Introduction to Unix
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Administering Unidata on UNIX Platforms
C:\Program Files\Adobe\FrameMaker8\UniData 7.2\7.2rebranded\ADMINUNIX\ADMINUNIXTITLE.fm March 5, 2010 1:34 pm Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta UniData Administering UniData on UNIX Platforms UDT-720-ADMU-1 C:\Program Files\Adobe\FrameMaker8\UniData 7.2\7.2rebranded\ADMINUNIX\ADMINUNIXTITLE.fm March 5, 2010 1:34 pm Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Notices Edition Publication date: July, 2008 Book number: UDT-720-ADMU-1 Product version: UniData 7.2 Copyright © Rocket Software, Inc. 1988-2010. All Rights Reserved. Trademarks The following trademarks appear in this publication: Trademark Trademark Owner Rocket Software™ Rocket Software, Inc. Dynamic Connect® Rocket Software, Inc. RedBack® Rocket Software, Inc. SystemBuilder™ Rocket Software, Inc. UniData® Rocket Software, Inc. UniVerse™ Rocket Software, Inc. U2™ Rocket Software, Inc. U2.NET™ Rocket Software, Inc. U2 Web Development Environment™ Rocket Software, Inc. wIntegrate® Rocket Software, Inc. Microsoft® .NET Microsoft Corporation Microsoft® Office Excel®, Outlook®, Word Microsoft Corporation Windows® Microsoft Corporation Windows® 7 Microsoft Corporation Windows Vista® Microsoft Corporation Java™ and all Java-based trademarks and logos Sun Microsystems, Inc. UNIX® X/Open Company Limited ii SB/XA Getting Started The above trademarks are property of the specified companies in the United States, other countries, or both. All other products or services mentioned in this document may be covered by the trademarks, service marks, or product names as designated by the companies who own or market them. License agreement This software and the associated documentation are proprietary and confidential to Rocket Software, Inc., are furnished under license, and may be used and copied only in accordance with the terms of such license and with the inclusion of the copyright notice. -
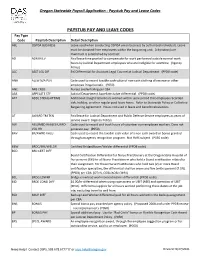
Oregon Statewide Payroll Application ‐ Paystub Pay and Leave Codes
Oregon Statewide Payroll Application ‐ Paystub Pay and Leave Codes PAYSTUB PAY AND LEAVE CODES Pay Type Code Paystub Description Detail Description ABL OSPOA BUSINESS Leave used when conducting OSPOA union business by authorized individuals. Leave must be donated from employees within the bargaining unit. A donation/use maximum is established by contract. AD ADMIN LV Paid leave time granted to compensate for work performed outside normal work hours by Judicial Department employees who are ineligible for overtime. (Agency Policy) ALC ASST LGL DIF 5% Differential for Assistant Legal Counsel at Judicial Department. (PPDB code) ANA ALLW N/A PLN Code used to record taxable cash value of non-cash clothing allowance or other employee fringe benefit. (P050) ANC NRS CRED Nurses credentialing per CBA ASA APPELATE STF Judicial Department Appellate Judge differential. (PPDB code) AST ADDL STRAIGHTTIME Additional straight time hours worked within same period that employee recorded sick, holiday, or other regular paid leave hours. Refer to Statewide Policy or Collective Bargaining Agreement. Hours not used in leave and benefit calculations. AT AWARD TM TKN Paid leave for Judicial Department and Public Defense Service employees as years of service award. (Agency Policy) AW ASSUMED WAGES-UNPD Code used to record and track hours of volunteer non-employee workers. Does not VOL HR generate pay. (P050) BAV BP/AWRD VALU Code used to record the taxable cash value of a non-cash award or bonus granted through an agency recognition program. Not PERS subject. (P050 code) BBW BRDG/BM/WELDR Certified Bridge/Boom/Welder differential (PPDB code) BCD BRD CERT DIFF Board Certification Differential for Nurse Practitioners at the Oregon State Hospital of five percent (5%) for all Nurse Practitioners who hold a Board certification related to their assignment. -

Small Group Instructional Diagnosis: Final Report
DOCUMENT RESUME JC 820 333 , ED 217 954 AUTHOR Clark, D. Joseph; Redmond, Mark V. TITLE Small Group Instructional Diagnosis: Final Report. INSTITUTION Washington Univ., Seattle. Dept. of Biology c Education. ., 'SPONS AGENCY Fund for the Improwsent of Postsecondary Education . (ED), Washington, D.C. , PUB DATE [82] NOTE 21p.; Appendices mentioned in the report are not _ included. EDRS PRICE , 401/PC01 Plus Postage. DESCRIPTORS *Course Evaluation; *Evaluation Methods; *Instructional Improvement; Postsecondary Education; *Student Evaluation of Teacher Performance;- tudent , Reaction; *Teacher Attitudes; Teacher Workshop IDENTIFIERS *Small group Instructional Diagnosis, ABSTRACT- A procedure for student evaluation andfeedback on faculty instruction was developed at the University of Washington. The system involved the use of,faculty members as facilitatorsin ,conducting Small Group Instructional Diagnosis (SGID) to generate student feedback to instructors about- the courses' strengths, areas needing improvement, and suggestions for bringing about these improvements. The SGID.procedure involves a number of steps:contact between the facilitator and instructor; classroomintervention to ascertain student opinions; a feedback session between facilitator and instructor; instructor. review of the SGID with the class;and ,a follow-up session between the facilitator and instructor.Following the development of the SGID process, handouts andvideotapes were produced to explain the procedure and the SGID technique was demonstrated in over 130 classes -

User Manual for Ox: an Attribute-Grammar Compiling System Based on Yacc, Lex, and C Kurt M
Computer Science Technical Reports Computer Science 12-1992 User Manual for Ox: An Attribute-Grammar Compiling System based on Yacc, Lex, and C Kurt M. Bischoff Iowa State University Follow this and additional works at: http://lib.dr.iastate.edu/cs_techreports Part of the Programming Languages and Compilers Commons Recommended Citation Bischoff, Kurt M., "User Manual for Ox: An Attribute-Grammar Compiling System based on Yacc, Lex, and C" (1992). Computer Science Technical Reports. 21. http://lib.dr.iastate.edu/cs_techreports/21 This Article is brought to you for free and open access by the Computer Science at Iowa State University Digital Repository. It has been accepted for inclusion in Computer Science Technical Reports by an authorized administrator of Iowa State University Digital Repository. For more information, please contact [email protected]. User Manual for Ox: An Attribute-Grammar Compiling System based on Yacc, Lex, and C Abstract Ox generalizes the function of Yacc in the way that attribute grammars generalize context-free grammars. Ordinary Yacc and Lex specifications may be augmented with definitions of synthesized and inherited attributes written in C syntax. From these specifications, Ox generates a program that builds and decorates attributed parse trees. Ox accepts a most general class of attribute grammars. The user may specify postdecoration traversals for easy ordering of side effects such as code generation. Ox handles the tedious and error-prone details of writing code for parse-tree management, so its use eases problems of security and maintainability associated with that aspect of translator development. The translators generated by Ox use internal memory management that is often much faster than the common technique of calling malloc once for each parse-tree node. -

Lecture 17 the Shell and Shell Scripting Simple Shell Scripts
Lecture 17 The Shell and Shell Scripting In this lecture • The UNIX shell • Simple Shell Scripts • Shell variables • File System commands, IO commands, IO redirection • Command Line Arguments • Evaluating Expr in Shell • Predicates, operators for testing strings, ints and files • If-then-else in Shell • The for, while and do loop in Shell • Writing Shell scripts • Exercises In this course, we need to be familiar with the "UNIX shell". We use it, whether bash, csh, tcsh, zsh, or other variants, to start and stop processes, control the terminal, and to otherwise interact with the system. Many of you have heard of, or made use of "shell scripting", that is the process of providing instructions to shell in a simple, interpreted programming language . To see what shell we are working on, first SSH into unix.andrew.cmu.edu and type echo $SHELL ---- to see the working shell in SSH We will be writing our shell scripts for this particular shell (csh). The shell scripting language does not fit the classic definition of a useful language. It does not have many of the features such as portability, facilities for resource intensive tasks such as recursion or hashing or sorting. It does not have data structures like arrays and hash tables. It does not have facilities for direct access to hardware or good security features. But in many other ways the language of the shell is very powerful -- it has functions, conditionals, loops. It does not support strong data typing -- it is completely untyped (everything is a string). But, the real power of shell program doesn't come from the language itself, but from the diverse library that it can call upon -- any program. -

Lecture 1 Introduction to Unix and C
Lecture 1 Introduction to Unix and C In this lecture • Operating System • Unix system shell • Why learn C • Program Development Process • Compilation, Linking and Preprocessing • ANSI-C • The C compiler – gcc • Jobs and Processes • Killing a Process • Moving from Java to C • Additional Readings • Exercises Operating System Each machine needs an Operating System (OS). An operating system is a software program that manages coordination between application programs and underlying hardware. OS manages devices such as printers, disks, monitors and manage multiple tasks such as processes. UNIX is an operating system. The following figure demonstrates the high level view of the layers of a computer system. It demonstrates that the end users interface with the computer at the application level, while programmers deal with utilities and operating system level. On the other hand, an OS designed must understand how to interface with the underlying hardware architecture. Copyright @ 2009 Ananda Gunawardena End user Programmer Application programs OS Designer Utilities Operating System Computer Hardware Unix is an operating system developed by AT&T in the late 60’s. BSD (Berkeley Unix) and Linux, are unix-like operating systems that are widely used in servers and many other platforms such as portable devices. Linux, an open source version of Unix-like operating system was first developed by Linus Torvalds . Linux has become a popular operating system used by many devices. Many volunteer developers have contributed to the development of many linux based resources. Linux is free, open source, and have very low hardware requirements. This makes linux a popular operating system for devices with limited hardware capabilities as well as running low cost personal computers. -

User's Manual
USER’S MANUAL USER’S > UniQTM UniQTM User’s Manual Ed.: 821003146 rev.H © 2016 Datalogic S.p.A. and its Group companies • All rights reserved. • Protected to the fullest extent under U.S. and international laws. • Copying or altering of this document is prohibited without express written consent from Datalogic S.p.A. • Datalogic and the Datalogic logo are registered trademarks of Datalogic S.p.A. in many countries, including the U.S. and the E.U. All other brand and product names mentioned herein are for identification purposes only and may be trademarks or registered trademarks of their respective owners. Datalogic shall not be liable for technical or editorial errors or omissions contained herein, nor for incidental or consequential damages resulting from the use of this material. Printed in Donnas (AO), Italy. ii SYMBOLS Symbols used in this manual along with their meaning are shown below. Symbols and signs are repeated within the chapters and/or sections and have the following meaning: Generic Warning: This symbol indicates the need to read the manual carefully or the necessity of an important maneuver or maintenance operation. Electricity Warning: This symbol indicates dangerous voltage associated with the laser product, or powerful enough to constitute an electrical risk. This symbol may also appear on the marking system at the risk area. Laser Warning: This symbol indicates the danger of exposure to visible or invisible laser radiation. This symbol may also appear on the marking system at the risk area. Fire Warning: This symbol indicates the danger of a fire when processing flammable materials. -

Introduction to Unix Shell (Part I)
Introduction to Unix shell (part I) Evgeny Stambulchik Faculty of Physics, Weizmann Institute of Science, Rehovot 7610001, Israel Joint ICTP-IAEA School on Atomic Processes in Plasmas February 27 – March 3, 2017 Trieste, Italy Contrary to popular belief, Unix is user friendly. It just happens to be very selective about who it decides to make friends with. Unknown Initially used at Bell Labs, but soon licensed to academy (notably, U. of California, Berkeley) and commercial vendors (IBM, Sun, etc). There are two major products that came out of Berkeley: LSD and Unix. We don’t believe this to be a coincidence. Jeremy S. Anderson, Unix systems administrator Historical overview (kind of) Unix is a family of multiuser, multitasking operating systems stemming from the original Unix developed in the 1970’s at Bell Labs by Ken Thompson, Dennis Ritchie1, and others. Some consider Unix to be the second most important invention to come out of AT&T Bell Labs after the transistor. Dennis Ritchie 1Also famous for creating the C programming language. Historical overview (kind of) Unix is a family of multiuser, multitasking operating systems stemming from the original Unix developed in the 1970’s at Bell Labs by Ken Thompson, Dennis Ritchie1, and others. Some consider Unix to be the second most important invention to come out of AT&T Bell Labs after the transistor. Dennis Ritchie Initially used at Bell Labs, but soon licensed to academy (notably, U. of California, Berkeley) and commercial vendors (IBM, Sun, etc). There are two major products that came out of Berkeley: LSD and Unix. -

CS 388 – UNIX Systems Programming Syllabus
CS 388 – UNIX Systems Programming Syllabus Instructor: Dr. Jack Tan Office: Phillips 135 Office Hours: click here Email: [email protected] Tel: 836-2408 Course Description: In-depth coverage of the UNIX command shell, file manipulation, process control, file system utilities, mail, pipes and filters, I/O redirection, process management, UNIX editors, scripting language, and shell scripting. Credits: 3 Prerequisites: CS 245 Courses that require this course as a prerequisite: none. Learning Resources: • Your UNIX: The Ultimate Guide, Sumitabha Das, McGraw-Hill, 2012. • Learning Perl: Making Things Easy and Hard Things Possible, Randall Schwartz, O’Reilly, 2016. • SED and AWK Pocket Reference, Arnold Robbins, O’Reilly, 2000. • Classic Shell Scripting: Hidden Commands that Unlock the Power of Unix, Arnold Robbins, 2017. Evaluation Midterm & Final: 20% Lab Assignments: 80% Course Outline Topic Number of weeks • UNIX commands and Utilities 2 • File and directory operations 1 • vi/vim editor 1 • UNIX file system 1 • UNIX Shell & shell scripting 2 • Process control 1 • grep, sed, and awk 2 • Regular expressions 1 • Perl programming 2 • System administration utilities 1 Course Outcomes: • Describe and apply the basic set of commands and utilities in Linux/UNIX systems. • Describe and process command-line arguments. • Apply important Linux/UNIX library functions and system calls. • Describe the inner workings of UNIX-like operating systems. • Design software for Linux/UNIX systems. • Use Perl and sed/awk/grep scripts to design programs for users. • Design conditional statements to control the execution of shell scripts. • Write shell scripts to perform repetitive tasks using while and for loops. • Design and implement shell functions. -

Unix Programmer's Manual
There is no warranty of merchantability nor any warranty of fitness for a particu!ar purpose nor any other warranty, either expressed or imp!ied, a’s to the accuracy of the enclosed m~=:crials or a~ Io ~helr ,~.ui~::~::.j!it’/ for ~ny p~rficu~ar pur~.~o~e. ~".-~--, ....-.re: " n~ I T~ ~hone Laaorator es 8ssumg$ no rO, p::::nS,-,,.:~:y ~or their use by the recipient. Furln=,, [: ’ La:::.c:,:e?o:,os ~:’urnes no ob~ja~tjon ~o furnish 6ny a~o,~,,..n~e at ~ny k:nd v,,hetsoever, or to furnish any additional jnformstjcn or documenta’tjon. UNIX PROGRAMMER’S MANUAL F~ifth ~ K. Thompson D. M. Ritchie June, 1974 Copyright:.©d972, 1973, 1974 Bell Telephone:Laboratories, Incorporated Copyright © 1972, 1973, 1974 Bell Telephone Laboratories, Incorporated This manual was set by a Graphic Systems photo- typesetter driven by the troff formatting program operating under the UNIX system. The text of the manual was prepared using the ed text editor. PREFACE to the Fifth Edition . The number of UNIX installations is now above 50, and many more are expected. None of these has exactly the same complement of hardware or software. Therefore, at any particular installa- tion, it is quite possible that this manual will give inappropriate information. The authors are grateful to L. L. Cherry, L. A. Dimino, R. C. Haight, S. C. Johnson, B. W. Ker- nighan, M. E. Lesk, and E. N. Pinson for their contributions to the system software, and to L. E. McMahon for software and for his contributions to this manual. -

UNIQUE E FLEXICR RETE XP P Polyme Er Modifie Ed Morta R
UNIQUE FLEXICRETE® XPP Polymer Modified Mortar Safety Data Sheet (Complies with OHSA 29 CFR 1910.1200) SECTION 1 ‐ PRODUCT IDENTIFICATION UNIQUE Paving Materials Corp. Information Telephone 3993 East 93rd Street Number Cleveland, Ohio 44105 ‐ USA (216) 341‐7711 www.uniquepavingmaterials.com Emergency Telephone Number (800) 424‐9300 Revision: April 3, 2015 UNIQUE Product Name Product # FLEXICRETE XP Polymer Modified Mortar N/A Product Use: Cementitious Mortar Section 2 – HAZARD IDENTIFICATION Physical Hazards Not Classified Health Hazards Skin corrosion / irritation Category 2 Serious Eye Damage Category 1 Carcinogenicity Category 1A Specific Target Organ Toxicity after Single Exposure Category 3 Specific Target Organ Toxicity after Repeated Exposure Category 1 OSHA defined hazards Not Classified Signal Word (GHS‐US): DANGER Hazard statement ‐ Causes skin irritation. Causes serious eye damage. May cause cancer. May cause respiratory irritation. May cause damage to organs (Lungs) through prolonged or repeated exposure. Form 205.136 (12-2015) 1 Page 3993 E. 93rd Street ι Cleveland, OH 44105 ι Phone 800.441.4880 ι Fax 216.341.8514 ι UniquePavingMaterials.com UNIQUE FLEXICRETE® XPP Polymer Modified Mortar Safety Data Sheet (Complies with OHSA 29 CFR 1910.1200) Precautionary statement Prevention ‐ Obtain special instructions before use. Do not handle until all safety precautions have been read and understood. Do not breathe dust. Wash thoroughly after handling. Use in a well‐ventilated area. Wear protective gloves/protective clothing/eye protection/face protection. Response ‐ If exposed or concerned: Get medical advice/attention. If in eyes: Rinse cautiously with water for several minutes. Remove contact lenses, if present and easy to do. Continue rinsing. -

Tour of the Terminal: Using Unix Or Mac OS X Command-Line
Tour of the Terminal: Using Unix or Mac OS X Command-Line hostabc.princeton.edu% date Mon May 5 09:30:00 EDT 2014 hostabc.princeton.edu% who | wc –l 12 hostabc.princeton.edu% Dawn Koffman Office of Population Research Princeton University May 2014 Tour of the Terminal: Using Unix or Mac OS X Command Line • Introduction • Files • Directories • Commands • Shell Programs • Stream Editor: sed 2 Introduction • Operating Systems • Command-Line Interface • Shell • Unix Philosophy • Command Execution Cycle • Command History 3 Command-Line Interface user operating system computer (human ) (software) (hardware) command- programs kernel line (text (manages interface editors, computing compilers, resources: commands - memory for working - hard-drive cpu with file - time) memory system, point-and- hard-drive many other click (gui) utilites) interface 4 Comparison command-line interface point-and-click interface - may have steeper learning curve, - may be more intuitive, BUT provides constructs that can BUT can also be much more make many tasks very easy human-manual-labor intensive - scales up very well when - often does not scale up well when have lots of: have lots of: data data programs programs tasks to accomplish tasks to accomplish 5 Shell Command-line interface provided by Unix and Mac OS X is called a shell a shell: - prompts user for commands - interprets user commands - passes them onto the rest of the operating system which is hidden from the user How do you access a shell ? - if you have an account on a machine running Unix or Linux , just log in. A default shell will be running. - if you are using a Mac, run the Terminal app.