Forensic Acquisition for Windows Mobile Pocketpc
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
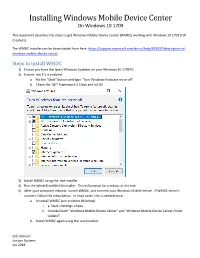
Installing Windows Mobile Device Center on Windows 10 1709
Installing Windows Mobile Device Center On Windows 10 1709 This document describes the steps to get Windows Mobile Device Center (WMDC) working with Windows 10 1709 (Fall Creators). The WMDC installer can be downloaded from here: https://support.microsoft.com/en-us/help/931937/description-of- windows-mobile-device-center Steps to install WMDC 1) Ensure you have the latest Windows Updates on your Windows 10 1709 PC. 2) Ensure .net 3.5 is enabled a. Hit the “Start” button and type “Turn Windows Features on or off” b. Check the .NET Framework 3.5 box and hit OK 3) Install WMDC using the .exe installer. 4) Run the WmdcFixesWin10 installer. This will prompt for a reboot at the end. 5) After your computer reboots, launch WMDC, and connect your Windows Mobile device. If WMDC doesn’t connect, follow the steps below. In most cases, this is needed once. a. Uninstall WMDC (see problem #4 below) i. a. Start->Settings->Apps ii. Uninstall both “Windows Mobile Device Center” and “Windows Mobile Device Center Driver Update”. b. Install WMDC again using the .exe installer. Zeb Johnson Juniper Systems Jan 2018 Problems (these are addressed in the steps above) 1) Initially after 1709 came out, WMDC would not install, complaining about a missing DLL. This has been fixed with a Windows Update. Update KB4054517 (Dec 11 2017 update) has this fixed, and it should carry forward to any future cumulative updates. It is unknown which updates had this fixed first (we didn’t go back any further to test). 2) After installing WMDC, WMDC will fail to launch. -

Current P SYCHIATRY
Current p SYCHIATRY Psyber Psychiatry To upgrade or not to upgrade? Should you purchase a new PDA or wait for the next wave of innovations? Here’s help deciding John Luo, MD Assistant clinical professor of psychiatry UCLA Neuropsychiatric Institute and Hospital Los Angeles, CA ersonal digital assistants (PDA) are in a Cons. PDA operating systems are updated fre- P state of flux. Thanks to a flurry of hard- quently, reflecting continuing improvements in ware and operating system improvements over handheld hardware. Microsoft late last year the last 18 months, PDAs that were cutting-edge upgraded its Pocket PC operating system and last year pale in comparison to newer models. changed its name to Windows Mobile. Should you buy a new PDA now, or stick Although frequent users will rejoice in the with your current model and wait for still more opportunity to do more, others might not want to innovations? This article can help you decide. spend $300 or more to get the latest features— only to see their new device become outmoded in WHY UPGRADE? a few months. Pros. Today’s PDAs are more versatile and intu- itive. For example, many combination PDA/ HARDWARE ADVANCES mobile phones have newer operating systems, Processors. The processor, the heart of a PDA, more memory, and greater software compatibility has also seen much change. Newer Palm and than earlier devices. Pocket PC devices are based A frequent PDA user John Luo, MD on the strongARM micro- who craves more speed or Dr. Luo’s column is processor produced by Intel featured monthly on added features might want to CURRENT PSYCHIATRY’s under the Xscale brand. -

Microsoft Mobility and Security for Enterprise Architects
Microsoft Mobility What IT architects need to know about mobility with Microsoft cloud services and Security for and platforms Enterprise Architects This topic is 1 of 4 in a series 1 2 3 4 Enable productivity and collaboration from anywhere while protecting data and applications Microsoft provides broad support for mobile productivity with support for applications and rich features for controlling access to your organization s assets. Microsoft mobile apps for business Developing your own mobile apps Microsoft produces a number of business class mobile apps for Use the Mobile Apps feature of Azure App Service to build engaging productivity. See page two for featured applications. iOS, Android, and Windows apps or cross-platform Xamarin or Cordova (Phonegap) apps for your customers and business. With an Office 365 for business subscription, you get mobile apps that help you get more done from your favorite device while keeping your Broadcast push with customer data secured. Use Intune Mobile Application Management to apply segmentation additional security when using these mobile applications. Enterprise single sign-on with Active Directory Autoscale to support millions of devices Skype for Business, Yammer, OneNote, and more apps for business Apps can work offline and sync are also available. Get the full list of apps and learn how to set them Social integration with Facebook, up on your devices. Twitter, Google Dynamics CRM also includes apps for phones and tablets. Cloud App Security for SaaS apps Mobile access to on-prem applications Microsoft Cloud App Security is a comprehensive service that provides Microsoft Azure Active Directory Application Proxy lets you publish deeper visibility, comprehensive controls, and improved protection for applications, such as web-based apps inside your private network and your cloud applications. -

Download Play Store Nokia Lumia 520
Download play store nokia lumia 520 LINK TO DOWNLOAD 11/1/ · HOW To download play store on my Lumia This thread is locked. You can follow the question or vote as helpful, but you cannot reply to this thread. Apps Store: All In One App - Your Play Store AppApp Store: All in one app - Your Play store App: save-mobile RAM, memory, time. Free. How to Install apps - Download apps from the::Windows Phone Store:: Nokia / Lumia / Install apps Nokia Lumia Install apps - Nokia Lumia 1 Before you start Before downloading and installing apps on your Lumia, your Microsoft account must be activated. Nokia Lumia PC suite is going to be download from this page. Here is the solution to connect your Nokia Lumia to PC via USB data cable on your windows XP sp3,7,8,10 and Vista on the go. This is the best alternative to Nokia Ovi suite for Lumia which is enabling you to perform various tasks of your device model above mentioned very smartly. Download this app from Microsoft Store for Windows 10 Mobile, Windows Phone , Windows Phone 8. See screenshots, read the latest customer reviews, and compare ratings for Lumia Play to. Cómo instalar Google Play Store en el Nokia Lumia todo lo que debes saber si de verdad quieres encontrar una solución a este problema. 15/6/ · The Google Play Store Whether it is an application to root the Nokia Lumia , an app to generate a backup of the Nokia Lumia , or any other type of app, the procedure is generally the same. -

Mobile Developer's Guide to the Galaxy
Don’t Panic MOBILE DEVELOPER’S GUIDE TO THE GALAXY U PD A TE D & EX TE ND 12th ED EDITION published by: Services and Tools for All Mobile Platforms Enough Software GmbH + Co. KG Sögestrasse 70 28195 Bremen Germany www.enough.de Please send your feedback, questions or sponsorship requests to: [email protected] Follow us on Twitter: @enoughsoftware 12th Edition February 2013 This Developer Guide is licensed under the Creative Commons Some Rights Reserved License. Editors: Marco Tabor (Enough Software) Julian Harty Izabella Balce Art Direction and Design by Andrej Balaz (Enough Software) Mobile Developer’s Guide Contents I Prologue 1 The Galaxy of Mobile: An Introduction 1 Topology: Form Factors and Usage Patterns 2 Star Formation: Creating a Mobile Service 6 The Universe of Mobile Operating Systems 12 About Time and Space 12 Lost in Space 14 Conceptional Design For Mobile 14 Capturing The Idea 16 Designing User Experience 22 Android 22 The Ecosystem 24 Prerequisites 25 Implementation 28 Testing 30 Building 30 Signing 31 Distribution 32 Monetization 34 BlackBerry Java Apps 34 The Ecosystem 35 Prerequisites 36 Implementation 38 Testing 39 Signing 39 Distribution 40 Learn More 42 BlackBerry 10 42 The Ecosystem 43 Development 51 Testing 51 Signing 52 Distribution 54 iOS 54 The Ecosystem 55 Technology Overview 57 Testing & Debugging 59 Learn More 62 Java ME (J2ME) 62 The Ecosystem 63 Prerequisites 64 Implementation 67 Testing 68 Porting 70 Signing 71 Distribution 72 Learn More 4 75 Windows Phone 75 The Ecosystem 76 Implementation 82 Testing -

Dolphin Power Tools User's Guide Rev E
Dolphin® Power Tools For Windows Mobile® 5.0 Windows Mobile® 2003 Second Edition Windows® CE 5.0 (Dolphin 6100, 6500, 7600) User’s Guide Disclaimer Honeywell International Inc. (“HII”) reserves the right to make changes in specifications and other information contained in this document without prior notice, and the reader should in all cases consult HII to determine whether any such changes have been made. The information in this publication does not represent a commitment on the part of HII. HII shall not be liable for technical or editorial errors or omissions contained herein; nor for incidental or consequential damages resulting from the furnishing, performance, or use of this material. This document contains proprietary information that is protected by copyright. All rights are reserved. No part of this document may be photocopied, reproduced, or translated into another language without the prior written consent of HII. ©2007–2010 Honeywell International Inc. All rights reserved. Web Address: www.honeywellaidc.com Trademarks Dolphin, Dolphin RF, HomeBase, Mobile Base, and QuadCharger are trademarks or registered trademarks of Hand Held Products, Inc. or Honeywell International Inc. Microsoft, Windows, Windows Mobile, Windows CE, Windows NT, Windows 2000, Windows ME, Windows XP, ActiveSync, Outlook, and the Windows logo are trademarks or registered trademarks of Microsoft Corporation. Other product names mentioned in this manual may be trademarks or registered trademarks of their respective companies and are the property of their respective owners. Patents Please refer to the product packaging for a list of patents. Other Trademarks The Bluetooth trademarks are owned by Bluetooth SIG, Inc. U.S.A. -

HTC SPV MDA G1 Zdalny Unlock Kodem Po IMEI - Również DESIRE
GSM-Support ul. Bitschana 2/38, 31-420 Kraków mobile +48 608107455, NIP PL9451852164 REGON: 120203925 www.gsm-support.net HTC SPV MDA G1 zdalny unlock kodem po IMEI - również DESIRE Jest to usługa pozwalająca na zdjęcie simlocka z telefonów HTC / SPV / QTEK / MDA / G1-Google / Xperia poprzez kod - łącznie z najnowszą bazą! Kod podawany jest na podstawie numeru IMEI, modelu oraz sieci, w której jest simlock. Numer IMEI można sprawdzić w telefonie poprzez wybranie na klawiaturze *#06#. Do każdego numeru IMEI przyporządkowany jest jeden kod. W polu na komentarz prosimy podać model, IMEI oraz kraj i nazwę sieci, w której jest załozony simlock. Czas oczekiwania na kod to średnio 2h. Nie zdejmujemy simlocków kodem z HTC Touch HD z sieci Play, HTC Touch Pro z Orange Polska i innych, które wyraźnie są wymienione na samym dole opisu! Usługa obejmuje modele: DOPOD 310 (HTC Oxygen) DOPOD 535 (HTC Voyager) DOPOD 565 (HTC Typhoon) DOPOD 566 (HTC Hurricane) DOPOD 575 (HTC Feeler) DOPOD 577W (HTC Tornado) DOPOD 585 (HTC Amadeus) DOPOD 586 (HTC Hurricane) DOPOD 586W (HTC Tornado) DOPOD 595 (HTC Breeze) DOPOD 686 (HTC Wallaby) DOPOD 696 (HTC Himalaya) DOPOD 696i (HTC Himalaya) DOPOD 699 (HTC Alpine) DOPOD 700 (HTC Blueangel) DOPOD 710 (HTC Startrek) DOPOD 710+ (HTC Startrek) DOPOD 818 (HTC Magician) DOPOD 818 Pro (HTC Prophet) DOPOD 818C (HTC Wave) DOPOD 828 (HTC Magician) DOPOD 828+ (HTC Magician) DOPOD 830 (HTC Prophet) DOPOD 838 (HTC Wizard) DOPOD 838 Pro (HTC Hermes) DOPOD 900 (HTC Universal) DOPOD C500 (HTC Vox) DOPOD C720 (HTC Excalibur) DOPOD C720W -

Microsoft's Zune HD Leaked 15 April 2009, by John Messina
Microsoft's Zune HD Leaked 15 April 2009, by John Messina HD, which some sites have been talking about, will be leaking sometime soon. This will gives us a better idea of its dimensions and screen menus. The Zune HD is expected to be available the fourth quarter of this year, most likely in September. Microsoft also plans to make improvements to the Zune Marketplace and expand its Zune platform beyond just the US and Canada. © 2009 PhysOrg.com (PhysOrg.com) -- It looks like Microsoft's Zune HD player will be a strong competition for Apple's iPod Touch. Uunconfirmed technical specifications of Microsoft's Zune HD player have now emerged and the new portable media player looks like a good contender with Apple's Touch. The Zune HD will feature a multitouch OLED screen with a 16:9 aspect ratio and an HDMI TV output port. The Zune HD will be available in a 16 and 32 GB version. Both versions will have wireless support that will allow you to sync the device with a computer. There's also some speculation that the Zune HD may use the Nvidia's Tegra chipset that would support 3D xbox games. There will also be a Web browser incorporated into the player but no word yet as to what browser will be used. There's also speculation that the Zune HD may be running on Windows Mobile 6.5 which is expected to be released Q4, same as the player. Sources have confirmed that the Zune HD is Microsoft's next version of portable media players. -

Developing Applications for Pocket PC and GPRS/EDGE Devcentral White Paper
Developing Applications for Pocket PC and GPRS/EDGE devCentral White Paper Document Number 12588 Revision 2.0 Revision Date 10/15/03 AT&T Wireless Developer Program © 2003 AT&T Wireless. All rights reserved. Legal Disclaimer This document and the information contained herein (collectively, the "Information") is provided to you (both the individual receiving this document and any legal entity on behalf of which such individual is acting) ("You" and "Your") by AT&T Wireless Services, Inc. ("AWS") for informational purposes only. AWS is providing the Information to You because AWS believes the Information may be useful to You. The Information is provided to You solely on the basis that You will be responsible for making Your own assessments of the Information and are advised to verify all representations, statements and information before using or relying upon any of the Information. Although AWS has exercised reasonable care in providing the Information to You, AWS does not warrant the accuracy of the Information and is not responsible for any damages arising from Your use of or reliance upon the Information. You further understand and agree that AWS in no way represents, and You in no way rely on a belief, that AWS is providing the Information in accordance with any standard or service (routine, customary or otherwise) related to the consulting, services, hardware or software industries. AWS DOES NOT WARRANT THAT THE INFORMATION IS ERROR-FREE. AWS IS PROVIDING THE INFORMATION TO YOU "AS IS" AND "WITH ALL FAULTS." AWS DOES NOT WARRANT, -

LNCS 5101, Pp
Database Prebuffering as a Way to Create a Mobile Control and Information System with Better Response Time Ondrej Krejcar and Jindrich Cernohorsky VSB Technical University of Ostrava, Center of Applied Cybernetics, Department of measurement and control, 17. Listopadu 15, 70833 Ostrava Poruba, Czech Republic {Ondrej.Krejcar,Jindrich.Cernohorsky}@vsb.cz Abstract. Location-aware services can benefit from indoor location tracking. The widespread adoption of Wi-Fi as the network infrastructure creates the opportunity of deploying WiFi-based location services with no additional hardware costs. Additionally, the ability to let a mobile device determine its location in an indoor environment supports the creation of a new range of mobile control system applications. Main area of interest is in a model of a radio-frequency based system enhancement for locating and tracking users of our control system inside the buildings. The developed framework as it is described here joins the concepts of location and user tracking as an extension for a new control system. The experimental framework prototype uses a WiFi network infrastructure to let a mobile device determine its indoor position. User location is used for data pre-buffering and pushing information from server to user’s PDA. All server data is saved as artifacts (together) with its position information in building. Keywords: prebuffering; localization; framework; Wi-Fi; 802.11x; PDA. 1 Introduction The usage of various wireless technologies has been increased dramatically and would be growing in the following years. This will lead to the rise of new application domains each with their own specific features and needs. Also these new domains will undoubtedly apply and reuse existing (software) paradigms, components and applications. -

Microsoft Office Mobile (Windows Phone 7 版) 製品ガド
Microsoft Office Mobile (Windows Phone 7 版) 製品ガド 目次 Microsoft Office Mobile: 概要 .......................................................................................................................... 1 Office Mobile: 概要 ............................................................................................................................................ 2 Office Mobile: 詳細 ............................................................................................................................................ 3 Office ドキュメントの表示と更新 ........................................................................................................................................... 3 Office ハブ - 新機能 ............................................................................................................................................................ 3 ユーザー ンターフェス - 強化機能 ..................................................................................................................... 5 コメント - 新機能 ................................................................................................................................................................ 7 フゔル形式のサポート - 強化機能 ........................................................................................................................... 8 各製品の特長 .................................................................................................................................................................................... 9 Word Mobile ......................................................................................................................................................................... -

Towards the Quality Improvement of Cross-Platform Mobile Applications
Towards the quality improvement of cross-platform mobile applications Matias Martinez, Sylvain Lecomte Univ Lille Nord de France, F-59000 Lille, France, Universit´ede Valenciennes et du Hainaut Cambr´esis, Laboratoire LAMIH - UMR CNRS 8201 59313 Valenciennes Cedex 9 [email protected] Abstract—During last ten years, the number of smartphones A current challenge for business enterprises, software com- and mobile applications has been constantly growing. Android, panies, and independent mobile developers is to choose the iOS and Windows Mobile are three mobile platforms that cover target platforms for their mobile applications. To cover a large almost all smartphones in the world in 2017. Developing a mobile app involves first to choose the platforms the app will run, and number of users, companies and developers aim at releasing then to develop specific solutions (i.e., native apps) for each their mobile apps on the three mentioned platforms. More chosen platform using platform-related toolkits such as Android platforms targeted involves to potentially reach more users SDK. A cross-platform mobile application is an app that runs on and, thus, to increase the impact on the market. two or more mobile platforms. Several frameworks have been However, nowadays, creating a cross-platform application proposed to simplify the development of cross-platform mobile applications and to reduce development and maintenance costs. as we mentioned, implies the development of one native They are called cross-platform mobile app development frameworks. application for each platform to target. Thus, companies have However, to our knowledge, the life-cycle and the quality of cross- to afford the cost of two or more development processes platforms mobile applications built using those frameworks have of their cross-platform apps.