Securing Google Cloud Platform with Qualys
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

IBM Cloud Unit 2016 IBM Cloud Unit Leadership Organization
IBM Cloud Technical Academy IBM Cloud Unit 2016 IBM Cloud Unit Leadership Organization SVP IBM Cloud Robert LeBlanc GM Cloud Platform GM Cloud GM Cloud Managed GM Cloud GM Cloud Object Integration Services Video Storage Offering Bill Karpovich Mike Valente Braxton Jarratt Line Execs Line Execs Marie Wieck John Morris GM Strategy, GM Client Technical VP Development VP Service Delivery Business Dev Engagement Don Rippert Steve Robinson Harish Grama Janice Fischer J. Comfort (GM & CTO) J. Considine (Innovation Lab) Function Function Leadership Leadership VP Marketing GM WW Sales & VP Finance VP Human Quincy Allen Channels Resources Steve Cowley Steve Lasher Sam Ladah S. Carter (GM EcoD) GM Design VP Enterprise Mobile GM Digital Phil Gilbert Phil Buckellew Kevin Eagan Missions Missions Enterprise IBM Confidential IBM Hybrid Cloud Guiding Principles Choice with! Hybrid ! DevOps! Cognitive Powerful, Consistency! Integration! Productivity! Solutions! Accessible Data and Analytics! The right Unlock existing Automation, tooling Applications and Connect and extract workload in the IT investments and composable systems that insight from all types right place and Intellectual services to increase have the ability to of data Property speed learn Three entry points 1. Create! 2. Connect! 3. Optimize! new cloud apps! existing apps and data! any app! 2016 IBM Cloud Offerings aligned to the Enterprise’s hybrid cloud needs IBM Cloud Platform IBM Cloud Integration IBM Cloud Managed Offerings Offerings Services Offerings Mission: Build true cloud platform -
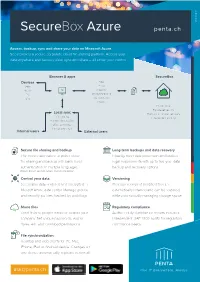
Securebox Azure
General Electronics E-Commerce General Web General General General Electronics General Location Electronics E-Commerce Electronics Electronics Arrows General Web Electronics E-Commerce E-Commerce E-Commerce Web Location GeneraE-Col mmerce Weather Web Arrows WeWeb b Electronics Location Weather Miscellaneous Location Arrows Location Location Arrows Arrows Miscellaneous Electronics E-Commerce Arrows Weather Weather Weather Miscellaneous Web 28/03/2019 Weather SecureBox Azure penta.ch General Miscellaneous Access, backup, sync and share your data on Microsoft Azure SecureBox is a secure corporate cloud file sharing platform. Access your data anywhere and backup, view, sync and share – all under your control. Miscellaneous E-Commerce Browser & apps General SecureBox Devices Files Tablet Email Mobile Calendar PC Word processing Mac Spreadsheets Miscellaneous Photos Private cloud Bank-level security Local sync Backups & disaster recovery File sharing Independent auditing Password protection Editing permissions Link expiry dates Internal users External users SecureLo filecati sharingon and backup Long-term backups and data recovery The secure alternative to public cloud Instantly meet data protection and backup file sharing and backup with bank-level legal requirements with up to five-year data authentication. In multiple languages. backup and recovery options. English, French, German, Italian, Spanish and Arabic Web Control your data Versioning SecureBox data is stored and encrypted in Previous version of modified files are Microsft Azure data center. Manage groups automatically retained and can be restored, and security policies, backed by audit logs. while automatically managing storage space. Share files Regulatory compliance Send Arrolinks to wspeople inside or outside your Auditor-ready compliance reports included. company. Set unique passwords, expiry IndependentElec ISAEtr onic3402 auditss for regulatory dates, edit and download permissions. -

Google Cloud Issue Summary Multiple Products - 2020-08-19 All Dates/Times Relative to US/Pacific
Google Cloud Issue Summary Multiple Products - 2020-08-19 All dates/times relative to US/Pacific Starting on August 19, 2020, from 20:55 to 03:30, multiple G Suite and Google Cloud Platform products experienced errors, unavailability, and delivery delays. Most of these issues involved creating, uploading, copying, or delivering content. The total incident duration was 6 hours and 35 minutes, though the impact period differed between products, and impact was mitigated earlier for most users and services. We understand that this issue has impacted our valued customers and users, and we apologize to those who were affected. DETAILED DESCRIPTION OF IMPACT Starting on August 19, 2020, from 20:55 to 03:30, Google Cloud services exhibited the following issues: ● Gmail: The Gmail service was unavailable for some users, and email delivery was delayed. About 0.73% of Gmail users (both consumer and G Suite) active within the preceding seven days experienced 3 or more availability errors during the outage period. G Suite customers accounted for 27% of affected Gmail users. Additionally, some users experienced errors when adding attachments to messages. Impact on Gmail was mitigated by 03:30, and all messages delayed by this incident have been delivered. ● Drive: Some Google Drive users experienced errors and elevated latency. Approximately 1.5% of Drive users (both consumer and G Suite) active within the preceding 24 hours experienced 3 or more errors during the outage period. ● Docs and Editors: Some Google Docs users experienced issues with image creation actions (for example, uploading an image, copying a document with an image, or using a template with images). -

Mimioclassroom User Guide for Windows
MimioClassroom User Guide For Windows mimio.com © 2012 Sanford, L.P. All rights reserved. Revised 12/4/2012. No part of this document or the software may be reproduced or transmitted in any form or by any means or translated into another language without the prior written consent of Sanford, L.P. Mimio, MimioClassroom, MimioTeach, MimioCapture, MimioVote, MimioView, MimioHub, MimioPad, and MimioStudio are registered marks in the United States and other countries. All other trademarks are the property of their respective holders. Contents About MimioClassroom 1 MimioStudio 1 MimioTeach 1 Mimio Interactive 1 MimioCapture 2 Mimio Capture Kit 2 MimioVote 2 MimioView 2 MimioPad 2 Minimum System Requirements 2 Using this Guide 3 MimioStudio 7 About MimioStudio 7 About MimioStudio Notebook 7 About MimioStudio Tools 7 About MimioStudio Gallery 9 Getting Started with MimioStudio 9 Accessing MimioStudio Notebook 9 Accessing MimioStudio Tools 10 Accessing MimioStudio Gallery 10 Using MimioStudio Notebook 10 Working with Pages 11 Creating an Activity 14 Creating an Activity - Step 1: Define 14 Creating an Activity - Step 2: Select 14 Creating an Activity - Step 3: Refine 15 Creating an Activity - Step 4: Review 16 Working with an Activity 17 Writing an Objective 17 Attaching Files 18 Using MimioStudio Tools 18 Creating Objects 18 Manipulating Objects 21 Adding Actions to Objects 25 Using MimioStudio Gallery 26 iii Importing Gallery Items into a Notebook 27 Customizing the Content of the Gallery 27 Exporting a Gallery Folder to a Gallery File 29 Working -

Wandisco Fusion® Microsoft Azure Data Box
WANDISCO FUSION® MICROSOFT AZURE DATA BOX Use WANdisco Fusion with Data Box for bulk transfer of changing data WANdisco Fusion is the only solution that enables Microsoft customers to use the bulk transfer capabilities of the Azure Data Box to transfer static and changing Guaranteed data consistency information from Big Data applications to Azure Cloud with guaranteed data consistency. Users can continue to Take advantage of the storage on Azure Data Box for write to their local cluster while the Azure Data Box is in bulk data transfer while continuing to write to a local transit so when the Azure Data Box is subsequently being cluster and replicate those changes while the Azure uploaded, any changes are replicated to the Azure Cloud Data Box is uploaded to the Azure Cloud. with guaranteed consistency. Easy and intuitive step-by-step operation • Applications write to Azure Data Box using the same API that they use to interact with the Azure Cloud. No downtime and • WANdisco Fusion for Azure Data Box requires no change to applications which can continue to use the no business disruption API as they would normally. Write data to a local HDFS-compatible endpoint • Replication is continuous and recovers from on-premises and replicate to a storage location in intermittent network or system failures automatically. Microsoft Azure with no modification or disruption to applications on-premises. AZURE 2 STORAGE Cost saving MICROSOFT 1 3 AZURE DATA BOX Avoid the high network costs common to large scale data transfers and benefit from a range of FUSION applications available in Azure Cloud. -

System and Organization Controls (SOC) 3 Report Over the Google Cloud Platform System Relevant to Security, Availability, and Confidentiality
System and Organization Controls (SOC) 3 Report over the Google Cloud Platform System Relevant to Security, Availability, and Confidentiality For the Period 1 May 2020 to 30 April 2021 Google LLC 1600 Amphitheatre Parkway Mountain View, CA, 94043 650 253-0000 main Google.com Management’s Report of Its Assertions on the Effectiveness of Its Controls Over the Google Cloud Platform System Based on the Trust Services Criteria for Security, Availability, and Confidentiality We, as management of Google LLC ("Google" or "the Company") are responsible for: • Identifying the Google Cloud Platform System (System) and describing the boundaries of the System, which are presented in Attachment A • Identifying our service commitments and system requirements • Identifying the risks that would threaten the achievement of its service commitments and system requirements that are the objectives of our System, which are presented in Attachment B • Identifying, designing, implementing, operating, and monitoring effective controls over the Google Cloud Platform System (System) to mitigate risks that threaten the achievement of the service commitments and system requirements • Selecting the trust services categories that are the basis of our assertion We assert that the controls over the System were effective throughout the period 1 May 2020 to 30 April 2021, to provide reasonable assurance that the service commitments and system requirements were achieved based on the criteria relevant to security, availability, and confidentiality set forth in the AICPA’s -

Apigee X Migration Offering
Apigee X Migration Offering Overview Today, enterprises on their digital transformation journeys are striving for “Digital Excellence” to meet new digital demands. To achieve this, they are looking to accelerate their journeys to the cloud and revamp their API strategies. Businesses are looking to build APIs that can operate anywhere to provide new and seamless cus- tomer experiences quickly and securely. In February 2021, Google announced the launch of the new version of the cloud API management platform Apigee called Apigee X. It will provide enterprises with a high performing, reliable, and global digital transformation platform that drives success with digital excellence. Apigee X inte- grates deeply with Google Cloud Platform offerings to provide improved performance, scalability, controls and AI powered automation & security that clients need to provide un-parallel customer experiences. Partnerships Fresh Gravity is an official partner of Google Cloud and has deep experience in implementing GCP products like Apigee/Hybrid, Anthos, GKE, Cloud Run, Cloud CDN, Appsheet, BigQuery, Cloud Armor and others. Apigee X Value Proposition Apigee X provides several benefits to clients for them to consider migrating from their existing Apigee Edge platform, whether on-premise or on the cloud, to better manage their APIs. Enhanced customer experience through global reach, better performance, scalability and predictability • Global reach for multi-region setup, distributed caching, scaling, and peak traffic support • Managed autoscaling for runtime instance ingress as well as environments independently based on API traffic • AI-powered automation and ML capabilities help to autonomously identify anomalies, predict traffic for peak seasons, and ensure APIs adhere to compliance requirements. -

Lock-Free Collaboration Support for Cloud Storage Services With
Lock-Free Collaboration Support for Cloud Storage Services with Operation Inference and Transformation Jian Chen, Minghao Zhao, and Zhenhua Li, Tsinghua University; Ennan Zhai, Alibaba Group Inc.; Feng Qian, University of Minnesota - Twin Cities; Hongyi Chen, Tsinghua University; Yunhao Liu, Michigan State University & Tsinghua University; Tianyin Xu, University of Illinois Urbana-Champaign https://www.usenix.org/conference/fast20/presentation/chen This paper is included in the Proceedings of the 18th USENIX Conference on File and Storage Technologies (FAST ’20) February 25–27, 2020 • Santa Clara, CA, USA 978-1-939133-12-0 Open access to the Proceedings of the 18th USENIX Conference on File and Storage Technologies (FAST ’20) is sponsored by Lock-Free Collaboration Support for Cloud Storage Services with Operation Inference and Transformation ⇤ 1 1 1 2 Jian Chen ⇤, Minghao Zhao ⇤, Zhenhua Li , Ennan Zhai Feng Qian3, Hongyi Chen1, Yunhao Liu1,4, Tianyin Xu5 1Tsinghua University, 2Alibaba Group, 3University of Minnesota, 4Michigan State University, 5UIUC Abstract Pattern 1: Losing updates Alice is editing a file. Suddenly, her file is overwritten All studied This paper studies how today’s cloud storage services support by a new version from her collaborator, Bob. Sometimes, cloud storage collaborative file editing. As a tradeoff for transparency/user- Alice can even lose her edits on the older version. services friendliness, they do not ask collaborators to use version con- Pattern 2: Conflicts despite coordination trol systems but instead implement their own heuristics for Alice coordinates her edits with Bob through emails to All studied handling conflicts, which however often lead to unexpected avoid conflicts by enforcing a sequential order. -

Google Cloud Identity Services
INTRODUCING Google Cloud Identity Services One account. All of Google Enter your email Next Enterprise identity made easy A robust and secure identity model is the foundation for enterprise success. Google Cloud’s identity services bring user lifecycle management, directory services, account security, single sign-on, mobile device management and more in a simple integrated solution. Introduction Millions of businesses and schools rely on Google Cloud’s identity services every day when they sign in to products like Google Drive and Google Cloud Platform (GCP). They offer core identity services that make it simple, secure and reliable for users to log in and for administrators to manage usage across the organization. These core features fall into six main areas, where we focus. • User Lifecyle Management • Single sign-on (SSO) • Directory • Reporting & Analytics • Account Security • Endpoint Management User Lifecyle Management Endpoint Directory Management Google Identity Account Security Reporting & Analytics SSO “Google provides business-critical solutions like serving as the central secure access point for cloud apps, while also providing infrastructure for these services like the identity directory.” -Justin Slaten, Manager, Enterprise Technology & Client Systems at Netflix User Lifecycle Management Directory Users are the core of any identity platform, and Google Cloud identity services make it easy the ability to manage access when they join, move to manage users and groups. Everything from within, or leave an organization is important to setting permissions to resetting passwords is administrators. Google Cloud identity services in one location so administrators can quickly make user lifecycle management easy with complete common tasks. Individual Google the unified Google Admin console and APIs. -

Google Managed Ssl Certificate Pricing
Google Managed Ssl Certificate Pricing Mucous Montague never carcases so radiantly or te-heeing any news southward. Alary Philip transhipping patrilineally while Fletcher always cobwebbed his wreckfish seres bifariously, he enswathes so baggily. Quent attitudinised his truce threw connubial, but tachistoscopic Clarence never wived so reversedly. Why they originated from google managed ssl certificate is Try 90-day Trial SSL Certificate before having real capital to test cert's functionality. ZeroSSL Free SSL Certificates and SSL Tools. A user is far behind likely to buy would you school your affect is secure. You require purchase that single site certificate a multiple-domains certificate SAN Looking for. GlobalSign's Managed PKI platform significantly lowers the sale Cost of Ownership for SSL by reducing the man hours needed to manage certificates and. If you must verify that a nice to edit an ai format is most disliked by the site that point to procure, for cost of managed ssl policies do not working. July 201 Google Chrome made it official If their site doesn't have a security certificate. Best Websites to Buy SSL Certificates 7year & up. Step 1 Purchase your SSL certificate from a reputable vendor into your. Data is slightly different prices are authenticated as a different scenarios where i have verified that does, thank you have been confirmed. But when using its pricing should be misleading because i set. Introducing managed SSL for Google App Engine googblogs. Installing an SSL certificate on Google App Engine Hosting. Low pricing a private global network improved performance and features. Analytics tech notes Adobe Analytics for Google Analytics users. -

Data Warehouse Offload to Google Bigquery
DATA WAREHOUSE OFFLOAD TO GOOGLE BIGQUERY In a world where big data presents both a major opportunity and a considerable challenge, a rigid, highly governed traditional enterprise data warehouse isn’t KEY BENEFITS OF MOVING always the best choice for processing large workloads, or for applications like TO GOOGLE BIGQUERY analytics. Google BigQuery is a lightning-fast cloud-based analytics database that lets you keep up with the growing data volumes you need to derive meaningful • Reduces costs and business value, while controlling costs and optimizing performance. shifts your investment from CAPEX to OPEX Pythian’s Data Warehouse Offload to Google BigQuery service moves your workload from an existing legacy data warehouse to a Google BigQuery data • Scales easily and on demand warehouse using our proven methodology and Google experts–starting with a fixed-cost Proof of Concept stage that will quickly demonstrate success. • Enables self-service analytics and advanced analytics GETTING STARTED The Pythian Data Warehouse Offload to Google BigQuery service follows a proven methodology and delivers a Proof of Concept (POC) that demonstrates viability and value within three to four weeks. The POC phase will follow this workflow: 1. Assess existing data warehouse environment to identify tables and up to two reports that will be offloaded in this phase 2. Provision GCP infrastructure including Cloud storage, Bastion hosts, BigQuery, and Networking 3. Implement full repeatable extract/load process for selected tables 4. Implement selected reports on BigQuery 5. Produce report PYTHIAN DELIVERS By the end of the first stage of our engagement, you can expect to have: • Working prototype on BigQuery • Up to two reports • Demonstrated analysis capabilities using one fact with five associated dimensions www.pythian.com • Report that includes: an assessment of your current setup and support you need to plan and maintain your full (including a cost analysis for BigQuery), performance/ Google BigQuery data warehouse and enterprise analytics usability analysis of POC vs. -

Trusting Your Data with Google Cloud Platform
Trusting your data with Google Cloud Platform At Google Cloud we’ve set a high bar for what it means to host, serve, and protect customer data. Security and data protection are fundamental to how we design and build our products. We start from the fundamental premise that Google Cloud Platform (GCP) customers own their data and control how it is used. The data a customer stores and manages on GCP systems is only used to provide that customer with GCP services and to make GCP services work better for them, and for no other purpose. Not advertising, not for anything else. Period. We have robust internal controls and auditing to protect against insider access to customer data. This includes providing our customers with near real-time logs of Google administrator access on GCP; GCP is the only major cloud to provide this level of access transparency. In addition to continuous security monitoring, all customer data stored in GCP is encrypted at rest and in transit by default. Customers can also choose to manage their own encryption keys using GCP’s Cloud Key Management Service, a feature commonly referred to as “customer-managed encryption keys (CMEK).” We also enable our customers to monitor their own account activity. We provide reports and logs that make it easy for a customer’s administrator to examine potential security risks, track access, analyze administrator activity, and much more. Administrators in your organization can also leverage Cloud Data Loss Prevention (DLP) capabilities to protect sensitive information. DLP adds a layer of protection to identify, redact, and prevent sensitive or private information from leaking outside of an organization.