The End of Ownership
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Christopher Soghoian Student Fellow Berkman Center for Internet & Society Harvard University 23 Everett Street, Second Floor Cambridge MA 02138
Comment of: Christopher Soghoian Student Fellow Berkman Center for Internet & Society Harvard University 23 Everett Street, Second Floor Cambridge MA 02138 Represented by: Phil Malone Director, Cyberlaw Clinic Arjun Mehra Clinical Student, Cyberlaw Clinic Harvard Law School Berkman Center for Internet & Society 23 Everett Street, Second Floor Cambridge MA 02138 Office of the General Counsel U.S. Copyright Office James Madison Memorial Building, Room LM-401 101 Independence Avenue, SE. Washington, DC 20559-6000 December 2, 2008 Re: RM 2008-8 -- Exemptions to Prohibition on Circumvention of Copyright Protection Systems for Defunct DRM and Copy Protection-Based Stores I. PROPOSED CLASS OF WORKS We respectfully request an exemption to DMCA §1201(a)(1)(A) for lawfully purchased sound recordings, audiovisual works, and software programs distributed commercially in digital format by online music and media stores and protected by technological measures that depend on the continued availability of authenticating servers, when such authenticating servers cease functioning because the store fails or for other reasons. We also request a separate exemption for the same class of works even prior to the failure of the servers for technologists and researchers studying and documenting how the authenticating servers that effectuate the technological measures function. The technological measures at issue include digital rights management (DRM) technologies and copy protection mechanisms encoded into purchased music, videos, and software, which are sold with a set of permissions and require authentication with remote servers in order to allow users to fully exercise those purchased rights, including the ability to access the works on other devices, or in some cases, to allow continued access to the works on the same device. -

Basics of OS Upgrades
Basics of OS Upgrades Everything you need to prepare for macOS Big Sur and iOS 14 Apple OS upgrades are coming. Are you ready? Exciting new versions of macOS (for Mac), iPadOS (for iPad) and iOS (for iPhone) are heading to a device near you. Your job is simple. Get these features into the hands of users, all without disrupting workflows or slowing productivity. As most organizations know, this can often be easier said than done, especially when factoring in the speed at which Apple users like to upgrade. Now for the good news. At Jamf, we’ve been doing this for more than 17 years, and are here to provide step-by-step guidance for successful Apple upgrades — regardless if it is your first, fifth or 17th OS season. Why an Contrary to other ecosystems, a variety of devices and OS platforms with major new versions of Apple’s a single management solution. Without the Apple operating systems are released complications and cost of licensing, Apple’s annually. A combination of the user-initiated upgrades are easy for end users upgrade is simple upgrade path and $0 to carry out autonomously. This is one of the cost help drive industry-leading reasons Apple’s operating systems have the highest adoption rate of any ecosystem. different adoption rates for consumers. End users are so excited to access the This trend is further accelerated by Apple’s new features; yet, you’re responsible for vertical integration of hardware and software: maintaining security controls and an accurate any new Mac, iPad or iPhone will always systems inventory at all times. -

Wing Commander II, Your Goal Is to Defeat the Kilrathi Enemy
Wing Commander TM II USER MANUAL PLAY HUNDREDS OF THE GREATEST GAMES EVER MADE, VISIT WWW.GAMETAP.COM AND GET YOUR FREE TRIAL NOW! GameTap is pleased to oer an online library of original game manuals. We have made these manuals available to create a more complete gaming experience -- and because some of them are pretty entertaining. Be aware that the representations, warranties, and guarantees (including replacement options) made in these manuals are no longer valid, and that GameTap and the original publisher are not responsible for honoring them. Control information for a PC title will, in most cases, accurately reect the game’s controls within GameTap. Please note that game controller instructions for console games won’t be correct. Feel free to ignore any installation instructions -- GameTap handles all the complex stu for you. Finally, please do not call the phone numbers that occasionally appear in the manuals. We're not sure anyone will pick up. If you do have questions about games within the GameTap service, please contact Customer Support at gametap.com. wc2_1 Page 1 of 2 C O N T E N T S PLAY GUIDE .....................................................2 Alternate Camera Views ......................12 The Story So Far….......................................2 Improved Target Starting the Game.........................................2 Tracking System .............................12 Transferring Characters ............................3 Jumping Out.......................................12 Creating a New Character ........................3 -

Illegal File Sharing
ILLEGAL FILE SHARING The sharing of copyright materials such as MUSIC or MOVIES either through P2P (peer-to-peer) file sharing or other means WITHOUT the permission of the copyright owner is ILLEGAL and can have very serious legal repercussions. Those found GUILTY of violating copyrights in this way have been fined ENORMOUS sums of money. Accordingly, the unauthorized distribution of copyrighted materials is PROHIBITED at Bellarmine University. The list of sites below is provided by Educause and some of the sites listed provide some or all content at no charge; they are funded by advertising or represent artists who want their material distributed for free, or for other reasons. Remember that just because content is free doesn't mean it's illegal. On the other hand, you may find websites offering to sell content which are not on the list below. Just because content is not free doesn't mean it's legal. Legal Alternatives for Downloading • ABC.com TV Shows • [adult swim] Video • Amazon MP3 Downloads • Amazon Instant Video • AOL Music • ARTISTdirect Network • AudioCandy • Audio Lunchbox • BearShare • Best Buy • BET Music • BET Shows • Blackberry World • Blip.fm • Blockbuster on Demand • Bravo TV • Buy.com • Cartoon Network Video • Zap2it • Catsmusic • CBS Video • CD Baby • Christian MP Free • CinemaNow • Clicker (formerly Modern Feed) • Comedy Central Video • Crackle • Criterion Online • The CW Video • Dimple Records • DirecTV Watch Online • Disney Videos • Dish Online • Download Fundraiser • DramaFever • The Electric Fetus • eMusic.com -

Apple TV Overhauled for Games, Shows, Shopping 9 September 2015
Apple TV overhauled for games, shows, shopping 9 September 2015 focused service Zillow, according to Apple executive Eddie Cue. Siri virtual assistant software built in Apple TV allowed for natural language searches for shows, say by asking for something funny or a certain actor by name. The new Apple TV will launch in late October at a starting price of $149. Apple TV has lagged rivals with similar devices. According to the research firm Parks Associates, Roku leads the US market with a 37 percent market share, to 19 percent for Google Chromecast and 17 Apple Senior Vice President of Internet Software and percent for Apple TV. Amazon's Fire TV devices Services Eddy Cue speaks about the new Apple TV on have 14 percent. September 9, 2015 in San Francisco, California © 2015 AFP Apple on Wednesday unveiled a new streaming television device with voice search, touchscreen remote control and an app store in a challenge to Google, Amazon, and video game console titans. Apple TV was overhauled as people increasingly stream films and television shows on-demand online and turn to mobile applications for entertainment. "Our vision for TV is simple, and perhaps a little provocative," Apple chief executive Tim Cook said at a media event in San Francisco. "We believe the future of television is apps." Apple released a software kit for outside developers, and showed off early versions of Apple TV applications already being crafted by show streaming services Netflix, Hulu, and HBO. Game makers are already working on applications, as are home-sharing service Airbnb and real estate- 1 / 2 APA citation: Apple TV overhauled for games, shows, shopping (2015, September 9) retrieved 26 September 2021 from https://phys.org/news/2015-09-apple-tv-overhauled-games.html This document is subject to copyright. -

Failing Gloriously and Other Essays
University of North Dakota UND Scholarly Commons The Digital Press at the University of North Digital Press Books Dakota 2019 Failing Gloriously and Other Essays Shawn Graham Follow this and additional works at: https://commons.und.edu/press-books Recommended Citation Graham, Shawn, "Failing Gloriously and Other Essays" (2019). Digital Press Books. 15. https://commons.und.edu/press-books/15 This Book is brought to you for free and open access by the The Digital Press at the University of North Dakota at UND Scholarly Commons. It has been accepted for inclusion in Digital Press Books by an authorized administrator of UND Scholarly Commons. For more information, please contact [email protected]. FAILIGN FAIILNG FAILING GLORIOUSLY FLAIING FALIGIN >And other essays > > > > > > > > >Shawn Graham Failing Gloriously and Other Essays by Shawn Graham with an introduction by Eric C. Kansa and an afterword by Neha Gupta The Digital Press at the University of North Dakota Grand Forks, ND 2019. The Digital Press at the University of North Dakota Unless otherwise indicated, all contributions to this volume appear under a Creative Commons Attribution 4.0 License: https://creativecommons.org/licenses/by/4.0/legalcode Library of Congress Control Number: 2019953926 ISBN-13: 978-1-7328410-6-2 (ebook) ISBN-13: 978-1-7328410-8-6 (Paperback) Failing Gloriously and Other Essays This volume is dedicated firstly to the students in the welding program at Pontiac High in Shawville, Quebec, and secondly to those who gave me the benefit of the doubt when -
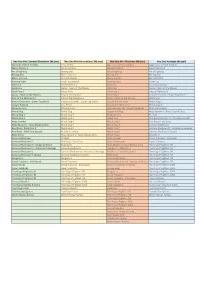
Comparatif Line up Neogeo Mini.Xlsx
Neo Geo Mini Samurai Showdown (40 jeux) Neo Geo Mini International (40 jeux) Neo Geo Mini Christmas (48 jeux) Neo Geo Asiatique (40 jeux) Agressor of Dark Combat 3 Count Bout Agressors of Dark Combat Aggressors of Dark Kombat Alpha Mission 2 Art of Fighting Alpha Mission 2 Alpha Mission II Art of Fighting Blazing Star Art of Fighting Art of Fighting Blazing Star Blue’s Journey Blazing Star Blazing Star Blue’s Journey Crossed Swords Blue’s Journey Burning Fight Burning Fight Fatal Fury Special Burning Fight Cyber-Lip Cyber Lip Foot Ball Frenzy Cyber Lip Fatal Fury Special Fatal Fury Garou : Mark of the Wolves Fatal Fury Garou : Mark of the Wolves Fatal Fury 2 Ghost Pilots Fatal Fury 2 King of Monsters 2 Garou : Mark of the Wolves King of the Monsters Fatal Fury 3 Kizuna Encounter : Super Tag Battle King of the Monsters 2 King of the Monsters 2 Garou : Mark of the Wolves Metal Slug Kizuna Encounter : Super Tag Battle Kizuna Encounter : Super Tag Battle King of the Monsters Metal Slug 2 League Bowling Last Resort King of the Monsters 2 Metal Slug 3 Magician Lord Magician Lord Kizuna Encounter : Super Tag Battle Ninja Commando Metal Slug Metal Slug League Bowling Ninja Master's : Haou Ninpou Chou Metal Slug 2 Metal Slug 2 Magician Lord Puzzled Metal Slug 3 Metal Slug 3 Metal Slug Real Bout Fatal Fury 2 : The Newcomers Ninja Combat Metal Slug 4 Metal Slug 2 Real Bout : Fatal Fury Ninja Master's : Haou Ninpou Chou Metal Slug 5 Metal Slug 3 Samurai Shodown II Real Bout : Fatal Fury 2 Metal Slug X Metal Slug 4 Samurai Shodown IV : Amakusa’s Revenge -

161 in 1 Neogeo Multigame Cartridge
PCBs : 161 in 1 NeoGeo Multigame Cartridge 161 in 1 NeoGeo Multigame Cartridge Rating: Not Rated Yet Price: Sales price: $99.95 Discount: Ask a question about this product This amazing cart combines 161 of the best Neo Geo games onto a single Neo Geo cartridge. The cartridge uses a built-in OSD (On Screen Display) to first graphically navigate to the game you wish to play. Once finished playing, simply hold down Player 1 START button for 5 seconds to immediately return to the OSD game selection screen again. Description Game List: 1 SNK VS CAPCOM + 2 SNK VS CAPCOM RMX 3 SVC SUPER PLUS 4 KOF 94 5 KOF 94 + 6 KOF 95 7 KOF 95 + 8 KOF 96 9 KOF 96 + 10 KOF 96 EVO 11 KOF 97 12 KOF 97 2003 13 KOF 97 REMIX 14 KOF 97 PLUS 15 KING OF GLADIATOR 16 KOG PLUS 17 KOF 98 18 KOF 98 + 19 KOF 98 ULTIMATE 20 KOF 98 OROCHI 21 KOF 99 22 KOF 99 + 23 KOF 99 CN 24 KOF 2001 25 KOF 2001 PLUS 26 C.T.H.D 27 C.T.H.D SUPER PLUS 28 KOF 2002 29 KOF 2002 MAGIC 30 KOF 2002 MAGIC 2 31 KOF 2002 CN 32 KOF 2002 OROCHI 33 KOF 2002 LUAN 34 KOF 2002 SUPER 35 KOF 2002 SUPER 2 36 KOF 2003 37 KOF 2004 SE PLUS 38 KOF 2004 SE 39 KOF 2004 SMP 40 KOF 10TH 41 KOF 05 UNIQUE 42 KOF 05 UNIQUE 2 43 KOF 10TH EXTRA + 44 RAGE OF DRAGONS 45 RAGE OF DRAGONS + 46 STRIKERS 1945 + 47 STRIKERS 1945 + + 48 AERO FIGHTERS 2 49 AERO FIGHTERS 3 50 METAL SLUG 51 METAL SLUG + 52 METAL SLUG 2 53 METAL SLUG 2 + 54 METAL SLUG 3 55 METAL SLUG 3 + 56 METAL SLUG 4 57 METAL SLUG 4 + 58 METAL SLUG X 59 METAL SLUG X + 60 METAL SLUG 6 61 METAL SLUG 6 + 62 SUPER SIDEKICKS 2 63 SUPER SIDEKICKS 3 64 ULTIMATE 11 65 NEO-GEO -

IFPI Digital Music Report 2010 Music How, When, Where You Want It Contents
IFPI Digital Music Report 2010 Music how, when, where you want it Contents 3. Introduction 4. Executive Summary: Music – Pathfinder In The Creative Industries’ Revolution 8. The Diversification Of Business Models 10. Digital Music Sales Around The World 12. In Profile: Pioneers Of Digital Music 18. Competing In A Rigged Market – The Problem Of Illegal File-Sharing 20. ‘Climate Change’ For All Creative Industries 24. Graduated Response – A Proportionate, Preventative Solution 28. The World Of Legal Music Services 30. Consumer Education – Lessons Learned Music How, When, Where You Want It – But Not Without Addressing Piracy By John Kennedy, Chairman & Chief Executive, IFPI This is the seventh IFPI Digital Music in new artists, we have to tackle mass legislation to curb illegal file-sharing. Report. If you compare it to the first piracy. Second, we are progressing towards Another clear change is within the music report published in 2004, you can an effective response. The progress is sector itself. It was, until recently, rare see a transformation in a business agonisingly slow for an industry which does for artists to engage in a public debate which has worked with the advance not have a lot of time to play with – but it is about piracy or admit it damages them. of technology, listened to the consumer progress nonetheless. In September 2009, the mood changed. and responded by licensing its music Lily Allen spoke out about the impact of in new formats and channels. On page 20 of the Report, Stephen illegal file-sharing on young artists’ careers. Garrett, head of the production company When she was attacked by an abusive In 2009 globally, for the first time, more Kudos, refers to a “climate change” in online mob, others came to her support. -

A Walled Garden Turned Into a Rain Forest
A Walled Garden Turned Into a Rain Forest Pelle Snickars More than ten months after the iPhone was introduced, Lev Grossman in Time Magazine, reflected upon the most valuable invention of 2007. At first he could not make up his mind. Admittedly, he argued, there had been a lot written about the iPhone —and if truth be told, a massive amount of articles, extensive media coverage, hype, “and a lot of guff too.” Grossman hesitated: he confessed that he could not type on the iPhone; it was too slow, too expensive, and even too big. “It doesn’t support my work e- mail. It’s locked to AT&T. Steve Jobs secretly hates puppies. And—all together now— we’re sick of hearing about it!” Yet, when Grossman had finished with his litany of complains, the iPhone was nevertheless in his opinion, “the best thing invented this year.” He gave five reasons why this was the case. First of all, the iPhone had made design important for smartphones. At a time when most tech companies did not treat form seriously at all, Apple had made style a trademark of their seminal product. Of course, Apple had always knew that good design was as important as good technology, and the iPhone was therefore no exception. Still, it was something of a stylistic epitome, and to Grossman even “pretty”. Another of his reasons had to do with touch. Apple didn’t invent the touchscreen, but according to Grossman the company engineers had finally understood what to do with it. In short, Apple’s engineers used the touchscreen to sort of innovate past the GUI, which Apple once pioneered with the Mac, to create “a whole new kind of interface, a tactile one that gives users the illusion of actually physically manipulating data with their hands.” Other reasons, in Grossman view, why the iPhone was the most valuable invention of 2007, was its benefit to the mobile market in general. -

Cloud Methodologies for a Seamless Integrated Chatbot
Published by : International Journal of Engineering Research & Technology (IJERT) http://www.ijert.org ISSN: 2278-0181 Vol. 9 Issue 08, August-2020 Cloud Methodologies for A Seamless Integrated Chatbot Sharan Kumar Paratala Rajagopal IEEE Member Senior Manager, Capgemini America, Inc. Dallas, Texas, USA Abstract—This research paper provides details of connecting C. Seamless AWS integrations Amazon connect to Amazon pinpoint to send SMS and also Amazon Lex provides built-in integration with AWS provides some insights on how it can be integrated with social Lambda and Amazon CloudWatch and you can easily platforms such as Facebook messaging and WhatsApp. Amazon integrate with many other services on the AWS platform Lex can be leveraged as standalone bot on the website or can be including Amazon Cognito and Amazon DynamoDB. You triggered from Amazon connect for Intelligent voice responses. can take advantage of the power of the AWS platform for Keywords—Amazon Lex, Amazon Connect, Amazon Pinpoint, security, monitoring, user authentication, business logic, WhatsApp, Facebook Messaging. storage and mobile app development. I. INTRODUCTION D. Cost effective Amazon Lex [1] is a service for building conversational With Amazon Lex, there are no upfront costs or minimum interfaces into any application using voice and text. Amazon fees. You are only charged for the text or speech requests that Lex provides the advanced deep learning functionalities of are made. Amazon Lex’ pay-as-you-go pricing and low cost automatic speech recognition (ASR) for converting speech to per request makes it a cost-effective way to build text, and natural language understanding (NLU) to recognize conversational interfaces anywhere. -

Online Platforms and Market Power Part 6: Examining the Dominance of Amazon, Apple, Facebook, and Google Questions for the Recor
Online Platforms and Market Power Part 6: Examining the Dominance of Amazon, Apple, Facebook, and Google Questions for the Record from the Honorable David N. Cicilline, Chairman, Subcommittee on Antitrust, Commercial and Administrative Law of the Committee on the Judiciary Questions for Mr. Tim Cook, CEO, Apple, Inc. 1. You testified that Apple’s apps “go through the same rules” that third-party apps are required to follow. The App Store Guidelines (“Guidelines”) are designed to ensure that the App Store remains a safe and trusted place for consumers to discover and download software for their Apple devices. The Guidelines apply to any app, Apple or third-party, that is available on the App Store in the first instance. a. How many Apple apps are pre-loaded on current iPhone models? The first iPhone included 13 integrated Apple apps. There were no third-party apps available for that iPhone. Apple’s subsequent decision to open the iPhone to third-party app development unleashed a wave of innovation and competition. Thirteen years later, there are more than 1.8 million third-party apps available through the App Store and only about 40 Apple apps integrated into the current iPhone models. Apple’s focus has always been to deliver a great consumer experience out of the box. That is why the iPhone comes with Apple apps like Phone, Notes, Settings, Files, Clock, Tips, Measure, and Reminders to provide basic functionality. In addition, apps like FaceTime, iMessage, Apple Music, TV, and others help differentiate the iPhone in a competitive smartphone market. The few apps that Apple has integrated into the iPhone are a drop in the bucket of the overall app ecosystem.