Mark Rogers Tuttle
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Dagrep-V007-I011-Complete.Pdf
Volume 7, Issue 11, November 2017 New Challenges in Parallelism (Dagstuhl Seminar 17451) Annette Bieniusa, Hans-J. Boehm, Maurice Herlihy, and Erez Petrank ........... 1 Algorithmic Cheminformatics (Dagstuhl Seminar 17452) Jakob L. Andersen, Christoph Flamm, Daniel Merkle, and Peter F. Stadler . 28 Connecting Visualization and Data Management Research (Dagstuhl Seminar 17461) Remco Chang, Jean-Daniel Fekete, Juliana Freire, and Carlos E. Scheidegger . 46 A Shared Challenge in Behavioural Specification (Dagstuhl Seminar 17462) Klaus Havelund, Martin Leucker, Giles Reger, and Volker Stolz . 59 Artificial and Computational Intelligence in Games: AI-Driven Game Design (Dagstuhl Seminar 17471) Pieter Spronck, Elisabeth André, Michael Cook, and Mike Preuß . 86 Addressing the Computational Challenges of Personalized Medicine (Dagstuhl Seminar 17472) Niko Beerenwinkel, Holger Fröhlich, and Susan A. Murphy . 130 Reliable Computation and Complexity on the Reals (Dagstuhl Seminar 17481) Norbert T. Müller, Siegfried M. Rump, Klaus Weihrauch, and Martin Ziegler . 142 DagstuhlReports,Vol. 7,Issue11 ISSN2192-5283 ISSN 2192-5283 Published online and open access by Aims and Scope Schloss Dagstuhl – Leibniz-Zentrum für Informatik The periodical Dagstuhl Reports documents the GmbH, Dagstuhl Publishing, Saarbrücken/Wadern, program and the results of Dagstuhl Seminars and Germany. Online available at Dagstuhl Perspectives Workshops. http://www.dagstuhl.de/dagpub/2192-5283 In principal, for each Dagstuhl Seminar or Dagstuhl Perspectives Workshop a report is published that Publication date contains the following: March, 2018 an executive summary of the seminar program and the fundamental results, Bibliographic information published by the Deutsche an overview of the talks given during the seminar Nationalbibliothek (summarized as talk abstracts), and The Deutsche Nationalbibliothek lists this publica- summaries from working groups (if applicable). -

Chicago Journal of Theoretical Computer Science the MIT Press
Chicago Journal of Theoretical Computer Science The MIT Press Volume 1997, Article 1 12 March 1997 ISSN 1073–0486. MIT Press Journals, 55 Hayward St., Cambridge, MA 02142 USA; (617)253-2889; [email protected], [email protected]. Published one article at a time in LATEX source form on the Internet. Pag- ination varies from copy to copy. For more information and other articles see: http://www-mitpress.mit.edu/jrnls-catalog/chicago.html • http://www.cs.uchicago.edu/publications/cjtcs/ • ftp://mitpress.mit.edu/pub/CJTCS • ftp://cs.uchicago.edu/pub/publications/cjtcs • Feige and Kilian Limited vs. Polynomial Nondeterminism (Info) The Chicago Journal of Theoretical Computer Science is abstracted or in- R R R dexed in Research Alert, SciSearch, Current Contents /Engineering Com- R puting & Technology, and CompuMath Citation Index. c 1997 The Massachusetts Institute of Technology. Subscribers are licensed to use journal articles in a variety of ways, limited only as required to insure fair attribution to authors and the journal, and to prohibit use in a competing commercial product. See the journal’s World Wide Web site for further details. Address inquiries to the Subsidiary Rights Manager, MIT Press Journals; (617)253-2864; [email protected]. The Chicago Journal of Theoretical Computer Science is a peer-reviewed scholarly journal in theoretical computer science. The journal is committed to providing a forum for significant results on theoretical aspects of all topics in computer science. Editor in chief: Janos Simon Consulting -

Sok: Tools for Game Theoretic Models of Security for Cryptocurrencies
SoK: Tools for Game Theoretic Models of Security for Cryptocurrencies Sarah Azouvi Alexander Hicks Protocol Labs University College London University College London Abstract form of mining rewards, suggesting that they could be prop- erly aligned and avoid traditional failures. Unfortunately, Cryptocurrencies have garnered much attention in recent many attacks related to incentives have nonetheless been years, both from the academic community and industry. One found for many cryptocurrencies [45, 46, 103], due to the interesting aspect of cryptocurrencies is their explicit consid- use of lacking models. While many papers aim to consider eration of incentives at the protocol level, which has motivated both standard security and game theoretic guarantees, the vast a large body of work, yet many open problems still exist and majority end up considering them separately despite their current systems rarely deal with incentive related problems relation in practice. well. This issue arises due to the gap between Cryptography Here, we consider the ways in which models in Cryptog- and Distributed Systems security, which deals with traditional raphy and Distributed Systems (DS) can explicitly consider security problems that ignore the explicit consideration of in- game theoretic properties and incorporated into a system, centives, and Game Theory, which deals best with situations looking at requirements based on existing cryptocurrencies. involving incentives. With this work, we offer a systemati- zation of the work that relates to this problem, considering papers that blend Game Theory with Cryptography or Dis- Methodology tributed systems. This gives an overview of the available tools, and we look at their (potential) use in practice, in the context As we are covering a topic that incorporates many different of existing blockchain based systems that have been proposed fields coming up with an extensive list of papers would have or implemented. -

Kein Folientitel
182.703: Problems in Distributed Computing (Part 3) WS 2019 Ulrich Schmid Institute of Computer Engineering, TU Vienna Embedded Computing Systems Group E191-02 [email protected] Content (Part 3) The Role of Synchrony Conditions Failure Detectors Real-Time Clocks Partially Synchronous Models Models supporting lock-step round simulations Weaker partially synchronous models Dynamic distributed systems U. Schmid 182.703 PRDC 2 The Role of Synchrony Conditions U. Schmid 182.703 PRDC 3 Recall Distributed Agreement (Consensus) Yes No Yes NoYes? None? meet All meet Yes No No U. Schmid 182.703 PRDC 4 Recall Consensus Impossibility (FLP) Fischer, Lynch und Paterson [FLP85]: “There is no deterministic algorithm for solving consensus in an asynchronous distributed system in the presence of a single crash failure.” Key problem: Distinguish slow from dead! U. Schmid 182.703 PRDC 5 Consensus Solvability in ParSync [DDS87] (I) Dolev, Dwork and Stockmeyer investigated consensus solvability in Partially Synchronous Systems (ParSync), varying 5 „synchrony handles“ : • Processors synchronous / asynchronous • Communication synchronous / asynchronous • Message order synchronous (system-wide consistent) / asynchronous (out-of-order) • Send steps broadcast / unicast • Computing steps atomic rec+send / separate rec, send U. Schmid 182.703 PRDC 6 Consensus Solvability in ParSync [DDS87] (II) Wait-free consensus possible Consensus impossible s/r Consensus possible s+r for f=1 ucast bcast async sync Global message order message Global async sync Communication U. Schmid 182.703 PRDC 7 The Role of Synchrony Conditions Enable failure detection Enforce event ordering • Distinguish „old“ from „new“ • Ruling out existence of stale (in-transit) information • Distinguish slow from dead • Creating non-overlapping „phases of operation“ (rounds) U. -

Chicago Journal of Theoretical Computer Science the MIT Press
Chicago Journal of Theoretical Computer Science The MIT Press Volume 1997, Article 2 3 June 1997 ISSN 1073–0486. MIT Press Journals, Five Cambridge Center, Cambridge, MA 02142-1493 USA; (617)253-2889; [email protected], [email protected]. Published one article at a time in LATEX source form on the Internet. Pag- ination varies from copy to copy. For more information and other articles see: http://www-mitpress.mit.edu/jrnls-catalog/chicago.html • http://www.cs.uchicago.edu/publications/cjtcs/ • ftp://mitpress.mit.edu/pub/CJTCS • ftp://cs.uchicago.edu/pub/publications/cjtcs • Kann et al. Hardness of Approximating Max k-Cut (Info) The Chicago Journal of Theoretical Computer Science is abstracted or in- R R R dexed in Research Alert, SciSearch, Current Contents /Engineering Com- R puting & Technology, and CompuMath Citation Index. c 1997 The Massachusetts Institute of Technology. Subscribers are licensed to use journal articles in a variety of ways, limited only as required to insure fair attribution to authors and the journal, and to prohibit use in a competing commercial product. See the journal’s World Wide Web site for further details. Address inquiries to the Subsidiary Rights Manager, MIT Press Journals; (617)253-2864; [email protected]. The Chicago Journal of Theoretical Computer Science is a peer-reviewed scholarly journal in theoretical computer science. The journal is committed to providing a forum for significant results on theoretical aspects of all topics in computer science. Editor in chief: Janos Simon Consulting -

Combinatorial Topology and Distributed Computing Copyright 2010 Herlihy, Kozlov, and Rajsbaum All Rights Reserved
Combinatorial Topology and Distributed Computing Copyright 2010 Herlihy, Kozlov, and Rajsbaum All rights reserved Maurice Herlihy Dmitry Kozlov Sergio Rajsbaum February 22, 2011 DRAFT 2 DRAFT Contents 1 Introduction 9 1.1 DecisionTasks .......................... 10 1.2 Communication.......................... 11 1.3 Failures .............................. 11 1.4 Timing............................... 12 1.4.1 ProcessesandProtocols . 12 1.5 ChapterNotes .......................... 14 2 Elements of Combinatorial Topology 15 2.1 Theobjectsandthemaps . 15 2.1.1 The Combinatorial View . 15 2.1.2 The Geometric View . 17 2.1.3 The Topological View . 18 2.2 Standardconstructions. 18 2.3 Chromaticcomplexes. 21 2.4 Simplicial models in Distributed Computing . 22 2.5 ChapterNotes .......................... 23 2.6 Exercises ............................. 23 3 Manifolds, Impossibility,DRAFT and Separation 25 3.1 ManifoldComplexes ....................... 25 3.2 ImmediateSnapshots. 28 3.3 ManifoldProtocols .. .. .. .. .. .. .. 34 3.4 SetAgreement .......................... 34 3.5 AnonymousProtocols . .. .. .. .. .. .. 38 3.6 WeakSymmetry-Breaking . 39 3.7 Anonymous Set Agreement versus Weak Symmetry Breaking 40 3.8 ChapterNotes .......................... 44 3.9 Exercises ............................. 44 3 4 CONTENTS 4 Connectivity 47 4.1 Consensus and Path-Connectivity . 47 4.2 Consensus in Asynchronous Read-Write Memory . 49 4.3 Set Agreement and Connectivity in Higher Dimensions . 53 4.4 Set Agreement and Read-Write memory . 59 4.4.1 Critical States . 63 4.5 ChapterNotes .......................... 64 4.6 Exercises ............................. 64 5 Colorless Tasks 67 5.1 Pseudospheres .......................... 68 5.2 ColorlessTasks .......................... 72 5.3 Wait-Free Read-Write Memory . 73 5.3.1 Read-Write Protocols and Pseudospheres . 73 5.3.2 Necessary and Sufficient Conditions . 75 5.4 Read-Write Memory with k-Set Agreement . -

Download This PDF File
T G¨ P 2012 C N Deadline: December 31, 2011 The Gödel Prize for outstanding papers in the area of theoretical computer sci- ence is sponsored jointly by the European Association for Theoretical Computer Science (EATCS) and the Association for Computing Machinery, Special Inter- est Group on Algorithms and Computation Theory (ACM-SIGACT). The award is presented annually, with the presentation taking place alternately at the Inter- national Colloquium on Automata, Languages, and Programming (ICALP) and the ACM Symposium on Theory of Computing (STOC). The 20th prize will be awarded at the 39th International Colloquium on Automata, Languages, and Pro- gramming to be held at the University of Warwick, UK, in July 2012. The Prize is named in honor of Kurt Gödel in recognition of his major contribu- tions to mathematical logic and of his interest, discovered in a letter he wrote to John von Neumann shortly before von Neumann’s death, in what has become the famous P versus NP question. The Prize includes an award of USD 5000. AWARD COMMITTEE: The winner of the Prize is selected by a committee of six members. The EATCS President and the SIGACT Chair each appoint three members to the committee, to serve staggered three-year terms. The committee is chaired alternately by representatives of EATCS and SIGACT. The 2012 Award Committee consists of Sanjeev Arora (Princeton University), Josep Díaz (Uni- versitat Politècnica de Catalunya), Giuseppe Italiano (Università a˘ di Roma Tor Vergata), Mogens Nielsen (University of Aarhus), Daniel Spielman (Yale Univer- sity), and Eli Upfal (Brown University). ELIGIBILITY: The rule for the 2011 Prize is given below and supersedes any di fferent interpretation of the parametric rule to be found on websites on both SIGACT and EATCS. -

Distinguished Lecture Series
DISTINGUISHED LECTURE SERIES NANCY LYNCH NEC Professor of Software Science and Engineering, Department of Electrical Engineering and Computer Science, Massachusetts Institute of Technology “A Theoretical View of Distributed Systems” Thursday, January 30, 2020 • 2-3 p.m Donald Bren Hall, Room 6011 ABSTRACT For several decades, my collaborators, students, and I have worked on theory for distributed systems, in order to understand their capabilities and limitations in a rigorous, mathematical way. This work has produced many different kinds of results, including: • Abstract models for problems that are solved by distributed systems, and for the algorithms used to solve them, • Rigorous proofs of algorithm correctness and performance properties (also some error discoveries), • Impossibility results and lower bounds, expressing inherent limitations of distributed systems, • Some new algorithms, and • General mathematical foundations for modeling and analyzing distributed systems. These various results have spanned many different kinds of systems, ranging from distributed data- management systems, to communication systems, to biological systems such as insect colonies and brains. In this talk, I will overview some highlights of our work over many years on theory for distributed systems. I will break this down in terms of three intertwined “research threads”: algorithms for traditional distributed systems, impossibility results, and mathematical foundations. At the end, I will say something about ourrecent work on algorithms for new kinds of distributed systems. BIO Nancy Lynch is the NEC Professor of Software Science and Engineering in MIT’s EECS department. She heads the Theory of Distributed Systems research group in the Computer Science and AI Laboratory. She received her PhD from MIT and her BS from Brooklyn College, both in Mathematics Lynch has (co-)written many research articles about distributed algorithms and impossibility results, and about formal modeling and verification of distributed systems. -

Tight Bounds for K-Set Agreement Soma Chaudhuri Maurice Herlihy CRL 98/4 Nancy A
TM Tight Bounds for k-Set Agreement Soma Chaudhuri Maurice Herlihy Nancy A. Lynch Mark R. Tuttle CRL 98/4 May 1998 Cambridge Research Laboratory The Cambridge Research Laboratory was founded in 1987 to advance the state of the art in both core computing and human-computerinteraction, and to use the knowledge so gained to support the Company’s corporate objectives. We believe this is best accomplished through interconnected pur- suits in technology creation, advanced systems engineering, and business development. We are ac- tively investigating scalable computing; mobile computing; vision-based human and scene sensing; speech interaction; computer-animated synthetic persona; intelligent information appliances; and the capture, coding, storage, indexing, retrieval, decoding, and rendering of multimedia data. We recognize and embrace a technology creation model which is characterized by three major phases: Freedom: The life blood of the Laboratory comes from the observations and imaginations of our research staff. It is here that challenging research problems are uncovered (through discussions with customers, through interactions with others in the Corporation, through other professional interac- tions, through reading, and the like) or that new ideas are born. For any such problem or idea, this phase culminates in the nucleation of a project team around a well articulated central research question and the outlining of a research plan. Focus: Once a team is formed, we aggressively pursue the creation of new technology based on the plan. This may involve direct collaboration with other technical professionals inside and outside the Corporation. This phase culminates in the demonstrable creation of new technology which may take any of a number of forms - a journal article, a technical talk, a working prototype, a patent application, or some combination of these. -

A Complexity-Based Hierarchy for Multiprocessor Synchronization
A Complexity-Based Hierarchy for Multiprocessor Synchronization Faith Ellen Rati Gelashvili Nir Shavit University of Toronto MIT MIT [email protected] [email protected] [email protected] Leqi Zhu University of Toronto [email protected] Abstract For many years, Herlihy’s elegant computability-based Consensus Hierarchy has been our best ex- planation of the relative power of various types of multiprocessor synchronization objects when used in deterministic algorithms. However, key to this hierarchy is treating synchronization instructions as distinct objects, an approach that is far from the real-world, where multiprocessor programs apply syn- chronization instructions to collections of arbitrary memory locations. We were surprised to realize that, when considering instructions applied to memory locations, the computability based hierarchy collapses. This leaves open the question of how to better capture the power of various synchronization instructions. In this paper, we provide an approach to answering this question. We present a hierarchy of synchro- nization instructions, classified by the space complexity necessary to solve consensus in an obstruction- free manner using these instructions. Our hierarchy provides a classification of combinations of known instructions that seems to fit with our intuition of how useful some are in practice, while questioning the effectiveness of others. In particular, we prove an essentially tight characterization of the power of buffered read and write instructions. Interestingly, we show a similar result for multi-location atomic assignments. 1 Introduction Herlihy’s Consensus Hierarchy [Her91] assigns a consensus number to each object, namely, the number of processes for which there is a wait-free binary consensus algorithm using only instances of this object and read-write registers. -

Chicago Journal of Theoretical Computer Science the MIT Press
Chicago Journal of Theoretical Computer Science The MIT Press Volume 1998, Article 2 16 March 1998 ISSN 1073–0486. MIT Press Journals, Five Cambridge Center, Cambridge, MA 02142-1493 USA; (617)253-2889; [email protected], [email protected]. Published one article at a time in LATEX source form on the Internet. Pag- ination varies from copy to copy. For more information and other articles see: http://mitpress.mit.edu/CJTCS/ • http://www.cs.uchicago.edu/publications/cjtcs/ • ftp://mitpress.mit.edu/pub/CJTCS • ftp://cs.uchicago.edu/pub/publications/cjtcs • Kupferman and Vardi Verification of Systems (Info) The Chicago Journal of Theoretical Computer Science is abstracted or in- R R R dexed in Research Alert, SciSearch, Current Contents /Engineering Com- R puting & Technology, and CompuMath Citation Index. c 1998 The Massachusetts Institute of Technology. Subscribers are licensed to use journal articles in a variety of ways, limited only as required to insure fair attribution to authors and the journal, and to prohibit use in a competing commercial product. See the journal’s World Wide Web site for further details. Address inquiries to the Subsidiary Rights Manager, MIT Press Journals; (617)253-2864; [email protected]. The Chicago Journal of Theoretical Computer Science is a peer-reviewed scholarly journal in theoretical computer science. The journal is committed to providing a forum for significant results on theoretical aspects of all topics in computer science. Editor in chief: Janos Simon Consulting editors: Joseph Halpern, -
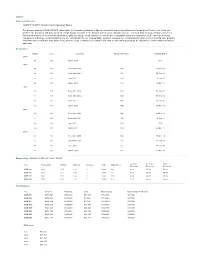
SIGACT Viability
SIGACT Name and Mission: SIGACT: SIGACT Algorithms & Computation Theory The primary mission of ACM SIGACT (Association for Computing Machinery Special Interest Group on Algorithms and Computation Theory) is to foster and promote the discovery and dissemination of high quality research in the domain of theoretical computer science. The field of theoretical computer science is interpreted broadly so as to include algorithms, data structures, complexity theory, distributed computation, parallel computation, VLSI, machine learning, computational biology, computational geometry, information theory, cryptography, quantum computation, computational number theory and algebra, program semantics and verification, automata theory, and the study of randomness. Work in this field is often distinguished by its emphasis on mathematical technique and rigor. Newsletters: Volume Issue Issue Date Number of Pages Actually Mailed 2014 45 01 March 2014 N/A 2013 44 04 December 2013 104 27-Dec-13 44 03 September 2013 96 30-Sep-13 44 02 June 2013 148 13-Jun-13 44 01 March 2013 116 18-Mar-13 2012 43 04 December 2012 140 29-Jan-13 43 03 September 2012 120 06-Sep-12 43 02 June 2012 144 25-Jun-12 43 01 March 2012 100 20-Mar-12 2011 42 04 December 2011 104 29-Dec-11 42 03 September 2011 108 29-Sep-11 42 02 June 2011 104 N/A 42 01 March 2011 140 23-Mar-11 2010 41 04 December 2010 128 15-Dec-10 41 03 September 2010 128 13-Sep-10 41 02 June 2010 92 17-Jun-10 41 01 March 2010 132 17-Mar-10 Membership: based on fiscal year dates 1st Year 2 + Years Total Year Professional