Vetting and Analyzing Network Services of Ios Applications
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Geo-Fencing »
PRODUCT CATALOG | SEPTEMBER 2018 Your partner for data driven programmatic solutions Table of Contents Cross-Platform Capabilities » ..................................................... 5 Service Models » .................................................................................................... 7 Targeting Tactics » ................................................................................ 9 Geo-Fencing » ......................................................................................................... 10 Keyword Search Retargeting » ............................................................................ 22 Facebook Newsfeed » ........................................................................................... 23 Native Programmatic » .......................................................................................... 24 Site Retargeting » ................................................................................................... 25 Contextual Targeting » .......................................................................................... 26 CRM Targeting » ..................................................................................................... 28 Programmatic Video » ........................................................................ 29 PRODUCT CATALOG OTT/CTV » ......................................................................................................... 31 SEPTEMBER 2018 The Data Difference » ......................................................................... -

BAMMA on FITE PR Release
For Immediate Release BAMMA 32 is set to air live on FITE TV Friday November 10 New York, NY – November 6, 2017 - BAMMA and FITE TV are delighted to announce a new partnership that will see BAMMA events broadcast around the world including the United States of America, Canada, Australia & Russia. Building on the ever expanding broadcast footprint, the new territories will be able to watch the upcoming BAMMA Dublin, Ireland event this Friday November the 10th from the 3Arena, Dublin. FITE is the leader in the combat sports video streaming category featuring the best of the MMA, Boxing and Pro Wrestling world. With over 600 live streamed events since its February 2016 launch and 5,000 plus hours of VOD content, FITE is the digital destination for the combat sports enthusiast. FITE programming is available as a free downloadable app through the Google Play and iTunes app stores and on its website www.FITE.tv. "The debut of BAMMA in November on FITE is another milestone achieved in our quest to continue to bring the best of MMA action from around the world to the FITE TV platform. BAMMA has a long tradition in MMA in the UK and we are excited to have them as part of the team," said FITE CEO Kosta Jordanov. BAMMA Dublin will mark the first of its broadcasted events for this multi-event deal. BAMMA 33 is set for Friday December 15th from the Metro Radio Arena in Newcastle, UK. BAMMA Dublin takes place at the 3Arena, Dublin on Friday November 10th and tickets are available at http://bit.ly/BAMMA32 ABOUT FITE brings premium combat sports programming to MMA, Boxing and Pro Wrestling fans to watch live on every screen - computer, tablet, phone and TV.The FITE mobile app works with any Wi-Fi connected television around the world as well as streaming devices such as Chromecast, PSX, Xbox, Apple TV and more. -

2015 IOGEAR Mini Guide August5a.Indd
PRODUCT GUIDE www.iogear.com IOGEAR’s A/V & Digital Home solutions allow you to enjoy HD media content wirelessly sent from different HD sources to your TV displays in multiple rooms in your home. at Home IOGEAR’s Computer Accessories offer the convenience to connect all your devices together so you can work more efficiently. IOGEAR, an ATEN International Company, headquartered in Foothill Ranch, California, manufactures innovative consumer electronics and information technology at Work solutions that enable convergence through connectivity. Travel with style and peace For further information, please visit IOGEAR’s Web site at of mind. IOGEAR Mobile www.iogear.com or the company’s blog at Solutions make it easy, fast www.iogear.com/blog. IOGEAR can also be followed on and convenient to charge Twitter @IOGEAR and Facebook. your smartphones and tablets. on-the-Go A/V & DIGITAL HOME | MOBILITY www.iogear.com KVM & KVMP | COMPUTER ACCESSORIES | NETWORKING IOGEAR’s A/V & Digital Home solutions allow you to enjoy HD media content wirelessly sent from different HD sources to your TV displays in multiple rooms in your home. at Home IOGEAR’s Computer Accessories offer the convenience to connect all your devices together so you can work more efficiently. IOGEAR, an ATEN International Company, headquartered in Foothill Ranch, California, manufactures innovative consumer electronics and information technology at Work solutions that enable convergence through connectivity. Travel with style and peace For further information, please visit IOGEAR’s Web site at of mind. IOGEAR Mobile www.iogear.com or the company’s blog at Solutions make it easy, fast www.iogear.com/blog. -

August 2018 M&A and Investment Summary
August 2018 M&A and Investment Summary Table of Contents 1 Overview of Monthly M&A and Investment Activity 3 2 Monthly M&A and Investment Activity by Industry Segment 9 3 Additional Monthly M&A and Investment Activity Data 41 4 About Petsky Prunier 58 Securities offered through Petsky Prunier Securities, LLC, member of FINRA. This M&A and Investment Summary has been prepared by and is being distributed in the United States by Petsky Prunier, a broker dealer registered with the U.S. SEC and a member of FINRA. 2 | M&A and Investment Summary August 2018 M&A and Investment Summary for All Segments Transaction Distribution . A total of 726 deals were announced in August 2018, of which 360 were worth $36.1 billion in aggregate reported value • August was the most active month of the past 36 months, highlighted by record activity in the Digital Media/Commerce and Business & IT Services segments . Software was the most active segment with 254 deals announced— 146 of these transactions reported $10.0 billion in value . Digital Media/Commerce was the most valuable segment with 157 transactions, 102 of which were worth a reported $13.2 billion . Strategic buyers announced 346 deals (65 reported $14.3 billion in value) . VC/Growth Capital investors announced 347 transactions (290 reported $16.0 billion in value) . Private Equity investors announced 33 deals during the month (five reported $5.8 billion in value) August 2018 BUYER/INVESTOR BREAKDOWN Transactions Reported Value Strategic Buyout Venture/Growth Capital # % $MM % # $MM # $MM # $MM Software 254 35% $9,950.1 28% 89 $6,684.1 7 - 158 $3,266.0 Digital Media/Commerce 157 22% 13,213.4 37% 55 2,998.9 4 - 98 10,214.5 Business Services 130 18% 3,159.4 9% 91 2,379.0 9 75.0 30 705.4 Marketing Technology 72 10% 1,870.6 5% 31 548.4 3 50.0 38 1,272.2 Agency & Marketing Services 39 5% 775.5 2% 32 436.0 3 12.5 4 327.0 Traditional Media 32 4% 1,102.8 3% 24 800.8 4 230.0 4 72.0 *Note, transactions valued at $6 billion or more have been excluded from totals to limit comparative distortions. -
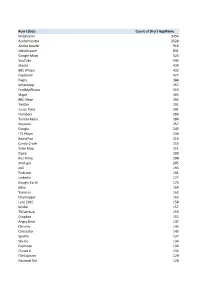
Row Labels Count of Short Appname Mobileiron 3454 Authenticator 2528
Row Labels Count of Short AppName MobileIron 3454 Authenticator 2528 Adobe Reader 916 vWorkspace 831 Google Maps 624 YouTube 543 iBooks 434 BBC iPlayer 432 Facebook 427 Pages 388 WhatsApp 357 FindMyiPhone 313 Skype 303 BBC News 292 Twitter 291 Junos Pulse 291 Numbers 289 TuneIn Radio 284 Keynote 257 Google 243 ITV Player 234 BoardPad 219 Candy Crush 215 Tube Map 211 Zipcar 209 Bus Times 208 mod.gov 205 4oD 193 Podcasts 191 LinkedIn 177 Google Earth 172 eBay 164 Yammer 163 Citymapper 163 Lync 2010 158 Kindle 157 TVCatchup 153 Dropbox 152 Angry Birds 147 Chrome 143 Calculator 143 Spotify 137 Sky Go 136 Evernote 134 iTunes U 132 FileExplorer 129 National Rail 128 iPlayer Radio 127 FasterScan 125 BBC Weather 125 FasterScan HD 124 Gmail 123 Instagram 116 Cleaner Brent 107 Viber 104 Find Friends 98 PDF Expert 95 Solitaire 91 SlideShark 89 Netflix 89 Dictation 89 com.amazon.AmazonUK 88 Flashlight 81 iMovie 79 Temple Run 2 77 Smart Office 2 74 Dictionary 72 UK & ROI 71 Journey Pro 71 iPhoto 70 TripAdvisor 68 Guardian iPad edition 68 Shazam 67 Messenger 65 Bible 64 BBC Sport 63 Rightmove 62 London 62 Sky Sports 61 Subway Surf 60 Temple Run 60 Yahoo Mail 58 thetrainline 58 Minion Rush 58 Demand 5 57 Documents 55 Argos 55 LBC 54 Sky+ 51 MailOnline 51 GarageBand 51 Calc 51 TV Guide 49 Phone Edition 49 Translate 48 Print Portal 48 Standard 48 Word 47 Skitch 47 CloudOn 47 Tablet Edition 46 MyFitnessPal 46 Bus London 46 Snapchat 45 Drive 42 4 Pics 1 Word 41 TED 39 Skyscanner 39 SoundCloud 39 PowerPoint 39 Zoopla 38 Flow Free 38 Excel 38 Radioplayer -

Download Movie for Free App Download Movie for Free App
download movie for free app Download movie for free app. Completing the CAPTCHA proves you are a human and gives you temporary access to the web property. What can I do to prevent this in the future? If you are on a personal connection, like at home, you can run an anti-virus scan on your device to make sure it is not infected with malware. If you are at an office or shared network, you can ask the network administrator to run a scan across the network looking for misconfigured or infected devices. Another way to prevent getting this page in the future is to use Privacy Pass. You may need to download version 2.0 now from the Chrome Web Store. Cloudflare Ray ID: 67a087b6e812c43d • Your IP : 188.246.226.140 • Performance & security by Cloudflare. 9 Best Free Apps for Streaming Movies. Stacy is a freelancer with over 20 years' experience writing about technology. She has published hundreds of articles, co-authored a book, and has appeared on national and local TV. Tweet Share Email. Streaming Devices Streaming TV, Movies, & More Music, Podcasts, & Audio Cutting the Cord. This list of free movie apps will put hundreds of free streaming movies at your fingertips. Install them on your smartphone or tablet and you'll be ready to watch the film of your choice in only a few minute's time. Not only do these free apps allow you to watch movies, but many also let you stream TV shows. This is a great way to catch up on your favorite shows when you're on the go. -

Thank You for Downloading This Free Sample of Pwtorch Newsletter #1409, Cover-Dated June 18, 2015. Please Feel Free to Link to I
Thank you for downloading this free sample of PWTorch Newsletter #1409, cover-dated June 18, 2015. Please feel free to link to it on Twitter or Facebook or message boards or any social media. Help spread the word! To become a subscriber and receive continued ongoing access to new editions of the weekly Pro Wrestling Torch Newsletter (in BOTH the PDF and All-Text formats) along with instant access to nearly 1,400 back issues dating back to the 1980s, visit this URL: www.PWTorch.com/govip You will find information on our online VIP membership which costs $99 for a year, $27.50 for three months, or $10 for a single month, recurring. It includes: -New PWTorch Newsletters in PDF and All-Text format weekly -Nearly 1,400 back issues of the PWTorch Newsletter dating back to the 1980s -Ad-free access to PWTorch.com -Ad-free access to the daily PWTorch Livecast -Over 50 additional new VIP audio shows every month -All new VIP audio shows part of RSS feeds that work on iTunes and various podcast apps on smart phones. Get a single feed for all shows or individual feeds for specific shows and themes. -Retro radio shows added regularly (including 100 Pro Wrestling Focus radio shows hosted by Wade Keller from the early 1990s immediately, plus Pro Wrestling Spotlight from New York hosted by John Arezzi and Total Chaos Radio hosted by Jim Valley during the Attitude Era) -Access to newly added VIP content via our free PWTorch App on iPhone and Android www.PWTorch.com/govip ALSO AVAILABLE: Print Copy Home Delivery of the Pro Wrestling Torch Newsletter 12 page edition for just $99 for a full year or $10 a month. -
User Manual Wireless Mobile and PC to TV
User Manual Wireless Mobile and PC to TV GWAVR PART NO. M1228-a www.iogear.com 1 ©2014 IOGEAR. All Rights Reserved. Part No. M1228-a IOGEAR, the IOGEAR logo, are trademarks or registered trademarks of IOGEAR. Microsoft and Windows are registered trademarks of Microsoft Corporation. All other brand and product names are trademarks or registered trademarks of their respective holders. IOGEAR makes no warranty of any kind with regards to the information presented in this document. All information furnished here is for informational purposes only and is subject to change without notice. IOGEAR assumes no responsibility for any inaccuracies or errors that may appear in this document. Table of Contents Introduction 4 Package Contents 5 System Requirements 5 Overview 6 Hardware Installation 7 Contect with Intel WiDi 8 Connect with Miracast 12 Connect with non-Miracast device (iOS/all other Android based) 16 Advanced Settings: 21 How to upgrade the firmware for GWAVR 25 Specification: 28 Compliance Information 29 Limited Warranty 30 Contact 30 3 Introduction IOGEAR's GWAVR allows you to enjoy all of your personal and online content wirelessly on your big screen HDTV. Using your smartphone, tablet or Intel® WiDi notebook you can sit back and experience your favorite movies, videos, photos, online shows and more in Full HD on your HDTV with great image, clarity and sound. In today's lifestyle of mobility and wireless, the GWAVR is the next step in connectivity for your wireless Audio/Video entertainment. Supports the latest Wi-Fi technology: • Wi-Fi Miracast - Also known as "Screen Mirroring" for Samsung devices* Streaming Screen Capture from Wi-Fi Miracast compatible device (such as smartphone / tablet / notebook) • Intel WiDi Streaming Screen Capture from Intel WiDi notebook • Works with non-Miracast Devices Using the Free App "iMediaShare Personal" you can stream your personal photos, videos, music and more wirelessly to your HDTV. -
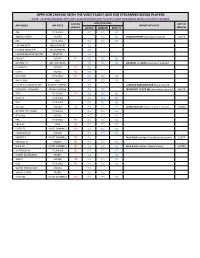
Apps for Casting and Streaming.Pdf
APPS FOR CASTING WITH THE VIZIO TABLET AND FOR STREAMING MEDIA PLAYERS NOTE: CASTING-ENABLED APPS MAY ALSO BE DOWNLOAD TO APPLICABLE STREAMING MEDIA PLAYERS IF DESIRED CASTING APPSTORE LINKS COST OF APP NAMES APP TYPES IMPORTANT NOTES ENABLED GOOGLE AMAZON ROKU TV SERVICES ABC TV SHOWS YES YES YES AMAZON VIDEO MOVIES YES YES AMAZON PRIME subscription required $99/YR CBS TV SHOWS YES YES YES CHROME BETA WEB BROWSER YES CHROME BROWSER WEB BROWSER YES CHROME REMOTE DESKTOP DESKTOP YES CRACKLE MOVIES YES YES YES YES DEFENSE TV MILITARY NEWS YES YES YES ANDROID and ROKU screensaver included FILMON TV MOVIES YES YES FLIPPS MOVIES YES YES FOX NOW TV SHOWS YES YES YES YES HAPPY KIDS KIDS YES YES YES LOGITECH HARMONY APP REMOTE CONTROL YES LOGITECH HARMONY HUB device required MICROSOFT ONEDRIVE CLOUD STORAGE YES YES MICROSOFT OFFICE 365 subscription required $69/YR MTV TV SHOWS YES YES YES YES NASA TV TV SHOWS YES YES YES NBC TV SHOWS YES YES YES NETFLIX MOVIES YES YES YES YES ULTRA-HD PLAN includes 4 device streams $12/MO OUTSIDE TELEVISION TV SHOWS YES YES YES OVGUIDE MOVIES YES YES YES PBS TV SHOWS YES YES YES YES PBS KIDS KIDS YES YES YES YES PLUTO TV MULTI-CHANNELS YES YES YES YES POPCORN FLIX MOVIES YES YES YES RABBIT TV MULTI-CHANNELS YES YES PLUS PLAN includes unlimited device streams $24/YR RED BULL TV SPORTS YES YES YES YES SLING TV MULTI-CHANNELS YES YES YES YES BLUE PLAN includes 3 device streams $25/MO SMITHSONIAN TV SHOWS YES YES YES YES SPORTS ILLUSTRATED SPORTS YES YES TUBITV MOVIES YES YES YES YES VH1 TV SHOWS YES YES YES YES WATCH MOVIES 2016 MOVIES YES YAHOO SPORTS SPORTS YES YES YOUTUBE MULTI-CHANNELS YES YES YES YES. -

Ios, Your OS, Everybody's OS: Vetting and Analyzing Network Services of Ios Applications
iOS, Your OS, Everybody’s OS: Vetting and Analyzing Network Services of iOS Applications Zhushou Tang, Shanghai Jiao Tong University and PWNZEN InfoTech Co., LTD; Ke Tang, Shanghai Jiao Tong University; Minhui Xue, The University of Adelaide; Yuan Tian, University of Virginia; Sen Chen, Nanyang Technological University; Muhammad Ikram, Macquarie University; Tielei Wang, PWNZEN InfoTech Co., LTD; Haojin Zhu, Shanghai Jiao Tong University https://www.usenix.org/conference/usenixsecurity20/presentation/tang This paper is included in the Proceedings of the 29th USENIX Security Symposium. August 12–14, 2020 978-1-939133-17-5 Open access to the Proceedings of the 29th USENIX Security Symposium is sponsored by USENIX. iOS, Your OS, Everybody’s OS: Vetting and Analyzing Network Services of iOS Applications Zhushou Tang1,6 Ke Tang1 Minhui Xue2 Yuan Tian3 Sen Chen4 Muhammad Ikram5 Tielei Wang6 Haojin Zhu1 1Shanghai Jiao Tong University 2The University of Adelaide 3University of Virginia 4Nanyang Technological University 5Macquarie University 6PWNZEN InfoTech Co., LTD Abstract Recent research evaluating the security of open port us- Smartphone applications that listen for network connections age in Android apps has demonstrated new attack avenues introduce significant security and privacy threats for users. that can exploit the vulnerability of network services and In this paper, we focus on vetting and analyzing the secu- access unauthorized sensitive data previously unthought rity of iOS apps’ network services. To this end, we develop of [22, 32, 55, 80]. Some works have also proposed vetting an efficient and scalable iOS app collection tool to down- methodologies to handle dynamic code loading [69], complex load 168,951 iOS apps in the wild. -

Download Movies on Mobile App Download Movies on Mobile App
download movies on mobile app Download movies on mobile app. Completing the CAPTCHA proves you are a human and gives you temporary access to the web property. What can I do to prevent this in the future? If you are on a personal connection, like at home, you can run an anti-virus scan on your device to make sure it is not infected with malware. If you are at an office or shared network, you can ask the network administrator to run a scan across the network looking for misconfigured or infected devices. Another way to prevent getting this page in the future is to use Privacy Pass. You may need to download version 2.0 now from the Chrome Web Store. Cloudflare Ray ID: 67a4af1e2b490d32 • Your IP : 188.246.226.140 • Performance & security by Cloudflare. Introducing the new Microsoft Office Mobile app. The new Office Mobile app combines Word, Excel, and PowerPoint with exclusive features to make it your go-to productivity app for phone, tablet—or both. Word, Excel, and PowerPoint in one app. View, edit, and share files without the need to switch between multiple apps. Uniquely mobile ways to make document creation easier. Transform pictures into editable Word and Excel files with the press of a button, and more. Quickly perform common mobile tasks with built-in Actions. Create and sign PDFs, use Sticky Notes, quickly transfer files between devices, and more. Get more productivity apps. How your mobile number or email address is used. Microsoft will use your phone number or email address only for this one-time transaction. -

Miracast Mirroring: Compatible With
MT20 The Matsunichi MT20 is your ultimate streaming media player. Share your mobile videos, photos, and music on a HDTV or HDMI-capable monitor in Full HD 1080p with your friends and family in a snap. Stream instantly over Wi-Fi to both your iOS and Android devices with the MeePlayer app, or through popular apps like YouTube and flipps! The MT20 also supports wireless display through Miracast. The MT20 easily connects audio/video through the HDMI dongle, is powered by USB, and can play media directly through an external USB storage device. Quickly share your media with friends at home, or take it on the go for work or play! • Easily share content from your mobile device to your big screen. • Beam free and premium content from apps like flipps, YouTube, Netflix, Hulu Plus, and more! Stream from Apps: • Mirror your Android 4.2 device to your big screen in real time with Miracast technology, incuding movies, games, presentations, web browsing, and more. • Quick and easy way to get your personal music blasting onto your home theater system. • Compatible with both iOS & Android devices. • Compact size and easy setup mean it will hide behind your TV like it’s not even there. Stream Local Content: Specifications Dimensions 3.4” x 1.1” x 0.5” CPU MediaTek® ARM11 DSP 1080p FHD Video Decoder, up to 80Mbps and 60 fps Flash Memory 256MB DRAM 256MB* Miracast Mirroring: Wi-Fi Wi-Fi (802.11 b/g/n) HDMI HDMI 1.4 (1080p) USB USB 2.0 Power Micro USB Power Indicator LED Supported File Types Photos: .jpg, .bmp, .png, .gif Audio: .wav, .mp3, .wma Compatible With: Video: .avi, .mkv, .flv, .wmv, .mp4, .mpg, .mpeg Accessories Micro USB Cable 3FT USB Power Adapter Remote Control Remote Control Receiver Quick Install Guide.