Bi - Annual Journal of Science and Humanities) Editor - in - Chief C.M
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

CORRIGENDUM TAMILNADU INDUSTRIAL DEVELOPMENT CORPORATION LIMITED Tender for Interior Fit out Renovation and Furnishing Works
CORRIGENDUM TAMILNADU INDUSTRIAL DEVELOPMENT CORPORATION LIMITED Tender for Interior Fit out Renovation and Furnishing Works inclusive of MEP Downstream Works to TIDCO Office, Third Floor, Egmore, Chennai Sl. Section/ As given in the Tender Document Amendment, to be read/included as no Clause Tender - Volume - I 1 Section -1 For and on behalf of Tamilnadu Industrial For and on behalf of Tamilnadu Industrial Development Corporation Development Corporation Limited (TIDCO), Limited (TIDCO), sealed tenders are invited under “Two Cover Tender sealed tenders are invited under “Two Cover System” for the following work from Class-I contractors registered Notice System” for the following work from Class-I, with any State/Central Government Department / Board / Quasi State level registered contractors having Government/ Government Undertaking having experience in similar experience in similar nature of works. nature of works. 2 Section-2 - Information about TIDCO: i. Tamil Nadu Industrial Development Corporation Limited (TIDCO) is a premier industrial development agency of the Government of Tamil Nadu, established in 1965. TIDCO endeavours to achieve a balanced and continual industrial growth by promoting medium and large industries in the State through Joint Ventures. TIDCO facilitates big industrial and infrastructure projects in Tamil Nadu involving large investments and huge employment potential. ii. TIDCO has promoted various joint venture companies in across manufacturing sectors such as Chemicals, Fertilizers, Pharmaceuticals, Textiles, Iron and Steel, Auto Components, Food & Agro, Floriculture, Engineering, Petroleum and Petrochemicals and infrastructure sectors such as IT/ITES Parks, Bio-Tech Parks, Special Economic Zones (SEZ), Road Development Projects and Agri Export Zones. iii. Important joint ventures of TIDCO are Titan Industries, TIDEL Park, Sl. -
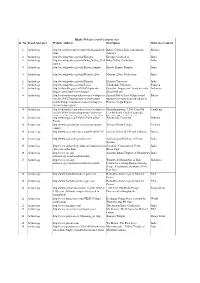
2.Hindu Websites Sorted Category Wise
Hindu Websites sorted Category wise Sl. No. Broad catergory Website Address Description Reference Country 1 Archaelogy http://aryaculture.tripod.com/vedicdharma/id10. India's Cultural Link with Ancient Mexico html America 2 Archaelogy http://en.wikipedia.org/wiki/Harappa Harappa Civilisation India 3 Archaelogy http://en.wikipedia.org/wiki/Indus_Valley_Civil Indus Valley Civilisation India ization 4 Archaelogy http://en.wikipedia.org/wiki/Kiradu_temples Kiradu Barmer Temples India 5 Archaelogy http://en.wikipedia.org/wiki/Mohenjo_Daro Mohenjo_Daro Civilisation India 6 Archaelogy http://en.wikipedia.org/wiki/Nalanda Nalanda University India 7 Archaelogy http://en.wikipedia.org/wiki/Taxila Takshashila University Pakistan 8 Archaelogy http://selians.blogspot.in/2010/01/ganesha- Ganesha, ‘lingga yoni’ found at newly Indonesia lingga-yoni-found-at-newly.html discovered site 9 Archaelogy http://vedicarcheologicaldiscoveries.wordpress.c Ancient Idol of Lord Vishnu found Russia om/2012/05/27/ancient-idol-of-lord-vishnu- during excavation in an old village in found-during-excavation-in-an-old-village-in- Russia’s Volga Region russias-volga-region/ 10 Archaelogy http://vedicarcheologicaldiscoveries.wordpress.c Mahendraparvata, 1,200-Year-Old Cambodia om/2013/06/15/mahendraparvata-1200-year- Lost Medieval City In Cambodia, old-lost-medieval-city-in-cambodia-unearthed- Unearthed By Archaeologists 11 Archaelogy http://wikimapia.org/7359843/Takshashila- Takshashila University Pakistan Taxila 12 Archaelogy http://www.agamahindu.com/vietnam-hindu- Vietnam -

Facts About Asia: India’S Thriving Technology Industry
Teaching Asia’s Giants: India Facts About Asia: India’s Thriving Technology Industry The Infy hallmark pyramid. It serves as the multimedia studio for Infosys’s headquarters in Bangalore. Source: Wikimedia Commons at https://tinyurl.com/y4orqfx4. Introduction North American readers of this journal, even if they are not especially tech savvy, are likely familiar with Silicon Valley, located in the San Francisco Bay area, and many of the companies like Apple and Google that make the region their home. Fewer are likely aware of India’s own “Silicon Valley” and the various Indian private compa- nies and startups that help to make the IT sector one of the more faster growing sectors of the economy and cre- ate the prospect of India becoming a world leader in technology companies. According to the 2020 Global Innovation Index, an annual study of the most innovative countries across a series of industries published by World Intellectual Property Organization (WIPO), Cornell University and IN- SEAD, a top international private business school, India ranks as the world’s top exporter of information tech- nology (IT) and eighth in the number of science and engineering graduates. The IT industry is a highly significant part of the Indian economy today with the sector contributing 7.7% of India’s total GDP by 2017, a most impressive increase from 1998 when IT accounted for only 1.2% of the nation’s GDP. IT revenues in 2019 totaled US $180 billion. As of 2020, India’s IT workforce accounts for 4.36 million employees and the United States accounts for two-thirds of India’s IT services exports. -
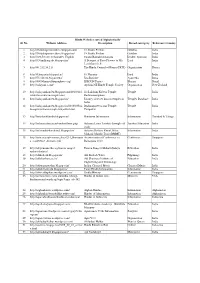
1.Hindu Websites Sorted Alphabetically
Hindu Websites sorted Alphabetically Sl. No. Website Address Description Broad catergory Reference Country 1 http://18shaktipeetasofdevi.blogspot.com/ 18 Shakti Peethas Goddess India 2 http://18shaktipeetasofdevi.blogspot.in/ 18 Shakti Peethas Goddess India 3 http://199.59.148.11/Gurudev_English Swami Ramakrishnanada Leader- Spiritual India 4 http://330milliongods.blogspot.in/ A Bouquet of Rose Flowers to My Lord India Lord Ganesh Ji 5 http://41.212.34.21/ The Hindu Council of Kenya (HCK) Organisation Kenya 6 http://63nayanar.blogspot.in/ 63 Nayanar Lord India 7 http://75.126.84.8/ayurveda/ Jiva Institute Ayurveda India 8 http://8000drumsoftheprophecy.org/ ISKCON Payers Bhajan Brazil 9 http://aalayam.co.nz/ Ayalam NZ Hindu Temple Society Organisation New Zealand 10 http://aalayamkanden.blogspot.com/2010/11/s Sri Lakshmi Kubera Temple, Temple India ri-lakshmi-kubera-temple.html Rathinamangalam 11 http://aalayamkanden.blogspot.in/ Journey of lesser known temples in Temples Database India India 12 http://aalayamkanden.blogspot.in/2010/10/bra Brahmapureeswarar Temple, Temple India hmapureeswarar-temple-tirupattur.html Tirupattur 13 http://accidentalhindu.blogspot.in/ Hinduism Information Information Trinidad & Tobago 14 http://acharya.iitm.ac.in/sanskrit/tutor.php Acharya Learn Sanskrit through self Sanskrit Education India study 15 http://acharyakishorekunal.blogspot.in/ Acharya Kishore Kunal, Bihar Information India Mahavir Mandir Trust (BMMT) 16 http://acm.org.sg/resource_docs/214_Ramayan An international Conference on Conference Singapore -

Emerging Investment Hotspots
Emerging investment hotspots Mining opportunities from the Complex Real Estate Terrain of India 2 On Point • Emerging investment hotspots ndia has its own unique and integral complexities and business is not an exception to it. Corporations strive for increased efficiency and productivity amidst these complexities. Real estate is an integral ingredient in the formation and growth of all Ibusinesses and steadily maturing into a big business itself. As such the performance of real estate sector depends largely on the performance of the economy and the businesses in specific. Decision makers have been in a state of indeterminacy given the fabric and structure of how the country keeps oscillating between promises & optimism and persistent challenges & policy inertia. The recently approved Real Estate Regulatory Bill is an important initiative by the government to address the concerns of real estate sector. Land Acquisition and Rehabilitation and Resettlement Bill that is yet to be approved is also expected to be another step towards regulating the real estate sector. However, information asymmetries and laxity in disclosure norms need to be addressed for the real estate sector to achieve optimum potential in development and investments. While the real estate sector is moving ahead slowly and steadily, certain inaction is resulting in to stagnation from this dense and multifaceted much to be attained growth. At a juncture like this, there is a need for a focused push in the right direction for the real estate industry to remain buoyant going forward. It is therefore essential for all stakeholders to equip themselves with a deeper understanding of not only the real estate sector but also the businesses they serve. -
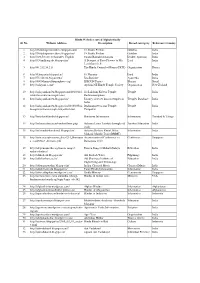
Hindu Websites Sorted Alphabetically Sl
Hindu Websites sorted Alphabetically Sl. No. Website Address Description Broad catergory Reference Country 1 http://18shaktipeetasofdevi.blogspot.com/ 18 Shakti Peethas Goddess India 2 http://18shaktipeetasofdevi.blogspot.in/ 18 Shakti Peethas Goddess India 3 http://199.59.148.11/Gurudev_English Swami Ramakrishnanada Leader- Spiritual India 4 http://330milliongods.blogspot.in/ A Bouquet of Rose Flowers to My Lord India Lord Ganesh Ji 5 http://41.212.34.21/ The Hindu Council of Kenya (HCK) Organisation Kenya 6 http://63nayanar.blogspot.in/ 63 Nayanar Lord India 7 http://75.126.84.8/ayurveda/ Jiva Institute Ayurveda India 8 http://8000drumsoftheprophecy.org/ ISKCON Payers Bhajan Brazil 9 http://aalayam.co.nz/ Ayalam NZ Hindu Temple Society Organisation New Zealand 10 http://aalayamkanden.blogspot.com/2010/11/s Sri Lakshmi Kubera Temple, Temple India ri-lakshmi-kubera-temple.html Rathinamangalam 11 http://aalayamkanden.blogspot.in/ Journey of lesser known temples in Temples Database India India 12 http://aalayamkanden.blogspot.in/2010/10/bra Brahmapureeswarar Temple, Temple India hmapureeswarar-temple-tirupattur.html Tirupattur 13 http://accidentalhindu.blogspot.in/ Hinduism Information Information Trinidad & Tobago 14 http://acharya.iitm.ac.in/sanskrit/tutor.php Acharya Learn Sanskrit through self Sanskrit Education India study 15 http://acharyakishorekunal.blogspot.in/ Acharya Kishore Kunal, Bihar Information India Mahavir Mandir Trust (BMMT) 16 http://acm.org.sg/resource_docs/214_Ramayan An international Conference on Conference Singapore -
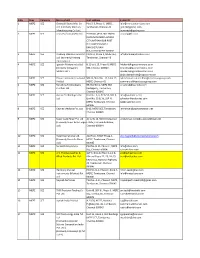
List of EOU SEZ Units and Developers
S.No. Zone Category Name of unit Unit address E-mail ID 1 MEPZ SEZ Godrej & Boyce Mfg. Co. Plot D-3, Phase-II, MEPZ, [email protected] Ltd. (Formerly Mercury Tambaram, Chennai-45 [email protected] Manufacturing Co. Ltd.) [email protected] 2 MEPZ SEZ Linea Fashions (I) Pvt Ltd PLOT NO.AP10 2ND CROSS [email protected] ROAD MAHINDRA WORLD CITY,NATHAM SUB POST OFFICECHENGALPET KANCHEPURAM DIS,,CHENGALPET-603002 3 MEPZ SEZ Pradeep Stainless India Pvt. Plot C-3, Phase II, MEPZ-SEZ, [email protected] Ltd. (formerly Pradeep Tambaram, Chennai-45 International.) 4 MEPZ SEZ Igarashi Motors India Ltd. B 12 to B 15, Phase II, MEPZ- [email protected] (formerly CG Igarshi SEZ, Chennai-600045 [email protected] Motors Ltd.) [email protected] [email protected] 5 MEPZ SEZ Classic Linens International SDF III, Shed No. 13, 14 & 17, [email protected] Pvt Ltd MEPZ, Chennai-45 [email protected] 6 MEPZ SEZ Switching Technologies B9, B10 & C1, MEPZ-SEZ, [email protected] Gunther Ltd. Kadappery, Tambaram, Chennai-600045 7 MEPZ SEZ Avalon Technologies Pvt. Unit No. 5, 6, 52 & 53, SDF II, [email protected] Ltd. Unit No. 15 & 16, SDF III, [email protected] MEPZ, Tambaram, Chennai - [email protected] 600045 8 MEPZ SEZ Cephas Medicals Pvt. Ltd. B-13, MEPZ-SEZ, Tambaram, [email protected] Chennai-600045 9 MEPZ SEZ Super Auto Forge Pvt. Ltd. AC 12 & 13, SIDCO Industrial [email protected] (Formerly Super Auto Forge Estate, Thirumudivakkam, Ltd) Chennai-600044 10 MEPZ SEZ Tata International Ltd. -
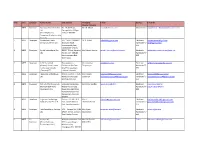
List of EOU SEZ Units and Developers
S.No. Zone Category Name of unit Unit address Managing E-mail Services E-mail ID Director/Director 1 MEPZ Developer Gateway Office Parks Pvt No. 16, GST Road, Mr. M. Murali [email protected] Multi Product [email protected] Ltd Perungalathur Village (FormerlyShriram chennai- 600 063 Properties & Infrastructure Pvt. Ltd.) 2 MEPZ Developer Coimbatore Hitech 365, " KGISL CAPMUS", Dr. B. Ashok [email protected] Electronic [email protected] Infrastructure Pvt. Ltd. thudiyalur Road, Hardware/IT/ [email protected] Saravampatty Post, IEES Coimbatore- 641 035 3 MEPZ Developer Syntel International Pvt. SIPCOT IT Park, Navalur ( Mr. Rakesh Khanna [email protected] Electronic [email protected] Ltd. P0) Sirv seri - 603103 Hardware/IT/ Kancheepuram Dsit. IEES Tamil Nadu 4 MEPZ Developer IG3 Infra Limited Thoraipakkam - Mr. Unnamali [email protected] Electronic [email protected] (formerly Indian Green Pallavaram 200 Feet Thiagarajan Hardware/IT/ Grid Group Limited) Road Thoraipakkam, IEES (Formerly ETL Chennai - 600 096 Infrastructrue Services 5 MEPZ Developer Hexaware Technologies Plot # H5 SIPCOT IT Park Mr. K. Baala [email protected] Electronic [email protected] Ltd. Navalur Post Siruseri Sundaram [email protected] Hardware/IT/ [email protected] Kanchipuram Dist. IEES 6 MEPZ Developer DLF Info City Chennai Ltd. 1/124, Shivaji Garden, Mr. Sriram Khattar [email protected] Electronic [email protected] (Formerly DLF Home Mount Poonamalee Hardware/IT/ [email protected] Developers Ltd.) Road, Moonlight Stop, IEES Nandam Pakkam Post Ramapuram, Chennai- 600089 7 MEPZ Developer Cognizant Technology Plot no.: H4, SIPCOT IT Mr. R. [email protected] Electronic [email protected] Solutions India Pvt. -

Equity Research
Equity Research INDIA March 5, 2019 BSE Sensex: 36443 Real Estate ICICI Securities Limited is the author and distributor of this report CRE: #10yearchallenge – Faster, higher, stronger While India’s Residential Real Estate (RRE) market has seen a slowdown over Sector update CY14-18 compared to a stellar run over CY09-13, the Commercial Real Estate (CRE) office market has seen contrasting fortunes with a painful CY09-13 period being Real Estate followed by a strong recovery and consolidation over CY14-18. The CY14-18 period has seen falling vacancy levels, rental appreciation and consolidation within the space with just a handful of 8-10 large pan-India office developers dominating the DLF market. At the same time, the office space has seen healthy inflow of institutional (BUY, TP Rs280) money from foreign investors (private market deals) to these developers’ portfolios Oberoi Realty to add incremental space. As we head into CY19, we continue to retain our bullish (BUY, TP Rs564) stance on office asset developers and reiterate our BUY ratings on DLF, Oberoi Realty, Prestige Estates and Brigade Enterprises. A possible listing of India’s first Prestige Estates Real Estate Investment Trust (REIT) by Embassy Office Parks in H1CY19 may (BUY, TP Rs301) provide clarity on the cumulative yields that Indian REITs may offer as a mix of The Phoenix Mills existing rental income and capital appreciation. (BUY, TP Rs772) Cycle remains favourable for office sector: The India office market continues to see Brigade Enterprises low vacancy levels and limited supply in the preferred micro-markets across India’s tier (BUY, TP Rs304) I cities. -

Tata Realty and Infrastructure Limited to Develop a State-Of-Art Ramanujan IT City in Chennai
Tata Realty and Infrastructure Limited to develop a State-of-art Ramanujan IT City in Chennai • The Rs. 3,500 Crore project is promoted by TRIL Infopark Limited, a JV between TRIL, TIDCO and IHCL • It is a tribute to Chennai’s legendary mathematician Srinivasa Ramanujan • The premium residential complex `Cambridge Greens’ is located at Ramanujan IT City Chennai, ----- December 2009: Tata Realty And Infrastructure Limited (TRIL), a 100% subsidiary of Tata Sons Ltd, one of India’s largest and most respected conglomerate, today announced their plans to develop ‘Ramanujan IT City’ , one of the state-of art commercial and residential projects located at Old Mahabalipuram Road (OMR) in Taramani, Chennai. This project will also envisage the development of a premium residential community called ‘Cambridge Greens’ which will be ready for occupancy by mid 2011. Ramanujan IT City is an IT Special Economic Zone (SEZ) to be built on 26 acres land at Taramani. The Rs. 3,500 Crore project is promoted by TRIL Infopark Limited which is a Joint Venture between Tata Realty & Infrastructure Limited, TIDCO & Indian Hotels Company Limited (IHCL). The hi-tech integrated development would consist of a duly notified IT/ITES along with Residential Apartments, a premium Retail Mall & Entertainment, serviced apartments and an International Convention Center. Ramanujan IT City is a tribute by the Tata Group to the legendary mathematician Srinivasa Ramanujan. `Cambridge Greens’, comprising 150 super luxury apartments and spread over three lakh sq feet, will be a perfect blend of design and functionality. The site is strategically located and will offer its residents a home with state of the art facilities that characterize an opulent lifestyle. -

Minutes of the 62Nd Boa SEZ Meeting Held on 24Th July, 2014 Size
Minutes of the 62nd meeting of the Board of Approval for SEZ held on 24th July 2014 to consider proposals for setting up Special Economic Zones and other miscellaneous proposals The Sixty Second (62nd) meeting of the Board of Approval (BoA) for Special Economic Zones (SEZ) was held on 24th July, 2014 under the Chairmanship of Shri Rajeev Kher, Secretary, Department of Commerce, at 10.30 A.M. in Room No. 47, Udyog Bhawan, New Delhi, to consider proposals in respect of notified/approved SEZs. The list of participants is annexed (Annexure-1). 2. Addressing the members of Board of Approval, the Chairman informed that so far 565 formal approvals have been granted for setting up of SEZs out of which 388 SEZs stand notified. He further informed that as on 31.03.2014, over Rs. 2,96,663 crores have been invested in the SEZs and employment to 12,83,309 persons is being provided in the SEZs. During the financial year 2013-14, total exports to the tune of Rs. 4,94,077 crores were made from the SEZs, registering a growth of about 4% over the exports for the year 2012-13. Item No. 62.1: Requests for extension of validity of formal approvals BoA in its meeting held on 14th September, 2012, examining similar cases observed as under: - “The Board advised the Development Commissioners to recommend the requests for extension of formal approval beyond 5th year and onwards only after satisfying that the developer has taken sufficient steps towards operationalisation of the project and further extension is based on justifiable reasons. -

Requests for Extension of Validity of Formal Approvals Boa in Its Meeting Held on 14
Agenda for the 62 nd meeting of the Board of Approval (BoA) for SEZ to be held on 24 th July, 2014, in Room No. 47, Udyog Bhawan, New Delhi Item No. 62.1: Requests for extension of validity of formal approvals BoA in its meeting held on 14 th September, 2012, examining similar cases observed as under: - “The Board advised the Development Commissioners to recommend the requests for extension of formal approval beyond 5 th year and onwards only after satisfying that the developer has taken sufficient steps towards operationalisation of the project and further extension is based on justifiable reasons. Board also observed that extensions may not be granted as a matter of routine unless some progress has been made on ground by the developers. The Board, therefore, after deliberations, extended the validity of the formal approval to the requests for extensions beyond fifth years for a period of one year and those beyond sixth year for a period of 6 months from the date of expiry of last extension”. (i) Request of M/s. DLF Info Park (Pune) Ltd. for further extension of the validity period of formal approval, granted for setting up of sector specific SEZ for IT/ITES at Rajiv Gandhi Infotech Park, Phase II, Pune, Maharashtra, beyond 26th June, 2014 The developer was granted formal approval for setting up the above mentioned SEZ on 27th June, 2008. The SEZ is yet to be notified. The developer has been granted three extensions of the formal approval, the validity of which was up to 26th June, 2014.