Windows Phone 7: Implications for Digital Forensic Investigators
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Here Is Event: Nokia Announced the Lumia Windows Benefit to Both Nokia and Microsoft
Workplace Service First Cut Number: 2011-FC10 Aragon November 1, 2011 Research Topics: Mobile Issues: What are the trends impacting mobile computing? What are the technologies and architectures that make up a mobile ___________________________________________________________________________________________________________Author: Mike Anderson ecosystem? " " Nokia and Microsoft: Partnership Bears building the much-needed ecosystem, but right First Fruit in Mobile Ecosystem Battle now Windows 7 Phone remains far behind the leaders with apps in its Windows Phone Summary: On October 26th at its Nokia World Marketplace. 2011 event in London, Nokia announced the Lumia 800 and 710, its first smartphones Overall, the main intent of these initial Windows based on Windows Phone 7. Phone 7 products is to establish presence in markets historically loyal to Nokia. There is Event: Nokia announced the Lumia Windows benefit to both Nokia and Microsoft. Nokia Phone-based line of smartphones as the first feature phone users who want smartphone step to replace its own Symbian ecosystem on options now have a viable choice from Nokia, the journey to competing with Apple and and they have them ahead of the 2011 Google. holidays. Microsoft has a partner with solid devices to advance its need for relevance in Analysis: Nokia’s strategy, outlined by new mobile, and the smartphone market. CEO Stephen Elop in February 2011, promised decisive and swift action in replacing its failing Nokia’s Windows Phones will not launch in the Symbian operating system for smartphones U.S. until 2012. Building on its strengths, Nokia with Windows Phone 7 through Nokia’s is launching in Europe first, with more countries partnership with Microsoft. -
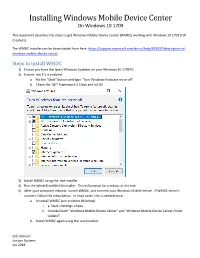
Installing Windows Mobile Device Center on Windows 10 1709
Installing Windows Mobile Device Center On Windows 10 1709 This document describes the steps to get Windows Mobile Device Center (WMDC) working with Windows 10 1709 (Fall Creators). The WMDC installer can be downloaded from here: https://support.microsoft.com/en-us/help/931937/description-of- windows-mobile-device-center Steps to install WMDC 1) Ensure you have the latest Windows Updates on your Windows 10 1709 PC. 2) Ensure .net 3.5 is enabled a. Hit the “Start” button and type “Turn Windows Features on or off” b. Check the .NET Framework 3.5 box and hit OK 3) Install WMDC using the .exe installer. 4) Run the WmdcFixesWin10 installer. This will prompt for a reboot at the end. 5) After your computer reboots, launch WMDC, and connect your Windows Mobile device. If WMDC doesn’t connect, follow the steps below. In most cases, this is needed once. a. Uninstall WMDC (see problem #4 below) i. a. Start->Settings->Apps ii. Uninstall both “Windows Mobile Device Center” and “Windows Mobile Device Center Driver Update”. b. Install WMDC again using the .exe installer. Zeb Johnson Juniper Systems Jan 2018 Problems (these are addressed in the steps above) 1) Initially after 1709 came out, WMDC would not install, complaining about a missing DLL. This has been fixed with a Windows Update. Update KB4054517 (Dec 11 2017 update) has this fixed, and it should carry forward to any future cumulative updates. It is unknown which updates had this fixed first (we didn’t go back any further to test). 2) After installing WMDC, WMDC will fail to launch. -

Microsoft'sevolving App Strategy
CAN MICROSOFT MAP THE FUTURE OF IT? Microsoft’s Evolving App Strategy Microsoft is trying to better align its applications through a new interface and improved cloud connectivity. Is this the right strategy? BY BRIEN M. POSEY THE NEW INTERFACE WHERE RT AND OFFICE FIT CLOUD CONNECTIVITY CAN MICROSOFT MAP THE FUTURE OF IT? VER THE PAST two decades, Microsoft’s strategy for desktop and mobile ap- plications has remained relatively static. Microsoft devoted much of its energy to creating operating systems and allowed applications to develop almost as an afterthought. THE NEW Even today the company adheres to this haphazard approach to applications. INTERFACE O At the same time, the company’s most recent product-release cycle demonstrates that Microsoft’s support for desktop and mobile apps is evolving. WHERE RT AND OFFICE FIT When it comes to application support in the company’s latest releases, two major themes have emerged: the new tile-based user interface (UI) and cloud con- nectivity. While both of these technologies benefit a segment of Microsoft’s cus- CLOUD CONNECTIVITY tomer base, they have also created numerous challenges for IT professionals. In particular, the new Windows 8 interface has been an impediment to adop- tion among business users, but it is part of a concerted effort on Microsoft’s part to build consistency throughout its application set. Despite this imperfect strat- egy, there are signs that the approach is pointing Microsoft in a direction that al- lows business users to productively use Windows, Office and other applications on PCs, tablets and smartphones. 2 MICROSOFT’S EVOLVING APP STRATEGY THE NEW INTERFACE WINDOWS’ NEW INTERFACE The most well-known element of the Windows 8 operating system is the new user interface (which at one time was called the Metro interface and is now known as the Windows 8-style UI). -

Microsoft Mobility and Security for Enterprise Architects
Microsoft Mobility What IT architects need to know about mobility with Microsoft cloud services and Security for and platforms Enterprise Architects This topic is 1 of 4 in a series 1 2 3 4 Enable productivity and collaboration from anywhere while protecting data and applications Microsoft provides broad support for mobile productivity with support for applications and rich features for controlling access to your organization s assets. Microsoft mobile apps for business Developing your own mobile apps Microsoft produces a number of business class mobile apps for Use the Mobile Apps feature of Azure App Service to build engaging productivity. See page two for featured applications. iOS, Android, and Windows apps or cross-platform Xamarin or Cordova (Phonegap) apps for your customers and business. With an Office 365 for business subscription, you get mobile apps that help you get more done from your favorite device while keeping your Broadcast push with customer data secured. Use Intune Mobile Application Management to apply segmentation additional security when using these mobile applications. Enterprise single sign-on with Active Directory Autoscale to support millions of devices Skype for Business, Yammer, OneNote, and more apps for business Apps can work offline and sync are also available. Get the full list of apps and learn how to set them Social integration with Facebook, up on your devices. Twitter, Google Dynamics CRM also includes apps for phones and tablets. Cloud App Security for SaaS apps Mobile access to on-prem applications Microsoft Cloud App Security is a comprehensive service that provides Microsoft Azure Active Directory Application Proxy lets you publish deeper visibility, comprehensive controls, and improved protection for applications, such as web-based apps inside your private network and your cloud applications. -

Download Play Store Nokia Lumia 520
Download play store nokia lumia 520 LINK TO DOWNLOAD 11/1/ · HOW To download play store on my Lumia This thread is locked. You can follow the question or vote as helpful, but you cannot reply to this thread. Apps Store: All In One App - Your Play Store AppApp Store: All in one app - Your Play store App: save-mobile RAM, memory, time. Free. How to Install apps - Download apps from the::Windows Phone Store:: Nokia / Lumia / Install apps Nokia Lumia Install apps - Nokia Lumia 1 Before you start Before downloading and installing apps on your Lumia, your Microsoft account must be activated. Nokia Lumia PC suite is going to be download from this page. Here is the solution to connect your Nokia Lumia to PC via USB data cable on your windows XP sp3,7,8,10 and Vista on the go. This is the best alternative to Nokia Ovi suite for Lumia which is enabling you to perform various tasks of your device model above mentioned very smartly. Download this app from Microsoft Store for Windows 10 Mobile, Windows Phone , Windows Phone 8. See screenshots, read the latest customer reviews, and compare ratings for Lumia Play to. Cómo instalar Google Play Store en el Nokia Lumia todo lo que debes saber si de verdad quieres encontrar una solución a este problema. 15/6/ · The Google Play Store Whether it is an application to root the Nokia Lumia , an app to generate a backup of the Nokia Lumia , or any other type of app, the procedure is generally the same. -

Performance and Power Characterization of Cellular Networks and Mobile Application Optimizations
Performance and Power Characterization of Cellular Networks and Mobile Application Optimizations by Junxian Huang A dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy (Computer Science and Engineering) in The University of Michigan 2013 Doctoral Committee: Associate Professor Z. Morley Mao, Chair Associate Professor Jason N. Flinn Associate Professor Robert Dick Technical Staff Subhabrata Sen, AT&T Labs Research c Junxian Huang 2013 All Rights Reserved To my family and my love. ii ACKNOWLEDGEMENTS I became a graduate student in the University of Michigan in the fall of 2008. Five years have passed and I would like to thank many people during this long and unique Ph.D. journey in my life. The completion of this dissertation would not be possible without anyone of them. First of all, I would like to sincerely thank my advisor, Professor Z. Morley Mao. I first met her when I was an intern in Microsoft Research Asia in 2007, wondering about my future, and she offered me much helpful advice for pursuing a Ph.D. degree in the U.S. Morley has provided me excellent and professional guidance on various research projects throughout my Ph.D. study, given her expertise in the computer networking and mobile computing, as well as delicious birthday cakes, when even I forgot my birthday myself. Moreover, she helped me gain the confidence, ability and most importantly, the enthusiasm to tackle difficult real-world problems. Her diligence and enthusiasm has set a great model for me and the experiences working with her would be my life-long treasure. -

Mobile Developer's Guide to the Galaxy
Don’t Panic MOBILE DEVELOPER’S GUIDE TO THE GALAXY U PD A TE D & EX TE ND 12th ED EDITION published by: Services and Tools for All Mobile Platforms Enough Software GmbH + Co. KG Sögestrasse 70 28195 Bremen Germany www.enough.de Please send your feedback, questions or sponsorship requests to: [email protected] Follow us on Twitter: @enoughsoftware 12th Edition February 2013 This Developer Guide is licensed under the Creative Commons Some Rights Reserved License. Editors: Marco Tabor (Enough Software) Julian Harty Izabella Balce Art Direction and Design by Andrej Balaz (Enough Software) Mobile Developer’s Guide Contents I Prologue 1 The Galaxy of Mobile: An Introduction 1 Topology: Form Factors and Usage Patterns 2 Star Formation: Creating a Mobile Service 6 The Universe of Mobile Operating Systems 12 About Time and Space 12 Lost in Space 14 Conceptional Design For Mobile 14 Capturing The Idea 16 Designing User Experience 22 Android 22 The Ecosystem 24 Prerequisites 25 Implementation 28 Testing 30 Building 30 Signing 31 Distribution 32 Monetization 34 BlackBerry Java Apps 34 The Ecosystem 35 Prerequisites 36 Implementation 38 Testing 39 Signing 39 Distribution 40 Learn More 42 BlackBerry 10 42 The Ecosystem 43 Development 51 Testing 51 Signing 52 Distribution 54 iOS 54 The Ecosystem 55 Technology Overview 57 Testing & Debugging 59 Learn More 62 Java ME (J2ME) 62 The Ecosystem 63 Prerequisites 64 Implementation 67 Testing 68 Porting 70 Signing 71 Distribution 72 Learn More 4 75 Windows Phone 75 The Ecosystem 76 Implementation 82 Testing -

Mobiliųjų Telefonų Modeliai, Kuriems Tinka Ši Programinė Įranga
Mobiliųjų telefonų modeliai, kuriems tinka ši programinė įranga Telefonai su BlackBerry operacinė sistema 1. Alltel BlackBerry 7250 2. Alltel BlackBerry 8703e 3. Sprint BlackBerry Curve 8530 4. Sprint BlackBerry Pearl 8130 5. Alltel BlackBerry 7130 6. Alltel BlackBerry 8703e 7. Alltel BlackBerry 8830 8. Alltel BlackBerry Curve 8330 9. Alltel BlackBerry Curve 8530 10. Alltel BlackBerry Pearl 8130 11. Alltel BlackBerry Tour 9630 12. Alltel Pearl Flip 8230 13. AT&T BlackBerry 7130c 14. AT&T BlackBerry 7290 15. AT&T BlackBerry 8520 16. AT&T BlackBerry 8700c 17. AT&T BlackBerry 8800 18. AT&T BlackBerry 8820 19. AT&T BlackBerry Bold 9000 20. AT&T BlackBerry Bold 9700 21. AT&T BlackBerry Curve 22. AT&T BlackBerry Curve 8310 23. AT&T BlackBerry Curve 8320 24. AT&T BlackBerry Curve 8900 25. AT&T BlackBerry Pearl 26. AT&T BlackBerry Pearl 8110 27. AT&T BlackBerry Pearl 8120 28. BlackBerry 5810 29. BlackBerry 5820 30. BlackBerry 6210 31. BlackBerry 6220 32. BlackBerry 6230 33. BlackBerry 6280 34. BlackBerry 6510 35. BlackBerry 6710 36. BlackBerry 6720 37. BlackBerry 6750 38. BlackBerry 7100g 39. BlackBerry 7100i 40. BlackBerry 7100r 41. BlackBerry 7100t 42. BlackBerry 7100v 43. BlackBerry 7100x 1 44. BlackBerry 7105t 45. BlackBerry 7130c 46. BlackBerry 7130e 47. BlackBerry 7130g 48. BlackBerry 7130v 49. BlackBerry 7210 50. BlackBerry 7230 51. BlackBerry 7250 52. BlackBerry 7270 53. BlackBerry 7280 54. BlackBerry 7290 55. BlackBerry 7510 56. BlackBerry 7520 57. BlackBerry 7730 58. BlackBerry 7750 59. BlackBerry 7780 60. BlackBerry 8700c 61. BlackBerry 8700f 62. BlackBerry 8700g 63. BlackBerry 8700r 64. -

UI Design and Interaction Guide for Windows Phone 7
UI Design and Interaction Guide 7 for Windows Phone 7 July 2010 Version 2.0 UI Design and Interaction Guide for Windows Phone 7 July 2010 Version 2.0 This is pre-release documentation and is subject to change in future releases. This document supports a preliminary release of a software product that may be changed substantially prior to final commercial release. This docu- ment is provided for informational purposes only and Microsoft makes no warranties, either express or implied, in this document. Information in this document, including URL and other Internet Web site references, is subject to change without notice. The entire risk of the use or the results from the use of this document remains with the user. Unless otherwise noted, the companies, organizations, products, domain names, e-mail addresses, logos, people, places, and events depicted in examples herein are fictitious. No association with any real company, organization, product, domain name, e-mail address, logo, person, place, or event is intended or should be inferred. Complying with all applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form or by any means (electronic, mechanical, photocopying, recording, or otherwise), or for any purpose, without the express written permission of Microsoft Corporation. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this docu- ment. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. -

Microsoft's Zune HD Leaked 15 April 2009, by John Messina
Microsoft's Zune HD Leaked 15 April 2009, by John Messina HD, which some sites have been talking about, will be leaking sometime soon. This will gives us a better idea of its dimensions and screen menus. The Zune HD is expected to be available the fourth quarter of this year, most likely in September. Microsoft also plans to make improvements to the Zune Marketplace and expand its Zune platform beyond just the US and Canada. © 2009 PhysOrg.com (PhysOrg.com) -- It looks like Microsoft's Zune HD player will be a strong competition for Apple's iPod Touch. Uunconfirmed technical specifications of Microsoft's Zune HD player have now emerged and the new portable media player looks like a good contender with Apple's Touch. The Zune HD will feature a multitouch OLED screen with a 16:9 aspect ratio and an HDMI TV output port. The Zune HD will be available in a 16 and 32 GB version. Both versions will have wireless support that will allow you to sync the device with a computer. There's also some speculation that the Zune HD may use the Nvidia's Tegra chipset that would support 3D xbox games. There will also be a Web browser incorporated into the player but no word yet as to what browser will be used. There's also speculation that the Zune HD may be running on Windows Mobile 6.5 which is expected to be released Q4, same as the player. Sources have confirmed that the Zune HD is Microsoft's next version of portable media players. -

Htc Kaiser User Manual Download Htc Kaiser User Manual
Htc Kaiser User Manual Download Htc Kaiser User Manual Even if anyone have any broken HTC Kaiser TyTn II laying around collecting dust im interested in these as well if i cant find the manuals ill buy the broken units for parts etc. Thanks in advance. DaveShaw HTC Kaiser alias MDA Vario III We should expect to see quite soon at T-Mobile the HTC Kaiser smartphone which will appear under the name of MDA Vario III, as the German operator will rename it. Para encontrar más libros sobre kaiser mix 2306dusb manual pdf, puede utilizar las palabras clave relacionadas : Aluminum Extrusion Die Design Kaiser, Introductory Circuit Analysis Laboratory Manual Solution Manual, Manual Practical Manual Of Vampirism Paulo Coelho, Solution Manual-instructer Manual-java Programming-pdf, CISA "manual 2012" "manual 2014", Solution Manual For Coulson And.HTC Kaiser. Jan 2, 2008 by wheaties82. Previously I had owned the 8525 and enjoyed its functionality and versatility, however the phone began giving me the white screen of death and so I was.“HTC Connection Settings” is a free app from HTC which comes pre-loaded on some of HTC’s Windows Phone 7 mobile phones and can be downloaded from the company’s “HTC Hub” app or from the Marketplace. Unfortunately, this app suddenly decided that my phone didn’t need data access anymore – talk about bad news. HTC TyTN II - user opinions and reviews. Released 2007, July 190g, 19mm thickness Microsoft Windows Mobile 6.0 Professional. HTC Kaiser HTC TyTN II HTC P4550 AT&T 8925. Rating 0 | Reply; Is there any mobile that will allow me to connect an Ipod Touch to the Internet via wifi no matter where I am if I purchase web n walk (or an alternative). -

The HTC HD7 Boasting an Impressive 4.3 Inch Display
Mar 12, 2011 21:53 GMT The HTC HD7 boasting an impressive 4.3 inch display The HTC HD7 has a very large and impressive 4.3 display and kickstand to allow it to sit upright when viewing back those videos in High Definition recorded with the phones own 5 megapixel camera. The phone which operates the new Windows Phone OS 7 operating system comes with many impressive features such as customisable tiles on the Start screen which update information live when you hit the front physical key. The handset is powered by a 1 GHz processor and supported by 576 megabytes of random access memory to power multiple applications at once. Internal storage is offered by a read-only memory of 512 megabytes along with a further 8 gigabytes of storage. Connectivity is provided with a standard microUSB connector for syncing and more, along with Bluetooth 2.1 with Enhanced Data Rate including the A2DP and AVRCP profiles for audio sharing to wireless stereo headsets and other devices. The HD7 allows you to see photos form the 5 megapixel camera with auto offices and dual LED flash on the Pictures hub (application) along with live photos on Facebook or Windows Live all together. The Music and Videos hub which is powered by Zune, also lets you download music, and listen to the radio among other features. The handset features impressive sound alongside the High Definition capabilities, with Dolby Mobile and SRS surround sound featured. The phone provides a Start screen which can be customised with multiple live tiles which dynamically update all the relevant information such as missed calls, new text messages, a friends new Facebook status or a change in the weather.