Increasing Dependency on Uncaptured GDP in Global ICT Firms
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
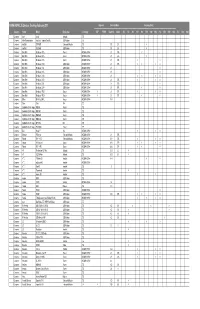
18 January 2011 HSPA+ and LTE Device Tracker (2).Xlsx
GSMA HSPA/LTE Devices Tracking February 2011 Approval Data rate (Mb/s) Frequency (MHz) Category Vendor Model Device type Technology GCF PTCRB Downlink Uplink 450 700 800 850 900 1700 1800 1900 2100 2300 2500 2600 2700 3300 3800 Consumer Acer Iconia Netbook LTE Consumer Altair Semiconductor FourGee™ ExpressCard UE USB Modem LTE Consumer AnyData DTP960S Embedded Module LTE 50 25 x Consumer AnyData ADU960S USB Modem LTE 50 25 x Consumer BandRich BandLuxe R300 Router WCDMA HSPA+ 21 5.76 xx Consumer BandRich BandLuxe R305 Router WCDMA HSPA+ 21 5.76 x Consumer BandRich BandLuxe R306 Router WCDMA HSPA+ 21 5.76 xx Consumer BandRich BandLuxe C320 USB Modem WCDMA HSPA+ 21 5.76 xx xx Consumer BandRich BandLuxe C321 USB Modem WCDMA HSPA+ 21 x Consumer BandRich BandLuxe C325 USB Modem WCDMA HSPA+ 21 x Consumer BandRich BandLuxe C326 USB Modem WCDMA HSPA+ 21 xx xx Consumer BandRich BandLuxe C330 USB Modem WCDMA HSPA+ 21 5.76 xxx Consumer BandRich BandLuxe C331 USB Modem WCDMA HSPA+ 21 5.76 x Consumer BandRich BandLuxe C339 USB Modem WCDMA HSPA+ 21 5.76 xx Consumer BandRich BandLuxe PR30 Router WCDMA HSPA+ x 21 5.76 xxx Consumer BandRich BandLuxe PR39 Router WCDMA HSPA+ x 21 5.76 xx Consumer Billion BiPAC 6200NXL Router WCDMA HSPA+ 14.4 Consumer Cisco Cius N/A LTE Consumer CradlePoint Technology MBR90 Router LTE Consumer CradlePoint Technology MBR900 Router LTE Consumer CradlePoint Technology MBR1000 Router LTE Consumer CradlePoint Technology MBR1200 Router LTE Consumer CradlePoint Technology NFS750L N/A LTE Consumer CradlePoint Technology PCS1400L Router -

Form 20-F for the Fiscal Year Ended March 31, 2017
UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 Form 20-F ‘ REGISTRATION STATEMENT PURSUANT TO SECTION 12(b) OR 12(g) OF THE SECURITIES EXCHANGE ACT OF 1934 or Í ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the fiscal year ended March 31, 2017 or ‘ TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the transition period from/to or ‘ SHELL COMPANY REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 Date of event requiring this shell company report: Commission file number 1-6439 Sony Kabushiki Kaisha (Exact Name of Registrant as specified in its charter) SONY CORPORATION (Translation of Registrant’s name into English) Japan (Jurisdiction of incorporation or organization) 7-1, KONAN 1-CHOME, MINATO-KU, TOKYO 108-0075 JAPAN (Address of principal executive offices) J. Justin Hill, Senior Vice President, Investor Relations Sony Corporation of America 25 Madison Avenue, 26th Floor New York, NY 10010-8601 Telephone: 212-833-6722 E-mail: [email protected] (Name, Telephone, E-mail and Address of Company Contact Person) Securities registered or to be registered pursuant to Section 12(b) of the Act: Title of Each Class Name of Each Exchange on Which Registered American Depositary Shares* New York Stock Exchange Common Stock** New York Stock Exchange * American Depositary Shares evidenced by American Depositary Receipts. Each American Depositary Share represents one share of Common Stock. ** No par value per share. Not for trading, but only in connection with the listing of American Depositary Shares pursuant to the requirements of the New York Stock Exchange. -

The Apple Ecosystem
APPENDIX A The Apple Ecosystem There are a lot of applications used to manage Apple devices in one way or another. Additionally, here’s a list of tools, sorted alphabetically per category in order to remain vendor agnostic. Antivirus Solutions for scanning Macs for viruses and other malware. • AVG: Basic antivirus and spyware detection and remediation. • Avast: Centralized antivirus with a cloud console for tracking incidents and device status. • Avira: Antivirus and a browser extension. Avira Connect allows you to view device status online. • BitDefender: Antivirus and malware managed from a central console. • CarbonBlack: Antivirus and Application Control. • Cylance: Ransomware, advanced threats, fileless malware, and malicious documents in addition to standard antivirus. • Kaspersky: Antivirus with a centralized cloud dashboard to track device status. © Charles Edge and Rich Trouton 2020 707 C. Edge and R. Trouton, Apple Device Management, https://doi.org/10.1007/978-1-4842-5388-5 APPENDIX A THe AppLe ECOSYSteM • Malware Bytes: Antivirus and malware managed from a central console. • McAfee Endpoint Security: Antivirus and advanced threat management with a centralized server to track devices. • Sophos: Antivirus and malware managed from a central console. • Symantec Mobile Device Management: Antivirus and malware managed from a central console. • Trend Micro Endpoint Security: Application whitelisting, antivirus, and ransomware protection in a centralized console. • Wandera: Malicious hot-spot monitoring, jailbreak detection, web gateway for mobile threat detection that integrates with common MDM solutions. Automation Tools Scripty tools used to automate management on the Mac • AutoCasperNBI: Automates the creation of NetBoot Images (read: NBI’s) for use with Casper Imaging. • AutoDMG: Takes a macOS installer (10.10 or newer) and builds a system image suitable for deployment with Imagr, DeployStudio, LANrev, Jamf Pro, and other asr or Apple Systems Restore-based imaging tools. -

Evaluation of LTE-M Towards 5G Iot Requirements
White Paper Evaluation of LTE-M towards 5G IoT requirements Contributing and Supporting Companies: V1.0 December 2017 Evaluation of LTE-M towards 5G IoT requirements for Category-M1 Devices White Paper Executive Summary LTE-M, a machine-focused variant of the 3GPP LTE standard, is designed to meet the high-coverage, low-cost, and low- power consumption requirements of the Internet of Things (IoT). In January 2017, a group of more than a dozen industry players evaluated LTE-M’s coverage performance, and published a white paper which concludes that LTE-M supports the very deep coverage required for IoT applications [1]. This follow-up paper takes the next step to evaluate the message latency, battery life, and capacity performance for LTE-M category-M1 devices. More specifically, this paper evaluates LTE-M performance against the initial Cellular IoT (CIoT) requirements in 3GPP TR 45.820 [2], but – perhaps more importantly – also compares LTE-M performance to the more recently published 3GPP 5G IoT or massive Machine-Type Communications (mMTC) requirements. The 5G IoT requirements for coverage, message latency, and battery life are specified in 3GPP TR 38.913 [3] and the capacity requirements are defined by the two ITU reports IMT-2020 evaluation guidelines [4] and IMT-2020 requirements [6]. Starting with the CIoT requirements, the message latency for LTE-M in extremely deep coverage conditions was found to be 6.2 seconds, which is well under the stated goal of 10 seconds. Battery life in extremely deep coverage conditions was determined to be 10.4 years, which is over the 10-year requirement assuming one 200 byte uplink message per day. -

MTC 008 V1.1.1 (2010-05) Group Specification
ETSI GS MTC 008 V1.1.1 (2010-05) Group Specification Mobile Thin Client (MTC); Use Cases and Requirements 2 ETSI GS MTC 008 V1.1.1 (2010-05) Reference DGS/MTC-0001 Rqmts Keywords ETSI 650 Route des Lucioles F-06921 Sophia Antipolis Cedex - FRANCE Tel.: +33 4 92 94 42 00 Fax: +33 4 93 65 47 16 Siret N° 348 623 562 00017 - NAF 742 C Association à but non lucratif enregistrée à la Sous-Préfecture de Grasse (06) N° 7803/88 Important notice Individual copies of the present document can be downloaded from: http://www.etsi.org The present document may be made available in more than one electronic version or in print. In any case of existing or perceived difference in contents between such versions, the reference version is the Portable Document Format (PDF). In case of dispute, the reference shall be the printing on ETSI printers of the PDF version kept on a specific network drive within ETSI Secretariat. Users of the present document should be aware that the document may be subject to revision or change of status. Information on the current status of this and other ETSI documents is available at http://portal.etsi.org/tb/status/status.asp If you find errors in the present document, please send your comment to one of the following services: http://portal.etsi.org/chaircor/ETSI_support.asp Copyright Notification No part may be reproduced except as authorized by written permission. The copyright and the foregoing restriction extend to reproduction in all media. © European Telecommunications Standards Institute 2010. -

Transforming the Medical Imaging Workflow
Transforming the Medical Imaging Workflow: How Mac systems and open source software combine to make full-featured diagnostic imaging solutions affordable for today’s radiologist. By Roger Katen, M.D. San Francisco, CA White Paper 2 Transforming the Medical Imaging Workflow Contents Page 3 Executive Summary Page 5 The New Realities of Medical Imaging The Digital Data Explosion The Rise of Imaging Workstations A Cost Conundrum Page 8 A Compelling Alternative: The Mac and OsiriX Workstation OsiriX: Full-Featured, Open Source Mac OS X and Mac Systems A New Solution for a New Reality Page 10 Mac Systems and OsiriX in the Radiology Workflow Image Generation Equipment Picture Archiving and Communications Systems (PACS) Creating a PACS Archive with OsiriX Database Sharing and Autorouting Storage System Page 16 Building an Imaging Workstation Environment with OsiriX Working with Large Datasets Supporting Medical-Quality Displays Requirements for High-Performance Processors Accelerating Image Retrieval Page 19 Enabling the Imaging Workflow Options for Advanced Visualization Starting and Sending a New DICOM Series to PACS Emailing and Printing Images Integrating with Hospital and Radiology Information Systems Exploring Alternatives to Windows RIS Systems Page 24 Collaborating Beyond the Office with OsiriX Virtual Private Networks Remote Visualization via Apple Remote Desktop Citrix/Windows Terminal Services Teleradiology Collaboration iChat and iChat Theater Page 28 Conclusion White Paper 3 Transforming the Medical Imaging Workflow Executive Summary Today more than ever, the healthcare industry is reaping the benefits of advances in diagnostic medical imaging. Dramatic breakthroughs in higher-resolution CT, MRI, ultrasound, and interventional technologies have enabled healthcare providers to deliver more informed diagnoses, pursue more effective treatments, collaborate more easily with colleagues, and communicate more clearly with patients. -

Check Point Altair Semiconductor Solution Brief
Check Point and Altair Semiconductor | Solution Brief CHECK POINT + ALTAIR THREAT PREVENTION FOR MOBILE IOT DEVICES INSIGHTS Benefits Security is key for the safe and reliable operation of IoT (Internet of Things) connected devices. Security concerns cover personal privacy, financial transactions, the threat of Inspect all communications to and cyber theft, and safety. Network firewalls and protocols can manage the high-level from Altair LTE (Long-Term Evolution) chipsets on IoT devices traffic coursing through the Internet. IoT devices that usually have a very specific, with Check Point Capsule Cloud to defined mission with limited resources also have to be protected. prevent threats before they arrive into the device Applying common internet security practices in the IoT world requires substantial Offload security processing from IoT reengineering to address device constraints. Blacklisting, for example, requires too devices to Capsule Cloud much disk space to be practical for IoT applications. Embedded devices are designed Secure IoT devices with advanced for low power consumption, with a small silicon form factor, and often have limited threat prevention connectivity. They typically have only as much processing capacity and memory as Increase visibility of threats targeting needed for their tasks. IoT devices The endless variety of IoT applications poses an equally wide variety of security challenges. For example: tracking a device’s location, turning on the camera and microphone, and extracting application data information. A smart meter - one which is able to send energy usage data to the utility operator for dynamic billing or real-time power grid optimization - must be able to protect that information from unauthorized usage or disclosure. -

Smartphones 37 4.1 Customer Need: Mobility 37 4.2 Vendors 38 4.3 Operating System Duopoly 39 4.4 Hardware Specifications 40 Acronyms 46 Notes 47
Digital Services in the 21st Century IEEE Press 445 Hoes Lane Piscataway, NJ 08854 IEEE Press Editorial Board Tariq Samad, Editor in Chief Giancarlo Fortino Xiaoou Li Ray Perez Dmitry Goldgof Andreas Molisch Linda Shafer Don Heirman Saeid Nahavandi Mohammad Shahidehpour Ekram Hossain Jeffrey Nanzer Zidong Wang Digital Services in the 21st Century A Strategic and Business Perspective Antonio Sánchez Belén Carro Universidad de Valladolid, Spain Copyright 2017 by The Institute of Electrical and Electronics Engineers, Inc. All rights reserved. Published by John Wiley & Sons, Inc., Hoboken, New Jersey. Published simultaneously in Canada. No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning, or otherwise, except as permitted under Section 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, Inc., 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 750-4470, or on the web at www.copyright.com. Requests to the Publisher for permission should be addressed to the Permissions Department, John Wiley & Sons, Inc., 111 River Street, Hoboken, NJ 07030, (201) 748-6011, fax (201) 748-6008, or online at http://www.wiley.com/go/permission. Limit of Liability/Disclaimer of Warranty: While the publisher and author have used their best efforts in preparing this book, they make no representations or warranties with respect to the accuracy or completeness of the contents of this book and specifically disclaim any implied warranties of merchantability or fitness for a particular purpose. -
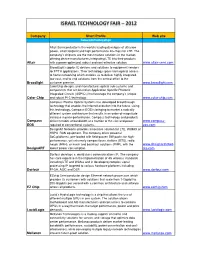
Technology Fair
Company Short Profile Web site Telecommunication Altair Semiconductor is the world's leading developer of ultra-low power, small footprint and high performance 4G chips for LTE. The company's chipsets are the most mature solutions in the market, offering device manufacturers integrating LTE into their products Altair with a power-optimized, robust and cost-effective solution. www.altair-semi.com BroadLight supplys IC devices and solutions to equipment vendors for FTTH applications. Thier technology spans from optical access to home networking which enables us to deliver highly integrated, low-cost, end-to-end solutions from the central office to the Broadlight customer premise. www.broadlight.com ColorChip designs and manufactures optical sub-systems and components that are based on Application Specific Photonic Integrated Circuits (ASPICs) that leverage the company’s unique Color Chip and robust PLC technology. www.color-chip.com Compass Electro-Optical Systems has developed breakthrough technology that enables the Internet evolution into the future. Using this technology, Compass-EOS is bringing to market a radically different system architecture that results in an order-of-magnitude increase in price-performance. Compass technology and products Compass deliver terabits of bandwidth at a fraction of the size and power www.compass- EOS required of conventional systems. eos.com DesignArt Networks provides innovative solution for LTE, WiMAX or HSPA RAN equipment. The company offers powerful SoC platforms, pre-loaded with field-proven SW packs for high- performance, yet extremely compact base stations (BTS), radio heads (RRH), or mesh and backhaul solutions (PMP), with the www.designartnetwo DesignART lowest power consumption rks.com Dorfour develops a world class communications IP. -

CEATEC JAPAN 2006 Exhibition Report
CONTENTS CEATEC JAPAN 2006 JAPAN CEATEC 1. SHOW INFORMATION 01 2. CHAIRMAN'S COMMENTS 02 3. OPENING EVENTS 03 4. EXHIBITION CONFIGURATION 04 5. EXHIBITION SITE 05 6. EXHIBITION TRENDS 06 7. SPONSORS PROJECTS AND SPECIAL EXHIBITS 13 8. CONFERENCE 15 9. EXHIBITORS 16 10. NUMBERS AND ANALYSIS OF VISITORS 19 11. ADVERTISING AND PUBLICITY 22 12. CEATEC JAPAN OFFICIAL WEB SITE 24 00 1. SHOW INFORMATION CEATEC JAPAN 2006 JAPAN CEATEC NAME CEATEC JAPAN 2006 (Combined Exhibition of Advanced TEChnologies-Providing Image, Information and Communications) OBJECTIVES 1.To allow visitors to experience the newest technologies, products, systems and software for the digital network age, and the convergence of communications, information and imaging technologies 2.To function as a highly specific exhibition capturing the interest and responding to the needs of users by presenting the industries' latest achievements and trends 3.As Asia's largest interactive exhibition of information on the communications, information and imaging fields, to present the achievements, trends and vitality of these industries to the world 4.To gather industry organizations to present clear social messages, thereby supporting industrial development and contributing to lifestyles, economies and society in the digital network age DURATION Tuesday, October 3-Saturday, October 7, 2006 (5 days), from 10:00 a.m.-5:00 p.m. Premiere Time: Tuesday, October 3, 10:00 a.m.-12:00 p.m. LOCATION Makuhari Messe 2-1 Nakase, Mihama-ku, Chiba, Japan ADMISSION Registration required Visitors Pre-registered on the Web: Free entry Visitors registering at the Gate: General: 1,000 (Students: 500) Note: Groups of 20 or more students and children under 12 years of age were admitted free of charge. -

How Current Apple 11-Serles Owners Can Step Ufj
How current Apple 11-serles owners can step UfJ oving up to the Iles is a But is it really a good buy? Will you board, and speaker cables from the logical next step for owners still be able to use all your old pe Ile motherboard Mof current Apple-II-series ripheral cards and software? Should • remove the base pan from the plas computers: You get a you keep your Ile and ignore the tic casing of the Ile and save the souped-up, Macintosh-like com Iles? Or is this the time to sell your speaker puter that still works with most of Ile, II Plus, or Ile system unit and • insert the Iles motherboard and your current software and peripher graduate to a genuine Iles? These the new base pan als. If you own an Apple Ile, it's pret are some of the questions I hope •reconnect the power supply, key ty obvious how you can upgrade to a you'll be able to answer after read board, and speaker cables. Iles-by purchasing an upgrade kit ing this article. The computer you end up with is from Apple that gives your old Ile Details of the Upgrade functionally no different from a real new innards. But that's only one ap The Iles upgrade kit consists of Iles-it just has a different keyboard proach to upgrading. Even if you three items: a Iles motherboard, a and a different case. Thus, you will have a Ile or a II Plus, there is still an metal base pan, and a manual that be able to take advantage of all the upgrade path for you. -

– and the March Towards MASSIVE IOT by James Blackman Editor, Enterprise Iot Insights FEATURE REPORT
DIGITAL INDUSTRY SOLUTIONS: ASSET TRACKING OCTOBER 2020 ASSET – and the march towards MASSIVE IOT by James Blackman Editor, Enterprise IoT Insights FEATURE REPORT 1 | What is asset tracking and what is it worth? (It’s a jungle – and it’s massive) Asset tracking is the oldest game in town, and remains the great engine of IoT; so why is it so hard to hit targets? hat is asset tracking, any- Who is right? Because no one communica- 50bn way? And what is it worth? tions’, and sets – IoT connections by Because tracking of machine agrees; which is the trouble five require- 2025; the sector has data, one way or another, is ments: battery been struggling to with crystal-gazing. Except live up to this famous Weasily conflated with the internet-of-things life of 10 years; there is consensus across forecast since (IoT) movement, at large. And we all know coverage pene- 2010 about the mad growth slated for gener- the stats and specs that it is tration of 164 dB; al-purpose IoT. Fifty billion connections, by going to be ‘massive’, and an throughput of 160 bits 2025? Gulp. argument to say it already is per second; capacity of million devices That single finger-in-the-air forecast, per square kilometre; round-trip latencies by Cisco and Ericsson, way back in 2010, so. A billion is a billion, after of 10 seconds; and, importantly, ultra-low has cast an impossible shadow over the all, and smartphone sales, by cost hardware. sector’s progress; the industry has been comparison, have stalled at These are the terms for cellular to serve trying to shake it ever since, even as it has massive-scale IoT.