Ios, Your OS, Everybody's OS: Vetting and Analyzing Network Services of Ios Applications
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Security to Android Mobile Applications: Camera Based
ISSN 2319-8885 Vol.04,Issue.29, August-2015, Pages:5534-5539 www.ijsetr.com Security to Android Mobile Applications: Camera Based Security and Theft Alert Mobile Phones 1 2 3 SANA SULTANA , G.VEERANJANEYULU , SALEHA FARHA 1PG Scholar, Dept of CSE, Shadan Women’s College of Engineering and Technology, Hyderabad, TS, India, E-mail: [email protected]. 2Professor, Dept of CSE, Shadan Women’s College of Engineering and Technology, Hyderabad, TS, India, E-mail: [email protected]. 3HOD, Dept of CSE, Shadan Women’s College of Engineering and Technology, Hyderabad, TS, India, E-mail: [email protected]. Abstract: Now Smartphone’s are simply small computers with added services such as GSM, radio. Thus it is true to say that next generations of operating system will be on these Smartphone and the likes of windows, IOS and android are showing us the glimpse of this future. Android has already gained significant advantages on its counterparts in terms of market share. One of the reason behind this is the most important feature of Android is that it is open-source which makes it free and allows any one person could develop their own applications and publish them freely. This openness of android brings the developers and users a wide range of convenience but simultaneously it increases the security issues. The major threat of Android users is Malware infection via Android Application Market which is targeting some loopholes in the architecture mainly on the end-users part. Attackers can implement spy cameras in malicious apps such that the phone camera is launched automatically without the device owner’s notice, and the captured photos and videos are sent out to these remote attackers. -

Building Vision and Voice Based Robots Using Android
1st Annual International Interdisciplinary Conference, AIIC 2013, 24-26 April, Azores, Portugal - Proceedings- BUILDING VISION AND VOICE BASED ROBOTS USING ANDROID Pradeep N. , Assistant Professor Dr. Mohammed Sharief, Professor Dr. M. Siddappa, Professor Dept. of Computer Science and Engineering, SSIT, Tumkur, Karnataka, India Abstract: This project uses Android, along with cloud based APIs and the Arduino microcontroller, to create a software-hardware system that attempts to address several current problems in robotics, including, among other things, line-following, obstacle-avoidance, voice control, voice synthesis, remote surveillance, motion & obstacle detection, face detection, remote live image streaming and remote photography in panorama & time-lapse mode. The rover, built upon a portable five-layered architecture, will use several mature and a few experimental algorithms in AI, Computer Vision, Robot Kinetics and Dynamics behind-the-scene to provide its prospective user in defense, entertainment or industrial sector a positive user experience. A minimal amount of security is achieved via. a handshake using MD5, SHA1 and AES. It even has a Twitter account for autonomous social networking. Key Words: Voice Synthesis, Voice Control, Robot-User Interaction, Face Detection, Motion and Object Detection, Remote Surveillance, Panoramic and Time-lapse Photography, Line-following and Obstacle-Avoiding Robotics, AI, Computer Vision, Image Processing, Network Security Introduction Android, which is actually a software stack, running atop the Linux kernel, is one of the most successful operating systems available to mobile users today. This success can be attributed to the fact that Android makes development of application softwares ('apps') really easy by allowing developers to code in Java (among many other languages) and thus enabling them to take advantage of the innumerable packages and modules made available by the Java community. -

Geo-Fencing »
PRODUCT CATALOG | SEPTEMBER 2018 Your partner for data driven programmatic solutions Table of Contents Cross-Platform Capabilities » ..................................................... 5 Service Models » .................................................................................................... 7 Targeting Tactics » ................................................................................ 9 Geo-Fencing » ......................................................................................................... 10 Keyword Search Retargeting » ............................................................................ 22 Facebook Newsfeed » ........................................................................................... 23 Native Programmatic » .......................................................................................... 24 Site Retargeting » ................................................................................................... 25 Contextual Targeting » .......................................................................................... 26 CRM Targeting » ..................................................................................................... 28 Programmatic Video » ........................................................................ 29 PRODUCT CATALOG OTT/CTV » ......................................................................................................... 31 SEPTEMBER 2018 The Data Difference » ......................................................................... -

When Program Analysis Meets Bytecode Search: Targeted and Efficient Inter-Procedural Analysis of Modern Android Apps in Backdroid
When Program Analysis Meets Bytecode Search: Targeted and Efficient Inter-procedural Analysis of Modern Android Apps in BackDroid Daoyuan Wu1, Debin Gao2, Robert H. Deng2, and Rocky K. C. Chang3 1The Chinese University of Hong Kong 2Singapore Management University 3The Hong Kong Polytechnic University Contact: [email protected] Abstract—Widely-used Android static program analysis tools, be successfully analyzed by its underlying FlowDroid tool. e.g., Amandroid and FlowDroid, perform the whole-app inter- Although HSOMiner [53] increased the size of the analyzed procedural analysis that is comprehensive but fundamentally apps, the average app size is still only 8.4MB. Even for difficult to handle modern (large) apps. The average app size has these small apps, AppContext timed out for 16.1% of the increased three to four times over five years. In this paper, we 1,002 apps tested and HSOMiner similarly failed in 8.4% explore a new paradigm of targeted inter-procedural analysis that can skip irrelevant code and focus only on the flows of security- of 3,000 apps, causing a relatively high failure rate. Hence, sensitive sink APIs. To this end, we propose a technique called this is not only a performance issue, but also the detection on-the-fly bytecode search, which searches the disassembled app burden. Additionally, third-party libraries were often ignored. bytecode text just in time when a caller needs to be located. In this For example, Amandroid by default skipped the analysis of way, it guides targeted (and backward) inter-procedural analysis 139 popular libraries, such as AdMob, Flurry, and Facebook. -

BAMMA on FITE PR Release
For Immediate Release BAMMA 32 is set to air live on FITE TV Friday November 10 New York, NY – November 6, 2017 - BAMMA and FITE TV are delighted to announce a new partnership that will see BAMMA events broadcast around the world including the United States of America, Canada, Australia & Russia. Building on the ever expanding broadcast footprint, the new territories will be able to watch the upcoming BAMMA Dublin, Ireland event this Friday November the 10th from the 3Arena, Dublin. FITE is the leader in the combat sports video streaming category featuring the best of the MMA, Boxing and Pro Wrestling world. With over 600 live streamed events since its February 2016 launch and 5,000 plus hours of VOD content, FITE is the digital destination for the combat sports enthusiast. FITE programming is available as a free downloadable app through the Google Play and iTunes app stores and on its website www.FITE.tv. "The debut of BAMMA in November on FITE is another milestone achieved in our quest to continue to bring the best of MMA action from around the world to the FITE TV platform. BAMMA has a long tradition in MMA in the UK and we are excited to have them as part of the team," said FITE CEO Kosta Jordanov. BAMMA Dublin will mark the first of its broadcasted events for this multi-event deal. BAMMA 33 is set for Friday December 15th from the Metro Radio Arena in Newcastle, UK. BAMMA Dublin takes place at the 3Arena, Dublin on Friday November 10th and tickets are available at http://bit.ly/BAMMA32 ABOUT FITE brings premium combat sports programming to MMA, Boxing and Pro Wrestling fans to watch live on every screen - computer, tablet, phone and TV.The FITE mobile app works with any Wi-Fi connected television around the world as well as streaming devices such as Chromecast, PSX, Xbox, Apple TV and more. -

2015 IOGEAR Mini Guide August5a.Indd
PRODUCT GUIDE www.iogear.com IOGEAR’s A/V & Digital Home solutions allow you to enjoy HD media content wirelessly sent from different HD sources to your TV displays in multiple rooms in your home. at Home IOGEAR’s Computer Accessories offer the convenience to connect all your devices together so you can work more efficiently. IOGEAR, an ATEN International Company, headquartered in Foothill Ranch, California, manufactures innovative consumer electronics and information technology at Work solutions that enable convergence through connectivity. Travel with style and peace For further information, please visit IOGEAR’s Web site at of mind. IOGEAR Mobile www.iogear.com or the company’s blog at Solutions make it easy, fast www.iogear.com/blog. IOGEAR can also be followed on and convenient to charge Twitter @IOGEAR and Facebook. your smartphones and tablets. on-the-Go A/V & DIGITAL HOME | MOBILITY www.iogear.com KVM & KVMP | COMPUTER ACCESSORIES | NETWORKING IOGEAR’s A/V & Digital Home solutions allow you to enjoy HD media content wirelessly sent from different HD sources to your TV displays in multiple rooms in your home. at Home IOGEAR’s Computer Accessories offer the convenience to connect all your devices together so you can work more efficiently. IOGEAR, an ATEN International Company, headquartered in Foothill Ranch, California, manufactures innovative consumer electronics and information technology at Work solutions that enable convergence through connectivity. Travel with style and peace For further information, please visit IOGEAR’s Web site at of mind. IOGEAR Mobile www.iogear.com or the company’s blog at Solutions make it easy, fast www.iogear.com/blog. -

Självständigt Arbete På Grundnivå Independent Degree Project - First Cycle
Självständigt arbete på grundnivå Independent degree project - first cycle Computer Engineering A framework for communicating with Android apps from the browser Karl Lindström A framework for communicating with Android apps from the browser Karl Lindström 2014-05-29 MID SWEDEN UNIVERSITY Avdelningen för Informations- och kommunikationssystem (IKS) Examiner: Ulf Jennehag, [email protected] Supervisor: Magnus Eriksson, [email protected] Author: Karl Lindström, [email protected] Degree programme: International Bachelor's Programme in Computer Engi- neering, 180 credits Main field of study: Computer Engineering Semester, year: 1, 2014 ii A framework for communicating with Android apps from the browser Karl Lindström 2014-05-29 Abstract With the recent growth of the mobile market, companies want to target mobile devices while at the same time keeping product development costs low. One way to do this is to develop web applications, which are accessed from a mobile de- vice’s web browser, instead of native applications. The same web application can then be used on different platforms such as Android and iOS. However, devices such as smart phones and tablets often include cameras and sensors that a web ap- plication may want to access, but which are only accessible from native applica- tions. A framework was developed that enables web applications to communicate with native Android applications. Native applications are launched by clicking a link in the browser, and the result produced is made available to the web applica- tion through a HTTP POST request or a local web server running on the device. Key characteristics of the framework include ease of extension and the ability to enable secure (SSL) communication if desired. -

Computing Homomorphic Program Invariants Benjamin Robert Holland Iowa State University
Iowa State University Capstones, Theses and Graduate Theses and Dissertations Dissertations 2018 Computing homomorphic program invariants Benjamin Robert Holland Iowa State University Follow this and additional works at: https://lib.dr.iastate.edu/etd Part of the Computer Sciences Commons Recommended Citation Holland, Benjamin Robert, "Computing homomorphic program invariants" (2018). Graduate Theses and Dissertations. 16818. https://lib.dr.iastate.edu/etd/16818 This Dissertation is brought to you for free and open access by the Iowa State University Capstones, Theses and Dissertations at Iowa State University Digital Repository. It has been accepted for inclusion in Graduate Theses and Dissertations by an authorized administrator of Iowa State University Digital Repository. For more information, please contact [email protected]. Computing homomorphic program invariants by Benjamin Robert Holland A dissertation submitted to the graduate faculty in partial fulfillment of the requirements for the degree of DOCTOR OF PHILOSOPHY Major: Computer Engineering (Secure and Reliable Computing) Program of Study Committee: Suraj Kothari, Co-major Professor Yong Guan, Co-major Professor Srikanta Tirthapura Hridesh Rajan Wei Le The student author, whose presentation of the scholarship herein was approved by the program of study committee, is solely responsible for the content of this dissertation. The Graduate College will ensure this dissertation is globally accessible and will not permit alterations after a degree is conferred. Iowa State University Ames, Iowa 2018 Copyright © Benjamin Robert Holland, 2018. All rights reserved. ii DEDICATION I would like to dedicate this work to my family, friends, colleagues, mentors, coworkers, and Amber. Without any of you this would not have been possible. -

Implementation of a Homematic Simulator Using Android
Fakultät für Informatik der Technische Universität München Bachelor’s Thesis in Informatics Implementation of a HomeMatic simulator using Android Johannes Neutze Fakultät für Informatik der Technische Universität München Bachelor’s Thesis in Informatics Implementation of a HomeMatic simulator using Android Implementierung eines HomeMatic Simulators unter Android Author: Johannes Neutze Supervisor: Prof. Dr. Uwe Baumgarten Advisor: Nils T. Kannengießer, M. Sc. Date: April 15, 2013 I assure the single handed composition of this bachelor thesis only supported by declared resources. Munich, 15th of April, 2013 Johannes Neutze Abstract This bachelor thesis is about the development of an Android application, simulating the HomeMatic system and the XMLAPI v1.2, designed to control the HomeMatic system, e.g. through the HomeDroid client. Configuration of the system, handshake with HomeDroid and persistent storage of the entire system status is implemented by using standard components, like a HTTP server, a relational database and an Android graphical user interface. As a result, the user can connect to the application via HomeDroid and interact with it, like with the real hardware. First, the foundation of emulated system and the environment used to develop the application, are explained. Then the system requirements are outlined and the architecture is illustrated. Finally, the implementation of each component, the graphical user interface and its testing are described. Table of contents Abstract..................................................................................................................................... -

An Industrial Study of Misusing Android Internet Sockets
When Program Analysis Meets Mobile Security: An Industrial Study of Misusing Android Internet Sockets Wenqi Bu Minhui Xue Lihua Xu East China Normal University, China New York University Shanghai East China Normal University, China [email protected] East China Normal University, China [email protected] [email protected] Yajin Zhou Zhushou Tang Tao Xie China Pwnzen Infotech Inc., China University of Illinois at [email protected] [email protected] Urbana-Champaign, USA [email protected] ABSTRACT ACM Reference format: Despite recent progress in program analysis techniques to identify Wenqi Bu, Minhui Xue, Lihua Xu, Yajin Zhou, Zhushou Tang, and Tao vulnerabilities in Android apps, significant challenges still remain Xie. 2017. When Program Analysis Meets Mobile Security: An Industrial Study of Misusing Android Internet Sockets. In Proceedings of 2017 11th for applying these techniques to large-scale industrial environ- Joint Meeting of the European Software Engineering Conference and the ACM ments. Modern software-security providers, such as Qihoo 360 and SIGSOFT Symposium on the Foundations of Software Engineering, Paderborn, Pwnzen (two leading companies in China), are often required to Germany, September 4–8, 2017 (ESEC/FSE’17), 6 pages. process more than 10 million mobile apps at each run. In this work, https://doi.org/10.1145/3106237.3117764 we focus on effectively and efficiently identifying vulnerable usage of Internet sockets in an industrial setting. To achieve this goal, we propose a practical hybrid approach that enables lightweight yet 1 INTRODUCTION precise detection in the industrial setting. In particular, we integrate Mobile apps and their users have witnessed a massive growth over the process of categorizing potential vulnerable apps with analysis the last decade. -

August 2018 M&A and Investment Summary
August 2018 M&A and Investment Summary Table of Contents 1 Overview of Monthly M&A and Investment Activity 3 2 Monthly M&A and Investment Activity by Industry Segment 9 3 Additional Monthly M&A and Investment Activity Data 41 4 About Petsky Prunier 58 Securities offered through Petsky Prunier Securities, LLC, member of FINRA. This M&A and Investment Summary has been prepared by and is being distributed in the United States by Petsky Prunier, a broker dealer registered with the U.S. SEC and a member of FINRA. 2 | M&A and Investment Summary August 2018 M&A and Investment Summary for All Segments Transaction Distribution . A total of 726 deals were announced in August 2018, of which 360 were worth $36.1 billion in aggregate reported value • August was the most active month of the past 36 months, highlighted by record activity in the Digital Media/Commerce and Business & IT Services segments . Software was the most active segment with 254 deals announced— 146 of these transactions reported $10.0 billion in value . Digital Media/Commerce was the most valuable segment with 157 transactions, 102 of which were worth a reported $13.2 billion . Strategic buyers announced 346 deals (65 reported $14.3 billion in value) . VC/Growth Capital investors announced 347 transactions (290 reported $16.0 billion in value) . Private Equity investors announced 33 deals during the month (five reported $5.8 billion in value) August 2018 BUYER/INVESTOR BREAKDOWN Transactions Reported Value Strategic Buyout Venture/Growth Capital # % $MM % # $MM # $MM # $MM Software 254 35% $9,950.1 28% 89 $6,684.1 7 - 158 $3,266.0 Digital Media/Commerce 157 22% 13,213.4 37% 55 2,998.9 4 - 98 10,214.5 Business Services 130 18% 3,159.4 9% 91 2,379.0 9 75.0 30 705.4 Marketing Technology 72 10% 1,870.6 5% 31 548.4 3 50.0 38 1,272.2 Agency & Marketing Services 39 5% 775.5 2% 32 436.0 3 12.5 4 327.0 Traditional Media 32 4% 1,102.8 3% 24 800.8 4 230.0 4 72.0 *Note, transactions valued at $6 billion or more have been excluded from totals to limit comparative distortions. -
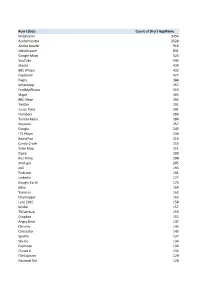
Row Labels Count of Short Appname Mobileiron 3454 Authenticator 2528
Row Labels Count of Short AppName MobileIron 3454 Authenticator 2528 Adobe Reader 916 vWorkspace 831 Google Maps 624 YouTube 543 iBooks 434 BBC iPlayer 432 Facebook 427 Pages 388 WhatsApp 357 FindMyiPhone 313 Skype 303 BBC News 292 Twitter 291 Junos Pulse 291 Numbers 289 TuneIn Radio 284 Keynote 257 Google 243 ITV Player 234 BoardPad 219 Candy Crush 215 Tube Map 211 Zipcar 209 Bus Times 208 mod.gov 205 4oD 193 Podcasts 191 LinkedIn 177 Google Earth 172 eBay 164 Yammer 163 Citymapper 163 Lync 2010 158 Kindle 157 TVCatchup 153 Dropbox 152 Angry Birds 147 Chrome 143 Calculator 143 Spotify 137 Sky Go 136 Evernote 134 iTunes U 132 FileExplorer 129 National Rail 128 iPlayer Radio 127 FasterScan 125 BBC Weather 125 FasterScan HD 124 Gmail 123 Instagram 116 Cleaner Brent 107 Viber 104 Find Friends 98 PDF Expert 95 Solitaire 91 SlideShark 89 Netflix 89 Dictation 89 com.amazon.AmazonUK 88 Flashlight 81 iMovie 79 Temple Run 2 77 Smart Office 2 74 Dictionary 72 UK & ROI 71 Journey Pro 71 iPhoto 70 TripAdvisor 68 Guardian iPad edition 68 Shazam 67 Messenger 65 Bible 64 BBC Sport 63 Rightmove 62 London 62 Sky Sports 61 Subway Surf 60 Temple Run 60 Yahoo Mail 58 thetrainline 58 Minion Rush 58 Demand 5 57 Documents 55 Argos 55 LBC 54 Sky+ 51 MailOnline 51 GarageBand 51 Calc 51 TV Guide 49 Phone Edition 49 Translate 48 Print Portal 48 Standard 48 Word 47 Skitch 47 CloudOn 47 Tablet Edition 46 MyFitnessPal 46 Bus London 46 Snapchat 45 Drive 42 4 Pics 1 Word 41 TED 39 Skyscanner 39 SoundCloud 39 PowerPoint 39 Zoopla 38 Flow Free 38 Excel 38 Radioplayer