Drivers and Kernel
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Glibc and System Calls Documentation Release 1.0
Glibc and System Calls Documentation Release 1.0 Rishi Agrawal <[email protected]> Dec 28, 2017 Contents 1 Introduction 1 1.1 Acknowledgements...........................................1 2 Basics of a Linux System 3 2.1 Introduction...............................................3 2.2 Programs and Compilation........................................3 2.3 Libraries.................................................7 2.4 System Calls...............................................7 2.5 Kernel.................................................. 10 2.6 Conclusion................................................ 10 2.7 References................................................ 11 3 Working with glibc 13 3.1 Introduction............................................... 13 3.2 Why this chapter............................................. 13 3.3 What is glibc .............................................. 13 3.4 Download and extract glibc ...................................... 14 3.5 Walkthrough glibc ........................................... 14 3.6 Reading some functions of glibc ................................... 17 3.7 Compiling and installing glibc .................................... 18 3.8 Using new glibc ............................................ 21 3.9 Conclusion................................................ 23 4 System Calls On x86_64 from User Space 25 4.1 Setting Up Arguements......................................... 25 4.2 Calling the System Call......................................... 27 4.3 Retrieving the Return Value...................................... -

Kernel Panic
Kernel Panic Connect, Inc. 1701 Quincy Avenue, Suites 5 & 6, Naperville, IL 60540 Ph: (630) 717-7200 Fax: (630) 717-7243 www.connectrf.com Table of Contents SCO Kernel Patches for Panics on Pentium Systems…………………………………..1 Kernel Panic Debug Methodologies..............................................................................3 SCO Kernel Patches for Panics on Pentium Systems SCO Kernel Patches for Panics on Pentium Systems Web Links http://www.sco.com/cgi-bin/ssl_reference?104530 http://www.sco.com/cgi-bin/ssl_reference?105532 Pentium System Panics with Trap Type 6; no dump is saved to /dev/swap. Keywords panic trap kernel invalid opcode pentium querytlb querytbl 386 mpx unix v4 dump swap double type6 no patch /etc/conf/pack.d/kernel/locore.o image locore Release SCO UNIX System V/386 Release 3.2 Operating System Version 4.0, 4.1 and 4.2 SCO Open Desktop Release 2.0 and 3.0 SCO Open Server System Release 2.0 and 3.0 Problem My system panics with a Trap Type 6, but no memory dump gets written. Cause There is a flaw in the kernel querytlb() routine that allows the Pentium to execute a 386-specific instruction which causes it to panic with an invalid opcode. querytlb() is only called when your system is panicking. The fault causes the system to double- panic and it thus fails to write a panic dump to disk. This means that the panic trap type 6 is concealing another type of panic which will show itself after the following patch has been applied. Solution You can apply the following patch, as root, to: /etc/conf/pack.d/kernel/locore.o Use the procedure that follows. -

The Linux Kernel Module Programming Guide
The Linux Kernel Module Programming Guide Peter Jay Salzman Michael Burian Ori Pomerantz Copyright © 2001 Peter Jay Salzman 2007−05−18 ver 2.6.4 The Linux Kernel Module Programming Guide is a free book; you may reproduce and/or modify it under the terms of the Open Software License, version 1.1. You can obtain a copy of this license at http://opensource.org/licenses/osl.php. This book is distributed in the hope it will be useful, but without any warranty, without even the implied warranty of merchantability or fitness for a particular purpose. The author encourages wide distribution of this book for personal or commercial use, provided the above copyright notice remains intact and the method adheres to the provisions of the Open Software License. In summary, you may copy and distribute this book free of charge or for a profit. No explicit permission is required from the author for reproduction of this book in any medium, physical or electronic. Derivative works and translations of this document must be placed under the Open Software License, and the original copyright notice must remain intact. If you have contributed new material to this book, you must make the material and source code available for your revisions. Please make revisions and updates available directly to the document maintainer, Peter Jay Salzman <[email protected]>. This will allow for the merging of updates and provide consistent revisions to the Linux community. If you publish or distribute this book commercially, donations, royalties, and/or printed copies are greatly appreciated by the author and the Linux Documentation Project (LDP). -

Procedures to Build Crypto Libraries in Minix
Created by Jinkai Gao (Syracuse University) Seed Document How to talk to inet server Note: this docment is fully tested only on Minix3.1.2a. In this document, we introduce a method to let user level program to talk to inet server. I. Problem with system call Recall the process of system call, refering to http://www.cis.syr.edu/~wedu/seed/Labs/Documentation/Minix3/System_call_sequence.pd f We can see the real system call happens in this function call: _syscall(FS, CHMOD, &m) This function executes ‘INT 80’ to trap into kernel. Look at the parameter it passs to kernel. ‘CHMOD’ is a macro which is merely the system call number. ‘FS’ is a macro which indicates the server which handles the chmod system call, in this case ‘FS’ is 1, which is the pid of file system server process. Now your might ask ‘why can we hard code the pid of the process? Won’t it change?’ Yes, normally the pid of process is unpredictable each time the system boots up. But for fs, pm, rs, init and other processes which is loaded from system image at the very beginning of booting time, it is not true. In minix, you can dump the content of system image by pressing ‘F3’, then dump the current running process table by pressing ‘F1’. What do you find? The first 12 entries in current process table is exactly the ones in system image with the same order. So the pids of these 12 processes will not change. Inet is different. It is not in the system image, so it is not loaded into memory in the very first time. -

UNIX Systems Programming II Systems Unixprogramming II Short Course Notes
Systems UNIXProgramming II Systems UNIXProgramming II Systems UNIXProgramming II UNIX Systems Programming II Systems UNIXProgramming II Short Course Notes Alan Dix © 1996 Systems Programming II http://www.hcibook.com/alan/ UNIX Systems Course UNIXProgramming II Outline Alan Dix http://www.hcibook.com/alan/ Session 1 files and devices inodes, stat, /dev files, ioctl, reading directories, file descriptor sharing and dup2, locking and network caching Session 2 process handling UNIX processes, fork, exec, process death: SIGCHLD and wait, kill and I/O issues for fork Session 3 inter-process pipes: at the shell , in C code and communication use with exec, pseudo-terminals, sockets and deadlock avoidance Session 4 non-blocking I/O and UNIX events: signals, times and select I/O; setting timers, polling, select, interaction with signals and an example Internet server Systems UNIXProgrammingII Short Course Notes Alan Dix © 1996 II/i Systems Reading UNIXProgramming II ¥ The Unix V Environment, Stephen R. Bourne, Wiley, 1987, ISBN 0 201 18484 2 The author of the Borne Shell! A 'classic' which deals with system calls, the shell and other aspects of UNIX. ¥ Unix For Programmers and Users, Graham Glass, Prentice-Hall, 1993, ISBN 0 13 061771 7 Slightly more recent book also covering shell and C programming. Ì BEWARE Ð UNIX systems differ in details, check on-line documentation ¥ UNIX manual pages: man creat etc. Most of the system calls and functions are in section 2 and 3 of the manual. The pages are useful once you get used to reading them! ¥ The include files themselves /usr/include/time.h etc. -

Toward MP-Safe Networking in Netbsd
Toward MP-safe Networking in NetBSD Ryota Ozaki <[email protected]> Kengo Nakahara <[email protected]> EuroBSDcon 2016 2016-09-25 Contents ● Background and goals ● Approach ● Current status ● MP-safe Layer 3 forwarding ● Performance evaluations ● Future work Background ● The Multi-core Era ● The network stack of NetBSD couldn’t utilize multi-cores ○ As of 2 years ago CPU 0 NIC A NIC B CPU 1 Our Background and Our Goals ● Internet Initiative Japan Inc. (IIJ) ○ Using NetBSD in our products since 1999 ○ Products: Internet access routers, etc. ● Our goal ○ Better performance of our products, especially Layer 2/3 forwarding, tunneling, IPsec VPN, etc. → MP-safe networking Our Targets ● Targets ○ 10+ cores systems ○ 1 Gbps Intel NICs and virtualized NICs ■ wm(4), vmx(4), vioif(4) ○ Layer 2 and 3 ■ IPv4/IPv6, bridge(4), gif(4), vlan(4), ipsec(4), pppoe(4), bpf(4) ● Out of targets ○ 100 cores systems and above ○ Layer 4 and above ■ and any other network components except for the above Approach ● MP-safe and then MP-scalable ● Architecture ○ Utilize hardware assists ○ Utilize lightweight synchronization mechanisms ● Development ○ Restructure the code first ○ Benchmark often Approach : Architecture ● Utilize hardware assists ○ Distribute packets to CPUs by hardware ■ NIC multi-queue and RSS ● Utilize software techniques ○ Lightweight synchronization mechanisms ■ Especially pserialize(9) and psref(9) ○ Existing facilities ■ Fast forwarding and ipflow Forwarding Utilizing Hardware Assists Least locks Rx H/W queues CPU 0 Tx H/W queues queue 0 queue 0 CPU 1 queue 1 queue 1 NIC A NIC B queue 2 queue 2 CPU 2 queue 3 queue 3 CPU 3 Packets are distributed Packets are processed by hardware based on on a received CPU to flow (5-tuples) the last Approach : Development ● Restructure the code first ○ Hard to simply apply locks to the existing code ■ E.g., hardware interrupt context for Layer 2, cloning/cloned routes, etc. -

Advancing Mac OS X Rootkit Detecron
Advancing Mac OS X Rootkit Detec4on Andrew Case (@attrc) Volatility Foundation Golden G. Richard III (@nolaforensix) University of New Orleans 2 hot research areas State of Affairs more established Live Forensics and Tradional Storage Memory Analysis Forensics Digital Forensics Reverse Engineering Incident Response Increasingly encompasses all the others Copyright 2015 by Andrew Case and Golden G. Richard III 3 Where’s the Evidence? Files and Filesystem Applica4on Windows Deleted Files metadata metadata registry Print spool Hibernaon Temp files Log files files files Browser Network Slack space Swap files caches traces RAM: OS and app data Volale Evidence structures Copyright 2015 by Andrew Case and Golden G. Richard III 4 Volale Evidence 1 011 01 1 0 1 111 0 11 0 1 0 1 0 10 0 1 0 1 1 1 0 0 1 0 1 1 0 0 1 Copyright 2015 by Andrew Case and Golden G. Richard III 5 Awesomeness Progression: File Carving Can carve Chaos: files, but More can't Faster Almost not very accurate Hurray! carve files well Tools Manual File type Fragmentaon, appear, MulDthreading, hex editor aware damned but have beer design stuff carving, et al spinning disks! issues Images: hLps://easiersaidblogdotcom.files.wordpress.com/2013/02/hot_dogger.jpg hLp://cdn.bigbangfish.com/555/Cow/Cow-6.jpg, hLp://f.tqn.com/y/bbq/1/W/U/i/Big_green_egg_large.jpg hLp://i5.walmarDmages.com/dfw/dce07b8c-bb22/k2-_95ea6c25-e9aa-418e-a3a2-8e48e62a9d2e.v1.jpg Copyright 2015 by Andrew Case and Golden G. Richard III 6 Awesomeness Progression: Memory Forensics Pioneering Chaos: More, efforts Beyond run more, show great Windows ?? strings? more promise pt_finder et al More aenDon Manual, Mac, … awesome but to malware, run strings, Linux, BSD liLle context limited filling in the gaps funcDonality Images: hLps://s-media-cache-ak0.pinimg.com/736x/75/5a/37/755a37727586c57a19d42caa650d242e.jpg,, hLp://img.photobucket.com/albums/v136/Hell2Pay77/SS-trucks.jpg hLp://skateandannoy.com/wp-content/uploads/2007/12/sportsbars.jpg, hLp://gainesvillescene.com/wp-content/uploads/2013/03/dog-longboard.jpg Copyright 2015 by Andrew Case and Golden G. -

Introduction to Linux Kernel Driver Programming
IntroductionIntroduction toto LinuxLinux kernelkernel driverdriver programmingprogramming Introduction to Linux kernel driver programming The Linux kernel device model Authors and license ● Authors – Michael Opdenacker ([email protected]) Founder of Bootlin, kernel and embedded Linux engineering company https://bootlin.com/company/staff/michael-opdenacker ● License – Creative Commons Attribution – Share Alike 4.0 https://creativecommons.org/licenses/by-sa/4.0/ – Document sources: https://github.com/e-ale/Slides Need for a device model ● For the same device, need to use the same device driver on multiple CPU architectures (x86, ARM…), even though the hardware controllers are different. ● Need for a single driver to support multiple devices of the same kind. ● This requires a clean organization of the code, with the device drivers separated from the controller drivers, the hardware description separated from the drivers themselves, etc. Driver: between bus infrastructure and framework In Linux, a driver is always interfacing with: ● a framework that allows the driver to expose the hardware features in a generic way. ● a bus infrastructure, part of the device model, to detect/communicate with the hardware. Let’s focus on the bus infrastructure for now Device model data structures The device model is organized around three main data structures: ● The struct bus_type structure, which represent one type of bus (USB, PCI, I2C, etc.) ● The struct device_driver structure, which represents one driver capable of handling certain devices on a certain bus. ● The struct device structure, which represents one device connected to a bus The kernel uses inheritance to create more specialized versions of struct device_driver and struct device for each bus subsystem. -

The Xen Port of Kexec / Kdump a Short Introduction and Status Report
The Xen Port of Kexec / Kdump A short introduction and status report Magnus Damm Simon Horman VA Linux Systems Japan K.K. www.valinux.co.jp/en/ Xen Summit, September 2006 Magnus Damm ([email protected]) Kexec / Kdump Xen Summit, September 2006 1 / 17 Outline Introduction to Kexec What is Kexec? Kexec Examples Kexec Overview Introduction to Kdump What is Kdump? Kdump Kernels The Crash Utility Xen Porting Effort Kexec under Xen Kdump under Xen The Dumpread Tool Partial Dumps Current Status Magnus Damm ([email protected]) Kexec / Kdump Xen Summit, September 2006 2 / 17 Introduction to Kexec Outline Introduction to Kexec What is Kexec? Kexec Examples Kexec Overview Introduction to Kdump What is Kdump? Kdump Kernels The Crash Utility Xen Porting Effort Kexec under Xen Kdump under Xen The Dumpread Tool Partial Dumps Current Status Magnus Damm ([email protected]) Kexec / Kdump Xen Summit, September 2006 3 / 17 Kexec allows you to reboot from Linux into any kernel. as long as the new kernel doesn’t depend on the BIOS for setup. Introduction to Kexec What is Kexec? What is Kexec? “kexec is a system call that implements the ability to shutdown your current kernel, and to start another kernel. It is like a reboot but it is indepedent of the system firmware...” Configuration help text in Linux-2.6.17 Magnus Damm ([email protected]) Kexec / Kdump Xen Summit, September 2006 4 / 17 . as long as the new kernel doesn’t depend on the BIOS for setup. Introduction to Kexec What is Kexec? What is Kexec? “kexec is a system call that implements the ability to shutdown your current kernel, and to start another kernel. -

System Calls
System Calls What are they? ● Standard interface to allow the kernel to safely handle user requests – Read from hardware – Spawn a new process – Get current time – Create shared memory ● Message passing technique between – OS kernel (server) – User (client) Executing System Calls ● User program issues call ● Core kernel looks up call in syscall table ● Kernel module handles syscall action ● Module returns result of system call ● Core kernel forwards result to user Module is not Loaded... ● User program issues call ● Core kernel looks up call in syscall table ● Kernel module isn't loaded to handle action ● ... ● Where does call go? System Call Wrappers ● Wrapper calls system call if loaded – Otherwise returns an error ● Needs to be in a separate location so that the function can actually be called – Uses function pointer to point to kernel module implementation Adding System Calls ● You'll need to add and implement: – int start_elevator(void); – int issue_request(int, int, int); – int stop_elevator(void); ● As an example, let's add a call to printk an argument passed in: – int test_call(int); Adding System Calls ● Files to add (project files): – /usr/src/test_kernel/hello_world/test_call.c – /usr/src/test_kernel/hello_world/hello.c – /usr/src/test_kernel/hello_world/Makefile ● Files to modify (core kernel): – /usr/src/test_kernel/arch/x86/entry/syscalls/syscall_64.tbl – /usr/src/test_kernel/include/linux/syscalls.h – /usr/src/test_kernel/Makefile hello_world/test_call.c ● #include <linux/linkage.h> ● #include <linux/kernel.h> ● #include -

Anatomy of Linux Loadable Kernel Modules a 2.6 Kernel Perspective
Anatomy of Linux loadable kernel modules A 2.6 kernel perspective Skill Level: Intermediate M. Tim Jones ([email protected]) Consultant Engineer Emulex Corp. 16 Jul 2008 Linux® loadable kernel modules, introduced in version 1.2 of the kernel, are one of the most important innovations in the Linux kernel. They provide a kernel that is both scalable and dynamic. Discover the ideas behind loadable modules, and learn how these independent objects dynamically become part of the Linux kernel. The Linux kernel is what's known as a monolithic kernel, which means that the majority of the operating system functionality is called the kernel and runs in a privileged mode. This differs from a micro-kernel, which runs only basic functionality as the kernel (inter-process communication [IPC], scheduling, basic input/output [I/O], memory management) and pushes other functionality outside the privileged space (drivers, network stack, file systems). You'd think that Linux is then a very static kernel, but in fact it's quite the opposite. Linux can be dynamically altered at run time through the use of Linux kernel modules (LKMs). More in Tim's Anatomy of... series on developerWorks • Anatomy of Linux flash file systems • Anatomy of Security-Enhanced Linux (SELinux) • Anatomy of real-time Linux architectures • Anatomy of the Linux SCSI subsystem • Anatomy of the Linux file system • Anatomy of the Linux networking stack Anatomy of Linux loadable kernel modules © Copyright IBM Corporation 1994, 2008. All rights reserved. Page 1 of 11 developerWorks® ibm.com/developerWorks • Anatomy of the Linux kernel • Anatomy of the Linux slab allocator • Anatomy of Linux synchronization methods • All of Tim's Anatomy of.. -
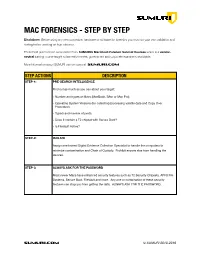
SUMURI Macintosh Forensics Best Practices
! MAC FORENSICS - STEP BY STEP Disclaimer: Before using any new procedure, hardware or software for forensics you must do your own validation and testing before working on true evidence. These best practices are summarized from SUMURI’s Macintosh Forensic Survival Courses which is a vendor- neutral training course taught to law enforcement, government and corporate examiners worldwide. More information about SUMURI can be found at SUMURI.com STEP ACTIONS DESCRIPTION STEP-1: PRE-SEARCH INTELLIGENCE Find out as much as you can about your target: • Number and types of Macs (MacBook, iMac or Mac Pro). • Operating System Versions (for collecting/processing volatile data and Copy Over Procedure). • Type/s and number of ports. • Does it contain a T2 chipset with Secure Boot? • Is FileVault Active? STEP-2: ISOLATE Assign one trained Digital Evidence Collection Specialist to handle the computers to minimize contamination and Chain of Custody. Prohibit anyone else from handling the devices. STEP-3: ALWAYS ASK FOR THE PASSWORD Most newer Macs have enhanced security features such as T2 Security Chipsets, APFS File Systems, Secure Boot, FileVault and more. Any one or combination of these security features can stop you from getting the data. ALWAYS ASK FOR THE PASSWORD. SUMURI.com © SUMURI 2010-2019 ! STEP ACTIONS DESCRIPTION STEP-4: IF COMPUTER IS ON - SCREEN SAVER PASSWORD ACTIVE Options are: • Ask for the Password - Confirm password and proceed to Step-6. • Restart to Image RAM - Connect a RAM Imaging Utility to the Mac such as RECON IMAGER. Conduct a soft-restart (do not power off if possible and image the RAM).