personal Information Management Systems (PIMS) to the Working Model and Personal Work System of Knowledge Workers?
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Directory Opus 6 Kurzanleitung
Directory Opus 6 für Windows Anleitung Copyright © 2007 HAAGE & PARTNER Computer GmbH, Deutschland Seite 1 von 58 Directory Opus 6 für Windows Anleitung Inhalt 1. Willkommen....................................................................................................................3 2. Die Installation ...............................................................................................................5 2.1. Voraussetzungen ......................................................................................................5 2.2. Installieren von Directory Opus 6 ..............................................................................5 2.3. Online-Registrierung .................................................................................................6 2.4. Der erste Start...........................................................................................................7 3. Einführung und Übersicht...........................................................................................10 3.1. Die Komponenten von Directory Opus....................................................................10 3.2. Grundlegende Konzepte: Wie Opus arbeitet...........................................................12 4. Erste Schritte ...............................................................................................................16 5. Einstellungen ...............................................................................................................19 5.1. Einstellungen...........................................................................................................19 -
Isys Information Architects Inc
Isys Information Architects Inc. Home Design Announcements Hall of Shame Isys Information Architects Inc. specializes in the design and development of New Entries robust, highly usable information systems. Isys focuses on ease of use, recognizing Controls that software should assist the user in the performance of some task rather than Stupidity becoming a task in itself. Isys was founded by Brian Hayes, a former professor of Visual Color Industrial Engineering, and system design consultant whose clients have included Terminology AT&T, General Electric, General Motors, Lucent Technologies, NASA, Siemens, Errors the U.S. Air Force, and the U.S. Army. Tabs Metaphors We are a full-service Our software development Globalization provider of user interface department specializes in the In-Depth design and usability design and development of engineering services. Our careful robust, highly usable information Books systems for the Windows operating Links attention to the user interface can system. We provide custom Index reduce system development time, Feedback increase user satisfaction, and reduce programming, database, and training costs. application development services. Hall of Fame Contact Us The Interface Hall of Shame The Interface Hall of is an irreverent look at Fame is a collection of ineffective interface design. images that demonstrate The site includes a collection of interface design solutions that are images from commercial, corporate, both creative and effective. and shareware applications that illustrate how software should not be designed. Isys Information Architects Inc. 5401 McNairy Drive, Suite 100 Greensboro, NC 27455 [email protected] © 1996-1999 Isys Information Architects Inc. All rights reserved. Reproduction in whole or in part in any form or medium without express written permission is prohibited. -

Good Cybernetics Is a Must in Policy Processes
Good social cybernetics is a must in policy processes. Structured Abstract: Purpose Illustrate supported by Beer’s Viable System Model and four vignettes the relevance of self-organisation, recursive structures, self-reference and reflexivity in policy processes. Design, Methodology, Approach First, the concepts of self-organisation, recursive structures, self-reference and reflexivity are briefly discussed to ground policy processes in good cybernetics. Then, with the support of four vignettes, the idea of good cybernetics in policies processes is illustrated. Findings The cybernetics of policy processes is often ignored. Limitations If the purpose of this paper were to influence policy-makers it would be necessary to further the empirical base of the four vignettes and clarify desirable forums to ground the relevance of self-organisation, recursive structures, self-reference and reflexivity in policy processes. Practical and Social Implications Beer’s recursive structures, self-reference and reflexivity have much to contribute to the betterment of policy processes and the amelioration of the unbearable social and organisational costs of many current policies. Originality The application of concepts such as self-organisation, recursive structures, self-reference and reflexivity adds to our understanding of policy processes. Keywords: Viable System Model, policy processes, self-organisation, structural recursion, self-reference, reflexivity Article Classification: Conceptual paper Introduction Policy processes are necessary to respond to issues such as development of clean energy, child care, transparent marketing, economic development and so forth. Multiple social and economic agents interact in the creation, regulation and production of these policies and through these interactions, mostly by self-organisation, they produce organisational systems. Self-organisation brings together social agents as they find common purposes and recognise the need to interact. -

W32.Ramnit Analysis
W32.Ramnit analysis SECURITY RESPONSE W32.Ramnit analysis Symantec Security Response Version 1.0 – February 24, 2015, 12:00 GMT It is estimated that the Ramnit botnet may consist of up to 350,000 compromised computers worldwide. CONTENTS SUMMARY ..................................................................... 3 Overview ....................................................................... 4 Operations ..................................................................... 6 Victims .......................................................................... 8 Technical analysis of W32.Ramnit.B ........................... 10 Overview ................................................................ 10 Exploit usage ......................................................... 11 Anti-analysis .......................................................... 11 Installer ................................................................. 11 Device driver .......................................................... 14 Embedded DLL_1 .................................................. 14 DLL_2 .................................................................... 16 Communications ................................................... 18 Master boot record infection routine .................... 19 Ramnit modules .................................................... 24 Detection guidance ..................................................... 30 Network traffic ...................................................... 30 Yara signature ...................................................... -

DLCC Software Catalog
Daniel's Legacy Computer Collections Software Catalog Category Platform Software Category Title Author Year Media Commercial Apple II Integrated Suite Claris AppleWorks 2.0 Claris Corporation and Apple Computer, Inc. 1987 800K Commercial Apple II Operating System Apple IIGS System 1.0.2 --> 1.1.1 Update Apple Computer, Inc. 1984 400K Commercial Apple II Operating System Apple IIGS System 1.1 Apple Computer, Inc. 1986 800K Commercial Apple II Operating System Apple IIGS System 2.0 Apple Computer, Inc. 1987 800K Commercial Apple II Operating System Apple IIGS System 3.1 Apple Computer, Inc. 1987 800K Commercial Apple II Operating System Apple IIGS System 3.2 Apple Computer, Inc. 1988 800K Commercial Apple II Operating System Apple IIGS System 4.0 Apple Computer, Inc. 1988 800K Commercial Apple II Operating System Apple IIGS System 5.0 Apple Computer, Inc. 1989 800K Commercial Apple II Operating System Apple IIGS System 5.0.2 Apple Computer, Inc. 1989 800K Commercial Apple II Reference: Programming ProDOS Basic Programming Examples Apple Computer, Inc. 1983 800K Commercial Apple II Utility: Printer ImageWriter Toolkit 1.5 Apple Computer, Inc. 1984 400K Commercial Apple II Utility: User ProDOS User's Disk Apple Computer, Inc. 1983 800K Total Apple II Titles: 12 Commercial Apple Lisa Emulator MacWorks 1.00 Apple Computer, Inc. 1984 400K Commercial Apple Lisa Office Suite Lisa 7/7 3.0 Apple Computer, Inc. 1984 400K Total Apple Lisa Titles: 2 Commercial Apple Mac OS 0-9 Audio Audioshop 1.03 Opcode Systems, Inc. 1992 800K Commercial Apple Mac OS 0-9 Audio Audioshop 2.0 Opcode Systems, Inc. -

Paul Collins Status Name/Startup Item Command Comments X System32
SYSINFO.ORG STARTUP LIST : 11th June 2006 (c) Paul Collins Status Name/Startup Item Command Comments X system32.exe Added by the AGOBOT-KU WORM! Note - has a blank entry under the Startup Item/Name field X pathex.exe Added by the MKMOOSE-A WORM! X svchost.exe Added by the DELF-UX TROJAN! Note - this is not the legitimate svchost.exe process which is always located in the System (9x/Me) or System32 (NT/2K/XP) folder and should not normally figure in Msconfig/Startup! This file is located in the Winnt or Windows folder X SystemBoot services.exe Added by the SOBER-Q TROJAN! Note - this is not the legitimate services.exe process which is always located in the System (9x/Me) or System32 (NT/2K/XP) folder and should not normally figure in Msconfig/Startup! This file is located in a HelpHelp subfolder of the Windows or Winnt folder X WinCheck services.exe Added by the SOBER-S WORM! Note - this is not the legitimate services.exe process which is always located in the System (9x/Me) or System32 (NT/2K/XP) folder and should not normally figure in Msconfig/Startup! This file is located in a "ConnectionStatusMicrosoft" subfolder of the Windows or Winnt folder X Windows services.exe Added by the SOBER.X WORM! Note - this is not the legitimate services.exe process which is always located in the System (9x/Me) or System32 (NT/2K/XP) folder and should not normally figure in Msconfig/Startup! This file is located in a "WinSecurity" subfolder of the Windows or Winnt folder X WinStart services.exe Added by the SOBER.O WORM! Note - this is not the legitimate -

Directory Opus 9
Reference Manual Directory Opus 9 (c) GPSoftware, Brisbane, 2008 Reference Manual Directory Opus 9 Contents · i Contents Copyright Notice ..................................................................................................................1 Program License...................................................................................................................2 Acknowledgments ................................................................................................................4 Introduction and Overview 6 System Requirements............................................................................................................7 Installing and Registering Directory Opus 9 ..........................................................................8 Launching Opus for the First Time......................................................................................10 Welcome to Directory Opus................................................................................................11 Summary ..............................................................................................................11 Directory Opus 9 Components 13 Overview............................................................................................................................14 New Features for Version 9 17 New Vista related ...............................................................................................................17 New Explorer Replacement Changes...................................................................................18 -

CIT381 COURSE TITLE: File Processing and Management
NATIONAL OPEN UNIVERSITY OF NIGERIA SCHOOL OF SCIENCE AND TECHNOLOGY COURSE CODE: CIT381 COURSE TITLE: File Processing and Management CIT381 COURSE GUIDE COURSE GUIDE CIT381 FILE PROCESSING AND MANAGEMENT Course Team Ismaila O. Mudasiru (Developer/Writer) - OAU NATIONAL OPEN UNIVERSITY OF NIGERIA ii CIT381 COURSE GUIDE National Open University of Nigeria Headquarters 14/16 Ahmadu Bello Way Victoria Island Lagos Abuja Office No. 5 Dar es Salaam Street Off Aminu Kano Crescent Wuse II, Abuja Nigeria e-mail: [email protected] URL: www.nou.edu.ng Published By: National Open University of Nigeria First Printed 2011 ISBN: 978-058-525-7 All Rights Reserved CONTENTS PAGE iii CIT381 COURSE GUIDE Introduction …………………..…………………………………… 1 What You Will Learn in this Course………………………………. 1 Course Aims ………………………………………………………. 2 Course Objectives …………………………………………………. 2 Working through this Course………………………….…………… 3 The Course Materials………………………………………………. 3 Study Units…………………………………………………………. 3 Presentation Schedule……………….……………………………… 4 Assessment…………………………………………………………. 5 Tutor-Marked Assignment…………………………………………. 5 Final Examination and Grading……………………………………. 6 Course Marking Scheme…………………………………………… 6 Facilitators/Tutors and Tutorials…………………………………… 6 Summary…………………………………………………………… 7 iv CIT381 FILE PROCESSING AND MANAGEMENT Introduction File Processing and Management is a second semester course. It is a 2- credit course that is available to students offering Bachelor of Science, B. Sc., Computer Science, Information Systems and Allied degrees. Computers can store information on several different types of physical media. Magnetic tape, magnetic disk and optical disk are the most common media. Each of these media has its own characteristics and physical organisation. For convenience use of the computer system, the operating system provides a uniform logical view of information storage. The operating system abstracts from the physical properties of its storage devices to define a logical storage unit, the file. -

ВНУТРИ UBUNTU О Космических Полетах И Open- Source С.62 KOFFICE 1.4 KDE Наносит Ответный Удар! ЧИТАЮТ ВСЕ ПОЛЬЗОВАТЕЛИ LINUX С
• KOFFICE 1.4 • НАСТОЛЬНЫЙ LINUX • ФАЙЛОВЫЕ МЕНЕДЖЕРЫ • CAIRO • SUPER SUDOKU • ВНУТРИ UBUNTU О космических полетах и open- source с.62 KOFFICE 1.4 KDE наносит ответный удар! ЧИТАЮТ ВСЕ ПОЛЬЗОВАТЕЛИ LINUX с. 18 №2(71) октябрь 2005 БЛОКИРУЕМ все необходимое для защиты вашего ХАКЕРОВ! компьютера • SSH • Bastille Linux • Брандмауэры • PGP • SELinux • Антивирусы ФАЙЛОВЫЕ УЧЕБНИКИ НА ЛЮБОЙ ВКУС МЕНЕДЖЕРЫ ПРИГОТОВЬТЕ ПЕРО И БУМАГУ Отделяем зерна от плевел с.30 Сжатие файлов с.74 Гель для GIMP с.80 ДНЕВНИКИ LINUX Знакомство с Gnuplot с.78 Вихри времени доносят дурные Программируем на Gambas с.86 вести – это и есть судьба Linux? с.56 PHP – и никаких коз с.90 «Кто-то дал мне упаковку с шестью банками пива и стопку дискет со Slackware. Так все и началось» Марк Шаттлворт с.62 добро поЖАЛовАтЬ Мой дом – К вАшим усЛуГАм... безопасность – главное слово этого выпуска. Мы моя крепость отправили сотрудникам редакции шифрованное сообщение, в котором спрашивалось: «Что может безопасность – это необходимое зло. Поскольку за миром IT заставить вас выдать свой пароль постороннему никто не присматривает, кто-нибудь обязательно захочет просто человеку? прийти и взять – ну или хотя бы попробовать. безопасность – зло, поскольку необходимые меры всегда очень назойливы. Лет 10 назад у меня был один PIN-код и пара паролей, а сейчас у меня – 12 пол Хадсон Грэхэм моррисон учетных записей, дюжина невесть откуда взявшихся девичьих фамилий «Согласен написать на «Угроза теста Войта- шоколадке. конечно, это не кампффа и различные матери и секретные вопросы, не поддающиеся запоминанию. будет мой настоящий пароль вопросы о черепахах, – он займет две лежащих на спине где-то в шоколадки» пустыне.» различные требования и реализации защитных систем в Интернете еще больше сбивают с толку простого пользователя и мешают ему запомнить информацию о себе. -

Takes You Straight to Where the Action Is
October, 2001 T65 Takesyoustraightto where the action is T65 White Paper, October 2001 &RQWHQWV Purpose of this document ........................................................................................... 3 Product overview .................................................................................................................. 4 Key functions and features ......................................................................................... 4 Functions and features for productivity ...................................................................... 5 Extras for fun ............................................................................................................. 6 Messaging ............................................................................................................................. 7 EMS – Enhanced text messaging ................................................................................ 7 Mobile chat ................................................................................................................ 7 E-mail ....................................................................................................................... 7 Synchronize calendar and phone book .................................................................................... 8 SyncML, an open standard ......................................................................................... 8 Local Synchronization ............................................................................................. -
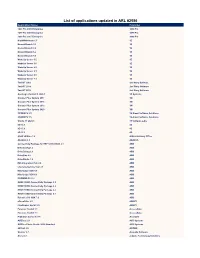
List of Applications Updated in ARL #2586
List of applications updated in ARL #2586 Application Name Publisher 1099 Pro 2005 Enterprise 1099 Pro 1099 Pro 2006 Enterprise 1099 Pro 1099 Pro 2007 Enterprise 1099 Pro NightWatchman 6.5 1E Nomad Branch 5.2 1E Nomad Branch 6.0 1E Nomad Branch 6.2 1E Nomad Branch 6.3 1E WakeUp Server 5.5 1E WakeUp Server 5.6 1E WakeUp Server 6.0 1E WakeUp Server 6.1 1E WakeUp Server 6.5 1E WakeUp Server 7.1 1E TaxACT 2002 2nd Story Software TaxACT 2014 2nd Story Software TaxACT 2018 2nd Story Software Geomagic Control X 2020.1 3D Systems Grouper Plus System 2017 3M Grouper Plus System 2018 3M Grouper Plus System 2019 3M Grouper Plus System 2020 3M CODESYS 2.3 3S-Smart Software Solutions CODESYS 3.5 3S-Smart Software Solutions Studio 3T 2020.9 3T Software Labs 4D 15.1 4D 4D 15.3 4D 4D 16.3 4D ASAP Utilities 7.8 A Must in Every Office AbaStart 2.5 ABACUS Connectivity Package for REF 541/543/545 2.1 ABB DriveConfig 1.2 ABB DriveDebug 2.9 ABB DriveSize 4.9 ABB DriveStudio 1.5 ABB IMS Integration Hub 2.8 ABB Lifecycle Service Tool 2.1 ABB MineScape SDK 5.1 ABB MineScape SDK 6.1 ABB PROMOD IV 11.2 ABB REM615 IED Connectivity Package 2.1 ABB REM615 IED Connectivity Package 2.2 ABB REU615 IED Connectivity Package 2.2 ABB REU615 IED Connectivity Package 5.1 ABB Robotics PC SDK 7.0 ABB eFormFiller 2.5 ABBYY FineReader Sprint 5.0 ABBYY Forensic Toolkit 7.1 AccessData Forensic Toolkit 7.1 AccessData PrizmDoc Server 13.14 AccuSoft ACDSee 2.0 ACD Systems ACDSee Photo Studio 2019 Standard ACD Systems dBTrait 5.5 ACOEM Soulver 2.7 Acqualia Software Arena 4.1 acQuire -

Mobile Phone R520 White Paper
EN/LZT 108 4308 R1A Mobile Phone R520 White Paper Ericsson is the leading provider in the new telecoms world, with communications solutions that com- bine telecom and datacom technologies with freedom of mobility for the user. With more than 100,000 employees in 140 countries, Ericsson simpliÞes communications for its customers - network operators, service providers, enterprises and consumers - the world over. First edition (September 2000) Publication number: EN/LZT 108 4308 R1A This document is published by Ericsson Mobile Communications AB, without any warranty. Improvements and changes to this text necessitated by typographical errors, inaccuracies of current information or improvements to programs and/or equipment, may be made by Ericsson Mobile Communications AB at any time and without notice. Such changes will, however, be incorporated into new editions of this document. Any hard copies of this documents are to be regarded as temporary reference copies only. All rights reserved. © Ericsson Mobile Communications AB, 2000 Contents PREFACE . 5 Purpose Of This Document . .5 PRODUCT DESCRIPTION . 6 R520 Always Online With The Mobile Internet . .6 Functions And Features For Productivity . .7 Technical Specifications For The Phone . .8 BLUETOOTHTM WIRELESS TECHNOLOGY . 9 Using Bluetooth Wireless Technology In The R520 . .10 Technical Specifications For Bluetooth Wireless Technology 10 SYNCHRONIZE CALENDAR AND PHONE BOOK 12 Synchronize With Local Calendar And Phone Book . .12 Synchronize Over Wide Area Network And Internet . .13 Hierarchical Phone Book With Contacts . .13 Synchronization Software And The R520 . .13 WAP SERVICES . 16 Using WAP In The R520 . .16 Technical Specifications Of The WAP Browser . .17 Bearer Type Characteristics . .19 Gateway Characteristics .